VPN vs Zero Trust: Rethinking Secure Access in a Modern World

Hoplon InfoSec
27 May, 2025
VPN vs Zero Trust the all new trend hapenning now in the tech world. As the digital workplace evolves, so must the strategies organizations use to protect their systems, data, and people. Traditional cybersecurity models designed for a time when all users and resources lived inside a well-defined corporate perimeter, no longer provide adequate protection. The modern enterprise is distributed; employees work remotely, applications are hosted in the cloud, and cyber threats grow more sophisticated daily.
In this new landscape, ensuring secure access to enterprise resources has become one of the most critical components of a resilient cybersecurity strategy. Two approaches often discussed in this context are Virtual Private Networks (VPNs) and the Zero Trust security model. VPNs have been the go to solution for decades, but Zero Trust is increasingly viewed as the future of secure access.
This blog explores the fundamental differences between VPNs and Zero Trust, evaluates their strengths and weaknesses, and provides guidance on when and how to use each in today’s threat environment. We’ll go beyond surface-level comparisons to give you a deep understanding of why Zero Trust is gaining traction and how it addresses modern security challenges more effectively.
What is a VPN?
A Virtual Private Network (VPN) is a technology that establishes a secure, encrypted connection between a user’s device and a corporate network. Its primary purpose is to allow remote users to access internal systems as if they were physically located within the organization’s trusted network.
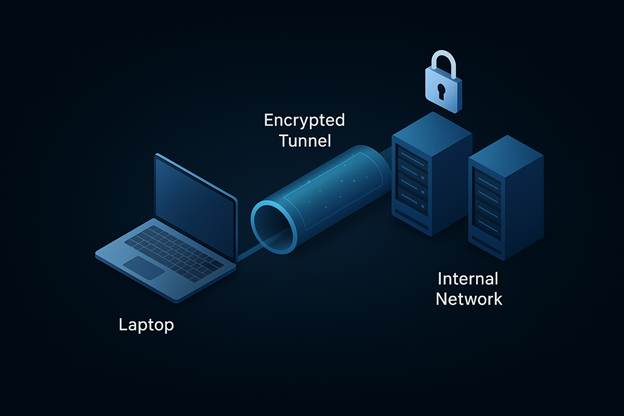
How VPNs Work?
When a user connects to a VPN, the software client initiates an encrypted tunnel to a VPN gateway (usually located at the organization’s data center). From there, the user’s traffic is routed into the corporate network, granting them access to internal applications and files. This process ensures that data transmitted between the device and the network is protected from eavesdropping and tampering.
In essence, the VPN acts like a digital moat, shielding users as they traverse potentially hostile internet terrain.
Benefits of VPNs
- Data Encryption: VPNs protect data in transit, making it harder for attackers to intercept or manipulate sensitive information.
- Remote Access: Employees can access corporate resources from anywhere, supporting remote work and business continuity.
- IP Masking: VPNs can mask the user’s IP address, making online activities less traceable.
- Simplicity and Compatibility: VPNs are relatively easy to implement and are supported by almost all operating systems and network setups.
Use Cases
- Small to mid-sized businesses with centralized IT environments
- Temporary remote access (e.g., contractors)
- Access to legacy, on-premises applications
- Situations where per-user or per-device context isn’t required
Limitations
While VPNs were adequate when most assets and users were on-premises, they fall short in today’s cloud-first, hybrid IT world:
- Over-Privileged Access: VPNs often grant broad access to internal resources once a connection is established, increasing the risk of lateral movement by attackers.
- Scalability Issues: VPN infrastructure can become a bottleneck during peak usage or when scaling rapidly, leading to performance degradation.
- Lack of Context: VPNs do not evaluate the context of access requests (e.g., device health, user behavior, or geographic location), limiting their ability to enforce dynamic risk-based access.
- Credential Exploits: If VPN credentials are stolen or phished, attackers can easily gain access to the internal network, often undetected.
- Maintenance Overhead: VPN appliances require continuous patching and upkeep to address vulnerabilities, increasing operational burden.
What is Zero Trust?
Zero Trust is a modern cybersecurity framework that operates on a fundamental principle: never trust, always verify. Unlike VPNs, which assume users can be trusted once authenticated, Zero Trust requires continuous verification of identity, context, and risk, regardless of whether the access attempt originates from inside or outside the network perimeter.

Key Principles of Zero Trust
- Continuous Verification: Trust is never implicit. Every access request is evaluated based on multiple factors including identity, device posture, location, time, and behavior. This ongoing evaluation ensures security decisions adapt to dynamic risk.
- Least Privilege Access: Users are granted the minimum level of access necessary to perform their job. Access is segmented and dynamically adjusted based on current risk. This limits exposure in the event of a breach.
