Hackers Earn $382K Exploiting 16 0-Days at Pwn2Own Automotive 2025

Hoplon InfoSec
22 Jan, 2025
The much-anticipated Pwn2Own Automotive 2025 commenced at Tokyo Big Sight, bringing together the world’s most skilled white-hat hackers to showcase the forefront of automotive cybersecurity research. As modern vehicles become increasingly software-driven, events like Pwn2Own are essential for identifying vulnerabilities in automotive systems, ensuring safer and more secure technologies for the future.
The opening day of this renowned event was a testament to the sophistication and dedication of cybersecurity researchers. Participants uncovered and exploited 16 previously unknown vulnerabilities across a variety of systems, including in-vehicle infotainment (IVI) systems, electric vehicle (EV) chargers, and operating systems (OS). Their collective efforts resulted in a prize pool of $382,750, awarded for creativity and technical prowess.
The Significance of Pwn2Own in Automotive Cybersecurity
Pwn2Own is more than just a competition; it is a vital platform for stress-testing modern automotive technologies. Vehicles become increasingly vulnerable to cyber threats as they become more intelligent and connected. By incentivizing researchers to uncover and responsibly disclose vulnerabilities, Pwn2Own fosters collaboration between manufacturers and security experts. This proactive approach to cybersecurity ensures that flaws are addressed before malicious actors can exploit them.
Key Highlights from Day 1
The first day of Pwn2Own Automotive 2025 set the stage for intense competition and groundbreaking discoveries. Researchers demonstrated innovative techniques, tackling various automotive technologies. Here are the significant achievements:
1. PCAutomotive: Stack-Based Buffer Overflow on Alpine IVI System
The team from PCAutomotive successfully exploited a stack-based buffer overflow on the Alpine IVI system, earning them $20,000 and two Master of Pwn points. Their exploit highlighted vulnerabilities in infotainment systems, central to the driver’s interaction with the vehicle.
2. Viettel Cyber Security: OS Command Injection on Kenwood IVI System
Another significant achievement came from Viettel Cyber Security, which leveraged an OS command injection bug to exploit the Kenwood IVI system. Their efforts were rewarded with $20,000 and two points, showcasing the importance of securing command interfaces in automotive systems.
3. Cong Thanh and Nam Dung: Integer Overflow on Sony XAV-AX8500 IVI
Researchers Cong Thanh and Nam Dung from ANHTUD discovered an integer overflow vulnerability in the Sony XAV-AX8500 IVI system. This vulnerability allowed them to gain code execution, earning them $20,000 and two points.
Pioneering Exploits in EV Chargers
EV chargers are an increasingly important part of the automotive ecosystem, and researchers have creatively demonstrated their vulnerabilities.
1. Sina Kheirkhah: Three-Bug Combo on Phoenix Contact CHARX SEC-3150
Sina Kheirkhah, representing the Summoning Team, combined three separate bugs to exploit the Phoenix Contact CHARX SEC-3150 EV charger. Although one of these bugs had been previously disclosed, his innovative approach earned him $41,750 and 4.25 points.
2. Synacktiv: Combined Exploit on ChargePoint Charger
The team from Synacktiv utilized a stack-based buffer overflow in conjunction with a known Open Charge Point Protocol (OCPP) bug. This exploit allowed them to manipulate signals on the ChargePoint charger, netting $47,500 and 4.75 points.
3. PHP Hooligans: Heap-Based Buffer Overflow on Autel Charger
The day’s standout performance came from PHP Hooligans, who uncovered a heap-based buffer overflow on the Autel charger. This remarkable exploit earned them the day’s highest prize of $50,000 and five Master of Pwn points.
4. Ubiquiti Charger Exploit
Later, Sina Kheirkhah returned with another success, exploiting a hard-coded cryptographic key vulnerability in a Ubiquiti charger. His efforts secured an additional $50,000 and five points, further solidifying his position as a top contender.
Bug Collisions: A Recurring Theme
A unique aspect of Pwn2Own is the phenomenon of bug collisions, where multiple teams independently target the same vulnerability. While collisions can reduce the awarded prize, they also highlight the importance of promptly fixing widely known flaws.
1. SK Shieldus: OS Command Injection on Alpine IVI
SK Shieldus encountered a collision while exploiting an unpatched OS command injection bug in the Alpine IVI system. Despite the overlap with last year’s contest, they earned $5,000 and one point.
