Google Docs Exploit Creates a Bypass for Microsoft 365 Security via G-Door
Hoplon InfoSec
23 Dec, 2024
In today’s digital age, organizations rely heavily on cloud-based productivity suites like Microsoft 365 to ensure seamless operations and robust security. However, a newly discovered vulnerability known as “G-Door” has highlighted critical gaps in these defenses. This flaw allows hackers to bypass Microsoft 365’s security measures by exploiting unmanaged Google Docs accounts, posing a significant threat to businesses worldwide.
The G-Door vulnerability is another technical glitch and a sophisticated exploitation of the interplay between Microsoft 365 and Google’s ecosystem. By creating personal or workspace Google accounts using an organization’s domain name, attackers can evade Microsoft 365’s Conditional Access (CA) policies. This creates opportunities for unauthorized access, data breaches, and persistent threats, making organizations need to understand and address this issue proactively.
The G-Door vulnerability arises from the ability to create Google accounts with corporate email addresses, which operate outside the purview of Microsoft 365 security controls. These accounts enable attackers to circumvent measures like multi-factor authentication (MFA) and geolocation restrictions, making it difficult for administrators to monitor and mitigate potential threats.
What Is the G-Door Vulnerability?
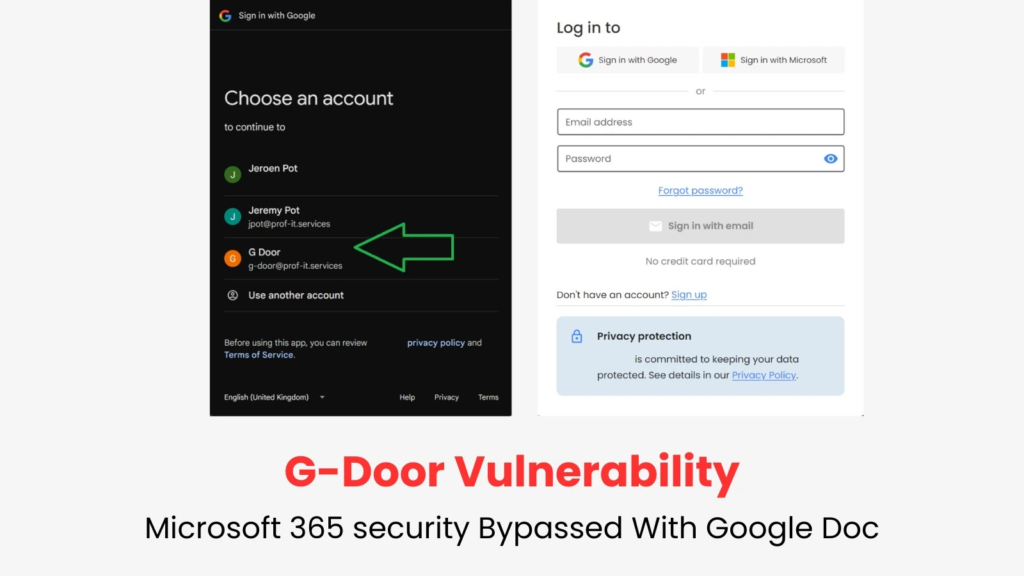
At its core, the G-Door vulnerability exploits the ability to create unmanaged Google accounts with corporate email addresses. These accounts operate outside the control of an organization’s Microsoft 365 environment, rendering key security measures like multi-factor authentication (MFA), device compliance checks, and geolocation restrictions ineffective.
The process is alarmingly simple. An attacker—or even an unwitting Employee—can set up a Google account linked to the organization’s domain without administrative approval. Once established, this unmanaged account can access third-party applications and services, bypassing Microsoft 365’s stringent security controls.
Why Is G-Door a Major Concern?
The rise of cloud-based platforms like Microsoft 365 and Google Workspace has revolutionized how organizations manage their digital environments, making them more efficient and accessible. However, integrating multiple services from different providers has also introduced new security challenges. One such challenge is the G-Door vulnerability, a primary concern for organizations relying on Microsoft 365 for their business operations. G-Door exploits the intersection of Microsoft 365’s security policies and unmanaged Google accounts, presenting significant risks to corporate data and access control.
The vulnerability allows attackers to bypass security measures, such as Conditional Access and Multi-Factor Authentication (MFA), by leveraging unmanaged Google accounts. These accounts are not subject to the same oversight and controls organizations typically enforce within their Microsoft 365 environment. Consequently, organizations that fail to manage these third-party accounts properly leave themselves exposed to potential breaches. This lack of control over Google identities allows attackers to maintain persistent access to sensitive data and systems even after compromising within the primary network.
As the digital landscape becomes increasingly interconnected, the risk posed by G-Door highlights a fundamental gap in cybersecurity practices: the absence of holistic access control and visibility across multiple cloud platforms. With the growth of remote work and external collaboration tools, ensuring security policies extend to all third-party services is paramount. Without this integration, organizations risk data exposure, persistent access by malicious actors, and difficulties responding to potential threats. Let’s dive deeper into the specific risks associated with the G-Door vulnerability.
