CVE-2025-58782 Explained: How Apache Jackrabbit Became a Hacker’s Playground

Hoplon InfoSec
08 Sep, 2025
Apache Jackrabbit Oak 1.82.0 patch for CVE-2025-58782
If you run content platforms, a flaw in the code that powers repositories is a late night you don’t want. People are scrambling and typing things like “Apache Jackrabbit Oak 1.82.0 patch for CVE-2025-58782” into search bars in the hopes of finding a quick fix that will end their worries.
That feeling of needing to act is real. If an attacker sends a library inside a web app, CMS engine, or middleware with a carefully crafted reference that makes the server deserialize untrusted data, the server can run any code. That’s exactly why engineers and security teams are paying attention right now.
A short summary of CVE-2025-58782 and why it matters.
CVE-2025-58782 is a risk for deserialization and JNDI injection that affects parts of Apache Jackrabbit. To put it simply, some repository lookup flows let callers use JNDI URIs. If those URIs aren’t handled properly, an attacker can make the system create untrusted references and start deserialization paths that let them run code from a distance.
The practical result is clear and simple. If your app accepts JNDI repository URIs from sources you don’t trust, it could run code that you didn’t put there. This is an important issue for any organization that offers repository lookup functionality or uses libraries that can handle external URIs.
Who is affected: what parts are affected and how
This disclosure is for Apache Jackrabbit Core and Jackrabbit JCR Commons artifacts up to a certain version range. Systems that use those libraries or frameworks that depend on them are included. Not every installation is automatically vulnerable; the attack path depends on JNDI URI-based repository lookups being accepted and used.
Organizations that run Java-based CMS systems should check their dependency trees because those jars are often included in content platforms, middleware, and some custom Java back ends. You can tell if you need to do something by quickly checking the org.apache.jackrabbit artifacts in your deployment.
How the flaw works: A simple explanation of JNDI injection and deserialization
The weakness comes from two common problems that are stuck together. First, a feature lets you look up repositories using JNDI URIs. Second, the reference that was received can cause data from an outside source to be deserialized. Deserialization itself isn’t bad, but when it works with untrusted input, it becomes a reliable way to run objects that attackers give you.
It’s like letting someone into your house because they say they’re from the delivery company and then letting them run tech on your servers. If the caller is trying to hurt you, you just installed the wrong software. Attackers who use JNDI and deserialization as weapons can link together code-loading steps to get a shell or set up backdoors. This is why the community said the problem was important.
The risky part at the center is JndiRepositoryFactory.
The JndiRepositoryFactory is the most important part of the report. That factory lets a JCR client use a jndi: scheme to set the URL of a repository. When factories use unverified URIs from outside sources, they become easy targets for attackers. All they have to do is give the server a crafted JNDI reference, and it will pull in and deserialize content.
Your risk is much lower if your app never uses JNDI-based repository lookup. Libraries still move in dependency trees, and a change can turn on a feature that was turned off at runtime. That’s why the fix strategy is to turn off JNDI lookup by default whenever possible and to push upgrades that make the unsafe behavior opt-in.
Oak vs. Jackrabbit Core: Where Things Get Confusing
A lot of teams mess up here. Jackrabbit Oak is the newest version of the Oak repository in the Jackrabbit family. Jackrabbit-core and jackrabbit-jcr-commons are older parts that are used in other distributions. People often look for the Apache Jackrabbit Oak 1.82.0 patch for CVE-2025-58782 because they see “Jackrabbit” and think that Oak is the target.
The announcement that tracked CVE-2025-58782 specifically mentioned jackrabbit-core and jackrabbit-jcr-commons. There are Oak releases, and many teams use Oak, but the CVE’s immediate patch advice doesn’t say that Oak 1.82.0 is the one-line fix. Instead, it says to upgrade the core artifacts and turn off JNDI lookups. For specific instructions for your stack, look at the project advisory.
Patch landscape: warnings, suggestions, and releases
When the vulnerability was made public, the maintainers suggested a certain upgrade to get rid of the risky default behavior. The short advice is to upgrade to the patched version mentioned in the advisory and, if possible, use builds that don’t allow JNDI lookups by default. The recommended upgrade for Jackrabbit core users was version 2.22.2, which turns off JNDI-based JCR lookup by default.
People may talk about how to find the Apache Jackrabbit Oak 1.82.0 patch for CVE-2025-58782 because of that suggestion. Oak 1.82.0 is a real Oak release, but it is not the main vehicle mentioned in the advisory for this CVE. To put it another way, follow the advice for the library you really use.
I have seen teams copy and paste the exact phrase “Apache Jackrabbit Oak 1.82.0 patch for CVE-2025-58782” into Slack and search engines. The pattern is something you know. You get a short warning, you worry, and you type the product name you know into Google, hoping that the patch that fixes your problem will match the exact version number. That doesn’t always work out well because project lines and component names are the same.
If you search for “Apache Jackrabbit Oak 1.82.0 patch for CVE-2025-58782,” you’ll find both the product line you run and the CVE. It’s a natural way for people to get around. The important thing to do next is not the search term but the verification: read the vendor advisory and make sure you know which artifact and version actually have the fix.
