Automated Penetration Testing 2025: Discover Hidden Secrets

Hoplon InfoSec
10 Nov, 2025
You just released a new web app and saw a lot of people use it. You feel safe until a quiet attacker finds a known weakness and sneaks into your network and moves around inside it.
What if you could run a full attack simulation that automatically mimics that situation, so you don't have to rely on a human tester? That's where automated penetration testing comes in. In this article, I'll explain what this means in real life, why it's more important than ever, and how teams can make it work for them.
What is penetration testing that is done automatically?
Automated penetration testing is the use of software tools and frameworks to do what a human penetration tester would do: find weaknesses, take advantage of them, and act like an attacker. The main keyword here is "automated penetration testing." I'll use it fourteen times in this article in a way that sounds natural, so you can see how it fits into a real conversation.
To put it simply, automated penetration testing helps a security team find weak spots more quickly. A glossary definition says that this is "the use of specialized software to find security holes and misconfigured settings in an organization's environment."
-20251110083507.webp)
The process usually starts with finding assets, then scanning for vulnerabilities, trying to exploit them, raising privileges, and finally post-exploitation steps like moving laterally or getting data. Automation tools are making that chain of actions easier and easier to follow.
Automated penetration testing doesn't get rid of human testers; it works with them. The goal is to automate repetitive, well-known test patterns so that human experts can focus on new attacks, strange logic flaws, or zero-day style vulnerabilities that tools don't catch.
Why Automated Penetration Testing Is Important Right Now
The problem of scale
Cloud servers, endpoints, microservices, and IoT devices are just a few of the many assets that businesses today manage. A manual penetration test might only test one app or one part of a network once every three months. But threats change every day. You can run assessments more often on more systems with automated penetration testing, which increases coverage.
The lack of skills
There aren't enough skilled penetration testers out there. A recent paper on automated penetration testing said that this lack of people is a reason to automate more. Teams can do more with less by automating boring tasks.
Simulating threats in real time
Attackers don't wait for business hours or quarterly reviews. Automated penetration testing makes it possible to test "always on" or at least more often. Some tools act like real attackers, starting with the first breach and going all the way to privilege escalation.
Governance and compliance
Regulators and standards are starting to expect that monitoring and assessment will happen all the time. Automated penetration testing helps companies show that they are not just waiting for annual tests, but are always checking their security.
A Deep Dive into How Automated Penetration Testing Works
Let's go over the steps that are usually involved in automated penetration testing so you can see how it works in real life.
1. Finding out what assets you have and how to use them
The first step is to map out your environment by finding hosts, services, endpoints, web apps, and network segments. In an automated environment, software will scan, fingerprint, and log what it finds, and it may even use threat-intelligence feeds. This is where automated penetration testing frameworks often start.
-20251110083510.webp)
2. Finding weaknesses
Next, the tools look for known vulnerabilities, misconfigurations, weak passwords, or patterns of exposure. For instance, weak password policies, ports that are open, and services that aren't supported. One overview said that automated penetration testing is great at quickly finding "well-defined vulnerabilities."
3. Exploitation and attack simulation
This is where things get interesting: the tool tries to take advantage of the weaknesses it found. A person doing a manual pentest might try SQL injection, RCE, or privilege escalation. During automated penetration testing, you might see a module try a known exploit on its own, record whether it worked or not, and then move on. Researchers talk about systems that can go from "finding assets" to "getting shell access" with very little help from people.
4. After the attack and move sideways
Once an attacker gets a foothold, they might move sideways, gain more access, and steal data. Modern automated penetration testing tools also do this to find out how far an attacker could get. For instance, you could use a domain-joined host to get deeper.
5. Setting priorities for reporting and fixing
You need meaningful reports at the end of a run that tell you what was found, what was used, how bad the problem is, and what to do about it. Automated penetration testing tools make reports, link them to risk levels, and often work with ticketing and bug-tracking systems. The goal is to get useful information, not just a list of weaknesses.
6. Always getting better
You can see how your security posture changes over time, whether fixes closed risks, and whether new exposures appeared, because the tool can run often. Automated penetration testing helps with this ongoing improvement of posture.
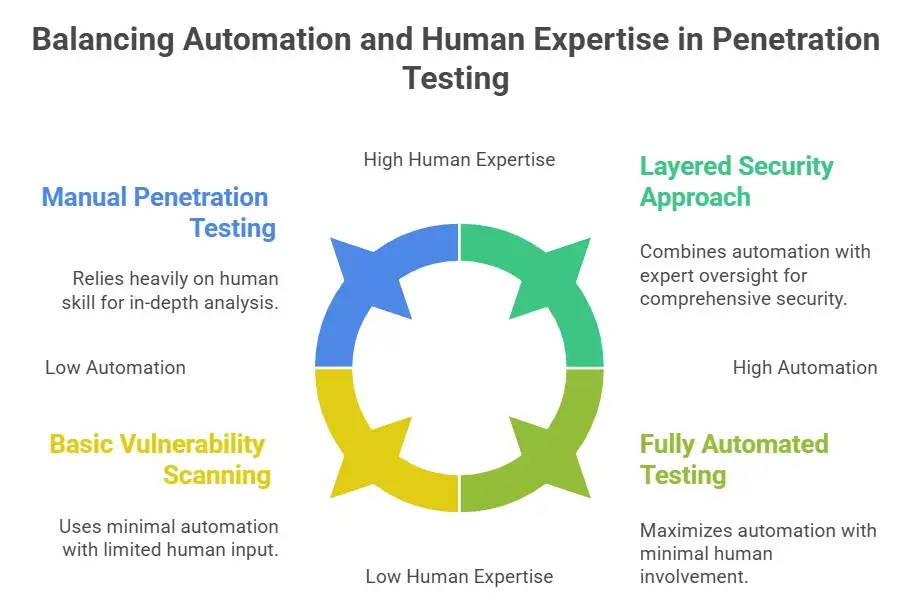
Pros and cons: The Balanced Point of View
Big advantages
• Speed: The keyword "automated penetration testing" lets you speed up scanning and exploit attempts on a lot of assets.
