North America's Weekly Cybersecurity Recap June 28 To July 3

Hoplon InfoSec
04 Jul, 2025
As the first week of July comes to a close, North America faces the aftermath of one of the most turbulent weeks in recent cybersecurity history. From elite academic institutions and food retailers to healthcare systems and national infrastructure, the breadth and depth of attacks between June 28 and July 3 underscore a worrying trend: no sector is immune, and no motive is off-limits.
This comprehensive recap examines the eight most critical breaches and incidents disclosed during the week. These events reveal the growing complexity of threat actors, the expansion of attack surfaces, and the widening gap between security preparedness and real-world cyber resilience.
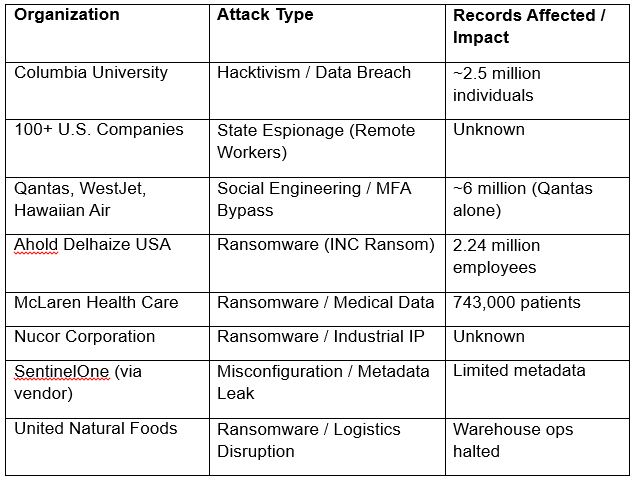
1. Columbia University Data Breach
Columbia University confirmed a highly targeted and politically motivated cyberattack that affected approximately 2.5 million individuals. The threat actor, a hacktivist using the alias “Computer Niggy Operations,” claimed responsibility for infiltrating Columbia’s internal infrastructure over a two-month period. The attacker accessed Student Information Systems, payroll databases, and admissions archives dating back over 25 years.
The stated goal was to expose the university’s alleged noncompliance with the 2023 U.S. Supreme Court decision that banned affirmative action in college admissions. The attacker used Trump-related symbolism and leaked a verified 1.6 GB sample of admissions and financial aid data.
Columbia has retained CrowdStrike and is currently notifying those affected. The breach raises urgent questions about ideological attacks on academic institutions and the challenge of securing legacy systems with complex, sprawling data networks.
2. The North Korean Remote-Worker Cyber Espionage Operation

The Department of Justice and FBI revealed that North Korean operatives infiltrated more than 100 U.S. companies by posing as legitimate remote IT workers. Using stolen U.S. identities, forged credentials, and deepfake-enhanced video interviews, these individuals gained access to sensitive internal systems.
North Korea’s weapons program received over $5 million in illicit income from the operation. Authorities raided 16 locations hosting “laptop farms,” seized over $900,000 in cryptocurrency, and uncovered critical evidence of insider-level access to proprietary data.
This case illustrates a significant evolution in cyberespionage tactics—blending social engineering with the vulnerabilities of remote workforce culture. It calls into question the adequacy of remote hiring and identity verification protocols in even the most security-conscious industries.
3. Airline Attacks by Scattered Spider
The cybercriminal group Scattered Spider shifted focus from financial institutions to the aviation sector, successfully launching attacks on Qantas, WestJet, and Hawaiian Airlines. Through a combination of phishing, SIM swapping, and helpdesk impersonation, the group bypassed MFA and infiltrated internal systems.
Qantas disclosed that up to 6 million customer records had been compromised, including names, travel history, loyalty account information, and birthdates. No payment data was exposed, but the risk of account fraud and identity theft remains significant.
The FBI issued a bulletin warning the airline industry about this threat group’s capabilities and highlighting the importance of staff training, particularly for IT support and service desk personnel. These breaches show how persistent social engineering remains a key threat vector—particularly when paired with knowledge of internal processes.
4. Ahold Delhaize Ransomware Breach
Ahold Delhaize USA, the grocery conglomerate that owns Stop & Shop and Food Lion, confirmed a ransomware breach originally launched in November 2024. The attack, attributed to the INC Ransom group, affected 2.24 million people and included highly sensitive HR data: Social Security numbers, health benefits information, immigration documents, and payroll records.
Though the breach occurred months earlier, the full scope and identity impact were only disclosed at the end of June 2025. Legal notices have been sent, and affected individuals are being offered two years of free identity monitoring.
The delayed disclosure and scale of the data exposed sparked criticism from labor unions and cybersecurity advocates. It also points out the need for faster breach reporting processes and transparency around recovery efforts in the retail sector.
5. McLaren Health Care Ransomware Incident
Michigan-based McLaren Health Care reported that a ransomware breach from July 2024 impacted more than 743,000 patients. Data exposed includes treatment records, insurance policy details, patient addresses, and health histories.

