Astaroth Malware Attack 2025: How Cybercriminals Are Using GitHub to Steal Your Banking Data

Hoplon InfoSec
13 Oct, 2025
Do you ever feel like someone is watching you, even while you're alone? The Astaroth virus attack in 2025 resembles that feeling, but it occurs online. Picture someone you can't see sitting next to your computer and discreetly watching every click, every password you write, and every time you go to your bank or crypto wallet. That's Astaroth, and it's smart. Very clever. It's now hiding on GitHub, a site that most of us trust totally.
Digital banking and cryptocurrency wallets have definitely made things easier. But there is a cost to being easy. Cybercriminals have used that ease to make malware like Astaroth. It waits and watches in silence, then attacks at the proper time.
How Astaroth Gets In
Most attacks start with something that seems innocent, like an email that is well-written. It can look like it originated from your bank, a well-known service, or even a job application. If you click on the wrong thing or open a zip file, Astaroth will discreetly install itself on your machine.
I read about a Brazilian company that lends money. A worker opened an invoice that seemed normal. Things started to happen that were unusual hours later. But the IT team always found that everything was alright. That's what makes Astaroth so brilliant and scary. It hides in plain sight, waiting to take your banking or cryptocurrency logins when you least expect it.
GitHub is a backup.
This is the bit that really caught my eye. Astaroth now uses GitHub as a backup instead of merely servers that can be shut down. GitHub is where the malware receives its configuration files. It also hides its instructions in conventional photographs using a technology called steganography. Security systems don't monitor GitHub content very regularly, so it stays running in the background even when the main servers go down.
This isn't the kind of spyware you see all the time. It's quite hard to get rid of the Astaroth virus attack from 2025. After McAfee alerted GitHub about the rogue repositories, the company's security staff took them down. For a short time, this stopped the attack. But the way the malware was built illustrates how far hackers have progressed in turning trusted platforms into covert weapons.
spyware Attack Process
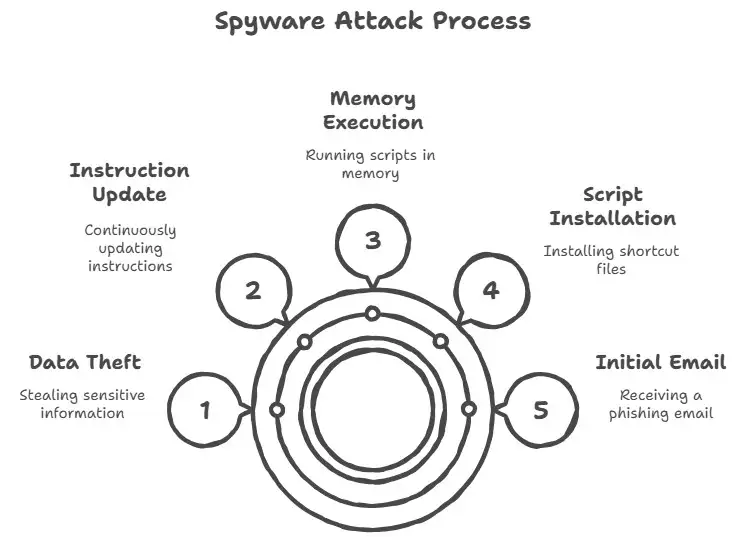
The Chain of Infection
This is how it generally works:
You get an email that seems like a scam to steal your information.
When you open the zip file that is attached, it installs a Windows shortcut file (.lnk) that launches scripts without your knowledge.
• The script combines elements of the payload in memory, making it hard to find.
The spyware watches your browser windows for sites that deal with banking or cryptocurrencies.
It records what you type and transfers it to the attackers using secure channels.
It continuously checks GitHub for fresh instructions in the meantime, which makes the assault more flexible.
Most antivirus programs can't find it because it largely runs in memory.
Who is at risk?
People that have cryptocurrencies and utilize online banking are the most likely to be targeted. Most of the attacks have happened in Brazil, Mexico, and other South American countries, but they might happen anywhere in the world. People who use bitcoins are considerably more in danger. Once Astaroth has your keys, getting your money back is almost impossible.
You may call it a master key maker. It not only makes copies of your keys, but it also hides them in secret places so that it can always get in, even if you "change the locks."
