Protect Against Rootkit Malware Exploiting Linux 0-Day Flaws

Hoplon InfoSec
14 Jan, 2025
In a recent breakthrough, Fortinet researchers uncovered an advanced rootkit malware that exploits multiple zero-day vulnerabilities in enterprise appliances. This sophisticated malware operates by executing a shell script (Install.sh), enabling attackers to establish persistence, hijack network traffic, and remotely control compromised Linux-based systems. By leveraging kernel modules and user-space processes, the attackers gained comprehensive system control, highlighting the critical need for robust cybersecurity measures.
This blog delves into the intricacies of the attack, the techniques employed by the malware, and the recommended strategies to mitigate such threats.
Understanding the Rootkit Malware

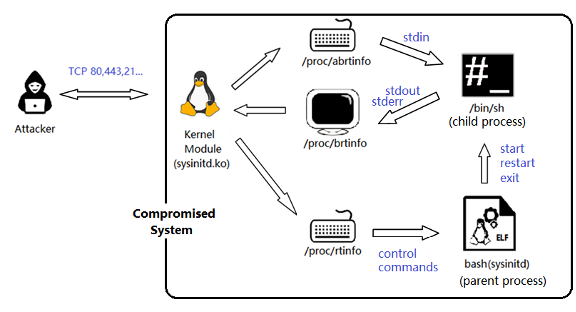
The rootkit malware employs a crafted shell script, Install.sh, to introduce its components into the targeted system. This script is the cornerstone of the attack, allowing the malware to embed itself deeply into the Linux operating environment. Two primary elements of the rootkit were identified:
- Kernel Module (sysinitd.ko): This module integrates at the kernel level, providing attackers with low-level system access and the ability to intercept network traffic.
- User-Space Binary (sysinitd): Disguised as a legitimate process, this component handles communication between the kernel module and the attacker.
The malware achieves persistence by embedding startup entries into critical Linux configuration files, such as /etc/rc.local and /etc/rc.d/rc.local. These entries ensure the malware is automatically loaded during system boot, making it difficult to detect and remove.
Key Components and Attack Methodology
Kernel Module Analysis
The kernel module (sysinitd.ko) is the backbone of the attack, designed to integrate seamlessly with the Linux kernel. Upon loading, the module performs several critical tasks:
- The decryption of Strings: It decrypts internal strings required for its operations, enhancing its stealth capabilities.
- Netfilter Hook Registration: The module registers a Netfilter hook at the NF_INET_PRE_ROUTING stage, allowing it to intercept and manipulate incoming network traffic.
- Notable File Entries: It creates file entries in the /proc directory (e.g., /proc/abrtinfo, /proc/brtinfo, and /proc/rtinfo) to facilitate communication with the user-space component.
The Netfilter hook is particularly noteworthy. InterceptingInteracting incoming TCP packets allows the malware to distinguish legitimate packets from those crafted by attackers. These crafted packets, known as “attack-init” packets, contain specific byte sequences and verification data, enabling secure and authenticated communication with the attacker.
User-Space Binary (salinity)
The user-space binary, sysinitd, is critical in executing attacker commands. To evade detection, it masquerades as a “bash” process. The binary communicates with the kernel module through the /proc entries, enabling the following functions:
- Command Execution: Attackers can remotely execute Linux commands with root-level privileges. These commands are sent through the Netfilter hook and processed by sysinitd.
- Process Management: The parent process of sysinitd acts as a daemon, managing child processes spawned via the fork() system call.
- Encryption Flexibility: Communication between the malware and the attacker can be encrypted, ensuring data confidentiality.
- Deception Techniques: The malware’s ability to disguise itself as a legitimate process adds another layer of stealth.
Capabilities of the Malware
The rootkit malware is a testament to the increasing sophistication of cyberattacks. Its key capabilities include:
- TCP Session Hijacking: The malware can hijack TCP sessions, including HTTPS, SSH, and FTP, using a three-way handshake.
- Remote Command Execution: By leveraging the Netfilter hook and user-space binary, attackers can execute a wide range of Linux commands, from file downloads to directory browsing.
- Stealth and Persistence: The combination of kernel-level integration and user-space processes ensures that the malware remains undetected while maintaining persistence.
- Dynamic Control: Attackers can dynamically manage processes, including restarting or terminating them, and send control signals such as Ctrl+C.
FortiGuard demonstrated the functionality of the rootkit using a Python script, simulating an attacker’s control over the compromised system. The demonstration highlighted the malware’s ability to execute commands and manipulate network traffic, as observed through tools like Wireshark.
Implications of the Attack
The advanced nature of this rootkit underscores the evolving complexity of cyberattacks. By combining kernel-level and user-space components, attackers can achieve:
- Complete System Control: The malware provides attackers with root-level access, enabling them to manipulate system processes and network traffic at will.
- Stealth and Evasion: Encryption, process disguise, and kernel-level integration make the malware challenging to detect and remove.
- Exploitation of Zero-Day Vulnerabilities: The attack highlights the importance of patching and updating systems to mitigate the risk of zero-day exploits.
FortiGuard’s Recommendations for Mitigation
To counter the threat posed by such sophisticated malware, FortiGuard provides the following recommendations:
1. Patch Management
Regularly update firmware and software to address known vulnerabilities. Ensure that all enterprise systems run the latest security patches to minimize the risk of zero-day exploits.
2. Auditing and Monitoring
Employ advanced monitoring tools to detect unusual processes and network traffic. Regular audits of system logs can help identify anomalies indicative of malicious activity.
3. Procfs Security
Harden the permissions of the /proc directory to prevent misuse by malicious actors. This can limit the ability of malware to communicate between kernel and user-space components.
4. Incident Response Preparation
Prepare incident response teams to detect and mitigate exploits quickly. Develop a robust incident response plan that includes steps for isolating compromised systems and removing persistent threats.
5. Network Security Measures
Implement firewalls, intrusion detection systems (IDS), and intrusion prevention systems (IPS) to monitor and block malicious traffic. Network segmentation can also help contain the spread of malware.
6. Employee Training
Educate employees about cybersecurity best practices, such as recognizing phishing attempts and reporting suspicious activity. Human error remains a significant factor in the success of cyberattacks.
Conclusion
Fortinet’s detailed analysis of this advanced rootkit malware provides invaluable insights into the techniques employed by attackers. By exploiting multiple zero-day vulnerabilities, the attackers achieved a high degree of stealth, persistence, and control over compromised systems.
This case is a stark reminder of the need for proactive cybersecurity measures, including regular patching, robust monitoring, and comprehensive incident response planning. As cyber threats evolve, organizations must stay vigilant and adopt a multi-layered approach to cybersecurity to safeguard their critical systems and data.
For more:
https://cybersecuritynews.com/rootkit-malware-controls-linux-systems-remotely/
Share this :