- Micro-Segmentation: Resources are segmented into small zones. Even if a threat actor gains access to one area, they cannot move freely throughout the network. This containment strategy is crucial for stopping advanced persistent threats (APTs).
- Assume Breach: Organizations operate as if attackers are already inside the network, ensuring all systems are continuously monitored, access is tightly controlled, and suspicious behavior is flagged immediately.
How Zero Trust Works
Implementing Zero Trust involves deploying an ecosystem of interconnected tools and practices:
- Strong identity and access management (IAM): Centralized platforms that manage user identities, enforce policy, and provide audit trails.
- Multi-factor authentication (MFA): Verifying user identity through multiple evidence points (e.g., password + mobile code + biometrics).
- Endpoint detection and response (EDR): Ensuring devices are healthy and compliant before access is granted.
- Security information and event management (SIEM): Correlating events across the enterprise for real-time threat detection.
- Cloud access security brokers (CASB): Securing access to cloud applications and services.
- Behavior analytics: Detecting anomalous behavior based on baselines to surface hidden threats.
Benefits of Zero Trust
- Granular Control: Access decisions are made in real-time based on identity, risk posture, and user behavior.
- Reduced Attack Surface: Micro-segmentation limits the spread of threats across the network.
- Better Visibility: Continuous monitoring and logging provide deep insights into who is accessing what, when, from where, and why.
- Cloud and Remote Readiness: Zero Trust aligns seamlessly with remote work, hybrid cloud environments, and mobile workforces.
- Improved Compliance: Auditable access policies and fine-grained control support regulatory frameworks such as HIPAA, GDPR, and NIST.
Why Zero Trust Is Replacing VPNs?
Organizations are increasingly embracing Zero Trust not as a trend but as a necessity. The reality is that VPNs, while useful in their time, are no longer capable of defending against today’s highly dynamic and complex cyber threats. The reasons for this shift are rooted in both operational challenges and security risks.
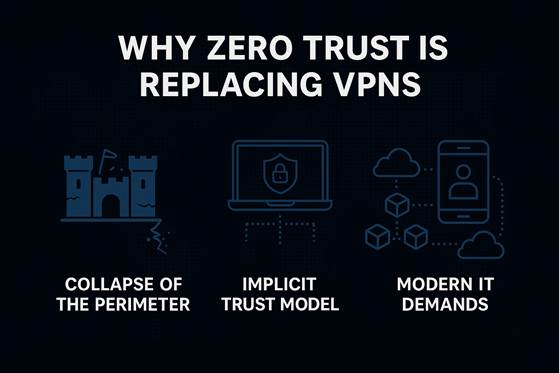
The Collapse of the Perimeter
In the past, the network perimeter was well-defined: employees worked within office networks, and security tools were built to defend the “castle.” VPNs extended that perimeter slightly but still relied on the idea that once inside, users could be trusted.
Today, that model has collapsed. Cloud applications, mobile devices, remote workers, and third-party integrations have dissolved the perimeter entirely. Users access data from everywhere. In this new reality, security must follow the user and device, not the network.
VPNs Trust Too Much, Too Soon
One of the most fundamental issues with VPNs is their implicit trust model. If a malicious actor obtains VPN credentials, they often receive full access to internal systems. There is no granular control, no behavioral monitoring, and no continuous validation.
Zero Trust, in contrast, doesn’t grant access simply because a user logged in. Every action is evaluated against real time contextual data; who is the user, what device are they on, where are they, what are they trying to do, and does this behavior make sense?
VPNs Struggle with Modern IT Demands
In today’s fast-paced, cloud-driven environments, performance and agility matter. VPNs can create significant latency, especially when routing traffic through centralized gateways. They also become bottlenecks during high-demand periods or DDoS attacks.
Zero Trust avoids this by allowing users to connect directly to applications with identity-based access policies. This not only improves performance but simplifies architecture, no need to backhaul all traffic to the corporate network.
Compliance and Auditing
Regulations such as HIPAA, PCI-DSS, GDPR, and CCPA require robust access controls, data protection, and auditable logs. VPNs offer little in terms of granular access control or auditability. Zero Trust, however, is built to support these requirements through policy enforcement, real-time logging, and user/session-level control.
Real-World Use Cases and Applications
Remote Workers
In a remote work scenario, VPNs provide connectivity, but once inside, users often have excessive access. In Zero Trust, users access only the specific tools and applications required for their role, and their behavior is continuously evaluated.
Mergers and Acquisitions
During a merger or acquisition, companies often need to grant access between networks quickly. With VPNs, this means connecting entire segments of one organization to another. Zero Trust offers a safer alternative by allowing fine-grained access controls without merging entire networks.
