Protect Against New Go-Based Malware Using Telegram C2

Hoplon InfoSec
15 Feb, 2025
Protect Against New Go-Based Malware Using Telegram C2. In today’s evolving cybersecurity landscape, threat actors continuously adapt their techniques to bypass traditional detection methods. One of the most concerning recent developments is the identification of a new backdoor malware written in the Go programming language. This malware is particularly notable because it uses Telegram—a popular cloud-based messaging application—as its command-and-control (C2) channel. Although the malware appears to be in an active development phase, it is fully functional and capable of executing various malicious activities. In this article, we explore the intricacies of this new threat, provide a detailed technical analysis, and discuss the broader implications for cybersecurity defenders.
Overview of the Go-Based Malware
Backdoor malware is a threat that allows unauthorized remote access to infected systems. The malware has been written in Golang, a language known for its efficiency and cross-platform capabilities. Researchers believe the malware could have Russian origins, although attribution remains complex. Despite its under-development status, the backdoor is operational. It includes several implemented commands that enable attackers to carry out various tasks, from executing arbitrary commands to maintaining persistence on the victim’s machine.
The choice of Telegram as a C2 channel is strategic. Unlike traditional C2 infrastructures that rely on dedicated servers or custom protocols, Telegram provides a cloud-based, globally accessible platform that can easily blend in with regular network traffic. By using Telegram’s legitimate API and communication methods, the malware can hide its malicious activities behind a veneer of benign application usage, complicating the efforts of cybersecurity teams.
Technical Analysis of the Go-Based Malware
Code Structure and Self-Installation Mechanism
At its core, the malware is compiled in Go and is designed to operate as a backdoor once executed on a target system. When the malware is launched, it initiates a self-installation process. The process begins by checking whether it runs from a specific file path, namely C:\Windows\Temp\svchost.exe. If it detects that it is not running from this predetermined location, the malware copies itself to this path relaunches the new instance and terminates the original process. This self-installation step is executed through an initialization function that runs before the primary function, ensuring the malware establishes persistence on the infected system.
This technique of relocating the executable is not uncommon in malware development. It serves multiple purposes: it helps to obscure the malware’s original entry point, facilitates persistence across system reboots, and reduces the likelihood of detection by some security tools that monitor standard execution directories.
Leveraging Golang’s Capabilities
Using Golang has several advantages for malware authors. The language is known for its simplicity, concurrency support, and ability to compile standalone binaries that work on multiple operating systems. These features allow the malware to run efficiently and evade many conventional security measures. Golang’s static linking also means that the resulting binary often contains all necessary libraries bundled within, making it harder for defenders to dissect the code and identify external dependencies or suspicious imports.
Interaction with Telegram as a Command-and-Control Channel
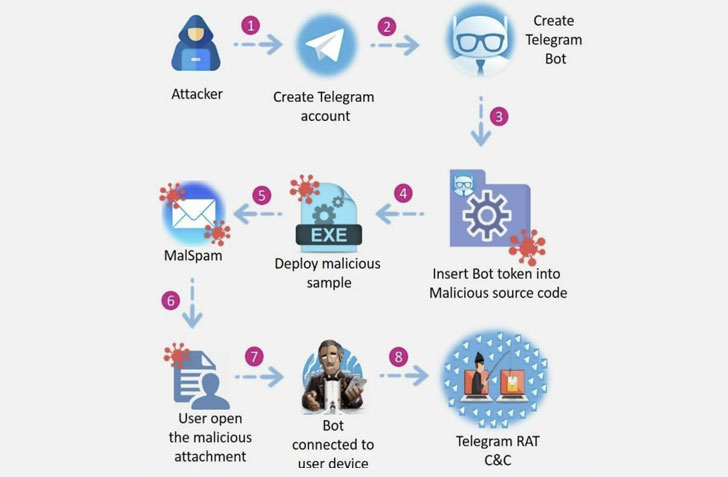
Integration with Telegram’s API
One of the most innovative aspects of this malware is its integration with Telegram for C2 communication. The malware utilizes an open-source Go package to interface with Telegram’s API. It specifically calls the NewBotAPIWithClient function to create a bot instance. This bot is authenticated using a token generated via Telegram’s BotFather, a tool that simplifies bot creation for developers. For instance, one analyzed a sample of the malware that included the token 8069094157:AAEyzkW_3R3C-tshfLwgdTYHEluwBxQnBuk, which serves as a unique identifier for the bot instance.
Once authenticated, the malware uses the GetUpdatesChan function to continuously poll a Telegram channel for incoming commands from its operators. This channel acts as the primary conduit for instructions, ensuring the attacker can relay commands to the compromised system anytime.
Advantages of Using Telegram
Choosing Telegram as a C2 channel offers several benefits to threat actors. Firstly, Telegram’s infrastructure is designed to support high volumes of legitimate traffic, meaning regular activity can easily mask malicious communications. Secondly, since Telegram is widely used worldwide, differentiating between benign and malicious traffic becomes a significant challenge for security teams. Finally, Telegram’s API and client libraries are openly available, simplifying the implementation process for developers—even those with limited coding experience.