Patients and privacy groups expressed frustration that the breach was not publicly disclosed until nearly a year later. The organization now faces inquiries under HIPAA regulations, and legal proceedings are expected to follow.
This case reinforces the importance of timely notification in healthcare breaches, where delays can leave patients unaware and unprotected against identity misuse, medical fraud, and insurance scams.
6. Nucor Corporation Breach
Nucor, one of the largest steel and industrial manufacturers in North America, disclosed a ransomware incident targeting proprietary data and internal operations. The attackers reportedly gained access to design blueprints, planning documentation, and engineering specifications.
Several production facilities experienced operational disruptions, although the exact number of individuals affected remained undisclosed. The attackers are believed to have demanded a ransom to prevent the public release of trade secrets, indicating a shift toward data-leverage tactics rather than system encryption.
This breach serves as a case study in how cybercriminals are targeting industrial intellectual property (IP) for profit and competitive advantage rather than just employee or customer data.
7. SentinelOne Third-Party Exposure
Cybersecurity firm SentinelOne announced a limited data exposure caused by a misconfigured third-party storage environment. Although no client credentials or sensitive files were leaked, metadata such as customer IDs and system telemetry logs were temporarily accessible.
The firm swiftly contained the issue, notified impacted customers, and launched a full internal audit. The incident illustrates how even elite security companies remain vulnerable to indirect exposure via vendor supply chains.
It also highlights the critical importance of vendor risk management, especially in scenarios where partners handle diagnostic or monitoring telemetry. Click her e to read more.
8. United Natural Foods Supply Chain Attack
United Natural Foods Inc. (UNFI), a major U.S. food distributor, suffered a ransomware attack that disrupted warehouse and fulfillment operations across multiple states. Although no consumer data loss was confirmed, the incident paralyzed logistics, resulting in delivery delays to grocery stores and restaurant suppliers.
The attack underlines how ransomware can affect public supply chains—even without direct data exfiltration. Recovery efforts included rebuilding internal infrastructure and rerouting shipments. This incident is a reminder that the real-world consequences of cyberattacks often extend beyond IT teams and into public life.
Trends and Key Factors
Sector Convergence
The week’s breaches affected a diverse set of industries: education, aviation, healthcare, manufacturing, retail, cybersecurity, and logistics. This convergence indicates that cybercriminals no longer specialize—they target weakness, not verticals.
Evolving Threat Actors
The mix of state-backed espionage, ideological hacktivism, and organized cybercrime shows how the motivations behind attacks are expanding. Columbia University’s breach was ideological. North Korea’s operation was geopolitical. Financial motivations drove Scattered Spider’s airline attacks.
Remote Work Is a Risk Surface
The North Korean scheme demonstrated how modern, distributed workforces can be exploited. Without robust identity verification tools and biometric background checks, even the most secure environments are susceptible to false identities and social engineering.
Delayed Disclosures Create Additional Risk
McLaren Health and Ahold Delhaize faced public backlash due to long gaps between breach and disclosure. These delays increase legal liability and leave victims unaware of the risks they face, preventing timely action like freezing credit or changing passwords.
Social Engineering Dominates
From phishing at airlines to deepfakes in interviews, the human element remains the weakest link. Many of this week’s incidents involved the exploitation of trust rather than the exploitation of code.
Summary Table of Weekly Cybersecurity News
Final Thoughts
This week’s breaches collectively underscore one truth: cybersecurity is no longer just an IT problem; it’s a national resilience issue. The diversity of victims, techniques, and motivations demands a stronger collective response across sectors.
Organizations must embrace proactive security: zero-trust architecture, rapid breach detection, mandatory vendor risk audits, and robust incident response protocols. Likewise, governments must mandate tighter regulations on breach reporting timelines and improve cross-border cybercrime enforcement.
The coming weeks will reveal whether affected entities recover transparently or whether more silent fallout awaits. For now, the message is clear: North America’s cyber defenses must evolve or continue to be breached.
Share this :