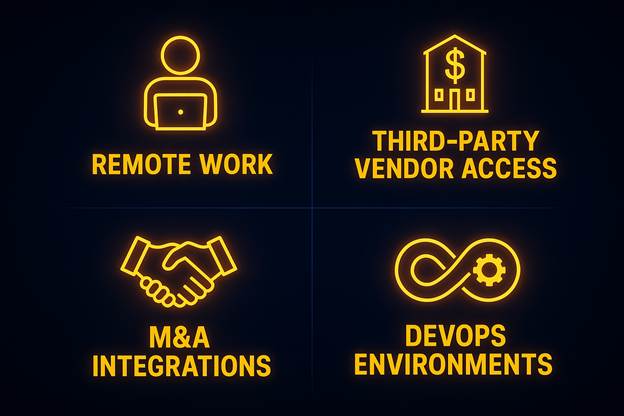
Third-Party Vendors
VPN access for vendors is risky. If their device is compromised, your entire network is exposed. Zero Trust enables time-bound, purpose-specific access tied to the individual and the device (not to a network segment).
DevOps and Cloud Teams
Modern DevOps pipelines involve dozens of tools, cloud services, and users with varying access needs. VPNs cannot keep up with the complexity. Zero Trust integrates directly with identity providers and CI/CD platforms, ensuring developers have seamless and secure access to what they need, nothing more.
Transitioning from VPN to Zero Trust
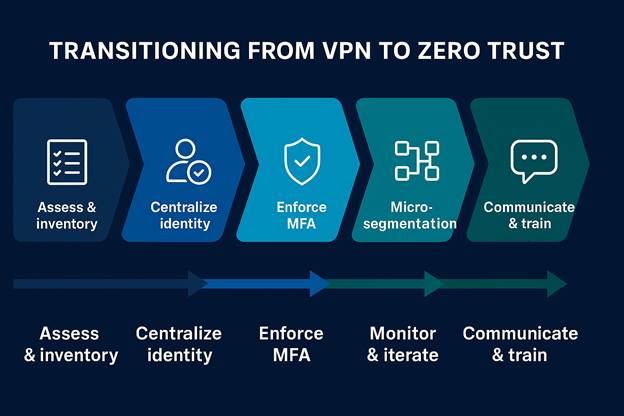
The transition from VPN to Zero Trust isn’t instant; it’s a journey that involves cultural, technical, and strategic change.
Step 1: Assess and Inventory
Identify all access points, users, roles, devices, and applications. Understand who needs access to what, and under what circumstances.
Step 2: Centralize Identity Management
A strong identity provider (IdP) such as Azure AD, Okta, or Ping Identity is foundational. These platforms support adaptive policies, MFA, and Single Sign-On (SSO).
Step 3: Enforce Strong Authentication
Multi-factor authentication should be a baseline requirement. Modern Zero Trust implementations also support risk-based authentication, which adjusts based on context (e.g., location anomalies, device status).
Step 4: Implement Micro-Segmentation
Instead of flat networks, break your infrastructure into small, isolated segments with unique access controls. This limits exposure and improves containment.
Step 5: Monitor and Iterate
Use EDR, SIEM, and User Behavior Analytics (UBA) to monitor access patterns. Continuously refine access policies based on observed risk.
Step 6: Communicate and Train
Zero Trust isn’t just a technology, it’s a mindset. End-user training is critical to ensure understanding and reduce resistance.
Coexistence and Hybrid Strategies
For many organizations, a full rip-and-replace isn’t feasible. That’s why hybrid models exist:
- VPNs can continue to secure access to legacy systems.
- Zero Trust policies can be layered over VPN traffic using proxy-based gateways.
- Conditional access policies can guide users to either VPN or Zero Trust pathways depending on the resource.
This coexistence allows businesses to modernize securely and incrementally.
Final Thoughts VPN vs Zero Trust

VPNs were built for a world that no longer exists, a world where employees worked from offices, data lived in on-premises servers, and trust was determined by network location.
That world has changed. Work is remote. Applications are in the cloud. Threats are persistent and increasingly sophisticated.
Zero Trust recognizes this change. It is not just an upgrade from VPN but it is a complete rethinking of how we manage identity, access, and risk. By continuously verifying users and their actions, limiting access to only what’s needed, and assuming that breaches will happen, Zero Trust offers a scalable, resilient model for cybersecurity in the 21st century.
The path forward is clear. The perimeter is gone. Trust must be earned. Access must be precise. Protection must be continuous.
Zero Trust delivers that future; one secured connection at a time.
Share this :