How to Protect Your Systems: Apache Tika PDF Parser XXE Exploit Mitigation

Hoplon InfoSec
21 Aug, 2025
Apache Tika PDF parser XXE exploit mitigation
Imagine this: you have a cup of coffee while Apache Tika goes through hundreds of PDF files for your business. It extracts text, metadata, and other critical information that assists with compliance, indexing, or internal search operations. Everything appears fine until one day a bad PDF sneaks through and puts vital internal files at risk. This isn’t a bad dream. This is what happens when document parsers have XXE flaws. All businesses that utilize Apache Tika need to know about these flaws and how to resolve them.
Document parsers are quite helpful, but they can be risky if they aren’t set up well. This article will explain how Apache Tika’s PDF parser works, what XXE vulnerabilities are, and how to protect your systems in a way that works.
What is Apache Tika, and Why is Its PDF Parser So Useful?
Apache Tika is a free and open-source tool that can read and write data from a wide range of file types, including PDFs, Word documents, and photos. For firms that have a lot of papers, Tika is like a librarian. It can quickly read and summarize thousands of files.
The PDF parser is a key part because it can read documents with text, pictures, and embedded metadata that are hard to understand. This parser is important for various business tasks that involve indexing, searching, and obeying the rules.
Some PDFs do have XML data in them, especially those that have XFA forms. You could make your system highly hazardous if you don’t handle this XML correctly. If you don’t set up the parser right, it could show private information by mistake. Hackers can get into private data or networks if you make a small mistake when processing XML. This is why it’s so vital to learn about and solve the Apache Tika PDF parser XXE attack.
What Are XXE Security Holes?
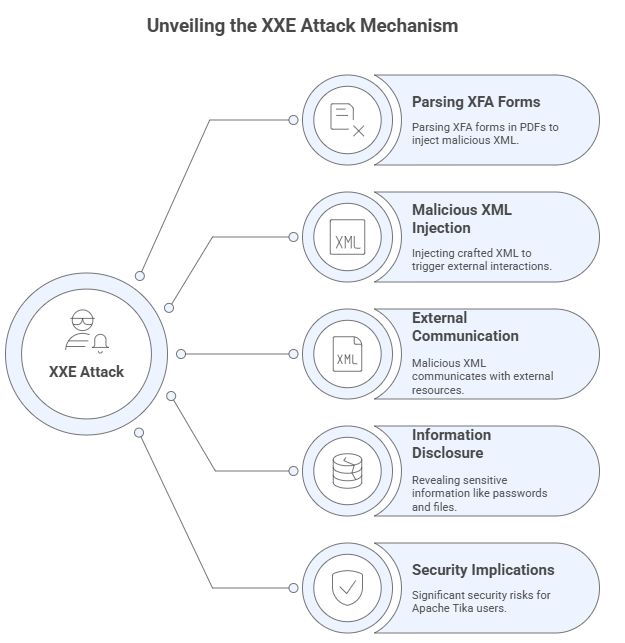
An XML External Entity (XXE) attack happens when an XML parser looks at external entities from sources that aren’t trustworthy. It’s like hiding a key beneath the carpet so that anyone can find it. People with bad intentions can develop XML code that tricks the parser into giving over confidential information, letting them into internal files, or sending queries to internal services.
Even the smallest amount of activity, like looking at a PDF, can lead to these attacks. In business, this could mean stealing data, spying on workers, or breaching the law.
If you don’t fix XXE vulnerabilities, they could have major consequences, even if the risk isn’t evident. To build the correct defenses, you need to know what these weaknesses are. Developers and system administrators need to know about the dangers of processing XML in PDFs.
How XXE Exploits Work in Apache Tika
A common approach to launch XXE attacks with Apache Tika is to parse XFA forms in PDFs. Hackers can enter XML that they have made deliberately into these forms. When the parser scans the PDF, the bad XML talks to things outside of it. This can reveal passwords, private files, or server information.
It’s like someone arriving at your office and showing the receptionist a fake ID. Then they can see files that they shouldn’t be able to. XXE attacks work in a similar way by tricking the parser into showing information that it shouldn’t.
The attack is sneaky. The parser might send queries or show private information without users seeing anything strange. Because of this, any business that uses Apache Tika needs to take action to safeguard itself ahead of time.
How XXE Security Holes Affect People in Real Life
A weakness in XXE can have big implications. A hacker may gain access to confidential customer information or financial data if they break into a bank’s document system. In healthcare, patient information could be made public, which would contradict privacy restrictions and make people less likely to trust the system.
Government entities can also be at risk. There is a risk that important reports or internal memos could leak, which could put national security at risk. These real-world examples highlight how important the CVE-2025-54988 issue was. Attackers might simply get into internal systems by sending PDFs that weren’t prepared correctly.
If businesses don’t pay attention to this threat, they could lose money, have their operations interrupted, and ruin their reputation. If you run a firm that uses Apache Tika, you need to act swiftly to defend yourself from XXE threats.
CVE-2025-54988 and Very High Severity
CVE-2025-54988 is a major security issue in the Apache Tika PDF parser. It shows that XML parsing needs to be set up appropriately so that even software that most people trust can be exploited. Several versions of Tika are broken, according to security researchers. This means that businesses need to do something right soon.
The critical assessment looks at the chances of data theft, internal network reconnaissance, and SSRF attacks. Companies need to understand what this flaw means for them and act quickly to rectify it.
