The Rise of Scattered Spider : The Airline Cyberattack Wave of June 2025

Hoplon InfoSec
30 Jun, 2025
A New Era of Aviation Cyber Risk
In the final week of June 2025, one of the most feared names in the cybercrime world Scattered Spider resurfaced in the headlines after launching coordinated attacks against multiple North American airlines. Known for their bold tactics and high-profile victims, this group has once again demonstrated that even the most regulated and security-conscious industries remain vulnerable to social engineering and identity compromise.
The targets this time include Hawaiian Airlines, WestJet, and several third-party vendors supporting aviation infrastructure. These attacks have prompted urgent advisories from U.S. and Canadian cybersecurity agencies and raised alarms about the growing sophistication of cybercriminal groups operating on Western soil.
Timeline of the Breach
A Coordinated and Escalating Attack
Initial signs of disruption emerged between June 25 and June 27, when Hawaiian Airlines identified irregular activity within its internal systems. Around the same time, WestJet’s IT team discovered potential identity impersonation attempts originating from support channels. The anomalies were not isolated. Within days, similar breaches and compromise reports surfaced from adjacent vendors and technology service providers within the aviation supply chain.
By June 28, public confirmation arrived via statements from both private threat intelligence firms and U.S. federal agencies. The culprit was identified as Scattered Spider, a group already notorious for breaching MGM Resorts and other high-value enterprises in previous years.
Unlike opportunistic ransomware attacks, this was a highly targeted and planned campaign. It exploited weaknesses in identity management systems, help desk protocols, and vendor trust relationships, all while avoiding detection in its early stages.
Methods of Attack

Social Engineering at Its Sharpest
Scattered Spider relies less on malware and more on manipulating human behavior. The attack begins with thorough reconnaissance, using public data from LinkedIn, company websites, and past breaches to build profiles of employees. The group then impersonates legitimate users, often calling help desks or IT support to request urgent password resets or multifactor authentication (MFA) bypasses.
This approach leverages the inherent trust within support teams, who are trained to solve problems efficiently but may lack security training. Once access is gained, the attackers escalate privileges, create persistence mechanisms, and begin lateral movement across cloud platforms such as Microsoft Entra ID (Azure AD), Citrix, and Okta.
What makes Scattered Spider unique is their ability to blend in with normal administrative activity. Their understanding of enterprise cloud environments allows them to mimic legitimate behavior, evading both automated and manual detection.
Impact on Airlines and Infrastructure

Disruption Without Detonation
Although no flights were canceled as a result of these intrusions, internal disruptions were significant. Hawaiian Airlines experienced temporary outages in administrative platforms and staff scheduling systems. WestJet initiated a full audit of its internal access logs and third-party connections, suggesting a potentially broader reach.
The deeper concern is what data and access levels may have been compromised. Scattered Spider often exfiltrates sensitive information without encrypting systems, allowing operations to continue while creating long-term security liabilities. In the airline industry, access to flight logs, passenger manifests, crew schedules, and internal communications can represent both a business and national security risk.
Another troubling factor is the role of third-party vendors. These service providers often have privileged access across multiple airline clients, creating a single point of failure. If Scattered Spider penetrated a vendor serving multiple companies, the full scope of compromise may not yet be known.
Why This Campaign Stands Out

High Stakes, High Visibility
There are several reasons why this wave of attacks is currently dominating the cybersecurity conversation.
First, the timing of the attacks is critical. They coincided with peak summer travel in North America, increasing the potential for passenger inconvenience, revenue loss, and reputational damage. Even minor delays in IT systems during this period could ripple into major logistical headaches.
Second, Scattered Spider’s reputation magnifies the threat. Unlike many ransomware crews, this group is based largely in English-speaking countries, possibly including the U.S., U.K., and Canada. Their operations are faster, more precise, and tailored to each target. Law enforcement faces additional hurdles because the attackers may reside within jurisdictions that typically cooperate on cybercrime, making legal action more complex.
Finally, the campaign reflects a strategic evolution in cyber threats. Instead of relying on brute-force ransomware, attackers now favor stealth, persistence, and identity compromise. This increases their ability to infiltrate critical infrastructure without causing immediate alarms.
Threat Actor Profile