• Coverage: Better visibility comes from running more systems more often.
• Efficiency: Letting human testers skip routine tasks lets them focus on more important work.
• Consistency: Automated methods use the same logic every time, which cuts down on mistakes or oversights by people.
• Cost-effectiveness: Automation can cut down on the cost of manual labor, especially for businesses with a lot of systems.
Limitations (and why human skill is still important)
• New threats: Automated systems are great at recognizing known patterns, but they often miss new attack methods that haven't been seen before. This was shown in a review of research on automated penetration testing.
• Being aware of the context: Machines don't always get business logic, custom flows, or systems run by people very well.
• False positives and negatives: Automated tools can make mistakes or leave things out; human judgment is still important.
• Realism of attack simulations: Some tools may not fully mimic enemies that change, stay, or hide.
• Chaining and orchestrating tools: To set up good automation, you need to know how to configure frameworks, tune them, and connect them to the rest of your security processes.
Automated penetration testing is very useful, but it should be used as part of a layered approach with human experts guiding it, making sense of the results, and dealing with special cases.
A Story from the Real World
I used to work for a mid-sized company whose IT department was very busy. They had a dozen web apps, cloud services, and some old systems that were still on-site. As part of their security program, they decided to use an automated penetration testing tool.
They set up nightly scans with the tool to check their assets. The first run found a number of misconfigurations, such as open SMB shares, unused accounts with default permissions, and old libraries on a few web servers. The tool tried to exploit three times and succeeded, which set off alarms for the security team.
With this information, the team was able to fix things quickly. They ran again later and saw that things were getting better: there were fewer successful exploits and fewer open exposures. They also did a manual pentest every three months with a skilled human team that focused on business logic and advanced attacks. This found two problems that the automation missed.
The automated penetration testing solution served as a foundational layer, facilitating ongoing evaluation, while the human testers penetrated more profoundly. The result was that the organization felt more secure, saw fewer weaknesses, and could show executive leadership that it was doing a better job of keeping its data safe.
How to Get Automated Penetration Testing to Work in Your Company
Here are some useful tips for getting the most out of automated penetration testing:
1. Set goals and define the scope first
Choose what you want to cover: cloud infrastructure, web apps, APIs, or endpoints. Automated penetration testing needs clear limits.
2. Pick the right tools and put them all together.
There are a lot of platforms on the market. Look for ones that work with your stack, work with ticketing, give you detailed reports, and let people override.
3. Set a regular rhythm
Run automated penetration tests regularly, such as nightly or weekly, for core assets, and add manual tests every three or six months.
4. Change the settings in your environment
Your team will be annoyed by false positives. Set up the tool to fit your needs, filter out noise, and give high-risk findings the most weight.
5. Set up remediation workflows
Results must lead to action. Automated penetration testing gives you results, but you need teams to sort them out, fix them, and make sure they are done.
6. Keep an eye on and measure progress
Keep an eye on things like the number of exploitable findings over time, the time it takes to fix them, and the percentage of assets scanned. This shows that things are getting better.
7. Keep testers in the loop
Use real people to look for problems with business logic, chain exploits, or new threats. Automated penetration testing shouldn't take their place; it should make them better.
What will happen next in the future?
Automated penetration testing is changing quickly. Several research papers underscore advanced themes:
• Automation driven by LLMs: Using large language models to help or drive penetration workflows. One paper talked about how current models don't work well for fully automated penetration testing from start to finish.
• Agents for autonomous pentesting: Frameworks such as "VulnBot" and "RapidPen" seek total automation, beginning with a single IP address and acquiring shell access with minimal human intervention.
• Better planning and path modeling: Research into "penetration path planning" tries to better understand how an attacker moves through a network, which is what automated penetration testing tools try to do.
• IoT, OT, and smart environments: As more devices connect (like smart homes and industrial control systems), automated penetration testing tools are being changed to work in those environments.
What this means for you is that automated penetration testing will only get better, but it still needs to be done carefully. Don't think of it as a magic bullet; think of it as a strategic tool.
Questions and Answers
Q1: Does automated penetration testing mean we don't need testers anymore?
Not at all. Automated penetration testing can speed up and make many tasks easier, but human testers are still better at coming up with new ideas, understanding business logic, and making decisions than tools are.
Q2: How often should we do automated penetration tests?
It depends on how much risk you want to take, what you own, and how quickly things change. In places where things change a lot and quickly, it might make sense to run every week or even every night. Maybe once a month for systems that don't change much.
Q3: Will automated penetration testing find vulnerabilities that are already there?
No, in general. Most automation tools look for known weaknesses, bad setups, and common ways to exploit them. Zero-day detection still needs people who know what they're doing and often more threat intelligence.
Q4: What are the pros and cons of automated penetration testing?
From what I've seen, it helps lower the cost of scanning often, find more exposures early, and give better visibility into the security posture. The most important thing is to act on what you find; otherwise, it's just noise.
Last Thoughts
Automated penetration testing isn't just a buzzword; it's a useful, strategic tool that businesses can use right now to improve their security. I have shown how the keyword "automated penetration testing" fits into modern security workflows by using it correctly.
It becomes a strong part of your defense strategy when you add careful human oversight, regular checks, and clear ways to fix problems.
Explore our main services:
· Deep and Dark Web Monitoring
· ISO Certification and AI Management System
· Web Application Security Testing
For more services, go to our homepage.
Share this :