Social Engineering Attacks: How to Spot and Prevent Them
Hoplon InfoSec
30 Mar, 2025
In today’s digital world, cybersecurity is a top priority for businesses and individuals alike. Yet, despite robust technical defenses, one of the most effective threats to security comes from an attack vector that preys on human behavior: social engineering. Social engineering attacks exploit psychological manipulation to deceive individuals into divulging confidential information or performing actions that compromise security. Understanding how these attacks work, how to spot them, and how to prevent them can save you from significant harm.
What Are Social Engineering Attacks?

Social engineering refers to a variety of malicious activities that manipulate individuals into breaking normal security procedures. Unlike technical attacks that rely on software or hardware vulnerabilities, social engineering attacks focus on human error and psychological tactics. The attacker often poses as a trusted entity to gain sensitive information, access systems, or persuade the victim to carry out certain actions.
These attacks can take various forms, including phishing, pretexting, baiting, and tailgating, all of which rely on exploiting human trust or curiosity.
Common Types of Social Engineering Attacks
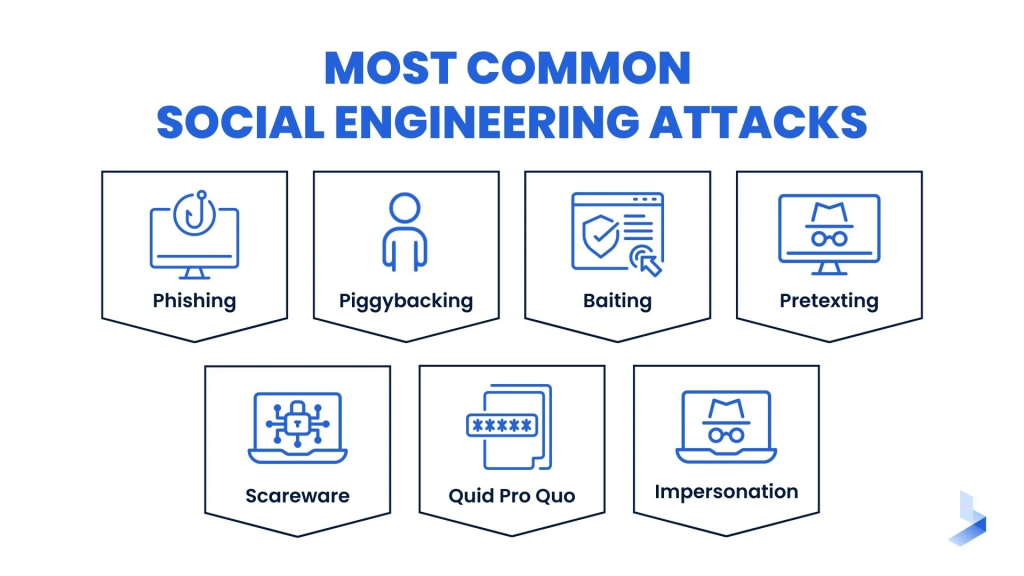
Phishing Attacks
Phishing is one of the most widely recognized forms of social engineering. In a phishing attack, the attacker masquerades as a trustworthy entity, such as a well-known company or service provider, to trick the victim into disclosing sensitive information, such as usernames, passwords, or credit card numbers. These attacks often occur via email, text messages, or social media platforms and typically contain links to fake websites that look identical to legitimate ones.
Pretexting
Pretexting involves creating a fabricated scenario, or pretext, to persuade the victim to release sensitive information. This might include pretending to be a coworker, a customer support agent, or a government official. The attacker may ask for details like your social security number, bank account information, or login credentials, often using a backstory to make the request seem legitimate.
Baiting
Baiting is an attack where the attacker entices the victim with something desirable, such as free software, a movie download, or exclusive content. The attacker’s goal is to lure the victim into clicking a link or downloading a malicious file that infects the victim’s device with malware or ransomware.
Tailgating
Tailgating occurs when an attacker follows someone into a secure area, such as an office building or data center, by closely trailing behind them and exploiting their good nature. In this attack, the victim may hold the door open for someone who appears to be authorized to enter, giving the attacker physical access to restricted areas.
How to Spot Social Engineering Attacks
Spotting social engineering attacks can be challenging because they rely on psychological manipulation. However, there are several warning signs and behaviors to be mindful of.
Unexpected Communication
If you receive an unexpected email, text message, or phone call requesting personal or sensitive information, be cautious. Even if the message seems to come from a legitimate source, always verify the authenticity of the request. Official organizations, such as banks or government agencies, will never ask for sensitive information via unencrypted messages.
Urgency or Pressure to Act Quickly
Attackers often use a sense of urgency to manipulate their victims into acting without thinking. Phrases like “Your account will be locked unless you respond immediately” or “This offer is only available for a limited time” are common in phishing attacks. If you feel rushed, take a moment to pause and think before responding.
Suspicious Links or Attachments
Always be cautious of unsolicited emails or messages that contain links or attachments. Even if the email appears to come from a trusted source, hovering your mouse over links can reveal their true destination. If the URL looks strange or unfamiliar, do not click on it. Similarly, avoid downloading attachments from unknown sources, as they may contain malware.
