Cloud Is Not Secure by Default: Why Cybersecurity Must Be Built In, Not Bolted On

Hoplon InfoSec
23 May, 2025
In the age of digital transformation, cloud computing has become the backbone of modern business operations. Cloud Security Services must be built in. Organizations across industries are migrating to cloud platforms like AWS, Microsoft Azure, and Google Cloud to enhance agility, scalability, and cost-efficiency. However, a dangerous misconception persists that cloud environments are secure by default. This misunderstanding has led to countless data breaches, compliance violations, and financial losses.
The truth is that cloud service providers (CSPs) operate under a shared responsibility model. While they ensure the infrastructure’s security, customers are responsible for securing their own data, configurations, and access controls. Failing to understand this division of responsibility opens the door to threats that traditional on-premises security models were not designed to handle.
This article explores why cloud cybersecurity must be embedded into every layer of your cloud strategy (not added as an afterthought) and how to build a resilient cloud environment that can withstand modern cyber threats.
The Shared Responsibility Model: What It Really Means
At the core of cloud security is the shared responsibility model. It delineates the division of security responsibilities between the CSP and the customer:
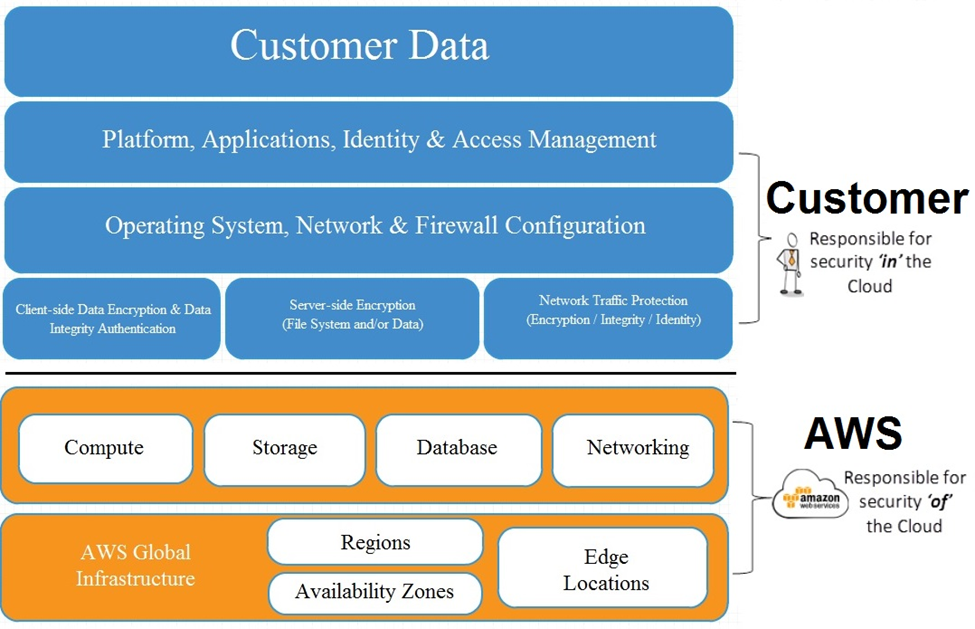
- Cloud Provider (e.g., AWS, Azure, GCP): Responsible for the security of the cloud. This includes physical security, hardware, network infrastructure, and foundational services.
- Customer: Responsible for security in the cloud. This includes securing data, managing user access, configuring firewalls, encrypting data, and monitoring applications.
Example: In AWS, if you store sensitive data in an S3 bucket, AWS ensures the server is physically and digitally secure, but you must set proper access controls. Many high-profile breaches have occurred simply because S3 buckets were left publicly accessible.
Understanding this distinction is critical. Cybersecurity in the cloud is not automatic. It’s a collaborative effort, and neglecting your end of the bargain leads to serious consequences.
