Apple Got Paragon Spyware Attack in Messages-Two Journalists Were Spied

Hoplon InfoSec
13 Jun, 2025
Imagine your iPhone quietly betraying your most private moments… without you even tapping a link. That’s exactly what apple got paragon spyware attack in messages, that is how it is steals your data without a hint.
‘Apple Got Paragon Spyware Attack in Messages’- What Exactly Went Down for that?
- The Flaw (CVE‑2025‑43200)
- Apple discovered a “logic issue” in iMessage’s handling of malicious media files, photos, or videos sent via an iCloud link.
- This flaw let attackers send specially crafted media that triggered code execution on its own, no clicks needed.
- Exploitation Phase
- In January–February 2025, two European journalists, including Italy’s Ciro Pellegrino, were targeted.
- Spyware installed via iMessage using a sender account called “ATTACKER1.”
- Their iPhones (running iOS 18.2.1) silently began communicating with a Paragon command-and-control server (e.g., IP 46.183.184.91).
- Detection & Patch
- On April 29, 2025, Apple sent them “state-sponsored attacker” warnings.
- By February 10, 2025, Apple had quietly patched the flaw in iOS 18.3.1, but only later disclosed it publicly as CVE‑2025‑43200.
How Did the Flaw Let It Happen?
This wasn’t your typical hack. No link to click. No app to install. Just a quiet message… And >BOOM<, the phone was infected.
Here’s how it started
Paragon, the spyware company, created a special trap. They packaged a hidden piece of malware inside a fake photo or video. But instead of sending a normal attachment, they wrapped it in an iCloud link the kind Apple uses to share large media safely. This media file was poisoned, but on the outside, it looked totally normal.
step two>the attacker, using an account named something like “ATTACKER1,” sent that iCloud link through iMessage. Now here’s the dangerous part: the victim didn’t even have to open the message. iMessage automatically tried to preview or render the media file in the background. That’s when the flaw kicked in.
step three>the hidden code inside that media file slipped past iOS defenses and executed silently. It was like sneaking a thief through a mail slot. The spyware, called Graphite, was now active. Without warning or any pop-up, it reached out to a server controlled by Paragon. That’s where it got its orders, what data to collect, which features to tap (like camera, mic, or messages), and how to send it all back.
Who is responsible for Attack?
· Paragon Solutions; a private-sector surveillance firm founded by ex-Israeli officials and headed by former Prime Minister Ehud Barak.
> Shortly after going public this year, Paragon was acquired by US private equity firm AE Industrial Partners ($500M+).
· The operation used one single Apple account and one command server, suggesting coordination by a single Paragon customer.
· Paragon has historically sold to democratic governments under “law enforcement” pretexts but has come under backlash for abusing it.
. Italy was a documented Paragon user from 2023–24 and emphasized it only monitored suspects in criminal or immigration cases.
> After public outrage, Italy canceled its contract; Paragon offered internal audit access to prove no journalist hacking Italy refused.
So Who Are Those 2 Victims?
Two confirmed journalists: Italian reporter Ciro Pellegrino and another person who is a prominent but unnamed European journalist.
How Bad Is the Damage?
Suppose you’re a journalist. You’re exposing corruption, tracking political abuse, or simply doing your job investigating truths people don’t want told. Then one day, without any click or warning, your phone is hacked. Your messages, emails, Signal chats, even your camera and mic everything is silently handed over to someone else. That’s what happened here. And not just to one person and at least 7 known victims, all journalists or activists. But experts say the real number could be dozens or even hundreds.
This spyware, Graphite, didn’t just snoop it completely took over the device. It recorded calls, read WhatsApp and iMessage, tracked location history, and even watched or listened through the camera and mic without ever asking or alerting the user. It was like someone sitting silently in your pocket, 24/7.
The consequences? It is Massive.
For the victims: total invasion of privacy. Sources exposed. Careers, investigations, and personal safety are endangered.
For society: Press freedom shaken. How can journalists report honestly if they’re being watched like this?
For Apple: Users trusted iMessage to be secure. Now that trust is deeply cracked.
For governments: Italy had to cancel its deal with Paragon. Public backlash was fierce. Internationally, it’s igniting debates on spyware ethics and digital surveillance laws.
As a result,
- Italy has cut ties with Paragon but disputed how it ended.
- EU reaction: Parliament to debate on June 16; European Commission condemns misuse.
- Meta’s move: WhatsApp sent a cease-and-desist; suing is on the table.
- Apple strengthens measures: patch, raise awareness, bolster silence-to-alert pipeline.
How People Can Be Attacked and How to Detect it?
This kind of spyware attack doesn’t need you to click anything. That’s what makes it dangerous. It just lands in your iMessage inbox, hides in a media file, and does the rest silently. No pop-up. No warning. Nothing to make you suspicious.
So how could you be attacked?
If your iPhone hasn’t been updated recently, the door is wide open. The attackers don’t need your help, they exploit flaws deep inside the iOS system that run automatically when a photo or video is sent.
So… how do you protect yourself?
Here’s the whisper-down list keep this close:
🔐 Basic Defenses
· Update iOS immediately. Always. Don’t wait. Zero-day flaws get patched quietly; miss it, and you’re exposed.
· Turn on Automatic Updates. Let the phone stay current even while you sleep.
· Use Lockdown Mode. Go to Settings > Privacy & Security > Lockdown Mode (especially if you’re a journalist, activist, or whistleblower). It limits risky features.
🧠 Stay Smart
· Watch Apple Threat Alerts. If you ever get one, take it seriously, and contact a digital security expert.
· Be mindful of iCloud links or messages from unknown senders. Even if nothing looks strange.
· Avoid using your main device for sensitive work. Use secondary phones, offline note-taking, and secure messengers where possible.