2. Bongeun Koo: Similar Exploit on Alpine IVI
Bongeun Koo from STEALIEN faced a similar situation, targeting the Alpine IVI system. Although his exploit was successful, the collision limited his winnings to $5,000.
These examples underscore the need for manufacturers to address known vulnerabilities more effectively, as repeated exploitation highlights persistent risks.
Challenges and Failures
While the day was filled with remarkable successes, not every attempt met its mark. For example:
- Riccardo Mori of Quarkslab faced challenges exploiting specific targets and could not secure points.
- Sina Kheirkhah, despite his successes, also encountered failures on particular attempts.
These experiences demonstrate the complexity of automotive cybersecurity, where even the most skilled researchers face obstacles.
The Leaderboard: Day 1 Standings
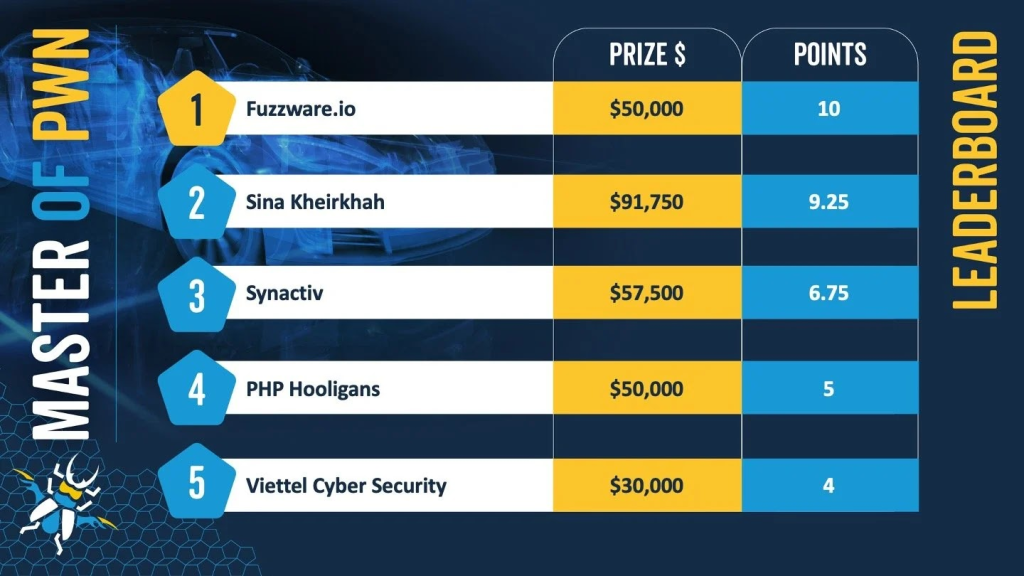
The competition’s leaderboard at the end of Day 1 reflected the intense efforts of the participants:
- fuzzware.io emerged as the leader in the Master of Pwn race, thanks to multiple successful exploits, including their innovative approach to the Autel MaxiCharger.
- Sina Kheirkhah secured a close second place, amassing $91,750 in winnings and 9.25 points through his persistent and creative efforts.
The Road Ahead: What to Expect
Pwn2Own Automotive 2025 will continue until January 24, providing researchers with more opportunities to uncover vulnerabilities. Targets for the upcoming days include additional IVI systems, EV chargers, and other critical components of modern vehicles.
The event’s focus on software-defined vehicles highlights the growing complexity of automotive cybersecurity. As cars integrate advanced features like autonomous driving, over-the-air updates, and connected services, ensuring their resilience against cyber threats becomes paramount.
Why Pwn2Own Matters
The findings from Pwn2Own Automotive 2025 emphasize the urgent need for manufacturers to prioritize cybersecurity. Vulnerabilities in automotive systems can have far-reaching consequences, from compromising driver safety to exposing sensitive data. The industry can avoid potential threats by partnering with ethical hackers and hosting events like Pwn2Own.
Final Thoughts
Day 1 of Pwn2Own Automotive 2025 was a resounding success, showcasing the expertise and ingenuity of the world’s top cybersecurity researchers. With 16 vulnerabilities uncovered and over $382,000 in prizes awarded, the event set a high standard for the days ahead. As the competition continues, the discoveries made here will play a crucial role in shaping the future of automotive cybersecurity, making our vehicles safer and more secure for everyone.
For more:
https://cybersecuritynews.com/hackers-exploited-multiple-0-days/
Share this :