The Massive Password Exposure Crisis: Inside the 16 Billion Credential Leak

Hoplon InfoSec
20 Jun, 2025
In June 2025, cybersecurity researchers made a stunning discovery: over 16 billion passwords were found exposed in the open, collected across multiple unsecured databases and cloud instances. These weren’t tied to a single company’s failure. Instead, they originated from thousands of malware-infected devices, then dumped together into massive archives online, some left open without any protection.
This discovery has raised alarms across the internet. With stolen credentials readily available and increasingly fresh, attackers don’t need to “hack” into your accounts. They just log in, using your actual password. And when this scenario happens at scale, it creates the conditions for identity theft, corporate compromise, and fraud on a global level.
This article breaks down what happened, why it matters, and what every internet user can do now to stay protected.
What Really Happened: The Anatomy of the 16 Billion Credential Exposure
This incident was not a hack; rather, it was a massive harvest of stolen credentials.
Unlike a breach of a single company’s database, this password exposure was the result of data aggregation, an enormous pile of stolen credentials gathered through malicious software known as infostealers. These are lightweight, stealthy malware that infect devices, usually after the user unknowingly downloads a fake program or clicks a suspicious link.
Once installed, the infostealer quietly searches for various types of sensitive information:
- Saved login credentials from browsers like Chrome or Firefox
- Autofill form data
- Session cookies (which keep users logged in)
- FTP tools, VPN clients, and even some email clients save passwords.
This data is then sent to a command-and-control server. From there, it’s either sold on underground markets or compiled into massive databases like the one discovered in this incident.
Discovered by Researchers, Not hackers.
The exposed credentials came to light when cybersecurity researchers found more than 30 publicly accessible databases, mostly on cloud platforms like Elasticsearch, MongoDB, and Amazon S3. These databases lacked passwords and access controls, making it possible for anyone with the right knowledge to download their contents.
Many of the records were fresh, meaning they had been collected in the past year or less. This increases their danger significantly, as many users still actively use the same login details, especially if they reuse passwords across multiple platforms.
Scope and Scale: How Big Is 16 Billion?
To understand the gravity of the situation, consider this: Earth has roughly 8 billion people. So, a pool of 16 billion passwords means there are likely multiple sets of credentials per person for different platforms, accounts, and services.
This does not imply that the data affected 16 billion unique individuals. In reality, some records are duplicates or linked to bots. However, the raw volume, combined with the freshness and exposure of the data, makes this one of the largest digital identity exposures ever discovered.
The databases included:
- Email addresses
- Passwords (many in plaintext)
- Associated websites and login portals
- Geographic and browser fingerprint data
This kind of dataset is a goldmine for cybercriminals, especially when combined with automation tools and credential stuffing scripts.
Why It Matters: Consequences Beyond Just Passwords
Credential Stuffing: The Silent Epidemic
Credential stuffing is an attack method where criminals take known username-password pairs and test them on hundreds of different websites automatically. This is extremely effective because so many people reuse the same password across multiple sites.
For instance, attackers may attempt to log into a user’s PayPal, Amazon, or work email accounts using their stolen Netflix credentials. If successful, the consequences can range from financial fraud to full corporate system breaches.
Business and Corporate Threats
Corporate logins, particularly remote access tools like VPNs and Microsoft 365 portals, are often associated with stolen credentials. An attacker can use a stolen business email account to impersonate employees, divert wire transfers, or send phishing emails that compromise an entire organisation.
This kind of internal compromise is extremely difficult to detect, especially if attackers use real credentials and behave like legitimate users. Companies often don’t realise what’s happened until money has already been stolen or confidential data has been leaked.
Rise in Phishing and Impersonation
Even if attackers don’t directly use a stolen password, they can weaponise the data to create highly personalised phishing attacks. These are far more convincing than generic spam. If an attacker knows your username, email address, and login activity, they can craft fake messages that look authentic.
Examples include:
- Fake password reset emails
- Security alerts that mimic real services
- These messages reference your actual login history.
These scams trick users into clicking malicious links or entering additional credentials, leading to even deeper compromise.
Real-World Impact: Not Just a “Cyber” Problem
The ripple effects of such exposures are already being felt.
In previous years, attackers used similar credential compilations to breach services like Dropbox, LinkedIn, and Yahoo. More recently, corporate ransomware attacks have begun with valid login credentials, not brute-force hacking.