Rise of Scattered Spider
Scattered Spider, also tracked by Mandiant and CrowdStrike under names like UNC3944 and Muddled Libra, is a cybercriminal syndicate known for leveraging advanced social engineering and identity abuse. Emerging in 2022, the group initially focused on SMS phishing (smishing) campaigns targeting enterprise users. They quickly evolved to include MFA fatigue attacks, SIM swapping, and help desk impersonation.
Most group members are believed to be young, fluent in English, and highly active on online forums such as Telegram and Discord. Their operations are agile and decentralized, and they frequently shift between tools and techniques to avoid detection.
They’ve previously collaborated with ransomware outfits like BlackCat/ALPHV, and some of their attacks have ended with encryption and extortion. However, their primary strength lies in access operations, getting in, staying hidden, and collecting data that can be monetized in various ways.
Airline Response and Industry-Wide Recommendations
Containment, Recovery, and Reinforcement
Both Hawaiian Airlines and WestJet responded quickly to the incidents. Hawaiian isolated the affected systems and called in external cybersecurity consultants to conduct forensic analysis. WestJet has remained publicly tight-lipped, but insiders confirm that full reviews of authentication systems and access logs are underway.
The broader aviation industry is also on alert. Companies are being urged to:
- Implement stricter help desk verification protocols, including callbacks and out-of-band confirmations.
- Limit administrative privileges and segment internal systems to reduce lateral movement.
- Adopt adaptive authentication mechanisms that respond dynamically to risk levels.
- Conduct regular phishing simulations and social engineering awareness training for all support teams.
Security professionals agree that MFA, while necessary, is no longer sufficient. Organizations must go further by layering behavioral analytics and identity risk scoring on top of basic login checks.
Comparing Past and Present Attacks
How This Campaign Builds on Prior Incidents
Scattered Spider’s airline campaign reflects both an evolution in technique and an expansion in target scope. To illustrate, we compare this attack with two previous high-profile campaigns:
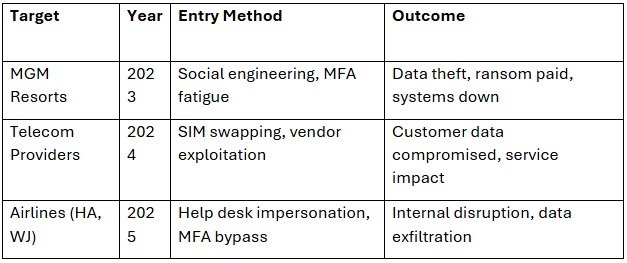
While the core tactics remain consistent, manipulating identity systems, the targets have shifted from service-based businesses to critical infrastructure, signaling a bold new phase for the group.
Broader Implications for National Security

Critical Infrastructure Is the New Frontline
The implications of these attacks extend beyond airlines. They underscore how identity-based attacks can scale across industries. As sectors like healthcare, logistics, and energy move to cloud environments and outsource IT support, the potential for similar breaches increases.
What makes this shift dangerous is that attacks may not be discovered for weeks or months. In the case of Scattered Spider, simply gaining long-term access can provide value, whether for financial fraud, espionage, or future ransomware deployment.
Governments are beginning to respond. CISA and FBI advisories have urged organizations to implement stronger identity controls, conduct audits of vendor access, and prepare for insider threat scenarios. However, these efforts will take time, and attackers are not waiting.
Conclusion
A Warning from the Skies
The June 2025 airline breaches orchestrated by Scattered Spider are more than a headline; they are a clear signal that critical infrastructure is under active threat, not just from foreign nation-states but from highly motivated criminal actors within our borders.
These events highlight the limits of traditional cybersecurity controls. Passwords, MFA, and VPNs are no match for attackers who can socially engineer their way into support channels. The most effective defenses today blend technical solutions with strong operational procedures and human awareness.
As airlines, regulators, and vendors rush to harden their environments, other industries would be wise to take note. This is not an isolated event but part of a pattern, one where attackers no longer break in through the back door but walk in through the front using a borrowed identity.
The challenge ahead is not just about securing networks but rebuilding trust in identity, access, and human judgment before the next Scattered Spider campaign takes flight.
Share this :