In June 2025, the Cybersecurity and Infrastructure Security Agency (CISA) released a chilling warning: ransomware actors had been targeting U.S. utility billing providers since at least January by exploiting a critical vulnerability, CVE‑2024‑57727 in the remote management software SimpleHelp. These attacks led to data exfiltration, service disruptions, and large-scale outages. The incident underscores the increasing risk that unpatched or poorly monitored remote management tools pose to the stability and security of critical infrastructure.
Remote Monitoring and Management (RMM) tools are essential for maintaining IT environments across enterprises, but their extensive access and privileges make them double-edged swords. When compromised, these tools can be weaponized by cybercriminals to orchestrate widespread attacks, gain persistent access, and deploy ransomware. The exploitation of SimpleHelp is a textbook case in how a single weak point can become a national risk when it sits at the heart of utility operations.
Understanding SimpleHelp RMM and CVE‑2024‑57727

What Is SimpleHelp RMM?
SimpleHelp is a cross-platform remote access and management tool designed to allow IT administrators to remotely control and support systems. Widely used by managed service providers (MSPs) and internal IT departments, SimpleHelp enables tasks like remote desktop sessions, diagnostics, software deployment, and system monitoring, all critical in modern IT operations.
Anatomy of the Vulnerability
CVE‑2024‑57727 is a severe unauthenticated path traversal vulnerability found in SimpleHelp versions 5.5.7 and earlier. The flaw allows an attacker to craft malicious HTTP requests to retrieve arbitrary files from the host system files that may contain sensitive configuration data, SSH keys, system password hashes, logs, and more.
What makes this vulnerability so dangerous is that it does not require authentication. An attacker does not need valid credentials to exploit it; they simply need to find an internet-exposed SimpleHelp server and send a specially crafted request using directory traversal techniques like ../../. This opens the door for reconnaissance, credential theft, and ultimately full system compromise.
Timeline and Emergence of Exploitation
Initial Discovery and Weaponization
Although the vulnerability existed earlier, exploitation began gaining traction in early January 2025. Security researchers and threat hunters started noticing a pattern of abnormal file requests being made to SimpleHelp endpoints. Attackers were leveraging the /allversions endpoint to identify software versions and then using the traversal flaw to retrieve system files from the root directory.
Once confirmed, CVE‑2024‑57727 was publicly disclosed and given a CVSS score of 9.8, placing it in the “critical” range due to its ease of use, lack of authentication requirement, and the potential impact of successful exploitation.
Involvement of Ransomware Gangs
Threat actors including well-known ransomware groups such as Play and DragonForce were quick to take advantage of this vulnerability. These groups are notorious for their double extortion tactics: encrypting victims’ data and simultaneously threatening to leak sensitive information if a ransom is not paid. In many reported cases, attackers accessed customer billing information, account data, and utility service records through breached SimpleHelp servers.
Impacts on U.S. Utility Billing Providers
Data Breach and Extortion Scenarios
Utility billing providers are integral to the operation of water, power, and waste management services. When these systems are compromised, customers may face delayed billing, inaccurate usage data, and even interruptions to essential services. By accessing billing records, attackers not only exfiltrate personally identifiable information (PII) but also disrupt the software logic that calculates rates, processes payments, and schedules maintenance.
In several confirmed cases, the attackers used stolen credentials to pivot further into the network. From there, they deployed ransomware, encrypted files, and demanded payments from providers already under pressure from customers and regulators.
Widespread Service Disruptions
The true cost of these breaches extends beyond stolen data. Providers affected by the breach were forced to shut down systems, disconnect servers, and rebuild compromised infrastructure, sometimes from scratch. This led to outages lasting several days in some regions, causing billing delays and interrupting support services for thousands of customers. In many cases, billing departments had to revert to manual processes, significantly slowing down operations and increasing the likelihood of human error.
How the Exploitation Works
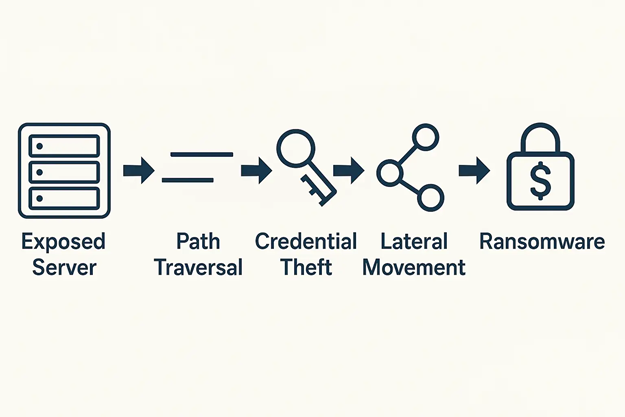
From Initial Access to Full Compromise
The attack chain typically starts with the identification of internet-facing SimpleHelp servers using tools like Shodan or Censys. Attackers then query the /allversions endpoint to determine if the instance is running a vulnerable version. If confirmed, they issue HTTP requests with encoded directory traversal paths
(e.g., ../../../../etc/passwd) to pull system files.
Files like serverconfig.xml often contain administrative credentials in plaintext or easily reversible formats. Once credentials are harvested, attackers can log into internal systems, escalate privileges, disable antivirus or endpoint detection systems, and finally execute ransomware payloads.
Indicators of Compromise (IoCs)
Organizations have reported the presence of unauthorized file access in system logs, unexpected execution of suspicious binaries (notably aaa.exe), and lateral movement across internal subnets. These signs often go unnoticed until the ransomware payload encrypts key files and displays a ransom note. By then, data has usually already been exfiltrated.
CISA’s Response and Mitigation Strategies