- Circumventing Conditional Access: Microsoft 365’s Conditional Access policies are designed to enforce security measures like MFA and device compliance. However, unmanaged Google accounts bypass these policies, leaving critical gaps in an organization’s defenses.
One of Microsoft 365’s primary security features is its Conditional Access policies, which enforce critical security measures such as Multi-Factor Authentication (MFA) and device compliance. These policies ensure that only trusted devices and users can access corporate resources. However, unmanaged Google accounts pose a significant risk by bypassing these protections. Since Microsoft 365’s security infrastructure does not manage these accounts, they are not subject to the same stringent security protocols. This allows attackers to circumvent Conditional Access measures, gaining unauthorized access to sensitive organizational data.
- Lack of Visibility: Activities on these unmanaged accounts do not appear in Microsoft 365 Admin Center logs. This lack of visibility makes it challenging for IT administrators to detect and respond to anomalies or potential threats.
Without the ability to track actions taken through unmanaged accounts, organizations face a considerable challenge in detecting and responding to potential attacks. Malicious actors can exploit this lack of visibility to carry out unauthorized activities, steal sensitive data, or maintain persistence within the organization’s systems. The inability to monitor these accounts severely hampers the organization’s ability to implement an effective security response, leaving it vulnerable to long-term threats that go unnoticed until it’s too late.
Data Exposure: Sensitive corporate data stored in Google Drive or created in Google Docs is not protected by the organization’s Data Loss Prevention (DLP) or Azure Information Protection (AIP) policies. This increases the risk of data leaks and non-compliance with regulatory requirements.
Data security is a top priority for any organization, especially when dealing with sensitive or regulated information. Regarding the G-Door vulnerability, Google accounts linked to Microsoft 365 environments often have unrestricted access to critical corporate data. This includes files stored in Google Drive and documents created in Google Docs, which are not covered by the organization’s Data Loss Prevention (DLP) or Azure Information Protection (AIP) policies. As a result, sensitive information may be exposed or shared without the necessary safeguards to prevent unauthorized access or leaks.
- Persistent Access: Even after an organization revokes access to a compromised Microsoft 365 account, attackers can retain access through a separately created Google identity. This persistent access can be used to exploit third-party apps and services.
This persistent access is dangerous because it is often not tied to the same security controls that govern primary Microsoft 365 accounts. As a result, attackers can remain inside an organization’s digital ecosystem for an extended period, gathering intelligence and escalating their attacks. This makes it difficult for IT teams to sever the attacker’s access completely, as the Google account acts as a secondary point of entry, keeping the threat active even after the primary breach is mitigated.
- Inadequate Offboarding: When employees leave the organization, unmanaged Google accounts linked to corporate emails may continue to provide unauthorized access to connected apps and data repositories.
The lack of control over these unmanaged Google accounts means that offboarding procedures are often incomplete, leaving former employees with the ability to access corporate data and systems. If the Google account is compromised or used maliciously, this can lead to data breaches, unauthorized access, and other security incidents. Ensuring that all accounts—regardless of the platform—are properly deactivated during the offboarding process is essential to maintaining strong security and preventing potential threats from lingering long after an Employee has left the organization.
Strengthening Defenses Against the G-Door Vulnerability
The discovery of the G-Door vulnerability has exposed critical gaps in organizations’ security measures using Microsoft 365. This flaw allows attackers to exploit unmanaged Google accounts, bypassing essential controls and posing significant risks to corporate data. To safeguard against these emerging threats, organizations need a comprehensive approach that addresses multiple facets of their security infrastructure.
Proactive measures are the cornerstone of mitigating the risks associated with G-Door. It begins with understanding how attackers leverage unmanaged Google accounts linked to a corporate domain. By exploiting these accounts, they bypass key security protocols like Conditional Access policies, creating unauthorized access points. Organizations must respond with a multi-layered strategy that involves domain verification, continuous monitoring, and user education to close these gaps.
Effective mitigation strategies must address both technical and behavioral aspects of security. The technical side involves auditing unmanaged accounts, implementing enhanced security solutions, and developing a robust incident response plan. On the behavioral front, user awareness campaigns can significantly reduce the likelihood of employees unintentionally creating vulnerabilities. This dual approach ensures that human and technological factors are accounted for in the fight against cyber threats.
The implications of the G-Door vulnerability extend beyond immediate risks. It highlights organizations’ challenges in managing security across interconnected platforms like Microsoft 365 and Google Workspace. As reliance on cloud-based productivity tools grows, addressing such vulnerabilities becomes a technical and business necessity.
