UK Government's Enhanced Cybersecurity Measures Explained

Hoplon InfoSec
25 Oct, 2025
The UK woke up to a sharper, louder warning: cyber threats are not a distant headline; they are a daily pressure on hospitals, factories, banks, and the services we all take for granted. The UK Government's Enhanced Cybersecurity Measures are not a nice-to-have policy paper. They are a response to real incidents that froze production lines, exposed millions of records, and forced ministers to say publicly that business as usual will not cut it anymore.
Why this matters now
When a country says it is enhancing its defenses, you should listen. The UK Government's Enhanced Cybersecurity Measures are being shaped by an increase in sophisticated attacks, many of them state-backed or highly organized criminal operations that move faster and hit harder than before.
That change in scale pushed ministers to draft sweeping reforms, update regulatory expectations, and demand faster reporting when things go wrong. These steps are meant to protect essential services and to shore up the supply chains that underpin our digital economy.
What the new measures actually are: a plain-language tour
At the center of the changes is a package of policies and a new bill that together aim to modernize old rules and bring more parts of the economy into view. The headline items include stronger rules for critical suppliers, shorter deadlines for incident notification, wider coverage so data centers and managed service providers are regulated, and clearer expectations on supply chain security. The design is to make sure the places that support hospitals, energy, and transport can withstand and recover from attacks without taking the whole country down with them.
One concrete change is a proposed two-stage incident reporting requirement: notify regulators and the National Cyber Security Centre quickly, then follow up with detailed information. That shift pushes firms to move from slow, internal-only reactions to coordinated, timely disclosure. It also gives defenders better early warning and helps stop bigger cascades of harm.
The law behind the measures: Cyber Security and Resilience Bill
The legislative backbone is the Cyber Security and Resilience Bill. Announced in the King’s Speech and laid out in a policy statement, the bill updates the older NIS framework and aims to future-proof UK rules against new threats. Expect wider powers for regulators, clearer duties on suppliers, and mechanisms to update technical standards more quickly as threats evolve. The bill is intended to be practical: not just lofty language, but enforceable duties, fines, and obligations that nudge behavior across industries.
The evidence driving change
This is not theoretical. The National Cyber Security Centre’s recent reviews and public reporting show a steep rise in nationally significant incidents, including attacks that damaged operations and disclosed sensitive data.
Examples over the last two years include major supply chain-related breaches and high-impact ransomware attacks that affected well-known firms and service providers. Those events have been used as proof points by policymakers pushing the UK government's enhanced cybersecurity measures.
One recent real-world episode that fed public debate involved a large outsourcing firm fined after a breach that exposed millions of records and tested regulatory patience. Cases like that illustrate the cost of inaction and help explain why courts, regulators, and ministers are pressing for tighter rules and clearer accountability.
What this means for businesses: the human, practical side
If you run a business that touches public services, hosts customer data, or supplies critical infrastructure, this will change how you operate. The UK government's enhanced cybersecurity measures mean organizations must sharpen incident response playbooks, map second- and third-tier suppliers more carefully, and be ready to show auditors and regulators that the right controls exist and work. This is not just an IT task; it is a board-level responsibility.
Think of it like preparing a city for flooding. You do not wait for water in the streets. You reinforce embankments, plan evacuation routes, and run drills. The same logic applies to cyber: containment, recovery, and rehearsed communications reduce panic and economic harm when an attack hits.
Supply chain security: the weak link the new rules target
One of the clearest lessons from recent breaches is that attackers exploit suppliers. A small contractor with lax security can be the route into a national service. The new measures put explicit pressure on companies to verify the security posture of their vendors and to demand demonstrable standards from partners. That could mean contractual clauses, minimum technical requirements, or mandatory audits for suppliers playing a role in essential services.
For smaller suppliers this is a challenge. They will need support, guidance, and sometimes investment to meet higher expectations. Governments and industry groups often recognize that and sometimes pair regulation with help programs. The policy signals make it clear: no more easy backdoors through weak partners.
Technology and practice: what good looks like
Practically, effective cyber resilience mixes people, processes, and technology. You need logging and detection that work, clear crisis leadership, and rehearsed communication with regulators. You also need basic hygiene: multi-factor authentication, timely patching, good asset inventories, and segmenting networks so an intruder cannot roam freely.
The National Cyber Security Centre offers guidance and toolkits for boards and operational teams. Following those playbooks and aligning with expected standards will make demonstrating compliance simpler and less stressful when inspectors come calling.
Balancing security with growth and innovation
A common criticism of heavy regulation is that it stifles innovation. The UK government's enhanced cybersecurity measures acknowledge that tension. The policy language tries to balance resilience with growth, for example, by offering scope for proportionate requirements and tools to update the rules quickly as threats change, rather than locking in rigid standards that become obsolete. That flexibility aims to protect innovation while closing the most dangerous gaps.