By leveraging Telegram, attackers can make their operations less conspicuous and more resilient to takedown attempts. This approach is a stark reminder of how legitimate cloud-based applications can be repurposed for nefarious activities.
Command Set and Functional Functionalities
The backdoor malware supports commands that allow remote operators to control and manipulate the infected system. Although the malware is still being developed, three primary commands are fully implemented, and one is partially functional. Below is a detailed explanation of these commands:
1. Executing PowerShell Commands (/cmd)
The /cmd command enables the attacker to execute arbitrary PowerShell commands on the target machine. When this command is received via the Telegram channel, the malware prompts the Russian operator to input a specific PowerShell command. The malware then runs the command in a hidden mode, capturing the output and sending it back through the same encrypted Telegram channel. This functionality can be particularly dangerous, providing attackers with a powerful tool to manipulate the system, gather sensitive data, or install additional malicious components.
2. Establishing Persistence (/persist)
The /persist command ensures the malware remains active on the infected system. When triggered, the command causes the malware to re-launch itself from the specified directory (C:\Windows\Temp\svchost.exe). This relaunch mechanism maintains the malware’s presence even if the initial process is terminated and helps it avoid detection by consistently running from a less suspicious file path. Persistence mechanisms like this are common in advanced malware, making remediation and removal more difficult.
3. Screenshot Capture (/screenshot)
While not fully implemented, the /screenshot command is intended to capture a screenshot of the victim’s desktop. When this command is issued, the malware sends a placeholder message back via Telegram, indicating that a screenshot was “captured.” The eventual goal of this command is likely to allow attackers to visually monitor the target system, thereby gaining insights into user behavior, active applications, or other sensitive information. Although the implementation is rudimentary, further development could expand this functionality to include full-screen capture and real-time monitoring.
4. Self-Destruct Mechanism (/selfdestruct)
The /self-destruct command allows the attacker to delete the malware from the system and terminate its process. This command is particularly insidious, as it allows the malware to remove traces of its existence when the operator deems it necessary. The self-destruction capability is an effective countermeasure against forensic analysis and incident response, ensuring that evidence of the compromise is minimized or entirely eradicated.
Challenges for Cybersecurity Defenders

Integrating cloud-based applications like Telegram as C2 channels significantly complicates detection and mitigation efforts for cybersecurity professionals. Traditional network monitoring tools often rely on identifying anomalous behavior or traffic patterns that deviate from normal usage. However, when an attacker uses a widely adopted platform like Telegram, the malicious communications can easily blend in with legitimate traffic.
Stealth Through Legitimate Infrastructure
One of the primary challenges this malware poses is its ability to leverage legitimate infrastructure. Many organizations allow traffic to and from cloud applications such as Telegram, OneDrive, GitHub, and Dropbox. This leniency means that security systems must distinguish between benign API calls and malicious activity—an increasingly complex task. The use of Telegram’s API, for example, not only facilitates remote control but also masks the malware’s C2 communications behind encrypted, standardized requests that resemble normal usage.
Obfuscation and Evasion Techniques
Beyond using legitimate platforms, the malware also employs several techniques to obfuscate its presence on the system. The self-installation mechanism that copies the executable to a less-monitored directory, combined with encrypted communications, significantly reduces the likelihood of detection by traditional endpoint security solutions. This dual approach of obfuscation and evasion is a hallmark of modern malware, continually adapting to outpace defensive technologies.
The Broader Threat Landscape
The discovery of this Go-based backdoor malware is a stark reminder that attackers continually seek new ways to exploit existing technologies. Cloud services for C2 communications are not limited to Telegram; other popular platforms such as OneDrive, GitHub, and Dropbox could be similarly exploited. This trend signals a broader shift in the threat landscape, where the lines between legitimate and malicious activity are becoming increasingly blurred. As such, organizations must remain vigilant and adopt a multi-layered approach to cybersecurity that can adapt to these evolving threats.
Defensive Measures and Detection Strategies
In response to the growing threat posed by advanced malware such as this Go-based backdoor, cybersecurity vendors and organizations must update their detection and response strategies. One notable example is Netskope Advanced Threat Protection, which has proactively identified and flagged this threat under the identifier “Trojan.Generic.37477095.”
Leveraging Threat Intelligence
Organizations should leverage threat intelligence feeds and platforms to stay informed about emerging threats. The detailed technical indicators, including indicators of compromise (IOCs), provided by threat researchers and vendors like Netskope, are invaluable for updating security rules and detection signatures. Regularly reviewing these feeds can help security teams identify unusual patterns or connections associated with known malicious activity.
Network Segmentation and Monitoring
Given the stealthy nature of this malware, organizations should consider implementing network segmentation and enhanced monitoring of outbound traffic. Segmentation limits the lateral movement of malware within an organization, while advanced monitoring solutions can detect unusual communications—even those that appear legitimate. For example, unusual patterns in Telegram traffic or unexpected API calls may indicate the presence of a compromised system.