📚 Learn & Prepare
· Understand digital hygiene. Read up on device security, spyware threats, and secure communication.
· Follow trusted tech/security sites. (Like Citizen Lab, Access Now, and EFF)
· Use encrypted messengers like Signal (though even these can be accessed if your phone is compromised).
Where Did Things Break?
The attack happened because of a hidden weakness in how iPhones handled images and videos sent through iMessage. Apple’s security system, called BlastDoor, is designed to scan and block dangerous content before it reaches your phone. But this time, it missed a small flaw in the code; something deep in the way media files were processed. That tiny error opened the door for attackers to slip in spyware without the user clicking anything.
The real problem, though, isn’t just technical, it’s about trust and responsibility. Paragon took a common feature (sharing media through iCloud links) and turned it into a spying weapon. This spyware was supposed to be used to track serious threats, not silence reporters. But governments misused it, and Apple, instead of sounding the alarm quickly, fixed the issue quietly and said nothing for months. In Italy, officials even denied journalists were being targeted, until outside researchers proved otherwise. So, the failure wasn’t just in the code. It was in the decisions, the silence, and the systems that were supposed to protect people, not betray them.
At a glance:
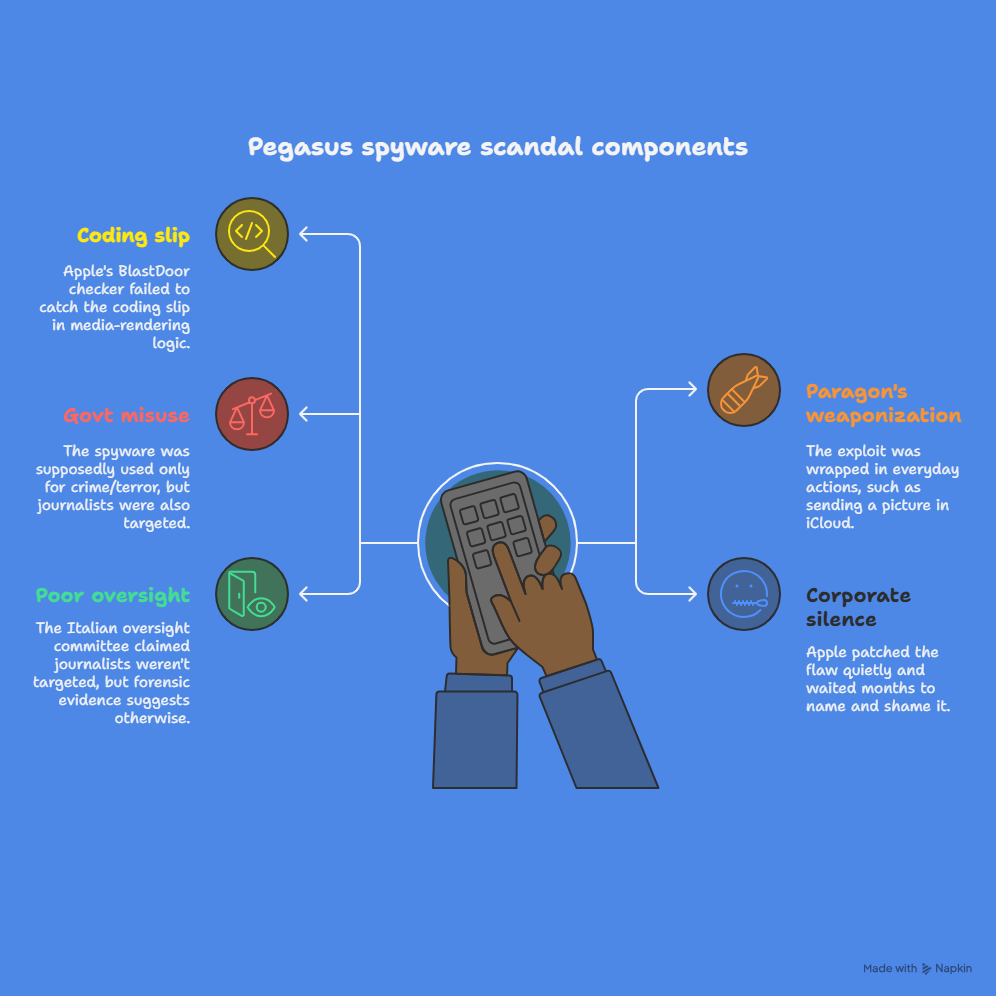
- Coding slip in media-rendering logic Apple’s BlastDoor checker didn’t catch it.
- Paragon’s weaponization: wrapping exploit in everyday actions (sending a pic in iCloud).
- Govt misuse: supposedly used only for crime/terror, but journalists got caught.
- Corporate silence: Apple patched quietly and waited months to name and shame the flaw.
- Poor oversight: The Italian oversight committee (COPASIR) said tools were used but journalists were not targeted; but forensic evidence says otherwise.
Final thoughts
This wasn’t just a tech glitch or some random cyber bug; this was a real-world breach of privacy, trust, and human rights. When tools meant for law enforcement fall into the wrong hands or are used in the wrong way the damage isn’t just digital. It’s personal. Journalists, who are supposed to be the voice for truth, became the target. And that’s something we all need to care about.
What this incident really teaches us is simple: no one is too secure, too important, or too unknown to be targeted. If a phone can betray someone without a click, it means we’ve hit a point where silent surveillance can become normal, and that’s not okay. We need stronger protections, louder accountability, and faster transparency from the tech giants, the companies that build these tools, and the governments that use them.
Stay updated. Stay aware. And never assume your device is smarter than the people trying to break it. Stay connected with us to get updated news in Cyber Security.
Resources
The Hacker News
Security Affairs
Share this :