A well-rounded defense strategy does more than protect against current threats—it builds resilience for the future. Organizations must remain vigilant, adapt to evolving security landscapes, and continuously refine their approaches to ensure comprehensive protection against vulnerabilities like G-Door.
Domain Verification
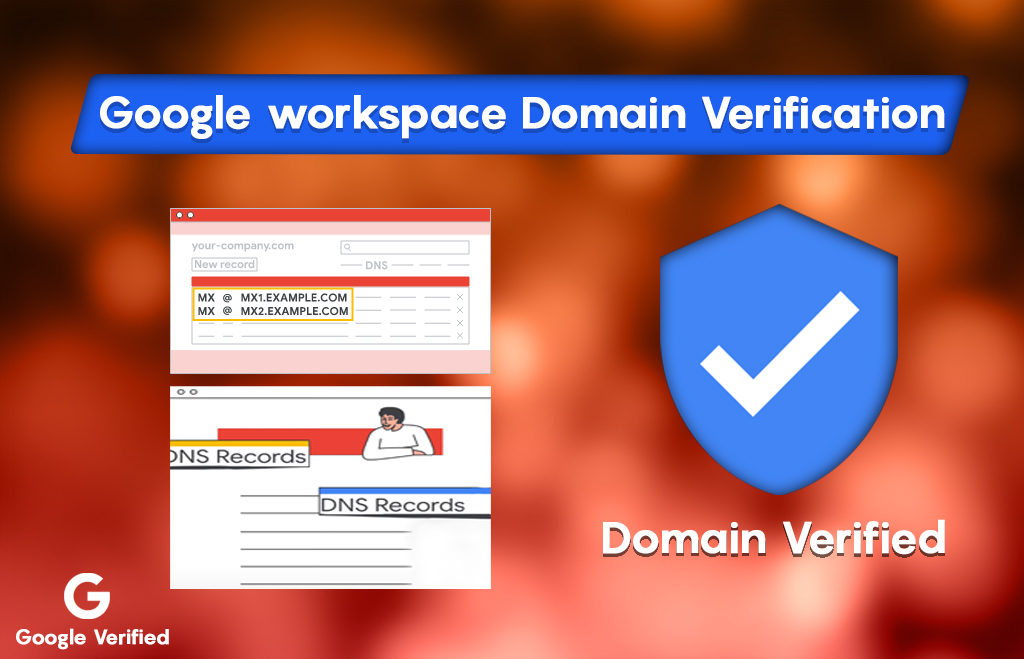
Domain verification is a critical first step in addressing the G-Door vulnerability. By implementing strict verification processes for Google Workspace, organizations can ensure that only authorized users can create accounts linked to their domain. This simple yet effective measure reduces the risk of attackers exploiting unmanaged accounts.
In addition to preventing unauthorized account creation, domain verification strengthens the overall integrity of an organization’s digital environment. It establishes clear boundaries between corporate and personal accounts, making monitoring and managing account activity easier for IT administrators. Organizations prioritizing domain verification can close one of the key entry points exploited by the G-Door vulnerability.
Auditing Unmanaged Accounts
Regularly auditing unmanaged accounts is essential for identifying and addressing potential risks. These audits allow organizations to detect accounts linked to their domain that operate outside the managed environment, providing visibility into unauthorized activity.
Through consistent auditing, organizations can reduce their exposure to threats and take corrective actions before vulnerabilities are exploited. This process also ensures compliance with regulatory requirements and reinforces the organization’s commitment to maintaining a secure operational environment.
User Education
Educating employees about the risks associated with unmanaged accounts is crucial to mitigating the G-Door vulnerability. Many employees unknowingly create vulnerabilities by using work email addresses for personal accounts. Awareness campaigns can help prevent such behaviors and empower employees to make informed decisions about account usage.
Effective user education programs go beyond basic training. They foster a culture of cybersecurity awareness, encouraging employees to take an active role in protecting organizational assets. OrganizationsBy addressing the human factor, organizations can significantly enhance their defenses against vulnerabilities like G-Door.
Enhanced Security Solutions
Implementing advanced security solutions is vital for monitoring and controlling access across cloud platforms. These tools provide visibility into unmanaged accounts and enforce consistent security policies, ensuring that no account operates outside the organization’s control.
Enhanced security solutions also offer capabilities like anomaly detection and automated incident response, further strengthening an organization’s defense against sophisticated threats. Investing in these tools is a proactive step toward building a resilient cybersecurity infrastructure.
Incident Response Planning
A robust incident response plan is indispensable in mitigating the impact of vulnerabilities like G-Door. Such plans provide a clear roadmap for detecting, responding to, and recovering from security incidents, minimizing damage and downtime.
Regularly updating the incident response plan ensures it remains effective against evolving threats. Organizations prioritizing incident response are better equipped to handle challenges, maintain operational continuity and safeguard their reputation in the face of cyberattacks.
For more:
https://cybersecuritynews.com/g-door-bypass-microsoft-365-security/
Share this :