Apache Tika Packages That Are Affected
The bug affects a number of Tika packages that use the PDF parser module. These are:
- tika-parser-pdf-module
- typical Tika modules
- parsers-standard package for tika parser
- tika-app
- tika-grpc
- tika-server-standard
Enterprise settings are more likely to be attacked since so many packages are broken. Businesses that utilize any of these programs should look at upgrading and putting security measures in place right soon.
Things You Need to Do Before You Can Exploit
For attackers to use XXE in Tika, they need:
- Sending in a faulty PDF
- XFA file that is supposed to start XXE
- Weak Tika variation
- Not much contact with users
If even one setting is overlooked, a PDF parser can permit persons who shouldn’t have access to important internal resources. When establishing security plans, you need to think about every phase of the document processing workflow.
Possibility of SSRF and Exposure of the Internal Network
XXE lets attackers employ Server-Side Request Forgery to get a vulnerable system to send requests to servers inside the network. This makes confidential information, passwords, and network endpoints available to everyone.
Attackers can readily steal private data if network segmentation and monitoring aren’t done well. To lower these risks, you need to always be on the watch and set up your system in a safe way.
Upgrade Apache Tika to Version 3.2.2
The safest thing you can do is to upgrade to Apache Tika version 3.2.2. This version stops processing foreign entities by default and employs safe XML parsing. It is still very conceivable that hackers will break into older versions of systems.
It’s not enough to just update the software. To keep things safe over time, businesses must also set up parsers correctly, validate inputs, and keep an eye on things all the time.
More Things to Do to Stay Safe
Organizations can protect themselves even better by following best practices:
- Use XML parsers that have safe settings by default
- Give the parser only the characteristics that your program needs
- Before processing, look over the PDFs
- To decrease the effect, break the network up into smaller pieces
- Look through logs for unusual XML activity
These measures keep the parser from mistakenly giving out private information, even if a malicious PDF gets into the system.
A Plan to Minimize Risk One Step at a Time
A useful workflow for reducing risk includes:
- Copy the current Tika environment and the settings for the custom parser
- Download the newest version of Tika and update the project’s dependencies
- Stop XML parsers from being able to handle external entities
- Make sure that your PDFs don’t have too many XXE holes
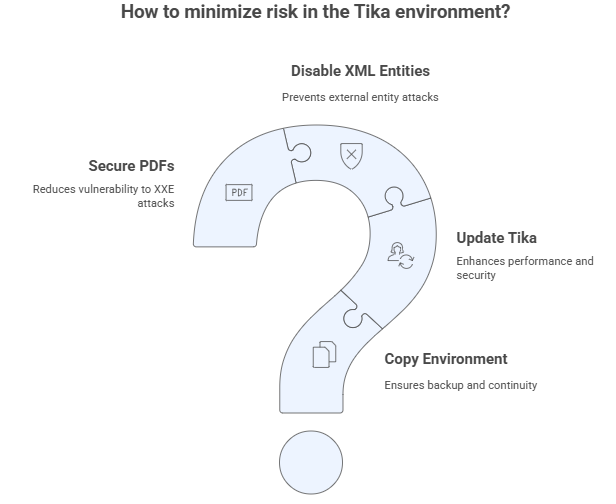
For long-term protection, you should employ both patching and correct configuration. This structured method dramatically decreases risk while still allowing for quick document processing
Checking XXE Protection
Testing is highly crucial for good mitigation. Create PDFs with XFA forms that will launch XXE, and then run them through the parser. The mitigation works if the parser can read the file without trying to get in without permission.
Regular testing helps ensure that protection stays in place as libraries, workflows, and new techniques evolve. You can’t just do security once; you have to do it all the time.
Adding XXE Mitigation to Development Workflows
Every day, security should be a component of development, not something that comes up later. These are the steps:
- Adding security checks to CI/CD pipelines
- Adding unit tests to routines that read PDFs
By making these principles a part of the process, any new feature or upgrade will preserve a robust security posture.
Giving Back to the Community and Learning
To keep things safe, the Apache Tika community is really vital. Researchers talk about issues, suggest solutions, and offer tips on how to do things correctly. XXE is less likely to attack organizations that listen to the community and make changes rapidly.
When teams learn from real-life scenarios, they may better protect themselves.
Why It’s Important to Be Aware
XXE attacks are not easy to see, yet they are quite powerful. A network can have great security, but unpatched parsers are still vulnerable. The organization’s whole cybersecurity culture is stronger when everyone knows how to protect themselves from attacks, CVEs, and other threats.
Proactive knowledge gives developers, system administrators, and security teams the skills they need to stop breaches before they happen. Security awareness and technological solutions work together to keep you safe in the long run.
Final Thoughts
It’s not just a technical need to protect the Apache Tika PDF parser against XXE; it’s also a promise to keep sensitive information safe. It is less likely that XXE will be used if you upgrade your software, set up parsers in a safe way, check inputs, keep a watch on workflows, and instruct your personnel.
Think of document parsers as key entry points. If you keep aware and make security a high priority, small security gaps won’t evolve into huge ones. Hackers will always be one step behind companies that take a proactive and tiered approach to security.
Follow us on X (Twitter) and LinkedIn for more cybersecurity news and updates. Stay connected on YouTube, Facebook, and Instagram as well. At Hoplon Infosec, we’re committed to securing your digital world.
Share this :