The Consequences of Misunderstanding Cloud Security Service
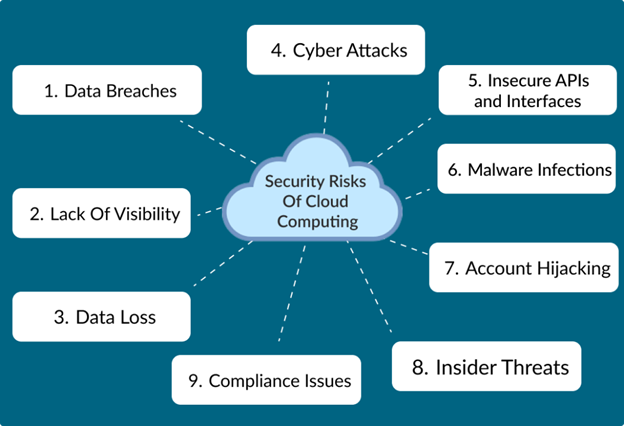
1. Data Breaches Due to Misconfigurations
According to Gartner, “through 2025, 99% of cloud security failures will be the customer’s fault.” Misconfigured storage, poorly defined access controls, and excessive permissions are the main culprits.
Real Case: The Capital One breach (2019) occurred because of a misconfigured web application firewall in AWS, which allowed a hacker to access over 100 million customer records. The breach didn’t stem from AWS but from customer-side vulnerabilities.
2. Shadow IT and Shadow Data
When employees use unauthorized cloud services (Dropbox, personal Google Drive, ChatGPT), your data may live in uncontrolled, unmonitored environments. These shadow IT resources create blind spots that security teams can’t see or control.
3. Lack of Visibility and Logging
Cloud environments are vast and dynamic. Without proper logging and monitoring (e.g., AWS CloudTrail, Azure Monitor), you can’t detect anomalous behavior until it’s too late. Many organizations don’t enable logging by default.
4. Compliance Failures
Cloud compliance frameworks like HIPAA, PCI-DSS, or GDPR demand strict data handling, encryption, and logging standards. Without proper configuration, companies can inadvertently expose sensitive data and incur heavy fines.
Why Traditional Security Tools Don’t Work in the Cloud
Legacy tools such as firewalls, antivirus software, and on-premises intrusion detection systems were designed for static, perimeter-based environments. These tools rely on fixed network boundaries and known traffic patterns to detect threats.
In the cloud, those boundaries no longer exist. Instead:
- Workloads are dynamic: Instances are spun up and terminated rapidly using autoscaling and container orchestration tools.
- Assets are ephemeral: IP addresses and instances are short-lived, making signature-based detection ineffective.

- Traffic is API-driven: Cloud services communicate internally and externally via APIs, not traditional TCP/IP protocols.
- Resources are globally distributed: Data and applications may span multiple regions or availability zones.
These differences render traditional tools inadequate for cloud-native threats like IAM abuse, privilege escalation, insecure APIs, and lateral movement via misconfigured roles. To defend cloud environments, organizations must adopt behavior-based, context-aware, and policy-enforced security that integrates natively with cloud services.
Embedding Security into the Cloud Lifecycle
To build a resilient cloud security posture, security must be woven into every stage of the cloud lifecycle, not simply appended after deployment.
1. Design Phase: Secure-by-Design Architecture
- Zero Trust Principles: Build under the assumption that no user or component is inherently trusted. Apply verification at every access point.
- Segmentation: Use VPCs, subnets, and network ACLs to isolate sensitive workloads and restrict east-west traffic.
- Access Control Policies: Define strict IAM policies and role-based access control (RBAC). Prevent privilege escalation through scoped access.
- Threat Modeling: Conduct early threat modeling to identify data flows, attack surfaces, and high-risk components before writing code.
2. Build Phase: DevSecOps and Infrastructure as Code (IaC)
- Static and Dynamic Analysis: Integrate tools like SonarQube and Snyk into your CI/CD pipelines to catch vulnerabilities in code and dependencies.
- IaC Security: Use IaC scanning tools like Checkov or tfsec to enforce security best practices in Terraform or CloudFormation templates.
