Postman Data Leak Exposes 30,000 Workspaces This Could Lead to Massive Hack

Hoplon InfoSec
25 Dec, 2024
Are you aware of Postman Data Leak? In recent years, the widespread adoption of Application Programming Interfaces (APIs) has played a crucial role in driving digital transformation across various industries. However, a concerning trend involves significant data leaks from Postman, a popular cloud-based platform used for API development and testing. An investigation conducted by the TRIAD Team has uncovered the serious nature of this problem, emphasizing the critical vulnerabilities that arise from inadequate management of Postman workspaces.
The Scope of the Issue and the Postman Data Leak
Postman workspaces are collaborative environments where developers and teams share API collections, configurations, and testing data. However, a lack of stringent access controls and improper handling of sensitive information has led to over 30,000 publicly accessible collections exposing API keys, access tokens, refresh tokens, and proprietary user data. These leaks create an open invitation for malicious actors, potentially leading to massive data breaches and unauthorized misuse. TRIAD’s year-long analysis documented numerous instances where sensitive information was inadvertently made public, underscoring the pervasive nature of the problem.
Okta IAM API Leak in the Athletic Industry
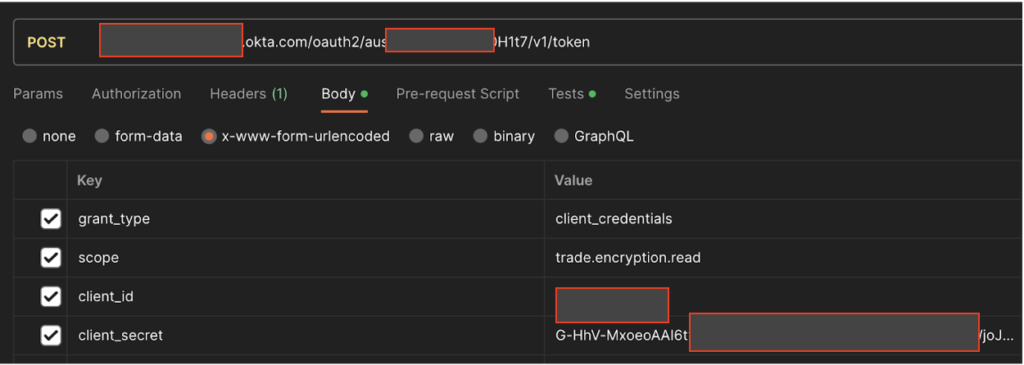
One of the most significant cases involved an Okta IAM API leak within the athletic industry. A major athletic apparel company unknowingly exposed sensitive credentials through a third-party vendor’s Postman workspace. This oversight allowed malicious actors to access sensitive business data, including invoices, shipment details, and trade-related information. Unauthorized access to internal APIs can lead to substantial financial losses and reputational damage, highlighting the importance of robust monitoring systems and controlled access.
Zendesk Admin Credentials Leak in Healthcare
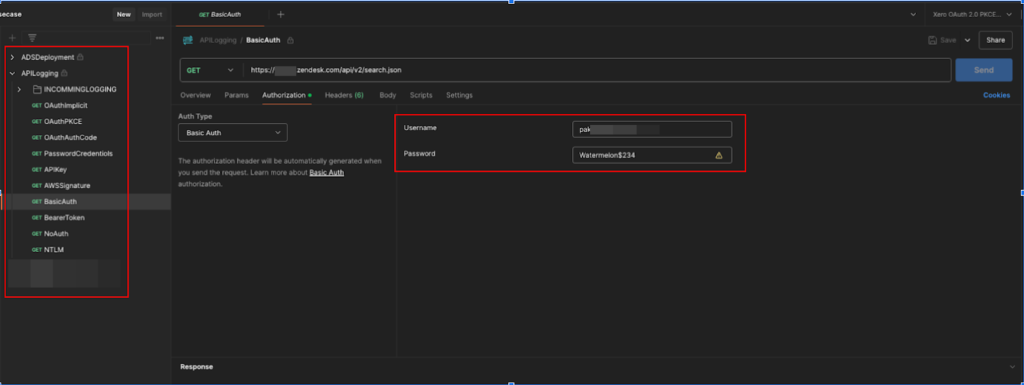
A company inadvertently exposed active Zendesk administrator credentials in the healthcare sector through a shared Postman workspace. This lapse posed a severe risk, as threat actors could manipulate support operations, access patient data, and create phishing schemes. Such incidents jeopardize financial stability and erode the trust of patients and stakeholders, emphasizing the need for strict access controls and regular audits.
