23andMe Hacked: Ancestry Data Breach Sparks Privacy and Trust Concerns
Hoplon InfoSec
19 Jun, 2025
In a digital era where data defines identity and influences opportunity, no type of information is more personal or permanent than genetic data. That reality became chillingly clear between June 17 and 18, 2025, when regulators from Canada and the United Kingdom released the results of a cross-border investigation into 23andMe’s 2023 data breach. What was once viewed as a technical mishap has now erupted into a full-scale privacy crisis, revealing that the genetic data of more than 7 million people also DNA ancestry was compromised due to the company’s failure to implement adequate safeguards.
Unlike a stolen password or credit card number, genetic data cannot be changed. It is immutable and hereditary, making this breach not just a privacy violation but a deeply personal, bioethical, and potentially generational threat. The fallout has already resulted in regulatory penalties, class action lawsuits, and a collapsing foundation of consumer trust.
What Happened? Anatomy of the 23andMe’s Ancestry Data Breach
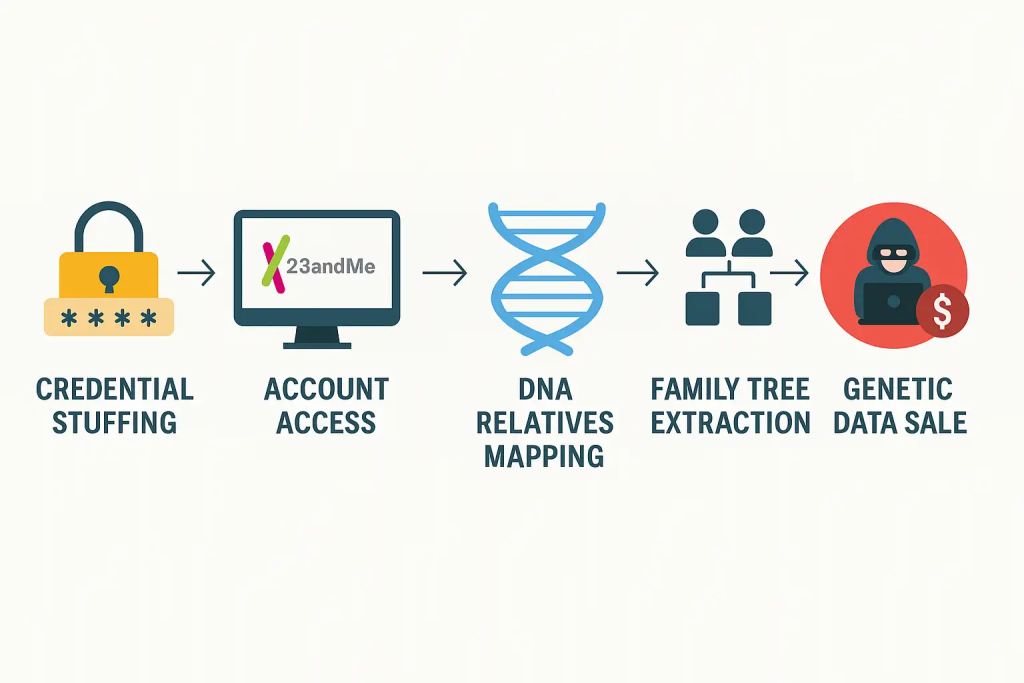
The initial breach occurred in 2023 when hackers launched a credential stuffing attack against 23andMe. This technique uses stolen credentials from other data breaches to gain unauthorized access to user accounts. Once inside, attackers leveraged 23andMe’s “DNA Relatives” feature to scrape extensive networks of connected profiles.
This meant that even if only one family member’s account was breached, the attacker could gain indirect access to the genetic markers and relationships of dozens, sometimes hundreds of people. Over time, this snowballed into a massive dataset that mapped entire family trees, health predispositions, and ancestral origins.
By mid-2024, snippets of this data were found circulating on hacker forums, being sold in packages labeled by ethnicity and genetic traits. Although 23andMe initially downplayed the severity, the June 2025 joint report from the UK’s Information Commissioner’s Office (ICO) and Canada’s Privacy Commissioner (OPC) confirmed widespread systemic failures in protecting this sensitive data.
The Regulatory Bombshell
The investigation concluded that 23andMe failed in several key areas of compliance and responsibility. Most notably, the company had not implemented multi-factor authentication (MFA) as a default, nor had it monitored for unusual access behavior; both considered best practices in data security.
