Phishing Attacks: Types, Real-World Examples, Prevention Tips, and How to Respond

Hoplon InfoSec
31 Mar, 2025
Phishing Attacks are one of the most widespread and persistent cyber threats in the digital world. Every year, millions of individuals and businesses fall victim to phishing scams that steal data, money, or compromise systems. In this comprehensive guide, we’ll explore how phishing works, its different types, real-life examples, prevention strategies, and how to respond if you become a victim.
What are Phishing Attacks
Phishing is a form of online fraud that tricks people into revealing sensitive data—like passwords, banking details, or identity information—or downloading malware. It’s a social engineering attack where cybercriminals impersonate trusted sources such as banks, colleagues, or service providers to bait victims into taking unsafe actions.
Phishing messages often appear urgent, claiming that an account is compromised, a payment is pending, or an opportunity awaits. These messages are typically delivered via email, text, phone calls, or social media and often include malicious links or attachments. The goal is to lure users into clicking or sharing private information.
How Phishing Works (And Why It’s So Effective)
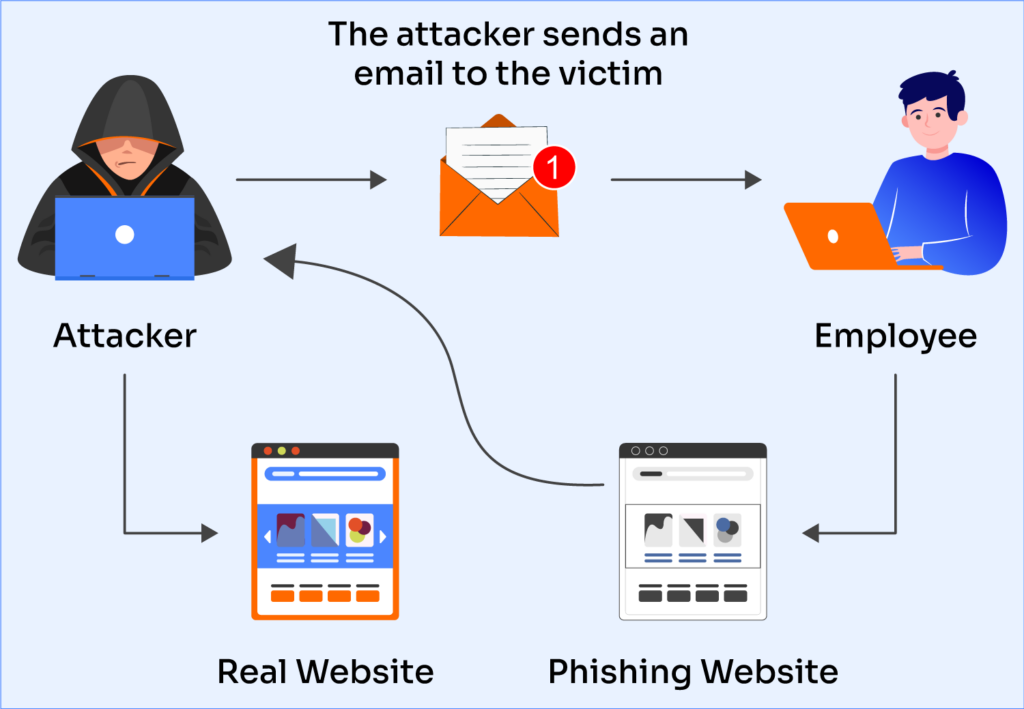
Phishing attacks typically unfold in four stages:
- Impersonation and Setup: Attackers research and impersonate a credible source. They may spoof email addresses, clone websites, and copy logos to make communications look authentic.
- The Lure: Messages create urgency or fear—like fake account lockouts or suspicious activity alerts—prompting users to act quickly.
- The Hook: Victims are asked to click a link, download a file, or enter credentials into a fake site. These actions either steal data or infect devices with malware.
- The Exploit: Stolen data is used to access accounts, commit fraud, or infiltrate networks. In advanced attacks, this initial access leads to larger breaches.
Phishing Attacks work because they target human behavior—not technical flaws. Even tech-savvy users can be tricked during busy moments, making awareness and caution vital.
Common Types of Phishing Attacks
Cybercriminals use different phishing methods based on their target and delivery channel. Here’s a breakdown:
1. Email Phishing Attacks: The most familiar form, email phishing, involves mass emails from seemingly trustworthy sources. These often include fake login links or infected attachments. Messages usually sound urgent or enticing—like “Reset your password now” or “Your account has been compromised.”
Tip: Look for signs like generic greetings, poor grammar, strange sender addresses, or mismatched URLs.
2. Spear Phishing Attacks: Unlike generic phishing, spear phishing targets specific individuals. Attackers research victims to craft tailored messages, often posing as colleagues or vendors. For example, an employee may receive an email from a fake CFO requesting login credentials or financial transfers.
3. Whaling: Whaling targets senior executives, CEOs, or financial officers. These attacks aim for high-stakes rewards, like tricking a company into wiring large sums. Messages often appear urgent and confidential, impersonating legal, financial, or C-suite contacts.
4. Vishing (Voice Phishing): In vishing, attackers call victims pretending to be tech support, government agencies, or banks. They often spoof caller IDs to appear legitimate. Victims may be urged to install malicious Software or share PINs and passwords.
5. Smishing (SMS Phishing): Smishing involves Phishing via text messages. Messages often mimic banks, delivery services, or popular brands and include malicious links or phone numbers. A fake text might say: “Your package is delayed—confirm details here [malicious link].”