Razorpay API Key Exposures
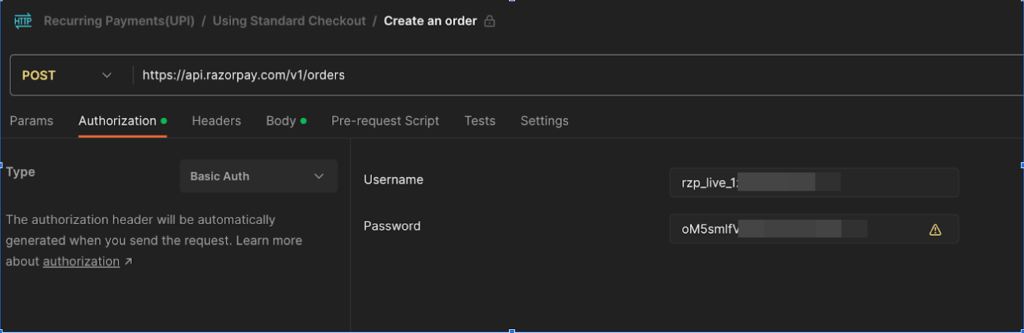
Another alarming case involved Razorpay, a popular payment gateway platform. API keys were exposed in multiple Postman workspaces, leaving payment systems vulnerable to unauthorized transactions and financial fraud. The aftermath of such breaches can be devastating, necessitating significant investments in system overhauls and efforts to rebuild user trust.
CRM Token Leaks
A Postman workspace was found to have exposed a refresh token and session secrets for a CRM platform alongside an endpoint to generate access tokens. This allowed attackers to hijack sessions or directly access sensitive systems. CRM systems often contain customer data and insights, making them a prime target for exploitation.
New Relic API Credentials Exposure
In another instance, a significant software company accidentally exposed New Relic API keys through Postman workspaces. These keys granted potential access to internal logs, microservices, and operational data. Such exposure can reveal proprietary insights, providing attackers a competitive and operational advantage.
Root Causes of the Leaks
The investigation revealed several root causes contributing to these leaks. Developers often share collections containing sensitive data without properly masking credentials. Misconfigured access controls further exacerbated the problem, allowing unauthorized access to workspaces. Additionally, storing sensitive information in plaintext within collections or environment files made such data easily accessible. Long-lived tokens that were not frequently rotated compounded these risks, as their exposure increased the likelihood of misuse. Human error, such as uploading unmasked credentials to public platforms like GitHub, further highlighted the need for better training and awareness among developers.
The Pervasive Nature of the Issue
The TRIAD Team’s research also uncovered large-scale exposure across popular API services. For example, over 5,900 leaked credentials were associated with the GitHub API, while Slack APIs saw over 10,000 combined leaks. Other platforms, including Salesforce, Microsoft, and Razorpay, were similarly affected. These findings underscore the widespread nature of the problem, emphasizing the need for a comprehensive approach to address it.
Preventative Measures
Addressing the issue of API data leaks requires a multi-faceted approach. One critical recommendation is using environment variables to store sensitive information securely, avoiding hardcoding such data within collections. Organizations must also implement stringent access controls, ensuring that collections and environments are shared only with authorized personnel. Regular audits of permissions can help identify and rectify vulnerabilities.
Another essential practice is frequent token rotation. Employing short-lived tokens and automating their rotation can significantly reduce the risk of misuse. Secrets management tools like HashiCorp Vault or AWS Secrets Manager offer secure storage and management solutions for sensitive data. Regular security audits, including monitoring access logs and reviewing shared collections, are indispensable for identifying potential vulnerabilities.
Postman’s Response
In light of these findings, Postman has enhanced its security measures. The platform now includes a secret-protection policy that proactively warns users when sensitive data is detected in public workspaces. This feature guides users toward corrective actions, reinforcing Postman’s commitment to safeguarding user information. However, while these measures represent progress, the ultimate responsibility for API security lies with organizations and developers who use the platform. Cultivating a culture of security awareness and adopting best practices are vital for mitigating risks.
The Broader Implications
The TRIAD Team’s findings highlight the critical importance of API security in today’s interconnected world. APIs are the backbone of modern applications, powering digital ecosystems across industries. Ensuring their protection is essential to protect sensitive data and maintain trust in digital platforms. Organizations must prioritize the secure handling of API credentials, invest in developer training, and adopt advanced tools to safeguard their APIs. By doing so, they can mitigate risks, protect their reputation, and ensure the integrity of their digital operations.
Conclusion
The widespread data leaks from Postman workspaces are a stark reminder of the vulnerabilities inherent in collaborative API development environments. While tools like Postman are invaluable for streamlining API workflows, their misuse can lead to catastrophic consequences. By adopting robust security practices and fostering a culture of awareness, organizations can mitigate the risks associated with API development and ensure the safety of their digital ecosystems.
For More:
Share this :