The ICO issued a £2.31 million fine, citing gross negligence and repeated failure to act on previous warnings about user security. Meanwhile, the OPC has not yet issued a fine but has mandated that 23andMe overhaul its security infrastructure, provide breach notification to every impacted Canadian user, and limit the use of shared genetic features unless explicitly authorized.
These findings are more than just punitive. They reflect a shift in regulatory philosophy. Governments are beginning to treat genetic data as critical infrastructure, not unlike national ID systems or biometric databases. That elevates the stakes for companies operating in this space.
What Makes Genetic Data So Dangerous When Exposed?
Most cybersecurity incidents involve data that can be reset or replaced passwords, credit cards, even Social Security numbers. But genetic data is fundamentally different.
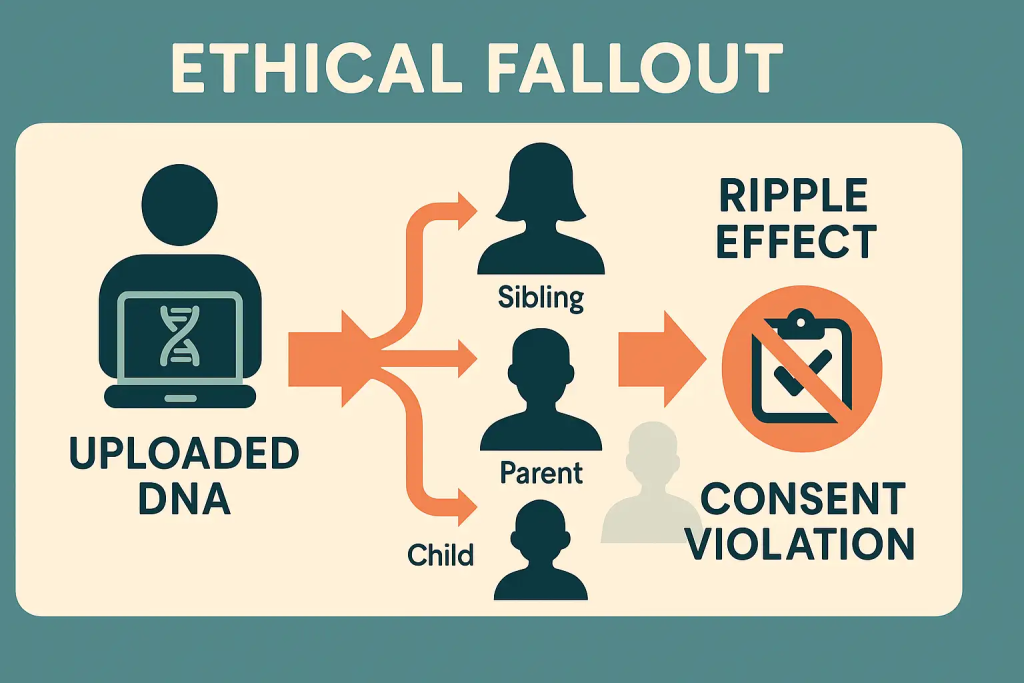
First, DNA is permanent. You cannot opt out of your genome. Once exposed, it becomes a part of the public data sphere indefinitely. Second, your DNA implicates not just you, but your biological relatives. If one person’s profile is breached, their siblings, parents, and children may also be exposed by association.
Additionally, genetic data contains information about a person’s health risks, mental predispositions, and even behavioral traits. Malicious actors can use this data to discriminate, blackmail, or tailor highly specific social engineering attacks. In a worst-case scenario, state actors could use such data for ethnic targeting or surveillance.
Thus, the 23andMe breach is not simply a violation of privacy, it is a bio-security incident with far-reaching implications.
Who Was Affected?
According to 23andMe’s own disclosures and the joint investigation findings, approximately 7 million individuals had their data accessed, either directly or indirectly. Affected data includes full names, email addresses, locations, family tree connections, and genetic heritage percentages. In many cases, health predisposition data and carrier status for genetic conditions were also exposed.
While users from the United States, Canada, and the United Kingdom make up the bulk of affected individuals, the breach may also extend to users in Australia, parts of Europe, and Southeast Asia. Due to the family-linked nature of genetic profiles, even individuals who had never signed up for 23andMe may have had parts of their genome exposed through a relative’s profile.
This has raised serious ethical questions about consent and secondary exposure, which we explore in the next section.
Legal and Ethical Implications

The legal framework around genetic data protection is both complex and insufficient. In the United States, HIPAA governs medical data within healthcare institutions but does not apply to most direct-to-consumer (DTC) genetic services. This leaves companies like 23andMe in a legal gray zone unless they explicitly partner with healthcare providers.