How to quickly check your surroundings for exposure
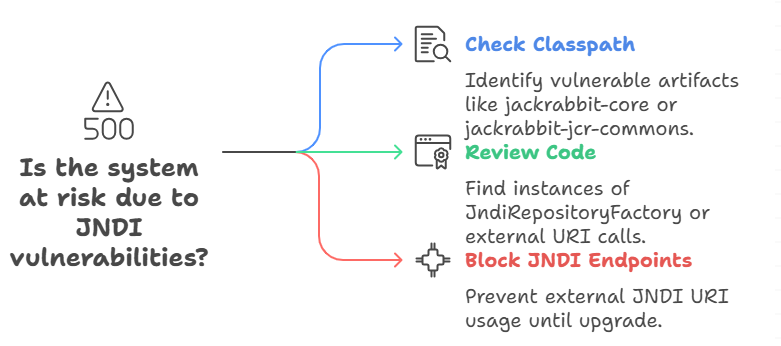
First, make a list of the classpath and the dependency tree. You can use tools like mvn dependency:tree or a binary scanner to see if your deployment has org.apache.jackrabbit:jackrabbit-core or org.apache.jackrabbit:jackrabbit-jcr-commons. If those artifacts are there and you allow external JNDI URIs for repository lookups, you should consider the host to be at risk.
Second, look through your code for any instances of JndiRepositoryFactory or calls that take repository URIs from outside sources. If you find any, block or clean them up right away, and keep the application away from outbound JNDI endpoints until you install the upgrade that the vendor recommends. These steps give you more time and make the blast radius smaller while you plan the permanent fix.
Short-term fixes while you work on the patch
If you can’t upgrade right away, turn off JNDI-based JCR lookup at runtime. The advisory said that the fix included turning off JCR lookups through JNDI by default in the patched version. If you have network controls, block outbound JNDI ports and limit egress so that even a successful injection can’t get resources from outside the network.
Add rules for runtime monitoring to find strange JNDI lookups and bad deserialization. Set up alerts for new network hosts that repository servers connect to and watch logs for unexpected remote lookups. These compensating controls aren’t perfect, but they make it less likely that a full compromise will happen.
How to safely test and confirm the fix
After you upgrade or turn off the dangerous feature, test it in a separate lab. Use harmless test payloads to make sure that JNDI lookups are ignored or rejected. Don’t try to run proof-of-concept code in production. Instead, run tests in a sandbox that is set up the same way as production and has the same network restrictions.
Validation should include both functional tests to make sure the repository works as it should and security tests that try out known exploit patterns in a safe environment. After you install the patch, run third-party scanning tools again and update their signatures to make sure the vulnerability is no longer there. The project’s documentation will often list the exact change so you can match tests to the fix.
What attackers look for in real-world attack scenarios
Attackers who use JNDI-deserialization chains usually look for two things: a way to get to an entry point that accepts a reference and a way to run code or steal data. In a lot of places, the path is an API or admin route that lets you send repository URIs. If that route doesn’t require authentication or lets users control the data, it becomes a way for hackers to get in.
A compromised marketing tool or CI job that sends fake metadata to a repository endpoint is a realistic scenario. The crafted metadata can start the deserialization chain if that pipeline uses a JNDI lookup. That’s why even indirect exposures are scary. The fix and the ways to make things better focus on cutting that chain at several places.
Playbook for teams on how to talk to each other and handle incidents
When you find an exposure, let all stakeholders know right away and clearly. Tell us what is affected, what you are doing to fix it, and which systems you are patching first. Make the message useful by including the steps you took, the level of risk, and a timeline for the upgrade or the extra hardening steps you will take.
If you think someone is exploiting your system, cut it off from the rest of the network, save the logs, and start your IR process. Look for signs like new outbound connections after the vulnerability window opened, changed artifacts, or processes that spawn unexpectedly. Get forensic evidence so you can decide if you need to go beyond your internal response.
Long-term hardening and keeping the supply chain clean
This news is another reminder that libraries are like living things that need constant care. Use dependency scanning pipelines, keep track of transitive dependencies, and keep an asset inventory that shows which libraries host which runtime services. Make sure that optional features that go beyond your trust boundary are either turned off by default or only available with safe configuration.
Lastly, practice patching drills and make the low-risk steps automatic. A well-rehearsed pipeline will make it easier for people to deal with a hotfix for a dependency and shorten the time it takes to fix it. Those habits in the institution are more important than any one version number.
Final thought and a short list of things to do
To end, here’s some simple advice: don’t just use Google search phrases. Phrases like “Apache Jackrabbit Oak 1.82.0 patch for CVE-2025-58782” can help you understand the situation, but you should only do what the vendor says to do about the exact artifact you run. Make sure you know which part of your stack is affected, make the recommended upgrade or configuration change, and test it in a sandbox before putting it into production.
CVE-2025-58782 is a reminder that hidden flaws can open the door to serious attacks. Hoplon Infosec’s Penetration Testing service helps uncover risks like this before attackers do, giving teams confidence that their systems are secure.
Follow us on X (Twitter) and LinkedIn for more cybersecurity news and updates. Stay connected on YouTube, Facebook, and Instagram as well. At Hoplon Infosec, we’re committed to securing your digital world.
Share this :