Protect Against Apache MINA Vulnerability: Prevent Remote Code Attacks

Hoplon InfoSec
26 Dec, 2024
A new critical Apache MINA Vulnerability, CVE-2024-52046, has been discovered in Apache MINA, a widely used networking library. This vulnerability has raised alarm bells across the cybersecurity community, allowing attackers to potentially execute remote code by exploiting insecure deserialization processes.
In this article, we’ll delve into the technical details of the vulnerability, outline the impacted versions, and provide actionable steps to mitigate the risk. By the end of this discussion, you’ll have a comprehensive understanding of the issue and how to safeguard your systems.
What is Apache MINA?
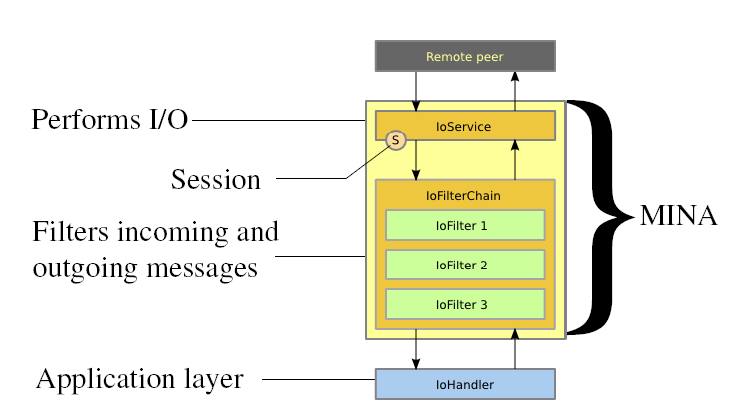
Apache MINA (Multipurpose Infrastructure for Network Applications) is a Java-based networking framework developers use to build high-performance and scalable network applications. At its core, Apache MINA simplifies the development of networked applications by providing an abstract, event-driven API for handling various communication protocols. It enables developers to focus on application logic rather than the complexities of network programming.
Key Features of Apache MINA
- Protocol Flexibility: Apache MINA supports many protocols, including TCP, UDP, and serial communication. Developers can quickly implement custom protocols using the framework.
- Scalability: The framework is designed to handle thousands of concurrent connections efficiently, making it ideal for high-traffic applications.
- Extensibility: Apache MINA’s modular architecture allows developers to integrate additional functionalities and customize behavior.
- Ease of Use: The framework includes utilities like IoFilter and IoHandler, which simplify tasks such as data transformation, logging, and handling I/O events.
Common Use Cases
Due to its versatility, Apache MINA is widely used in various industries and applications:
- File Transfer Protocols (FTP): Many FTP servers use Apache MINA because of its reliable and scalable networking capabilities.
- Real-Time Messaging: Chat applications and messaging systems utilize MINA for low-latency and real-time communication.
- IoT Systems: Devices in the Internet of Things (IoT) ecosystem often use Apache MINA to facilitate data exchange.
- Custom Server Applications: Developers use Apache MINA to build custom servers tailored to business needs.
Apache MINA’s broad adoption underscores its significance in modern networked application development. However, its popularity also makes it a prime target for attackers, emphasizing the need for robust security practices.
The Apache MINA Vulnerability Explained

At the core of this vulnerability lies the ObjectSerializationDecoder component of Apache MINA. This component leverages Java’s native deserialization mechanism to decode serialized data. While deserialization is a standard process in many Java applications, it comes with inherent risks if not handled securely.
How the Exploit Works
The ObjectSerializationDecoder in Apache MINA lacks adequate security checks, enabling attackers to inject malicious serialized data. When this data is deserialized, it can execute arbitrary code on the server, effectively allowing Remote Code Execution (RCE). This type of attack can lead to severe consequences, such as:
- Unauthorized access to sensitive information.
- Compromise of the server’s integrity.
- Introduction of malware or backdoors.
The issue is particularly critical because deserialization vulnerabilities are often challenging to detect, and exploited code can be readily crafted if attackers understand the application’s logic.
Versions Impacted
The vulnerability affects multiple versions of Apache MINA:
- 2.0 through 2.0.26
- 2.1 through 2.1.9
- 2.2 through 2.2.3
Organizations using these versions should take immediate action to mitigate the risk. Fortunately, the Apache MINA Team has already released updates to address the issue:
- 2.0.27
- 2.1.10
- 2.2.4
These updated versions enhance the security of the deserialization process by introducing stricter validation mechanisms for incoming serialized data.
Mitigation Steps
Upgrade to the Latest Versions
The most effective way to mitigate the vulnerability is to upgrade to the patched versions of Apache MINA:
- 2.0.27
- 2.1.10
- 2.2.4
Delaying the upgrade significantly increases the risk of exploitation, especially since the vulnerability details are now public knowledge.
Enforce Secure Deserialization
After upgrading, it’s crucial to configure the ObjectSerializationDecoder only to allow specific classes to be deserialized. Apache MINA has introduced three new methods to facilitate this:
- Accept (ClassNameMatcher classNameMatcher): Allows specifying class name patterns for safe deserialization.
- Accept (Pattern pattern): Enables matching classes against a regular expression.
- Accept (String… patterns): Permits a list of class name patterns.
The decoder will now reject all classes by default unless explicitly allowed. This ensures that even if malicious data is injected, it cannot trigger harmful deserialization.
Assess Application Usage
Conduct an internal review to determine if your application uses the following:
- IoBuffer#getObject() method
- ProtocolCodecFilter with ObjectSerializationCodecFactory
If these features are not in use, the vulnerability may not affect your application. This step can help narrow down the scope of your mitigation efforts.
Additional Insights
Sub-Projects Not Affected
It is worth noting that the following sub-projects under the Apache MINA umbrella are confirmed to be unaffected by this vulnerability:
- Apache FtpServer
- Apache SSHd
- Apache Vysper
Lessons Learned
The discovery of CVE-2024-52046 highlights several critical cybersecurity principles:
- The Risks of Insecure Deserialization: Deserialization vulnerabilities are a recurring issue in Java applications. Developers must prioritize secure coding practices and leverage tools to analyze deserialization risks.
- Regular Updates: Keeping third-party libraries up-to-date is essential. Vulnerabilities often stem from outdated dependencies.
- Proactive Security Policies: Enforcing strict validation rules and implementing defense-in-depth strategies can reduce the impact of unknown vulnerabilities.
Conclusion
The CVE-2024-52046 vulnerability in Apache MINA underscores the importance of proactive security practices. Organizations must swiftly mitigate this risk by upgrading to the latest versions and enforcing secure deserialization policies.
To recap:
- Upgrade immediately to versions 2.0.27, 2.1.10, or 2.2.4.
- Configure the ObjectSerializationDecoder to allow safe class deserialization explicitly.
- Review application usage to determine the scope of the vulnerability.
Organizations can protect their systems from exploitation and maintain a secure environment by taking these steps. Furthermore, regular audits of third-party libraries and adherence to secure coding practices will help mitigate future risks.
Cybersecurity is an ongoing process, and addressing vulnerabilities like CVE-2024-52046 is a critical part of that journey. Stay vigilant and ensure your systems are always protected against emerging threats.
For More:
Share this :