XSS Vulnerabilities in the Krpano Framework: A Deep Dive into the 360XSS Campaign

Hoplon InfoSec
27 Feb, 2025
Recently, some serious cross-site scripting (XSS) Vulnerabilities were discovered within the Krpano framework—a widely used tool for embedding 360° images and creating immersive virtual tours. This vulnerability, exploited in a campaign dubbed “360XSS,” has affected over 350 websites, ranging from government portals and educational institutions to high-traffic commercial websites. In this blog post, we will explore the technical details of this vulnerability, the methods employed by the attackers, and practical steps developers and website owners can take to protect their sites.
What Is the Krpano Framework?
Krpano is a versatile software solution that creates interactive virtual tours and displays panoramic images. Its ease of use and flexibility have made it popular among photographers, travel agencies, universities, and even corporate organizations. The framework supports embedding high-resolution 360° images and provides an engaging way for users to experience locations virtually. However, as with any software that interacts with the web, security flaws can sometimes arise, and the recent XSS vulnerability is a case in point.
The Nature of Cross-Site Scripting (XSS)
Cross-site scripting (XSS) is a prevalent web security vulnerability that allows attackers to inject malicious scripts into web pages viewed by other users. These scripts can steal sensitive data, hijack user sessions, or spread spam advertisements. The core issue lies in how web applications handle untrusted data—if an application fails to validate or sanitize user input correctly, it becomes susceptible to malicious code injections.
The vulnerability in the Krpano framework centers on how the software processes specific URL parameters. Specifically, the “XML” parameter, which is intended to specify the location of external XML configuration files, became an unintended vector for malicious code.
How the XSS Vulnerabilities Was Exploited
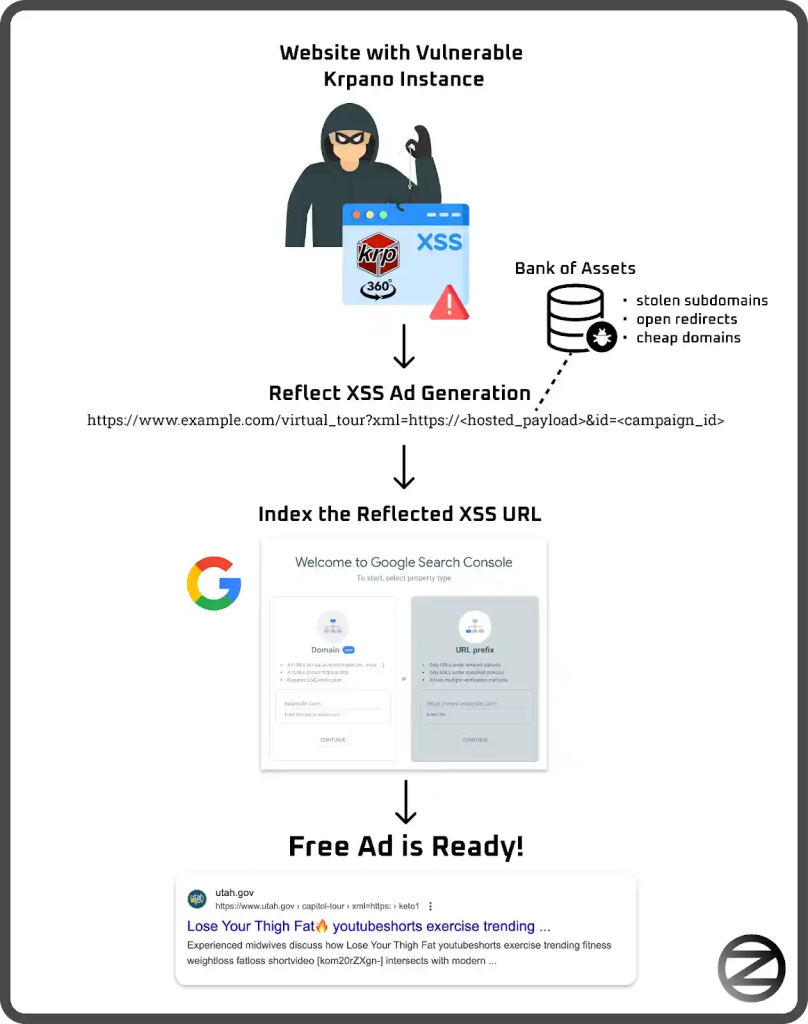
Security researcher Oleg Zaytsev first identified the anomaly when encountering a suspicious advertisement on a Google Search result. The ad, which led to a Yale University domain, redirected users to a pornography site. This unexpected redirection raised alarm bells, prompting further investigation into the underlying mechanics of the attack.