Take the Colonial Pipeline ransomware incident in the U.S., which began with a compromised VPN account that lacked multi-factor authentication. Or consider the Uber breach, where attackers used stolen passwords to bypass access controls and reach critical systems.
These aren’t isolated cases. As more credentials flood the dark web, attackers are focusing less on hacking and more on logging in using your password.
Who Should Be Worried?
Every Internet User
If you use the internet for email, banking, social media, or shopping, you’re a potential target. Even if you’ve never experienced direct hacking, a breached website or malware-infected device could potentially harvest your passwords.
Employees and professionals.
Work accounts are especially valuable. Attackers may not care about your personal Netflix password, but they’ll gladly use your Microsoft Teams or Slack login to impersonate you inside your company. Remote work setups have only increased this risk.
Businesses and Governments
Organisations that fail to enforce strong password policies or multifactor authentication are especially vulnerable. A single compromised credential could allow attackers to move laterally through networks, access sensitive data, or disrupt services.
What You Can Do: Practical Steps to Protect Yourself
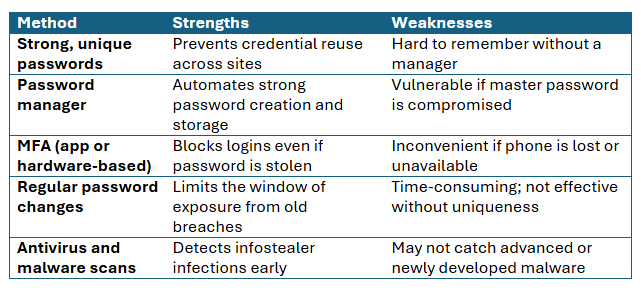
Use a Password Manager.
A password manager helps generate, store, and autofill strong, unique passwords for every account. This ensures that if one site is breached, your other accounts remain safe.
Avoid writing passwords down, using browser autofill alone, or reusing passwords across platforms. Popular password managers include Bitwarden, 1Password, Dashlane, and Keeper.
Enable Multi-Factor Authentication (MFA).
Always enable MFA wherever it’s offered. MFA adds a second step to your login—like a code from an app or hardware key. Even if an attacker has your password, they won’t get in without that second factor.
Avoid relying on SMS codes alone. Instead, use app-based tools like Google Authenticator, Microsoft Authenticator, or Authy. For higher security, consider hardware keys like YubiKey.
Scan Your Devices for Malware
Infostealer malware often runs silently in the background. Use trusted antivirus software and run full scans regularly. If your system has been infected in the past, assume your saved passwords were compromised.
Look for unusual system behaviours, unauthorised logins, or browser extensions you didn’t install. Removing the malware is only the first step—you must also reset your passwords afterwards.
Check for Breaches.
Use services like:
- https://haveibeenpwned.com
- Your password manager’s breach report tools
These services let you check if your email or password has appeared in known leaks. Additionally, they can alert you if another breach uncovers your credentials.
Comparing Credential Protection Strategies
The Big Picture: What This Means for the Future
The exposure of 16 billion credentials is not just an isolated incident; it’s a warning shot. As attackers shift from brute-force hacks to data-driven infiltration, our digital identities become the new perimeter. This means traditional firewalls and antivirus tools aren’t enough. We need better authentication, greater user awareness, and company-wide policies that prioritise digital hygiene.
It also means governments and enterprises must act fast. Real-time monitoring, threat intelligence, and proactive user education must complement regulatory compliance, despite its importance. For users, digital safety is no longer optional. Just like you lock your front door at night, you need to lock down your digital identity with strong passwords, multi-factor protection, and regular security check-ups. To know more about tips and tricks on Digital Security you can book consultancy or read our blogs also can connected us.
Conclusion: One Exposure, Billions at Risk
The discovery of over 16 billion exposed passwords may not have come from a single breach, but its implications are just as severe. This serves as a global alert. In a world where malware quietly collects your most private credentials and dumps them into public databases, inaction is the greatest risk.
From casual internet users to Fortune 500 executives, everyone shares responsibility in securing their digital footprint. In today’s internet, the question has shifted from “Have I been breached?” to “What will I do when I am?”
The tools to stay safe are already in your hands. Now is the time to use them.
Resources:
Business Stndard
Forbes
Share this :