The Talenthook Data Breach: How a Simple Cloud Misstep Exposed Millions of Job Seekers

Hoplon InfoSec
10 Jul, 2025
The digital hiring landscape has transformed how people find jobs and how employers screen candidates. But this convenience comes with hidden risks. In one of the most significant data exposures of the year, Talenthook, a popular applicant tracking system, left nearly 26 million resumes exposed to the open internet. The breach wasn’t the result of sophisticated hacking. Instead, it stemmed from a common but dangerous mistake: cloud misconfiguration.
Talenthook’s failure underscores a growing pattern in modern cybersecurity: well-intentioned platforms overlooking foundational security hygiene. As remote hiring and digital applicant management continue to dominate recruitment strategies, the integrity of platforms like Talenthook becomes central not only to operations but also to trust.
What Is Talenthook, and Why Does It Matter?
TalentHook is a software platform used by recruiters, HR departments, and staffing agencies to manage the job application process. It serves as a digital repository for resumes, cover letters, and applicant data. Many companies rely on systems like Talenthook to automate talent sourcing, shortlist candidates, and store documentation for future roles.

While it offers convenience to employers, it also becomes a central repository of sensitive personal and professional data. The trust placed in such platforms makes them high-value targets or, in this case, high-risk liabilities when not properly secured. In today’s job market, where candidates share more personal information than ever , even minor gaps in data protection can lead to far-reaching damage.
How Was the Data Exposed?
The breach occurred not because of malware or cybercriminal ingenuity, but due to a public Microsoft Azure Blob storage container. This container, meant to be private, was configured to allow unrestricted public access. Anyone with a web browser and the correct URL could download files; no login required.

Within this container were nearly 26 million resumes. Some were PDF files. Others were Word documents. But all of them contained deeply personal information. The exposure was discovered by security researchers who routinely scan the web for unprotected databases, and while the exact duration of exposure remains unclear, the size and accessibility of the files suggest the issue persisted for a significant period.
The Depth of the Exposed Information Talenthook Data Breach
Each resume revealed more than just a name or phone number. Many included:
- Full legal names
- Email addresses and phone numbers
- Home mailing addresses
- Employment history and current job roles
- Educational credentials and certifications
- Skills, personal interests, and salary expectations
This combination of professional and personal data makes resume files highly valuable to cybercriminals. Much of this information is permanent, unlike leaked passwords that are changeable. Job seekers may not even be aware that their resume was stored in Talenthook’s system, especially if their data was submitted by recruiters or through third-party job boards integrated with the platform.
The Real-World Risk to Job Seekers

When such data is exposed, job seekers become prime targets for scams. With access to a person’s entire work history, fraudsters can create customized phishing emails that appear convincingly legitimate. Some impersonate recruiters, using real data to trick victims into providing additional details like banking information, identity documents, or social security numbers.
Another common risk is job fraud. Scammers may reach out with fake job offers, asking candidates to pay for background checks, work-from-home equipment, or training programs, all under the guise of legitimate employment.
The long-term threat is especially concerning. Resume data, once exposed, does not expire. Threat actors may sit on this information for years, combining it with other data sets from future breaches to build full identity profiles for impersonation, credential stuffing, or financial fraud.
Comparison with Similar Resume Data Breaches
This isn’t the first time a resume hosting service has suffered a leak due to cloud misconfiguration. Similar breaches have occurred across various platforms recently. What makes the Talenthook breach stand out is its scale and the absence of active cybersecurity controls.
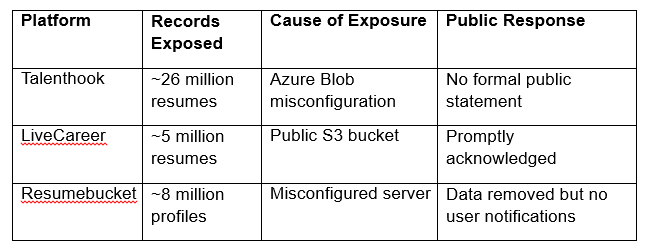
This trend shows that resume data remains poorly protected across several platforms, despite its sensitivity. It also suggests that existing standards for third-party HR technology vendors may be insufficient to safeguard the vast amount of personal data they manage.
Why Cloud Misconfigurations Keep Happening
Misconfigured cloud storage is one of the leading causes of data exposure in recent years. Public cloud platforms like Azure and AWS provide powerful infrastructure, but that power comes with responsibility. When organizations don’t fully understand their cloud settings or skip essential security checks, they can unintentionally leave sensitive data wide open.