Endpoint Detection and Response (EDR)
Another critical strategy is deploying robust Endpoint Detection and Response (EDR) solutions. EDR tools can monitor system behavior in real-time, flagging anomalies such as unexpected file relocations, process injections, or unauthorized executions of PowerShell commands. Security teams can quickly identify and remediate compromised endpoints by correlating these events with known malicious indicators.
Employee Training and Awareness
While technical measures are essential, human factors play a significant role in the overall cybersecurity posture. Regular training and awareness programs can help employees recognize signs of compromise or suspicious activity. Educating staff about the risks of using unauthorized or unmonitored cloud applications can reduce the attack surface.
Incident Response Planning
Finally, organizations should ensure that their incident response plans are up-to-date and include specific procedures for dealing with backdoor malware. Rapid response is critical; knowing how to isolate affected systems, analyze the malicious code, and remediate the compromise can distinguish between a minor incident and a major security breach. Collaboration with threat intelligence providers and cybersecurity experts can also help refine these plans and improve overall resilience.
Future Implications and Evolving Threat Landscape
The emergence of this Go-based backdoor malware underscores a significant shift in the methods used by threat actors. Cloud-based platforms for C2 communication will likely become more prevalent as attackers seek to exploit the trusted infrastructures already in place across most organizations. This evolution poses several long-term challenges:
- Increased Complexity of Detection: As attackers blend malicious traffic with legitimate communications, traditional detection methods based solely on traffic analysis may no longer be sufficient. Security teams must adopt more sophisticated analytical tools and machine learning techniques to differentiate between normal and abnormal patterns.
- Rapid Evolution of Malware: The ongoing development of this malware indicates that threat actors are continuously refining their tools. Future iterations may introduce additional commands, enhanced obfuscation techniques, and more robust persistence mechanisms. This rapid evolution necessitates continuous monitoring and agile defensive strategies.
- Broader Use of Cloud Infrastructure: Exploiting platforms like Telegram, OneDrive, and GitHub for C2 communications demonstrates that no cloud service is immune to abuse. As organizations increasingly rely on cloud-based applications for daily operations, ensuring the security of these services will become a critical component of overall cybersecurity strategy.
- International and Legal Challenges: The potential attribution to a specific nation-state, such as Russia, adds complexity to international cybersecurity efforts. Legal frameworks and international cooperation will mitigate the threat and hold responsible parties accountable.
Additional Technical Details and Resources
Several resources are available for cybersecurity professionals seeking to dive deeper into the technical aspects of this malware. Netskope Threat Labs has provided detailed indicators of compromise (IOCs) and further technical documentation. These resources are accessible through their GitHub repository, which contains valuable insights into the malware’s architecture, command structure, and communication protocols.
How to Use These Resources
- Threat Intelligence Integration: Incorporate the IOCs and technical details into your security information and event management (SIEM) systems. This integration can help automate detection and trigger alerts when suspicious activity is observed.
- Forensic Analysis: Use the provided technical documentation to conduct forensic analysis on suspected compromised systems. Understanding the self-installation mechanisms and command structure can help identify the presence of the malware.
- Collaborative Research: Share findings and insights with the cybersecurity community. Collaboration can lead to developing more effective countermeasures and improving overall threat intelligence.
Conclusion
The discovery of this new Go-based backdoor malware highlights the ever-changing nature of cybersecurity threats. By leveraging Telegram as a command-and-control channel, attackers are not only simplifying their operational framework. Still, they are also significantly complicating the efforts of security professionals tasked with defending against such threats. Using legitimate, widely adopted cloud applications for malicious purposes represents a significant evolution in deploying and managing backdoor malware.
This means that traditional security measures may no longer be sufficient for organizations. A multi-layered approach that includes threat intelligence, network segmentation, EDR solutions, and regular employee training is essential to counteract these advanced techniques. Moreover, staying informed about emerging threats and participating in collaborative cybersecurity research will be key to maintaining robust defenses.
In an era where malware can hide behind the façade of trusted applications like Telegram, proactive monitoring, and agile incident response strategies have never been more critical. As attackers continue to innovate, so too must our defenses evolve. The insights researchers and vendors such as Netskope provide are invaluable tools in this ongoing battle. Cybersecurity teams must remain vigilant, continuously update their knowledge bases, and adapt strategies to counter these sophisticated threats.
By understanding the mechanisms behind this malware—from its self-installation and persistence techniques to its use of Telegram for covert communications—organizations can better prepare themselves to detect, analyze, and mitigate such intrusions. The lessons learned from this case study are a powerful reminder of the importance of proactive cybersecurity measures in an increasingly connected and complex digital world.
For more:
https://cybersecuritynews.com/new-go-based-malware-exploits-telegram-and-use-it-as-c2-channel/
Share this :