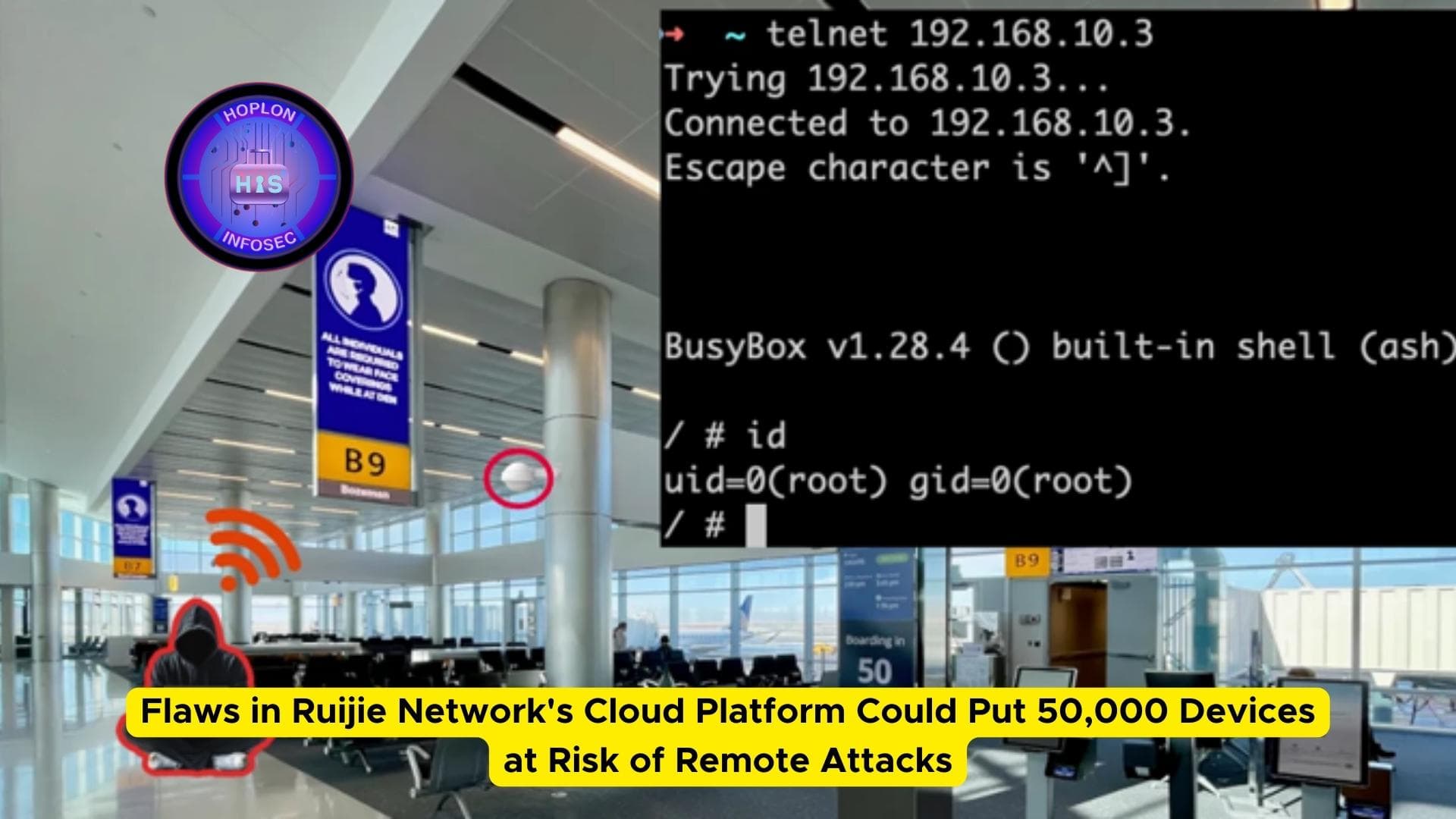
Flaws in Ruijie Network's Cloud Platform Could Put 50,000 Devices at Risk of Remote Attacks
Hoplon InfoSec
25 Dec, 2024
In a recent revelation, cybersecurity researchers have uncovered significant vulnerabilities in the cloud management platform developed by Ruijie Networks. These flaws, if exploited, could grant attackers control over network appliances, posing severe threats to organizations relying on these devices. The implications of these findings underscore the need for heightened vigilance in securing the Internet of Things (IoT) and cloud-enabled devices.
The Scope of the Vulnerabilities
According to Claroty researchers Noam Moshe and Tomer Goldschmidt, these vulnerabilities affect the Reyee platform and the Reyee OS network devices. “The vulnerabilities, if exploited, could allow a malicious attacker to execute code on any cloud-enabled device, giving them the ability to control tens of thousands of devices,” they stated in their analysis. Such access can lead to widespread disruption, data breaches, and unauthorized control over critical infrastructure.
The operational technology (OT) security company investigated Ruijie’s IoT solutions and identified 10 distinct security flaws. To demonstrate the potential risks, the researchers devised an attack dubbed “Open Sesame,” capable of breaching an access point in close physical proximity via the cloud and gaining unauthorized network access.
Highlights of the Critical Vulnerabilities

Of the 10 identified vulnerabilities, three have been rated as Critical in severity:
CVE-2024-47547 (CVSS score: 9.4):
This vulnerability arises from a weak password recovery mechanism. Such a mechanism leaves the authentication process susceptible to brute force attacks, enabling attackers to compromise device security.