The broader issue is one of assumptions: assuming default settings are secure, assuming developers know how to configure privacy options, and assuming internal teams will catch mistakes before they scale. This breach highlights the urgent need for better cloud governance and hands-on security training across technical and non-technical roles alike.
How Long Was the Data Exposed?
While the exact duration is unclear, the publicly accessible container may have been online for months. Security researchers found the data and responsibly disclosed it to the platform’s parent company. However, no public timeline or statement was issued confirming how long the data was live or whether it was accessed by bad actors before being locked down.
The absence of this timeline leaves affected individuals in the dark and adds to public distrust. In cybersecurity, timing matters; a delay in response can multiply the potential harm and erode accountability.
The Silence from Talenthook
Perhaps the most troubling aspect of this breach is the response, or lack thereof. As of mid-July 2025, Talenthook and its parent company have not issued a formal public apology, user notifications, or support documentation for affected individuals. There has been no visible acknowledgment of responsibility.
In data breaches, silence is rarely neutral. It can undermine trust, damage a brand’s reputation, and trigger long-term fallout from regulators and the public. Today’s consumers expect transparency. The lack of immediate communication suggests either unpreparedness or avoidance, both of which can be damaging in equal measure.
What This Breach Means for Employers
Employers who use Talenthook to manage their applicant pipelines may now be indirectly involved in this breach. Candidates who applied through their job postings could have their data compromised. If those employers didn’t realize the extent to which Talenthook was storing and exposing applicant data, they may still be unaware that their applicants were impacted.
This incident is a wake-up call for HR teams. It underscores the need to thoroughly vet any recruitment technology vendor not only for features and pricing but also for cybersecurity posture. Procurement decisions should involve IT and security leaders, not just HR professionals. Organizations must treat applicant data with the same care as customer or financial data.
Broader Implications for HR Technology Vendors
The Talenthook incident casts a long shadow over the HR tech industry. As platforms scale and integrate more cloud services, the likelihood of misconfiguration grows. Vendors must prioritize default security settings, offer better administrative guidance, and proactively monitor for misconfigured assets.
This also places pressure on HR vendors to shift from a compliance-first mindset to a security-first mindset. Compliance is about following rules. Security is about protecting people. In an industry that deals with human identities and career histories, the stakes couldn’t be higher.
Regulatory and Legal Fallout on the Horizon
Depending on the jurisdictions involved, Talenthook may face scrutiny from state attorneys general, data protection authorities, or federal regulators. In the United States, rules such as the California Consumer Privacy Act (CCPA) and similar laws in other states may apply.
If Talenthook stored data on EU citizens, GDPR obligations could be triggered as well. Even if no fines are immediately issued, the reputational and legal risks are now substantial.
Class-action lawsuits could also emerge. Job seekers whose data was exposed without consent may seek damages, especially if they experience fraud or phishing attacks traceable to the leaked information.
What Job Seekers Can Do to Protect Themselves
Those who have applied for jobs through Talenthook-integrated portals should take precautions. Even if they’re not sure their data was involved, it’s wise to assume exposure and act accordingly.
Recommended steps include:
- Monitoring email and SMS for suspicious job-related communications
- Avoiding any job offers that request upfront payments or banking information
- Updating account passwords and enabling two-factor authentication where possible
- Using a credit monitoring service to detect unusual activity
- Being cautious about how much information is included on publicly posted resumes
Being proactive now can mitigate long-term risks. In the age of digital recruitment, job seekers must become digital defenders of their own identities.
What Organizations Should Learn from This
For companies that rely on third-party platforms to manage recruitment, the Talenthook incident serves as a stark lesson in shared responsibility. Simply outsourcing a function does not eliminate risk. Organizations must verify that vendors meet basic security benchmarks and are capable of protecting applicant data.
IT departments should collaborate with HR teams during vendor selection and onboarding. Periodic audits, contract reviews, and incident response planning should be part of any company’s HR tech integration process.
Conclusion: A Breach That Could Have Been Prevented
The Talenthook data breach may not have involved sophisticated hacking, but it reflects a more dangerous trend: the normalization of carelessness in data security. This breach, potentially affecting nearly 26 million people, goes beyond resumes. It’s about trust, negligence, and a widespread failure to respect the value of personal information.
A single correctly configured permission setting could have prevented this incident. Millions of unsuspecting job seekers, whose data is forever out in the wild, are now bearing the cost of that oversight.
As the digital hiring landscape continues to grow, protecting job seekers must become a top priority, not an afterthought. The Talenthook breach should not be remembered as just another cloud leak. It should be remembered as a turning point in how we secure the tools that shape people’s futures.
Did you find this article helpful? Or want to know more about our Cybersecurity Products Services?
Explore our main services >>
Mobile Security
Endpoint Security
Deep and Dark Web Monitoring
ISO Certification and AI-Management System
Web Application Security Testing
Penetration Testing
For more services go to our homepage
Follow us on X (Twitter), LinkedIn for more Cyber Security news and updates. Stay connected on YouTube, Facebook and Instagram as well. At Hoplon Infosec, we’re committed to securing your digital world.
Share this :