Staying Safe
You can't get rid of all the hazards, but you can make them smaller:Don't open attachments or respond to emails from persons you don't know.
Whenever you can, use two-factor authentication (2FA).
Always keep your antivirus and security programs up to date.
Watch what your network is doing, especially when you utilize sites like GitHub.
Be wary and ask questions about anything that seems weird online.
Astaroth C2 & config below
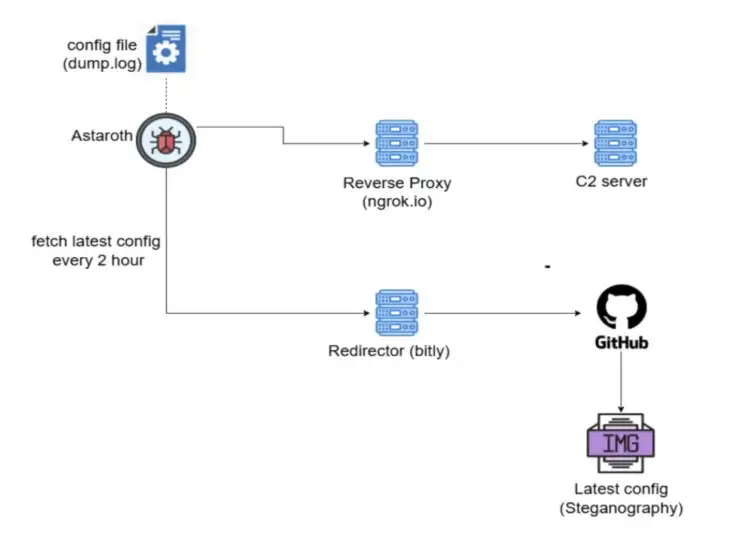
Source: McAfee
The Technical Side
Astaroth targets popular browsers and apps. It watches sites like caixa.gov.br, safra.com.br, and itau.com.br and crypto platforms like binance.com and metamask.io. The attackers obtain the stolen data using encrypted methods, and the virus updates itself every few hours from GitHub sources. This combination of outdated servers with GitHub makes it quite powerful.
Technical Breakdown
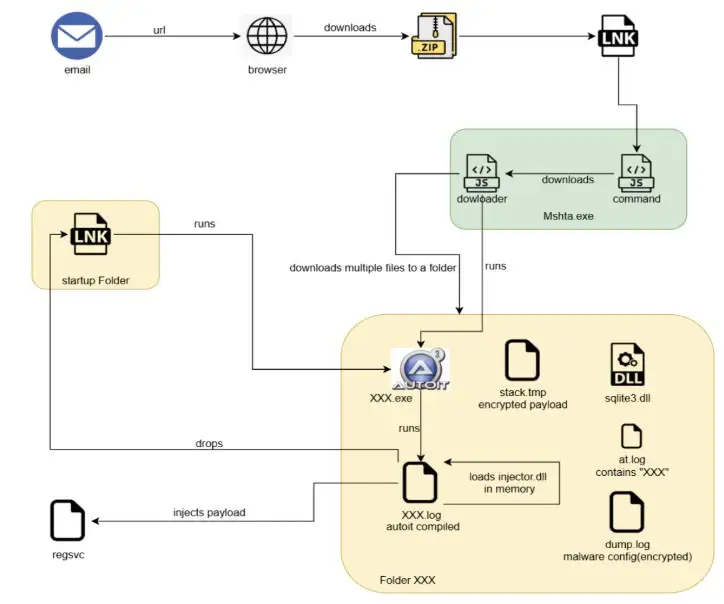
Source: McAfee
The Hoplon Insight Box
Be careful: Don't open emails or attachments that seem strange.
Behavior-Based Security: Always watch your devices.
Check Sources: You should always check files that other people send you.
Turn on 2FA to make your accounts safer.
If something doesn't seem right, tell the IT or security teams.
Source
Hoplon Infosec's Endpoint Security solution helps keep your devices safe from dangers like the Astaroth malware attack in 2025. It searches for unusual behavior, stops malware right away, and makes sure that important data is safe before any harm can be done.
Follow us on X (Twitter) and LinkedIn for more cybersecurity news and updates. Stay connected on YouTube, Facebook, and Instagram as well. At Hoplon Infosec, we’re committed to securing your digital world.
Share this :