Emergency Advisory and KEV Inclusion
On June 12, 2025, CISA issued a formal advisory (AA25-163A) addressing the active exploitation of CVE‑2024‑57727. It also added the flaw to its Known Exploited Vulnerabilities (KEV) catalog earlier in February, reinforcing its urgency. The agency called on all federal agencies and private critical infrastructure providers to immediately assess, isolate, and patch all affected systems.
CISA emphasized that any systems running vulnerable versions of SimpleHelp should be disconnected from public networks if patching is not immediately possible. It also recommended threat hunting for IoCs, backing up all data offline, and implementing network segmentation to reduce lateral movement risk.
Recommended Mitigation Steps
CISA’s mitigation guidance includes identifying all SimpleHelp RMM servers and clients, upgrading to the latest version, disabling unnecessary remote access services, and enforcing multi-factor authentication (MFA) wherever possible. Additionally, organizations are advised to implement strict firewall rules and intrusion detection signatures to catch traversal-based access attempts.
RMM Software and Supply Chain Risk
The Double-Edged Nature of RMM Tools
RMM tools, while essential for managing IT infrastructure, represent a significant security liability if not properly secured. These tools have extensive access to systems, including root or admin privileges, the ability to push updates, execute scripts, and retrieve logs or credentials. This makes them an attractive vector for ransomware groups aiming for large-scale impact with minimal effort.
The exploitation of SimpleHelp highlights how RMM tools can act as a force multiplier for threat actors. By compromising one central system, attackers can reach hundreds, if not thousands, of downstream clients who rely on the software for daily operations.
The Broader Impact on Supply Chains
This incident also raises questions about software supply chain integrity. Many utility billing providers incorporate SimpleHelp as part of third-party vendor packages, often without full visibility into its versioning or security posture. As a result, organizations may be unknowingly running vulnerable software, with neither the expertise nor the permissions to patch it directly.
Securing Critical Infrastructure in a Post-SimpleHelp World
Revisiting Vendor Trust and Zero Trust Architectures
The fallout from the SimpleHelp exploitation is a wake-up call for all sectors relying on remote access software. It’s no longer sufficient to assume that third-party tools are secure by default. Organizations must conduct regular software audits, require vendors to meet security baseline standards, and reduce the attack surface by limiting external access to internal systems.
Implementing a Zero Trust model where access is continuously verified based on identity, behavior, and context can significantly reduce the risk of lateral movement in case of a breach. By isolating systems and requiring granular permissions, the blast radius of an exploit like CVE‑2024‑57727 can be minimized.
Building Resilience Through Visibility and Backups
One of the core lessons from this event is the importance of maintaining full visibility into all software running within the environment. Having an accurate asset inventory, regular vulnerability scanning, and automated patch management are essential components of a secure IT strategy.
Moreover, organizations must ensure that backup systems are air-gapped and regularly tested. Offline backups remain one of the few effective mitigations against ransomware, allowing companies to restore services without succumbing to extortion.
Conclusion

The exploitation of CVE‑2024‑57727 in SimpleHelp RMM serves as a stark reminder that even widely trusted tools can become significant liabilities if not properly secured and maintained. The attacks on U.S. utility billing providers reveal how a single vulnerability in remote management software can disrupt critical services, compromise sensitive data, and empower ransomware actors to scale their operations.
As cyber threats evolve, so must the defenses of organizations entrusted with managing essential infrastructure. Vigilance, rapid patching, supply chain scrutiny, and resilience planning are not just best practices; they are necessities. The next major attack may already be brewing in an overlooked third-party tool, and the time to act is now.
Did you find this article helpful? Follow us on Twitter and LinkedIn for more Cyber Security news and updates. Stay connected on Facebook and Instagram as well. At Hoplon Infosec, we’re committed to securing your digital world.