Requests for Personal or Confidential Information
Legitimate organizations typically do not ask for sensitive information, such as passwords, Social Security numbers, or bank account details, via email or text. If you receive such a request, especially from an unexpected source, it’s a red flag. Verify the request by directly contacting the company or individual through known communication channels.
Unusual Behavior or Inconsistencies
Pay attention to any inconsistencies in communication. This might include poorly written emails, unusual greetings, or strange requests. Phishing emails, for example, often contain grammar errors or misspelled words. Similarly, pretexting attempts may involve suspicious or conflicting details in the attacker’s story. Trust your instincts if something feels off.
How to Prevent Social Engineering Attacks
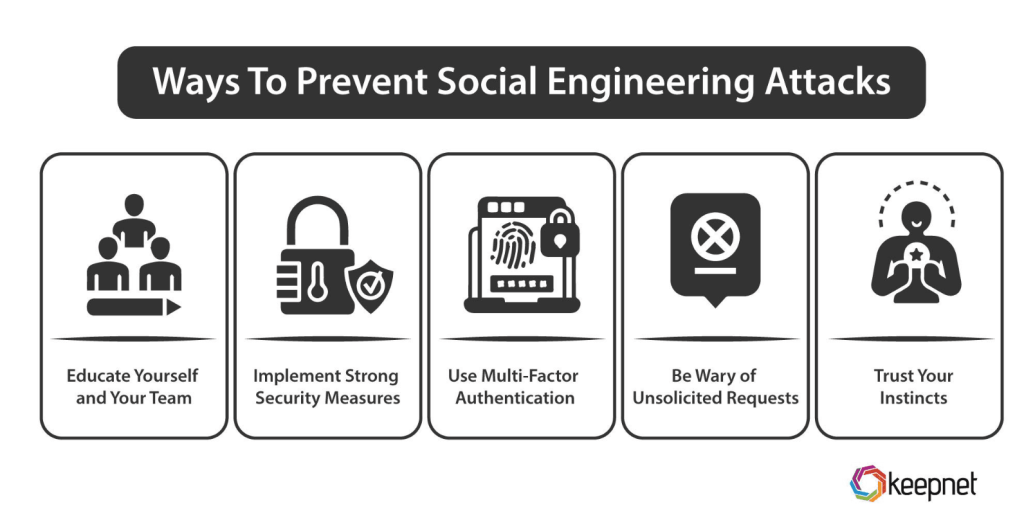
Preventing social engineering attacks requires a combination of awareness, vigilance, and proactive measures. By understanding the techniques used by attackers and implementing security best practices, you can significantly reduce your risk.
Educate Employees and Users
One of the most effective ways to prevent social engineering attacks is through education. Organizations should regularly train their employees on how to recognize and respond to phishing emails, pretexting attempts, and other types of social engineering. Conducting simulated phishing exercises and security awareness campaigns can help individuals recognize common tactics and develop critical thinking skills.
Implement Multi-Factor Authentication (MFA)
Even if an attacker successfully obtains a password through social engineering, multi-factor authentication (MFA) can provide an additional layer of security. MFA requires users to verify their identity using multiple methods, such as a fingerprint, text message code, or authentication app, making it much more difficult for attackers to gain unauthorized access.
Verify Requests
Before responding to any request for sensitive information, always verify the identity of the requester. If the request comes via email or phone, contact the individual or organization directly using a trusted phone number or email address. Avoid using the contact information provided in the suspicious message itself.
Use Strong, Unique Passwords
A strong, unique password for each account is crucial for reducing the impact of social engineering attacks. Use a combination of uppercase and lowercase letters, numbers, and symbols, and avoid using easily guessable information like names or birthdates. Consider using a password manager to generate and store complex passwords securely.
Limit Access to Sensitive Information
Limiting access to sensitive information on a need-to-know basis can help minimize the damage caused by a social engineering attack. Implementing the principle of least privilege ensures that employees and users only have access to the data necessary for their role. This reduces the likelihood that an attacker can gain access to critical systems or information through social engineering.
Be Cautious with Public Information
Attackers often gather information from social media and public records to craft convincing social engineering attacks. Be mindful of what you share online, and ensure that personal details, such as your job title, contact information, or family members’ names, are not easily accessible to the public. Adjust your privacy settings on social media platforms to limit the amount of information available to outsiders.
Monitor Systems for Suspicious Activity
Regularly monitoring your organization’s network and systems for unusual behavior or unauthorized access can help detect social engineering attacks early. Implement intrusion detection systems (IDS) and conduct regular security audits to identify any signs of a breach. The sooner you spot an attack, the quicker you can respond and mitigate potential damage.
Conclusion
Social engineering attacks are a growing threat to individuals and businesses alike. They rely on manipulating human psychology rather than exploiting technical vulnerabilities, making it difficult to prevent using traditional security measures. However, by educating yourself and others, being cautious with personal information, and adopting robust security practices, you can significantly reduce the risk of falling victim to these attacks. With increased awareness and vigilance, individuals and organizations can stay one step ahead of cybercriminals and protect their sensitive data and assets.
Share this :