Session Hijacking: How Stolen Tokens Bypass Your Defenses

Hoplon InfoSec
21 May, 2025
In the age of web apps, identity is the new perimeter. Once a user logs in, their session token becomes the gateway to everything, data, features, APIs. But if that token falls into the wrong hands, it’s not just a user who’s compromised, it’s your entire system that’s exposed.
Unlike brute force attacks or malware that leave traces, session hijacking is invisible. The attacker doesn’t break in; they walk in through a stolen key. This silent, often undetected exploit has become one of the most dangerous threats to modern applications.
What Is Session Hijacking?

Session hijacking is when an adversary takes control of a valid user session by capturing or predicting session tokens. These tokens usually stored in cookies or headers act as proof of authentication. Once hijacked, the attacker impersonates the user without needing a password or MFA.
Types of session hijacking:
- Active hijacking: Live interception during a session
- Passive hijacking: Listening and capturing tokens
- Session fixation: Tricking a user into authenticating with a token the attacker controls
What Is Token Theft?
Token theft is the unauthorized acquisition of credentials like:
- JSON Web Tokens (JWTs)
- OAuth access tokens
- SSO tokens
- API keys or cookies
Because modern web apps rely heavily on stateless authentication, stolen tokens become identity proxies. If the app trusts the token, it trusts the attacker.
Techniques Used by Attackers
1.Cross-Site Scripting (XSS)
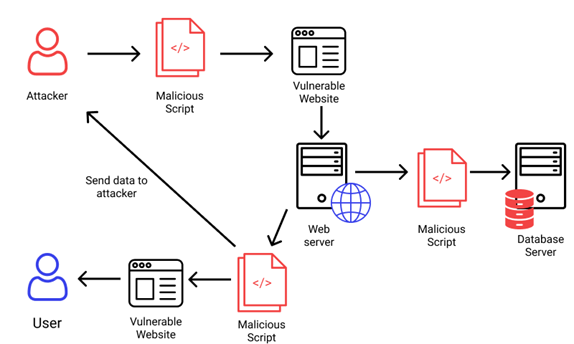
Injects malicious scripts into trusted websites to steal tokens from localStorage or cookies.
2.Man-in-the-Middle (MitM)
Intercepts HTTP traffic over unsecured connections to grab session headers or cookies.
3.Session Fixation
Tricks users into logging in with a known token the attacker can reuse.
4.Token Leakage
Tokens in URLs can show up in logs or referrer headers, leaking sensitive credentials.
5.Malware
Extracts tokens from memory, browser storage, or auto-fill extensions.
6.Clickjacking
Deceives users into performing actions in invisible frames while unknowingly staying authenticated.
Why Session Hijacking Is So Dangerous

- Bypasses MFA and login detection
- Leaves no audit trail — no suspicious login attempts
- Tokens often live for hours/days
- Can silently access APIs and admin panels
- Many apps don’t monitor session reuse
Once a token is stolen, attackers don’t need brute force they simply use what’s already trusted.
Real-World Breaches Involving Token Theft
1. Uber (2022)
Social engineering led to the theft of session tokens, giving attackers full access to Slack, AWS, and developer dashboards.
2. Microsoft Teams (2023)
Electron-based clients exposed session tokens stored in plaintext, enabling impersonation even after logout.
3. GitHub OAuth Breach
Compromised third-party OAuth apps leaked access tokens, exposing private repo data of multiple enterprises.
4. Slack (2019)
A misconfigured analytics script leaked session cookies to a third-party domain.
5. Reddit (2018)
Token theft via compromised employee accounts bypassed SMS 2FA and exposed user email logs.
Best Practices to Prevent Token Theft
1.Use Secure, HttpOnly, SameSite Cookies
This ensures cookies are encrypted, inaccessible to JavaScript, and not shared cross-site.
2.Avoid LocalStorage for Tokens
Unlike cookies, localStorage is vulnerable to XSS attacks.
3.Short Token Lifetimes + Refresh Flows
Reduce exposure by rotating tokens often and using secure refresh logic.
4.Bind Tokens to IP or Device
If a token is used from a different IP, prompt re-authentication.
5.Require Re-auth for Sensitive Actions
Critical functions (e.g., fund transfers) should require password or biometric reconfirmation.
6.Monitor Session Behavior
Use session analytics to detect anomalies like rapid IP switching, high request rates, or unusual user agents.
7.Use Content Security Policy (CSP)
Prevent token-stealing JavaScript via strong CSP headers and input validation.
Advanced Defenses and Emerging Strategies
1.Token Binding
Cryptographically ties tokens to the TLS connection or client stolen tokens fail outside the origin device.
2.Continuous Authentication
Revalidates user session context based on activity, environment, and biometrics.
3.WebAuthn & Passkeys
Replace token reliance with phishing-resistant, password less authentication.
4.Proof of Possession (PoP) Tokens
Require the client to demonstrate it still holds a cryptographic key.
5.AI & Machine Learning
Used in UEBA (User and Entity Behavior Analytics) to baseline typical user behavior and detect session anomalies.
6.Velocity and Geo-based Rules
Prevent login or session reuse from impossible distances or timeframes (e.g., login in US and Russia within 2 minutes).
Developer Mistakes That Lead to Breaches

- Using localStorage or exposing tokens in frontend code
- Keeping long-lived tokens without rotation
- Not verifying JWT signatures or using insecure algorithms (e.g., none)
- Not invalidating tokens on logout, password reset, or session timeout
- Storing access tokens in URLs or query strings
- Skipping HTTPS; allowing token sniffing over public Wi-Fi
The Role of AI in Session Hijack Detection
Modern systems are integrating AI to:
- Detect anomalies in session duration, location, velocity
- Analyze login consistency across time and device type
- Predict risky behavior with UEBA systems
- Automate session invalidation if anomalies are detected
AI doesn’t just flag risks, it can auto contain them by killing compromised sessions instantly.
Securing the Future
Session hijacking and token theft are no longer niche risks, they’re mainstream, scalable attack methods that silently bypass our most trusted security layers.
To secure the future:
- Treat tokens like passwords. Never expose or store carelessly
- Use adaptive, context-aware authentication
- Rotate, revoke, and monitor tokens actively
- Design for breach containment, assume session compromise and build defenses accordingly
- Educate developers to treat session integrity as core to app security
The trust we place in tokens must be earned continuously, not assumed permanently.
In this era of ghost sessions, attackers don’t break in, they’re already logged in.
It’s time we stop trusting and start verifying continuously.
Share this :