Web Application Security Testing
What is Web Application Security Testing?
Web Application Security Testing is the process of examining a web application to identify vulnerabilities that could be exploited by malicious attackers. This testing aims to uncover security flaws such as SQL injection, cross-site scripting (XSS), broken authentication, and insecure data storage, among others.
By detecting these weaknesses early, organizations can fix them before they are exploited, helping to protect sensitive data and maintain user trust. The testing process typically involves both automated tools, which quickly scan for common vulnerabilities, and manual techniques, where security experts simulate attacks to find more complex issues.
In one sentence, web application security testing services are some critical steps in ensuring that web applications remain safe and resilient against cyber threats.

Key Features of Web Application Security Testing
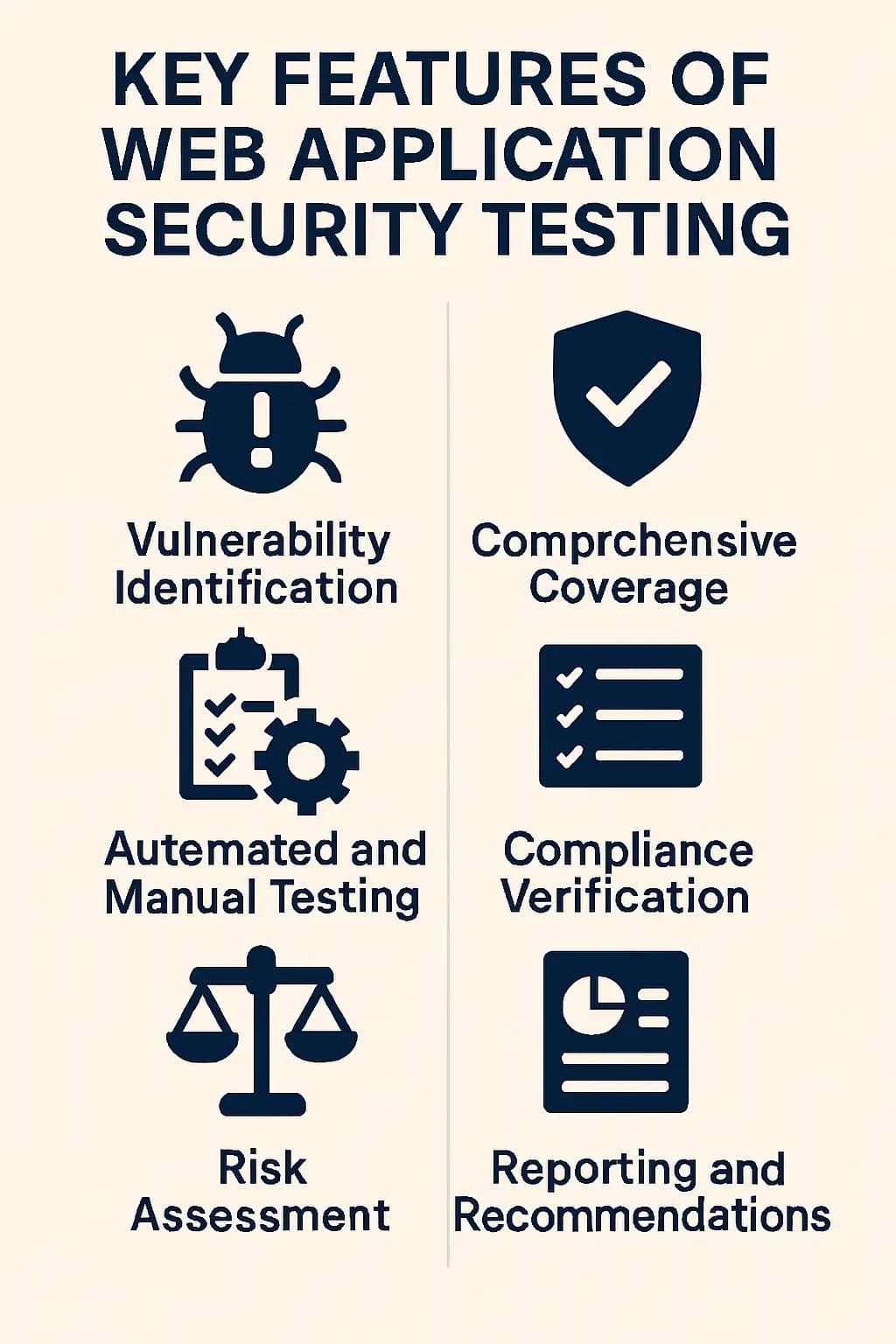
Why Web Application Security Testing is Important?

How Does Web Application Security Testing Work?

Why Hoplon?
Frequently Asked Questions
Everything you need to know about Web Application Security Testing
We're Here to Secure Your
Hard Work
Protect your system from cyber attacks by utilizing our comprehensive range of services. Safeguard your data and network infrastructure with our advanced security measures, tailored to meet your specific needs. With our expertise and cutting-edge technology, you can rest assured that your system is fortified against any potential threats. Don't leave your security to chance – trust our proven solutions to keep your system safe and secure.
Share this :