Aftermarket Car Cybersecurity Risks: The Hidden Roadblocks in a Connected World

Hoplon InfoSec
22 Aug, 2025
Aftermarket Car Cybersecurity Risks
Today, it’s hard to picture life without a car that connects to the internet. You can use your phone to unlock your doors, start the engine from a distance, stream music, or even get real-time traffic alerts. It feels like science fiction every time you drive. But there is a shadow that comes with that magic. Every new aftermarket gadget that promises more control or convenience also brings with it a hidden danger. Experts now call that danger “aftermarket car cybersecurity risks.”
Give it some thought. A driver buys an OBD-II dongle from a third party to keep track of how much gas they use. Someone else puts in an aftermarket infotainment system that can run apps. These are great improvements, but hackers can also use them to get in. You might not notice the danger until someone gets in, just like leaving the back door of your house unlocked.
Why the risks of aftermarket car cybersecurity are a topic of conversation in the boardroom
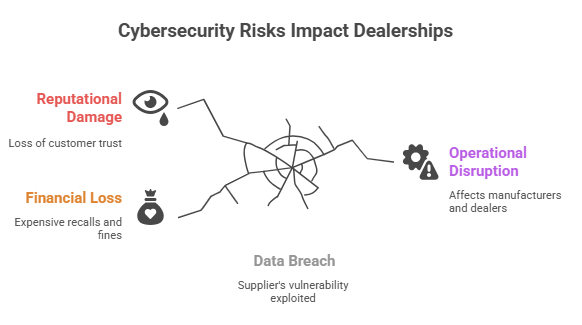
Ten years ago, the IT department was mostly in charge of cybersecurity. It’s now a topic of discussion at board meetings. CEOs and other high-level executives know that cybersecurity risks in the aftermarket can hurt dealerships, make customers lose trust, and lead to expensive recalls. A data breach at one supplier can have effects on manufacturers, dealers, and even insurance companies.
Boardrooms are waking up because the stakes are no longer just technical; they are also financial and reputational. One bad event can make the news, scare off investors, and make customers look for other options. In short, cybersecurity has gone from being an afterthought to a top priority.
The Aftermarket Boom: More gadgets, upgrades, and exposure
You can find hundreds of aftermarket parts in an auto parts store or online. These include dash cams, smart sensors, GPS trackers, advanced infotainment units, and performance chips. People who like to personalize their cars like them. The aftermarket business is growing quickly, which means that there are new risks that weren’t part of the original design.
The truth is that a lot of these gadgets are made to be cheap or easy to use, not strong. A tire pressure sensor that sends data over an unsecured connection may not seem like a big deal, but it could give hackers access to more sensitive parts of the car. The more devices we connect, the more vulnerable we become to attacks.
The Threat Landscape Is Getting Worse: Ransomware, Hacks of Infotainment Systems, and EV Charging Dangers
Cybercriminals are no longer only interested in computers. Cars are good things to steal. Ransomware attacks have really happened that locked down dealership systems and stopped sales.
Intruders have been able to listen in on conversations or change settings because of infotainment hacks. Even charging stations for electric vehicles aren’t safe. If someone messes with the charging infrastructure, they can cause bigger transportation problems.
This is why the risks of car cybersecurity in the aftermarket are so high. Hackers take advantage of opportunities. They look for the weakest link, which could be a poorly coded app, a cloud service, or an open charging port. Once inside, they can move to deeper systems, which can sometimes have scary results.
Weaknesses in the vehicle network: CAN Bus, APIs, and IoT exploits
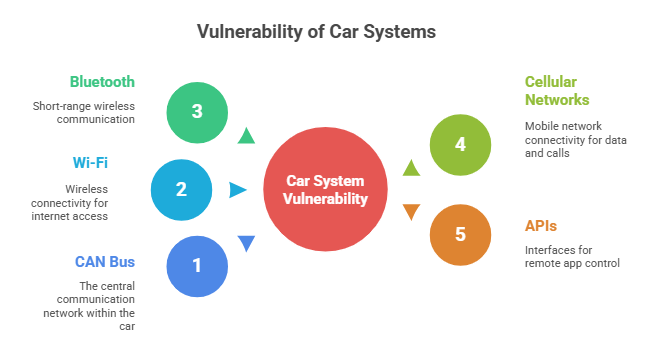
From the outside, cars may look sleek and simple, but they are really complicated computer networks. The CAN bus is like the nervous system; it sends signals between brakes, engines, and other parts. You can connect to Wi-Fi, Bluetooth, and cellular networks, as well as APIs for remote apps. This makes a lot of possible entry points.
Attackers love to find and attack weak points in these networks. If a hacker gets into the CAN bus through an aftermarket device, they can do more than just read data; they can also send commands. That could mean turning off safety features, opening doors, or even slowing down the car.
Scary True Stories: From Kia API Hacks to CDK Global Outage
Real-life stories show how dangerous these risks are. Researchers showed how easy it is to use weak APIs in Kia cars to unlock them and start their engines without permission. Owners didn’t know that the features that made their lives easier were putting them at risk.
Then there was the CDK Global ransomware attack, which shut down thousands of dealerships. Sales stopped, service centers froze, and customers lost faith in the company. The incident shows how fragile the ecosystem can be when cyber defenses fail, even though it wasn’t just aftermarket devices that were affected. There are real victims and real costs associated with aftermarket car cybersecurity risks.
