AsyncRAT Hackers Exploit ConnectWise ScreenConnect to Steal Credentials and Crypto

Hoplon InfoSec
11 Sep, 2025
AsyncRAT ConnectWise exploit
You open your laptop, and a tool you trust to help you from afar suddenly becomes the door the thief used to get into your files. What is shocking and disturbing about the recent AsyncRAT ConnectWise exploit story is that it is true. I’m going to explain what happened, why it matters, and what you should do in simple terms and with real-world examples.
This isn’t a far-off idea. For months, security teams have been watching a pattern where a real remote access channel is used to send a strong remote access trojan. The result is simple and bad: stolen passwords, empty wallets, long cleanup times, and a hard lesson about trust.
What is AsyncRAT?
AsyncRAT is a group of remote access trojans that let hackers take full control of a Windows computer that has been hacked. Think of it as remote desktop on steroids, with keylogging, file access, screen capture, and the ability to run commands in the background without anyone knowing. It can be broken down into parts and is often customized for the campaign that uses it.
There are many different versions and forks of the codebase. That makes it hard to figure out who is responsible, since tools change and threats use the same parts. For defenders, that means keeping an eye on behavior, not just static hashes.
What is ConnectWise ScreenConnect?
Many IT teams and service providers use ConnectWise ScreenConnect as a real remote support and monitoring tool. It was made so that support techs could connect to, troubleshoot, and fix machines from a distance. It is powerful when used correctly and dangerous when misused because it can open deep access on a host.
Attackers don’t have to do anything new. They like to fool people, take over installers, or break into support channels so that a piece of software that people trust can be used to send malware. That change from “tool” to “malware courier” is the bad one.
The attack, in short,
In general, the incident we’re talking about used ScreenConnect to run a fileless loader that eventually put AsyncRAT on the victim’s computers. Once the Trojan was on the computer, the operators stole data from the browser, saved passwords and crypto wallets, and copied clipboard content. This made it easy and quick to go from getting in to stealing money and exposing credentials.
That short summary doesn’t show all the details. The payloads are often hidden and staged. The attacker can easily execute their plan through the ScreenConnect session. After that, the attacker tries to stay in the system, move sideways, and quietly steal what they can before they are caught.
The infection chain and the fileless loader trick
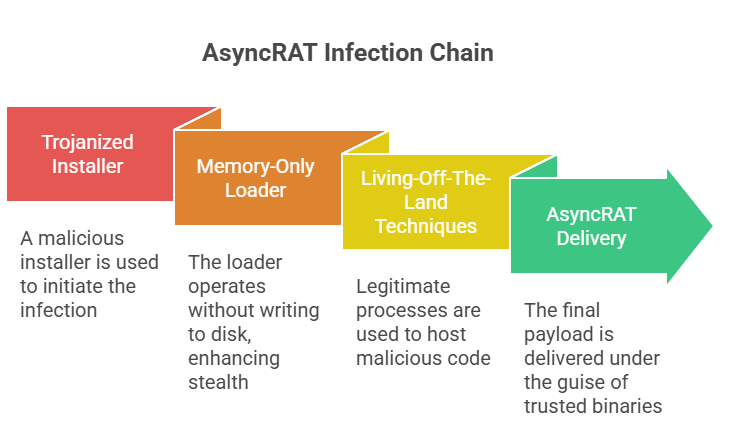
In a number of observed instances, the infection chain originated from a trojanized ScreenConnect installer or a bait that directed users to a malicious ScreenConnect server. The installer or session gave a memory-only loader that didn’t write an obvious executable to disk. That fileless method makes it harder for forensic tools to find things and slows down detection by endpoint tools.
The loader often uses living-off-the-land techniques during this chain, using real processes as hosts for code that is added. This makes it harder to analyze and find because the AsyncRAT payload runs under the cover of trusted binaries. Security researchers have recorded patterns of trojanized installers and drive-by downloads that resulted in AsyncRAT deliveries.