Zaytsev’s research revealed that the affected Yale University subdomain was running the Krpano viewer. The root of the vulnerability was traced back to the improper handling of the “XML” parameter in the URL. Under normal circumstances, this parameter should merely point to an external XML file containing configuration data. However, attackers discovered that by crafting a specially designed URL, they could manipulate the parameter to include a Base64-encoded payload. When processed by the Krpano viewer, this payload would redirect visitors to another website and execute malicious scripts on the fly.
The malicious scripts injected by the attackers were not benign. They served as vehicles to distribute spam advertisements, promoting dubious products and services such as pornography, diet supplements, and online casinos. In some instances, these hijacked pages were exploited to artificially boost YouTube view counts, further amplifying the campaign’s reach.
The 360XSS Campaign: A Widespread Threat
The scope of the 360XSS campaign is staggering. With over 350 websites affected, the attackers infiltrated various online platforms. The compromised sites included small and medium-sized websites and major institutions like government agencies, state government portals, universities, hotel chains, news outlets, car dealerships, and Fortune 500 companies. Many websites enjoy millions of monthly visitors, significantly increasing the malicious ads’ potential damage and reach.
A particularly troubling aspect of the campaign is its use of search engine optimization (SEO) poisoning. By injecting fake review counts and star ratings and optimizing the malicious links, the attackers ensured that their content appeared prominently in search engine results. This tactic, known as SEO poisoning, not only deceives users into clicking on harmful links but also undermines the trustworthiness of reputable websites. In one notable example, a fake article promoting online casinos was injected directly into CNN’s website. Similarly, Pakistan’s most prominent news site, geo.tv, fell victim to the same technique, further highlighting the severity of the threat.
Technical Breakdown of the Vulnerability
At the heart of this security flaw is a configuration setting known as “passQueryParameters.” This setting, when enabled, allows HTTP parameters from the URL to be passed directly to the Krpano viewer without sufficient validation. While this feature is intended to offer flexibility by enabling dynamic content loading, it inadvertently opens the door to XSS attacks when not handled correctly.
The Krpano development team updated version 1.20.10 to address this vulnerability, restricting the “passQueryParameters” functionality to an allowlist. However, reintroducing the XML parameter onto the allowlist unintentionally reintroduced the risk of XSS. This oversight underscores the challenges developers face when balancing user convenience with security.
The exploitation process itself involved several technical steps:
- Crafting the URL: The attacker created a URL that contained a malicious “xml” parameter. Instead of pointing to a benign configuration file, this parameter included a Base64-encoded payload.
- Redirection and Payload Execution: When a user visits the compromised URL, the Krpano viewer decodes the payload embedded in the XML parameter. The decoded data then triggered a redirection to a malicious website, where further code execution occurred.
- Injection of Malicious Scripts: Once redirected, the malicious website would serve additional scripts that injected harmful code into the original webpage. These scripts altered the page’s content and served up spam advertisements and other malicious content.
The attackers bypassed conventional security measures by exploiting the “passQueryParameters” configuration and seamlessly injected their payload into the affected websites.
The Impact on SEO and Online Trust
One of the 360XSS campaign’s more insidious aspects is its impact on search engine results. By leveraging SEO poisoning tactics, attackers could exploit the credibility of compromised domains. The malicious links were designed to mimic legitimate content, complete with fake review counts and star ratings. As a result, when users searched for related terms on popular search engines like Google, these poisoned links were among the top results.
This form of SEO manipulation not only misleads users but also tarnishes the reputation of the affected websites. For instance, users expecting to find authoritative information on well-known news platforms or educational websites might instead be confronted with links leading to disreputable sites or explicit content. The undermining of trust is particularly harmful in sectors such as government and academia, where credibility is paramount.
Moreover, the widespread attack means many internet users could be inadvertently exposed to malicious content. The ripple effects extend far beyond individual websites, affecting the overall web ecosystem and the reliability of search engine results.
Best Practices for Developers and Website Owners

After the 360XSS campaign, developers and website administrators must adopt robust security practices. Here are some essential steps that can help mitigate the risk of similar vulnerabilities:
Updating to the Latest Software Version
The most immediate action is to update the Krpano framework to version 1.22.4 or later. This update eliminates support for external configuration via the XML parameter, effectively mitigating the risk of XSS attacks. Keeping software up to date is fundamental in web security, as patches and updates often address known vulnerabilities.