Canada’s PIPEDA offers slightly broader protections, especially regarding consent and breach notification. However, enforcement mechanisms are limited, and fines are capped at levels that many large tech firms can absorb as operational costs. Europe’s GDPR treats genetic data as “special category” information, requiring stricter consent and storage policies, but enforcement across borders remains inconsistent.
The 23andMe breach is now fueling calls for a new category of data protection laws focused solely on genetic and biological data. Lawmakers in Canada and the EU are already drafting proposals for a “Genomic Privacy Act” that would enforce stronger data residency, audit trails, and usage disclosures.
From an ethical standpoint, the breach highlights the failure of current consent models. When one family member uploads their DNA, they are by default, sharing the genetic code of every biological relative. This violates the foundational principle of individual agency in privacy decisions.
The concept of genomic custodianship is now gaining traction. This proposes that companies handling DNA data should be legally classified not merely as data processors, but as stewards of irreversible identity data. Such a role would come with fiduciary-level responsibility, including mandatory transparency reports, independent ethical audits, and zero-data-retention policies for non-consenting relatives.
Comparative Context: Not the First Breach But the Worst of Its Kind
To better understand the gravity of the 23andMe breach, it helps to compare it to other biotech data breaches from the last decade:
| Company | Year | Data Breached | Affected Users | Notes |
| MyHeritage | 2018 | Email addresses, password hashes | 92 million | No genetic data leaked, limited regulatory action |
| LabCorp | 2019 | Medical test data, contact info | 7.7 million | HIPAA-covered; faced class-action lawsuits |
| 23andMe | 2023–2025 | Genetic data, family tree links | 7+ million | Involved hereditary data; ICO fined £2.31 million |
The takeaway is clear: 23andMe may not have suffered the largest breach in terms of raw numbers, but the type and depth of information lost makes it the most dangerous.
The Public and Investor Response
The public backlash was swift and widespread. On Reddit, Twitter, and TikTok, users began sharing tutorials on how to delete 23andMe accounts, disable DNA Relatives, and remove connected profiles. Privacy advocates launched a petition calling for a complete moratorium on DTC genetic testing until proper regulations are in place.
Investor confidence also took a hit. 23andMe’s stock dropped 18% in the week following the June 2025 regulatory report. Analysts now warn that the company may face long-term brand damage unless it fully restructures its approach to data security and transparency.
In response, 23andMe has promised sweeping reforms. These include mandatory multi-factor authentication, a new privacy dashboard, and hiring a Chief Genomic Ethics Officer to oversee future product decisions. While these are positive steps, critics argue that the changes are too little, too late.
The Larger Cybersecurity Wake-Up Call
The 23andMe breach has sounded alarm bells throughout the biotech and healthcare industries. Other companies that collect health, genetic, or biometric data are now conducting internal audits and hiring third-party cybersecurity firms to pre-empt similar scandals.
Cybersecurity professionals are calling for:
- Zero Trust architectures for all genetic databases.
- End-to-end encryption of raw genomic data.
- Regular red teaming and penetration testing.
Government agencies are also reacting. Canada’s Innovation Ministry is drafting legislation that would allow the OPC to levy percentage-based fines tied to global revenue. In the U.S., the Federal Trade Commission is considering new guidelines for companies collecting hereditary information outside traditional healthcare settings.
Globally, there is growing support for a UN-led framework on genomic ethics, akin to the Geneva Conventions, but focused on privacy rights for DNA data.
Conclusion: A Turning Point for Bio-Privacy
The 23andMe breach has done more than reveal a failure in cybersecurity, it has exposed the urgent need to rethink our relationship with personal data at the most fundamental level. Your DNA is not just a string of code; it’s your history, your health, and your future. Once exposed, it cannot be recalled or repaired.
For the millions affected, the breach represents a profound violation of trust. For regulators and lawmakers, it is a wake-up call to build laws that reflect the uniqueness and sensitivity of genetic information. And for tech companies in the bioinformatics space, it is a warning: collecting DNA comes with responsibilities far beyond those of a typical data processor.
23andMe has become a cautionary tale in a rapidly evolving digital landscape. What happens next may define the future of not just genetic testing, but data governance as a whole.
If you want to to safe yourself from big or small cyber attacks or want to gain basic knowledge about Cyber Security shcedule a consultancy with our Industry Experts or clicke here to know more about hoplon and learn more about Cyber Security services.
Share this :