6. Angler Phishing Attacks (Social Media): Cybercriminals use fake social media accounts to impersonate customer support or individuals. They monitor posts for complaints or inquiries, then respond with phishing links or ask for sensitive info via DMs.
7. Search Engine Phishing (SEO Poisoning): Attackers create fake websites (e.g., fake tech support or download pages) and push them to rank high in search engines. Unsuspecting users searching for services may click these malicious links and fall into phishing traps.
8. Clone Phishing Attacks: Attackers duplicate a legitimate email you’ve received but replace links or attachments with malicious ones. Since the email looks familiar, you’re more likely to trust it.
9. Pop-up Phishing Attacks: Also known as in-browser Phishing, this involves fake login pop-ups or virus warnings on websites. Victims may be tricked into entering credentials or downloading malware.
10. Pharming: Pharming redirects users to fake websites even when they type in the correct URL. This may happen due to malware or DNS manipulation, making it hard to detect.
Real-World Phishing Examples
1. Target Breach (2013): Attackers compromised a third-party vendor via Phishing and then used stolen credentials to access Target’s network. Malware was deployed on POS systems, compromising 40 million credit cards.
2. Google & Facebook (2013–2015): A scammer impersonated a vendor and sent fake invoices to both companies. They wired over $100 million to fraudulent accounts before discovering the fraud.
3. FACC CEO Fraud (2016): An Austrian aerospace company lost €42 million after a finance employee acted on an urgent (fake) request from someone impersonating the CEO.
4. FedEx Smishing Scam (2020): People received texts claiming to be from FedEx with tracking codes and malicious links. The links led to phishing sites disguised as surveys, requesting credit card details.
5. Twitter Bitcoin Hack (2020): Hackers used vishing to gain internal access to Twitter tools, then hijacked the accounts of Elon Musk, Obama, and others to run a Bitcoin scam.
How to Prevent Phishing Attacks
Prevention starts with awareness and vigilance. Here’s how individuals and organizations can stay safe:
For Individuals
- Think Before You Click: Don’t rush into clicking links or attachments in unsolicited messages.
- Verify Senders: Check email addresses closely. Minor changes (e.g., “[email protected]” with a capital ‘I’ instead of ‘l’) are common tricks.
- Avoid Sharing Sensitive Info: Legit companies don’t ask for personal info via email or SMS.
- Hover Over Links: Preview URLs by hovering to ensure they lead to trusted domains.
- Use MFA (Multi-Factor Authentication): Even if your password is stolen, MFA adds a second layer of protection.
- Keep Software Updated: Ensure your OS, antivirus, and browser are up to date.
- Use Spam Filters: Enable email filtering to block suspicious messages.
- Avoid Password Reuse: Use a password manager and strong, unique passwords for each site.
- Educate Yourself: Take phishing simulation quizzes and stay informed about current scams.
For Businesses
- Train Employees Regularly: Offer cybersecurity awareness training and run simulated phishing tests.
- Enforce Verification Procedures: Require secondary confirmation for sensitive tasks like wire transfers.
- Enable Email Authentication: Implement SPF, DKIM, and DMARC to prevent spoofing.
- Use Advanced Email Security: Employ tools that scan for suspicious links, attachments, and behaviors.
- Update Systems Frequently: Patch vulnerabilities in Software and operating systems.
- Limit Access with Least Privilege: Employees should only access what they need. This limits damage if an account is compromised.
- Segment Networks: Prevent threats from spreading laterally across the organization.
- Backup Data Securely: In the case of ransomware, frequent offline backups can be a lifeline.
- Create a Security Culture: Encourage open reporting of suspicious activity—without fear of punishment.
- Monitor and Alert: Stay aware of trending phishing campaigns and notify staff when new threats arise.
What to Do If You’ve Been Phished
Mistakes happen. Here’s how to respond swiftly:
- Disconnect Immediately: Unplug from the internet and stop any ongoing communication with the attacker.
- Scan Your Device: Run antivirus and anti-malware tools to remove infections.
- Change Passwords: Do this from a secure device, starting with your email and banking accounts.
- Enable MFA: If not already active, set up multi-factor authentication immediately.
- Contact Financial Institutions: If you give financial info, alert your bank or credit card provider to block fraud.
- Notify IT or Security Teams: At work, report incidents to IT quickly to prevent broader damage.
- Report the Attack: Forward phishing emails to [email protected] and report scams to local cybercrime units (e.g., FTC in the U.S.).
- Warn Your Contacts: If your account was hijacked, the attacker may use it to phish your friends or colleagues.
- Monitor Accounts: Keep an eye on your credit reports, bank statements, and email accounts for suspicious activity.
- Learn and Move Forward: Reflect on how the attack happened and take steps to avoid future incidents.
Conclusion
Phishing Attacks are not going away anytime soon. As long as attackers can exploit human emotions like fear, curiosity, and urgency, Phishing will remain a top cybersecurity threat. But by understanding how these attacks work, spotting the warning signs, and applying smart safety habits, you can dramatically reduce your risk.
To recap:
- Stay alert, and don’t trust messages unquestioningly.
- Verify before clicking, sharing, or replying.
- Technology like MFA and antivirus software can be used as safety nets.
- Educate yourself and others—awareness is half the battle.
- Respond quickly if you suspect you’ve been phished.
Whether you’re an individual managing personal accounts or an organization protecting sensitive systems, proactive defense is key. When in doubt, pause, verify, and protect yourself. Phishing may be common, but with the right tools and knowledge, you can avoid taking the bait.
Share this :