- Secrets Management: Avoid hardcoding credentials. Use secret management tools such as AWS Secrets Manager or HashiCorp Vault.
- Policy as Code: Implement Open Policy Agent (OPA) or Azure Policy to enforce guardrails on resource deployment.
3. Deployment and Runtime Phase
- Monitoring and Detection: Use anomaly detection and real-time alerting from cloud-native tools like GuardDuty, Azure Defender, or GCP SCC.
- Data Protection: Enforce encryption using customer-managed keys (CMKs) and HSMs. Monitor key usage and rotate keys periodically.
- Runtime Controls: Deploy agents or sidecars that monitor runtime behavior in containers, serverless, and virtual machines for indicators of compromise (IoCs).
4. Operations and Optimization Phase
- Cloud Security Posture Management (CSPM): Continuously evaluate security configurations against compliance standards and benchmarks (e.g., CIS, NIST).
- Identity Governance: Audit users and service accounts regularly. Use just-in-time access provisioning and activity logging.
- Automated Remediation: Automate responses to misconfigurations or policy violations using serverless functions or workflows.
- Incident Response Readiness: Simulate breach scenarios, maintain runbooks, and establish clear escalation paths.
Cloud-Native Security Tools to Know
Cloud providers offer a growing suite of native security tools tailored to their platforms. Knowing what’s available and how to use it can dramatically reduce risk.
- Amazon GuardDuty: Intelligent threat detection and monitoring using machine learning to identify anomalies.
- AWS Config: Tracks configuration history and compliance of resources. Useful for audits and drift detection.
- AWS Security Hub: Aggregates findings from other services (e.g., GuardDuty, Inspector) into a central dashboard.
- AWS Macie: Automatically classifies and protects sensitive data, such as PII.
- AWS KMS & CloudHSM: Provides encryption and cryptographic key lifecycle management.
Microsoft Azure
- Microsoft Defender for Cloud: Offers vulnerability management, threat protection, and compliance assessment across IaaS, PaaS, and hybrid clouds.
- Azure Key Vault: Manages secrets, certificates, and keys with access control and logging.
- Azure Policy: Enforces organizational standards and compliance across resources with policy-as-code.
- Azure Monitor + Log Analytics: Centralizes logs, metrics, and traces for visibility and diagnostics.
- Microsoft Sentinel: A scalable SIEM and SOAR platform with AI-powered threat detection and automated response.
Google Cloud Platform (GCP)
- Security Command Center (SCC): Centralized threat detection and security posture dashboard for GCP resources.
- Cloud Armor: Web application firewall (WAF) that defends against DDoS and OWASP Top 10 threats.
- Secret Manager: Securely stores and manages access to secrets and credentials.
- Binary Authorization: Enforces image signing and deployment policies for containers.
- Chronicle: Google’s enterprise-level security analytics platform for advanced threat hunting.
When these tools are configured and integrated properly, they provide deep visibility, automated detection, and continuous compliance forming the foundation of a secure cloud environment.
The Future of Cloud Security
The cybersecurity landscape is rapidly evolving. With the rise of:
- Serverless computing (e.g., AWS Lambda)
- Edge computing and IoT
- AI-powered attacks and defenses
- Post-quantum cryptography needs
…security must be agile, automated, and deeply integrated. Organizations that treat security as a checkbox or delay it until the end of deployment cycles will continue to suffer costly breaches. The future belongs to those who bake security in from the first line of code to the final system teardown.
Securing the Future
The cloud is powerful, flexible, and transformative but it is not secure by default. Believing otherwise can result in devastating data breaches, legal penalties, and reputational damage. As the cloud becomes more central to business operations, cybersecurity must become a fundamental design principle, not a last-minute fix.
Companies that embed security into every aspect of their cloud journey will not only avoid breaches but also gain a competitive edge by proving to customers and regulators that their data is safe. In a world where trust is currency, securing your cloud is no longer optional; it’s essential.
Share this :