Easy Ways In: Management Ports and Software Gaps in Vendor Software
Sometimes hackers can get in with very little effort. An unpatched vendor tool, a forgotten management port, or default login information can give someone access to the whole vehicle network. The aftermarket often adds these weak points because security is not usually the first thing that designers think about.
It’s like leaving a side door open while making the front gate stronger. Hackers like to get easy wins, and aftermarket shortcuts often give them just that.
When remote access costs a lot of money and trust
The real harm from these breaches is much worse than just a technical problem. When people misuse remote access, cars can stop working, customer information can leak, and trust can quickly disappear. People lose money not only when they have to fix things, but also when their reputations are damaged.
Picture yourself as a dealership that has to call customers to let them know that their information might have been stolen. Or imagine being a driver whose car breaks down all of a sudden after a software update that wasn’t safe. The money is important, but it’s even harder to rebuild trust on a personal level.
Digital Transformation: How Cloud Services Let Sneaky People In
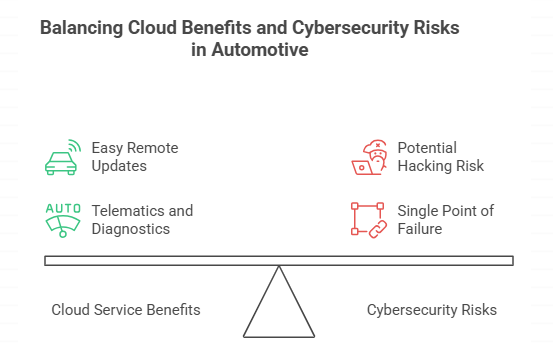
Cloud services are great for the auto industry because they make it easy to do remote updates, telematics, and diagnostics. But every cloud server could be a way for attackers to get in. If a hacker gets into an update server, they could send bad code to thousands of cars in a single night.
This is why every level of car cybersecurity risks must be taken into account, from the local device inside the car to the remote cloud system that sends updates. One weak link can spread an infection to the whole chain.
Supply Chain Holes: Risks to the Lifecycle of Third-Party Devices
Supply chains are like complicated webs, and many aftermarket devices come from smaller companies that may not follow strict security rules. Attackers are aware of this. They take advantage of the product’s lifecycle by putting bad firmware into the chain long before the device gets to a driver.
If one part isn’t secure, the whole system could be at risk. When it comes to cybersecurity, you need to trust your suppliers just as much as you trust your locks and passwords.
The Right-to-Repair Tug-of-War Between Standards and Guidelines
Regulators have made standards like ISO/SAE 21434 and UNECE WP.29 to help manufacturers and suppliers keep vehicles safe. But there is still a lot of talk about the right to repair. Supporters say that drivers should have full access to their car data and be able to fix or upgrade it without any restrictions. Car companies say that being too open makes things less safe.
It is a battle between safety and giving people power. Both sides have good points, but it’s important to find a middle ground for the future of connected cars.
Using smart controls to protect vehicle and customer data
Aside from keeping the car itself safe, there is also the issue of data security. Cars these days keep track of where they’ve been, how the driver behaves, and who they are. This information is just as valuable as the car if it is stolen. Every aftermarket solution must include encryption, access management, and clear policies for handling data.
The goal is simple: if hackers do get in, the data they find should be useless to them.
Best Practices for Aftermarket Security: Secure Design and Vendor Vetting
So, what can be done? One way to do this is to plan for security from the start. Threat modeling, zero-trust architecture, and layered defense strategies should be standard practices in the industry. Vendor vetting is another important thing to do. Before adding an aftermarket device, ask the supplier if they send out regular updates, provide clear documentation, and promise to fix security holes quickly.
Making better choices is the first step in preventing problems.
OTA Updates and Firmware Integrity: Are They Good or Bad?
Updates that come over the air are good and bad at the same time. They keep cars up to date and save trips to the dealership, but they also make it easy for the internet to connect to the car’s core systems. OTA updates can be hijacked if there aren’t strong integrity checks like digital signatures and rollback protection.
OTA is a powerful tool if you use it carefully. If you don’t pay attention to it, it can be a Trojan horse. The difference is in how much attention manufacturers and third-party sellers pay to security.

Keep an eye on the road ahead: constant monitoring, threat intelligence, and taking action.
Things will not get easier on the road ahead. Every year, cars get more digital, and so do hackers. It will be very important to keep an eye on things all the time, find intrusions, and work together through groups like Auto-ISAC.
The risks of car cybersecurity in the aftermarket won’t go away, but proactive defense can make them easier to deal with. In the digital world, it’s like driving defensively. You can’t control what other drivers do on the road, but you can stay alert, keep your distance, and look for warning signs.
Last Thoughts
We are in a golden age of car technology, where a car feels more like a computer on wheels than a machine made of steel and oil. That change is exciting, but it also brings new problems. The potholes on this journey are the risks to car cybersecurity that come from the aftermarket. Ignoring them would be foolish.
The lesson is clear: security needs to be as important as seatbelts and airbags. It’s not just about keeping cars safe; it’s also about keeping people, data, and trust safe. People who take that responsibility seriously and keep both hands on the wheel will be the ones who drive in the future.
Follow us on X (Twitter) and LinkedIn for more cybersecurity news and updates. Stay connected on YouTube, Facebook, and Instagram as well. At Hoplon Infosec, we’re committed to securing your digital world.
Share this :