CVE-2024-48874 (CVSS score: 9.8):
A server-side request forgery (SSRF) flaw can be exploited to access internal services used by Ruijie and its AWS-based cloud infrastructure. Attackers leveraging this flaw could disrupt cloud operations and access sensitive internal systems.
CVE-2024-52324 (CVSS score: 9.8):
The use of an inherently dangerous function that allows attackers to send malicious MQTT messages, potentially leading to arbitrary operating system command execution on affected devices.
Breaking MQTT Authentication
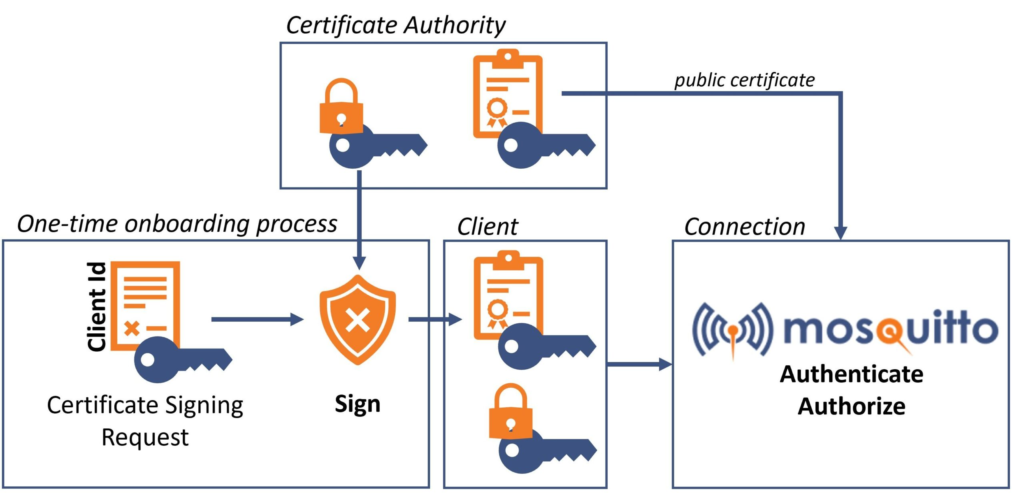
Photo Credit: https://cedalo.com
One of the critical findings in Claroty’s research is the ease of bypassing MQTT authentication by knowing the device’s serial number (CVE-2024-45722, CVSS score: 7.5). Exploiting this flaw enables access to Ruijie’s MQTT broker, revealing a complete list of all cloud-connected devices’ serial numbers.
Using leaked serial numbers, attackers can:
Generate valid authentication credentials for all cloud-connected devices.
Perform denial-of-service (DoS) attacks by authenticating on behalf of devices and disconnecting them.
Send fabricated messages and events to the cloud, misleading device users.
Access all MQTT message queues to issue malicious commands that execute on cloud-connected devices.
This chain of vulnerabilities significantly escalates the risks associated with Ruijie’s cloud management platform.
Open Sesame: Exploiting Wi-Fi Networks
Another alarming aspect of the research involves exploiting physical proximity to Ruijie’s Wi-Fi networks. An attacker adjacent to a Wi-Fi network using Ruijie access points can:
Extract the device’s serial number by intercepting raw Wi-Fi beacons.
Leverage MQTT communication vulnerabilities to achieve remote code execution (CVE-2024-47146, CVSS score: 7.5).
The researchers highlighted the cascading effects of such an attack, where a single point of vulnerability can compromise a broader network of devices.
The Scale of Impact and Resolution
Before Ruijie Networks addressed these issues, approximately 50,000 cloud-connected devices were estimated to be vulnerable. Following responsible disclosure, the Chinese company implemented fixes, and no user action is required to mitigate the threats.
“This is another example of weaknesses in so-called internet-of-things devices such as wireless access points, routers, and other connected things that have a fairly low barrier to entry onto the device, yet enable much deeper network attacks,” the researchers emphasized.
Broader Implications for IoT Security

Discovering these vulnerabilities in Ruijie’s platform is not an isolated incident. It highlights systemic issues in the IoT ecosystem, where weak security mechanisms can lead to catastrophic outcomes. This incident aligns with similar findings by security firm PCAutomotive, which flagged 12 vulnerabilities in the MIB3 infotainment unit used in certain Skoda cars.
Vulnerabilities in Skoda’s MIB3 Infotainment Unit
The flaws in Skoda’s infotainment unit include:
Code execution over Bluetooth.
Privilege escalation to root.
Bypassing secure boot for persistent code execution.
Controlling the infotainment unit via DNS channels every time the car starts.
These vulnerabilities allow attackers to:
Track a car’s location in real time.
Record conversations via the in-car microphone.
Take screenshots of the infotainment display.
Exfiltrate contact information from the system.
Lessons Learned and Future Directions
The vulnerabilities in Ruijie’s platform and Skoda’s infotainment unit underline the critical need for robust security in IoT and cloud-enabled devices. Organizations and manufacturers must prioritize security from the design phase, ensuring:
Strong authentication mechanisms.
Regular vulnerability assessments.
Swift responses to reported flaws.
Moreover, users must remain vigilant about applying security updates and monitoring device behavior for anomalies.
Conclusion
Claroty and PCAutomotive’s findings are stark reminders of the growing risks in an interconnected world. As IoT adoption continues to surge, securing these devices is no longer optional but imperative. Collaboration between researchers, manufacturers, and users is essential to address these challenges and build a safer digital ecosystem.
Follow us on Twitter and LinkedIn to stay informed about the latest cybersecurity updates. Together, we can work towards a more secure future.
For More:
https://thehackernews.com/2024/12/ruijie-networks-cloud-platform-flaws.html
Share this :