The Government Cyber Security Strategy: source
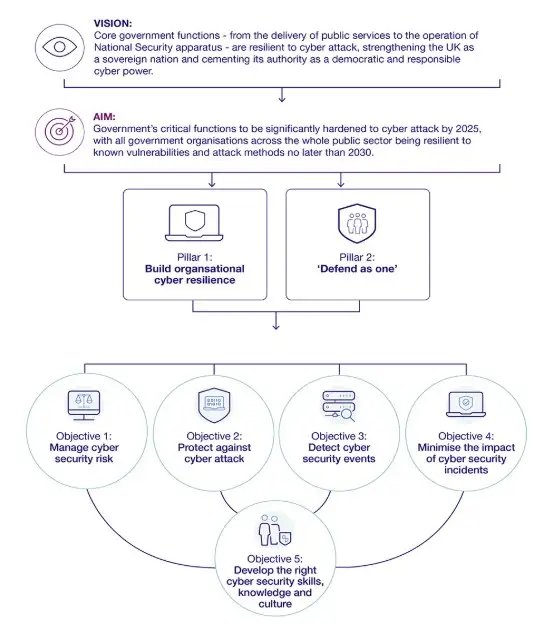
Real people, real stories: why leaders are changing tune
I once spoke with a CIO at a mid-size hospital who described waking at three in the morning to an alert that patient records were being encrypted. The hospital’s response was messy: phones were held up, staff improvised workarounds, and public confidence wobbled. The new measures are meant to stop that kind of chaotic recovery to make sure organizations have rehearsed plans and clear obligations so that the first instinct is recovery, not cover-up.
These reforms are less about blame and more about readiness. They shift incentives: be prepared, and you avoid the worst economic and human impacts. Be unprepared, and the reputational, financial, and operational consequences can be severe.
What citizens should expect
As a citizen, you will likely see three things: stronger statements from regulated organizations that they are meeting new standards, more transparent incident reporting when things go wrong, and targeted government action when national risks emerge. Ideally, this means quicker notices about breaches that might affect you and better protection for services you rely on.
It also means that companies may ask more of you in terms of security: stronger authentication, clearer privacy choices, and sometimes temporary disruptions while firms harden systems. Those are minor inconveniences compared with the cost of a compromised hospital or halted energy supply.
Practical steps organizations can take today
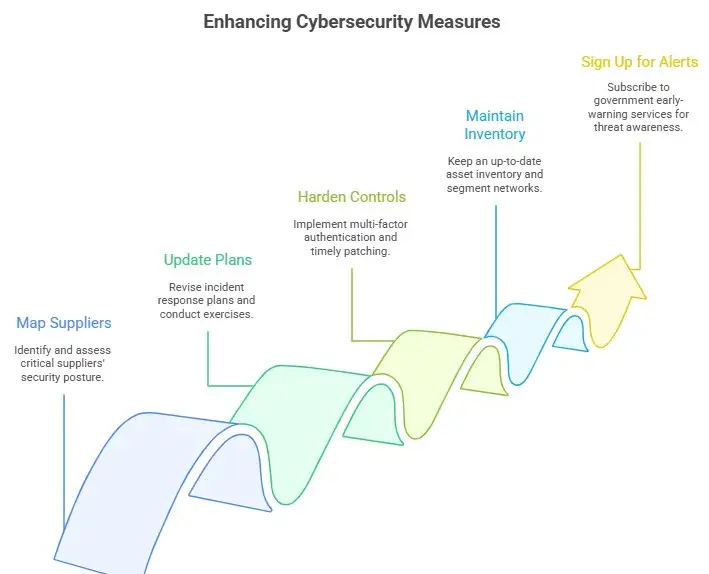
Here are concrete actions to start with, informed by the NCSC and the new policy directions:
1. Map your critical suppliers and ask for evidence of their security posture.
2. Update incident response plans, run tabletop exercises, and rehearse reporting to regulators.
3. Harden identity and access controls, enforce multi-factor authentication, and maintain timely patching.
4. Keep an up-to-date asset inventory and segment networks to limit lateral movement.
5. Sign up for government early-warning services and threat feeds to get faster situational awareness.
The politics and economics: why governments act
Cybersecurity is now national economic security. Attacks that disrupt supply chains or key industries carry political consequences. That is why the UK Government's Enhanced Cybersecurity Measures include both carrots and sticks: support for the cyber sector, alignment with industrial strategy, and, where needed, regulatory teeth such as fines or mandatory reporting. This blend aims to raise baseline security without permanently denting the country’s competitiveness.
A short, realistic prognosis
This is not a magic fix. Rules change incentives and raise the bar, but attackers adapt. Expect a period where organizations scramble to comply, regulators fine a few high-profile laggards, and the overall resilience gradually improves. Over time, the aim is a stronger ecosystem where supply chains are cleaner, incidents are contained earlier, and recovery is faster.
Closing takeaway: what to do if you care about resilience
If you care about resilience in your organization, treat these reforms as an opportunity, not just a compliance headache. Use the momentum to strengthen basic hygiene, to invest in people and training, and to build relationships with peers and government channels that make response faster.
The UK government's enhanced cybersecurity measures are a nudge—a big one—toward a safer, more dependable digital infrastructure. Get ahead of the curve, and you not only avoid penalties but also protect customers, staff, and your reputation.
Final note
Regulation alone will not stop every attack, but it changes the environment. The bill, the updated NCSC guidance, and the clearer expectations for suppliers are a step toward a more resilient UK. For leaders, the task is simple to state and hard to execute: treat cyber like a board-level risk, rehearse your response, and be honest and fast when things go wrong. That combination will keep services running and people safe.
Follow us on X (Twitter) and LinkedIn for more cybersecurity news and updates. Stay connected on YouTube, Facebook, and Instagram as well.
Share this :