How credentials are collected
Once AsyncRAT is running, one of its main goals is to steal credentials. The trojan can look for saved passwords in browser stores, dump credential caches, and run keyloggers. Sometimes, attackers use remote access to control the browser to export logins or start actions that make users type their passwords into forms that the attackers control.
Attackers use both automated stealing tools and people typing on a keyboard. That mixed method lets them quickly gather a lot of credentials, usually starting with high-value accounts like email, cloud consoles, and corporate SSO portals.
How people steal and clip crypto
People are now stealing crypto all the time. Attackers use clipboard monitoring to change the wallet addresses of victims to their own addresses while a transfer is happening. They also use clipboard clippers and cryptostealer modules to look for wallet files, seed phrases, and storage space in browser extensions. Getting money back is almost impossible once those secrets are out.
Some versions of AsyncRAT have built-in clipper and cryptostealer modules that let them steal wallets directly without any help from the user. These attacks are quick and effective because they combine automated stealing with manual oversight.
Campaigns and examples from the real world
This pattern is not just a theory. There have been many campaigns in which AsyncRAT and other stealers were delivered through ScreenConnect sessions, trojanized installers, malvertising, and hijacked links. One interesting method used was hijacked invite links and social engineering lures that sent victims to fake verification pages. These pages then led to the installation of remote tools and the delivery of payloads.
Researchers have found a number of campaigns that used these steps to hack users, steal their browser data, and get into their wallets. There are a lot of ways to get in, which is a clear sign that attackers will use any trusted channel they can control.
Why attackers like ScreenConnect
The attack surface explains why it’s interesting. Remote support tools have a lot of power and can often get around normal network controls. Administrators can add the tool to a list of trusted tools, and users are used to getting help from vendors and partners over the internet. Attackers take advantage of that trust.
The human factor is just as important as technical privilege. A convincing email or an ad that shows a support flow that looks familiar makes it easier for social engineering to work. If you have low resistance and high access, intruders will find it easy to get in.
Tactics, Techniques, and Procedures (TTPs) of the Enemy
People who use AsyncRAT usually follow a set of steps:
they get in through phishing, trojanized installers, or hijacked links, then they run a loader, move to persistence, and do reconnaissance. After that, they steal credentials and move on to high-value targets, such as crypto wallets.
They use obfuscation, living-off-the-land binaries, and encrypted command-and-control to hide their tracks. This means that defenders’ only reliable long-term strategy is to map behavior instead of just looking for indicators.
Signals for detection and signs of compromise
There are a number of practical signs that can signal a compromise, such as unexpected ScreenConnect sessions, strange parent-child process relationships, memory-only executables, sudden clipboard changes, and spikes in outbound connections to strange domains. Browser exports, repeated requests to change your password, or transactions in your wallet that you can’t explain are also signs of trouble.
Telemetry and logging are important. You can find the pattern early if your EDR and SIEM are set up to look for strange remote sessions and process injection. Add restricted access logging to the support tool itself.
Incident response: containment and recovery
If you find an intrusion like AsyncRAT, the first thing you should do is contain it. Separate the affected hosts, cancel session tokens, reset privileged credentials, and change the keys that automated systems use. If you lose money in crypto, freeze the accounts that are connected to it and let exchanges know if you can.
