Ransomware Delivered Through Microsoft Teams Voice Calls

Hoplon InfoSec
22 Jan, 2025
Sophos Managed Detection and Response (MDR) has recently uncovered two sophisticated ransomware campaigns targeting organizations via Microsoft Teams. These campaigns, operated by threat actors identified as STAC5143 and STAC5777, exploit a default configuration in Microsoft Teams that allows external users to initiate chats or meetings with internal users, exposing organizations to security vulnerabilities.
This article delves into the attack methodologies, specific campaigns, and actionable measures organizations can implement to safeguard their systems.
Exploiting Microsoft Teams Configuration
Microsoft Teams is a widely used collaboration platform in the corporate world. Its default settings, however, permit external users to communicate with internal teams, creating a potential entry point for cybercriminals. By taking advantage of this default configuration, the threat actors bypass traditional security measures and directly engage with unsuspecting employees, setting the stage for more extensive attacks.
Attack Methodology
The ransomware campaigns uncovered by Sophos employ a multi-step strategy to compromise their targets. These tactics are designed to maximize effectiveness while minimizing detection:
- Email Bombing: Victims are inundated with a flood of spam emails—up to 3,000 in under an hour—to distract and overwhelm them.
- Social Engineering: Attackers pose as IT support personnel and initiate calls via Microsoft Teams, gaining the victim’s trust.
- Remote Access Tools: Threat actors convince victims to install Microsoft Quick Assist or use Teams’ built-in remote control features.
- Malware Deployment: Once remote access is established, attackers deploy malicious payloads to further their objectives.
The STAC5143 Campaign
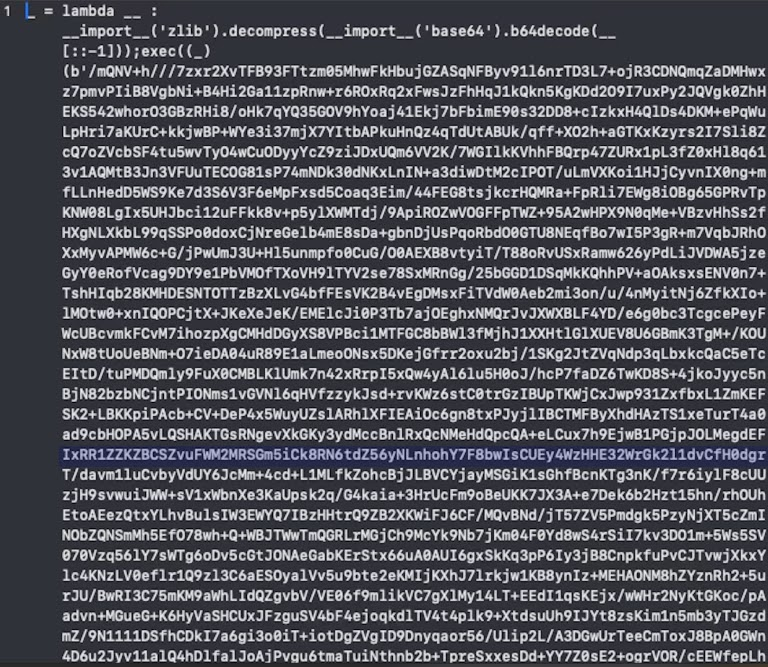
The STAC5143 campaign is a highly advanced cyber operation, employing various tools and techniques to compromise target systems. Its key features include:
Tools and Techniques
- Java Archive (JAR) Files and Python Backdoors: These are used to establish an initial foothold on the victim’s machine.
- RPivot Deployment: An obfuscated version of RPivot, a reverse SOCKS proxy tool, enables attackers to maintain stealthy access to the compromised network.
- Code Obfuscation: Utilizing a lambda function for code obfuscation, STAC5143 mimics methods used by the notorious FIN7 cybercrime group.
- C2 Communication: Connections to command-and-control (C2) servers are established over port 80, blending with normal HTTP traffic to evade detection.
Objectives and Impact
The campaign’s ultimate goal is to infiltrate corporate systems, establish persistence, and exfiltrate sensitive data, all while remaining undetected by standard security measures.
The STAC5777 Campaign
The STAC5777 campaign employs a combination of legitimate software and malicious components to penetrate and persist within target systems. Key aspects of this campaign include:
Malware Techniques
- Malicious DLL Loading: A malicious DLL named
winhttp.dllis side-loaded by the legitimate Microsoft executableOneDriveStandaloneUpdater.exe. - C2 Connections: Unsigned OpenSSL toolkit drivers are used for establishing secure communication with C2 servers.
Persistence Mechanisms
- Registry Modifications: The attackers add entries under “HKLM\SOFTWARE\TitanPlus” to specify C2 server addresses.
- Service Creation: A service and a
.lnkfile are created to ensure continued operation on the compromised system. - Lateral Movement: SMB scanning is conducted to propagate across the network.
Objectives and Impact
The STAC5777 campaign is designed for extensive network infiltration, data exfiltration, and system compromise. Notably, it attempts to disable security measures, such as Multi-Factor Authentication (MFA) solutions, to facilitate further exploitation.
In one instance, the campaign attempted to deploy Black Basta ransomware. However, this was successfully blocked by Sophos endpoint protection.
Capabilities of the Malware

The malware employed in these campaigns exhibits a wide range of capabilities, including:
- Collecting system and OS details
- Gathering user credentials
- Logging keystrokes via Windows API functions
- Conducting network discovery and lateral movement
- Exfiltrating sensitive data
Restricting External Communication in Microsoft Teams
Organizations should revisit Microsoft Teams’ default settings to prevent external entities from initiating calls or chats. This reduces the attack surface and minimizes the risk of social engineering attempts.
Limiting the Use of Remote Access Tools
Remote access tools such as Microsoft Quick Assist should be restricted to authorized personnel only. Application control settings can help prevent unauthorized execution of these tools.
Implementing Robust Endpoint Protection
Sophos has deployed detections for the malware used in these campaigns, including:
- ATK/RPivot-B
- Python/Kryptic.IV
- Troj/Loader-DV
Endpoint protection solutions should be updated regularly to detect and mitigate these threats effectively.
Leveraging Microsoft Office 365 Integration
Integrating security monitoring solutions with Microsoft Office 365 can provide enhanced visibility and protection against potential threats. This includes monitoring for suspicious activities and implementing automated responses.
Strengthening Multi-Factor Authentication
Although the STAC5777 campaign attempts to disable MFA, its implementation remains a crucial layer of defense. Organizations should use advanced MFA solutions that are resistant to tampering.
Educating Employees
Employee awareness is critical in defending against social engineering attacks. Regular training sessions should educate employees on recognizing phishing attempts, verifying IT support requests, and reporting suspicious activities.
Conclusion
The STAC5143 and STAC5777 ransomware campaigns highlight the evolving tactics employed by cybercriminals to exploit popular collaboration platforms like Microsoft Teams. By understanding these threats and implementing robust security measures, organizations can significantly reduce their risk of falling victim to such attacks.
Proactive measures—including restricting external communication, limiting remote access tools, and strengthening endpoint protection—are essential for safeguarding corporate networks. Additionally, fostering a culture of cybersecurity awareness among employees can serve as a vital line of defense against sophisticated cyber threats.
For more:
https://cybersecuritynews.com/threat-actors-delivering-ransomware-via-microsoft-teams/
Share this :