Turning off Unnecessary Parameters
Website owners should review their configuration settings, particularly the “passQueryParameters” setting. This parameter is highly recommended to be set to “false” unless there is a compelling reason to enable it. Limiting the amount of data passed directly through URL parameters significantly reduces the attack surface.
Implementing Strict Input Validation
Developers should implement comprehensive input validation and sanitization routines. Any data received from external sources, including URL parameters, must be treated as untrusted. Utilizing robust validation frameworks can help prevent malicious code from being executed on the server or client side.
Regular Security Audits
Regular security audits are vital for identifying potential vulnerabilities before they can be exploited. Engaging third-party security experts to perform penetration testing can reveal weaknesses internal teams might overlook.
Monitoring and Removing Infected Pages
Website owners are also advised to use tools such as Google Search Console to monitor their sites for signs of infection. If malicious content is detected, prompt action should be taken to remove the compromised pages and clean up any injected scripts.
Educating Teams on Security Best Practices
Finally, fostering a culture of security awareness within development teams is essential. Regular training on secure coding practices and emerging threats can empower developers to write more secure code and respond effectively to potential incidents.
The Role of Responsible Disclosure
The discovery and subsequent mitigation of the XSS vulnerability in Krpano serve as a testament to the importance of responsible disclosure. Security researcher Oleg Zaytsev was pivotal in identifying the flaw and alerting the developers. Responsible disclosure involves privately notifying the affected vendor about the vulnerability, allowing them sufficient time to develop and release a fix before the details are publicized.
This approach minimizes attackers’ window of opportunity and helps maintain public trust in affected software. By following responsible disclosure protocols, researchers like Zaytsev ensure that vulnerabilities are addressed, controlled, and systematically. Cooperation between security experts and software developers is crucial for building a safer digital environment.
Broader Implications for Web Security

The 360XSS campaign is a stark reminder of the ever-evolving nature of web threats. While XSS vulnerabilities have been known for years, attackers continually refine their techniques to exploit even minor oversights in code. This incident underscores several key lessons for the broader web development community:
The Need for Continuous Vigilance
Web security is not a one-time task. With new vulnerabilities emerging regularly, developers and security teams must remain vigilant. Regular updates, audits, and adherence to best practices are the cornerstones of a robust security strategy.
The Importance of Secure Configuration
Even features designed to enhance functionality, such as the “passQueryParameters” setting in Krpano, can become liabilities if not properly secured. Developers must strike a delicate balance between providing flexible features and ensuring that these features do not open new avenues for attack.
Collaboration Between Developers and Researchers
Successfully mitigating this vulnerability highlights the value of collaboration between software developers and the security research community. These groups can significantly reduce the risk of widespread exploitation by sharing insights and working together.
Educating End Users
Finally, website owners and end users must be educated about the risks of web vulnerabilities. Awareness campaigns, tutorials, and precise documentation can empower non-technical stakeholders to safeguard their online assets proactively.
Conclusion
The 360XSS campaign represents a significant challenge for web security professionals and website owners. By exploiting a vulnerability in the Krpano framework, attackers could inject malicious scripts into hundreds of websites, manipulate search engine results, and distribute spam advertisements to a vast audience. The incident underscores the importance of maintaining up-to-date software, enforcing strict input validation, and remaining vigilant in the face of evolving cyber threats.
Developers are encouraged to upgrade to the latest version of Krpano, turn off unnecessary features such as the “passQueryParameters” setting, and perform regular security audits. Website owners should use available tools to monitor and clean their sites, ensuring that any compromised pages are swiftly removed. The collaborative efforts between security researchers and developers, exemplified by the responsible disclosure of this vulnerability, demonstrate that a coordinated approach is essential in combating cyber threats.
In a digital ecosystem where trust and reliability are paramount, every stakeholder—from individual developers to large organizations—has a role in safeguarding web applications. By understanding the technical details of vulnerabilities like the one found in Krpano and adopting robust security practices, we can work together to build a safer, more secure online environment for everyone.
This incident serves as a learning opportunity and a call to action. As new threats emerge and attackers continue to innovate, the importance of web security can never be overstated. Whether you are a developer, a security professional, or a website owner, taking proactive steps to secure your web presence is essential. Let the lessons learned from the 360XSS campaign guide your efforts in creating and maintaining secure digital experiences.
For more:
https://cybersecuritynews.com/hackers-exploited-xss-vulnerability-framework/
Share this :