A forensic timeline is needed to figure out the vector, and there needs to be a full credential reset and backup validation as part of recovery. Take the Trojan off of hosts, but act as if anything that operators can get to may be compromised and plan accordingly. The goal is to contain the problem, get rid of it, and rebuild trust
Patches and configuration for hardening and prevention
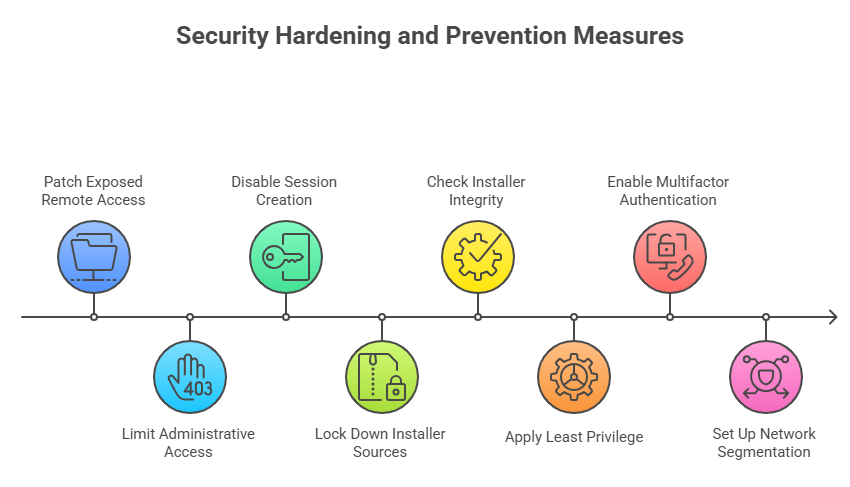
Quickly patch any exposed remote access instances, limit administrative access to ScreenConnect servers, and turn off the ability to create sessions without being logged in. Lock down installer sources and check their integrity before installation to make the attack surface smaller.
Use the least privilege principle on remote tools and turn on multifactor authentication for any account that can give remote access. Set up network segmentation so that one remote session can’t access all of your assets. These steps are normal, but they are very important. Vendor notes and industry advisories stress how important it is to patch and harden configurations quickly.
Useful tips for people and businesses
When it comes to businesses, think of remote support tools as high-risk assets. Keep track of who can start sessions, make installers get permission, and teach staff to question support prompts that come out of the blue. Do tabletop exercises that focus on a remote session compromise so that your playbooks become second nature.
Be careful of sudden requests for help from people, and never paste seed phrases or passwords when a remote session is going on. If you can, use hardware wallets for large amounts of crypto and keep a small, clean device handy for signing transactions.
Question 1: What is AsyncRAT, and why is it bad?
AsyncRAT is a type of malware that lets hackers take full control of a device that has been infected. It can record what you type, steal saved passwords, and even keep an eye on your crypto wallets. The threat comes from its ability to stay hidden while stealing sensitive data.
FAQ 2: How did the attackers use ConnectWise ScreenConnect to do this?
Cybercriminals used the real ConnectWise ScreenConnect tool to send AsyncRAT. They were able to get around user suspicion and get direct access to the systems they wanted by disguising malware as trusted remote support software.
FAQ 3: What can people and businesses do to keep themselves safe from the AsyncRAT ConnectWise exploit?
Patching and updating ConnectWise installations, using strong authentication, and keeping an eye on remote access sessions for strange behavior are all ways to protect yourself. Companies should also spend money on endpoint protection and being ready for incidents. Individuals can protect their crypto by using hardware wallets and not downloading anything that seems suspicious.
What to remember and what to do
The human detail is what makes this story memorable. Attackers used both trust and technology to turn a useful tool into a way to attack. This week, if you do one thing, check who has access to remote support, make sure they have stronger authentication, and look for any strange activity on ScreenConnect.
If you need help figuring out how to deal with this kind of attack or running a threat hunt, a targeted tabletop and incident playbook will pay off quickly. Fixing the small gaps now will save you from having to clean up a lot later.
AsyncRAT exploits legitimate tools like ConnectWise to target sensitive data. Hoplon Infosec’s Endpoint Security monitors, detects, and stops such threats with advanced malware detection and behavioral monitoring, keeping your organization protected against evolving attacks. Stay ahead with Hoplon Infosec.
Follow us on X (Twitter) and LinkedIn for more cybersecurity news and updates. Stay connected on YouTube, Facebook, and Instagram as well.
Share this :