The Best Mobile Security Compliance Software in 2025

Hoplon InfoSec
14 Oct, 2025
In 2025, it's no longer optional to make sure that mobile devices meet security and regulatory standards. If your users use smartphones or tablets to access corporate email, sensitive records, or internal applications, the software you choose needs to do more than just block bad apps. It also needs to constantly check the health of the devices, work with your access policies, and make evidence that is easy for auditors to understand. This article looks at the best mobile security and compliance platforms of 2025, talks about how to choose between them, and gives examples of how to use them in common business situations.
What Mobile Compliance Tools Need to Do in 2025
Any solution you look at should meet a few basic needs. First, it needs to support continuous posture validation, which means that the device's state, threat signals, OS versions, and app integrity are checked all the time, not just when the user signs up. Second, it should work with your identity and access stack so that risk signals can automatically lower or take away access. Third, there must be easy access to reporting and auditor-grade evidence (not "export this CSV and hope it matches your control framework"). Fourth, it has to work with the mix of devices in your environment, which could include iOS, Android, and maybe even Windows or Chromebook. Finally, when people are allowed to bring their own devices (BYOD), the tool should protect company assets without needing everyone to sign up for it.
With those requirements in mind, here are the best candidates for mobile security compliance in 2025.
Defender for Endpoint and Microsoft Intune
Intune is still the best UEM (Unified Endpoint Management) solution for businesses that are part of Microsoft's identity ecosystem. It is especially powerful today because it combines mobile threat defense (MTD) signals with its compliance engine. Conditional Access can automatically block risky devices (like those that have been rooted or jailbroken, have a malicious app, or have been hacked into a network) from accessing sensitive resources.
Intune has built-in support for third-party MTDs like Zimperium, Lookout, and Check Point, so you don't have to stick with one vendor. Microsoft made it easier to set up these connectors in 2024, so many use cases no longer need traditional Conditional Access policies. This cuts down on configuration time. Adding threat signals to Intune, which already manages policies, patching, app provisioning, and profile enforcement across iOS and Android, gives you a single posture model.
Intune also has built-in reporting and compliance dashboards for audit and compliance teams. You can connect your control framework (like CIS or NIST) to device settings and posture signals and then export evidence that is updated on a regular basis. Many businesses choose Intune as their main mobile compliance layer because it lets them see everything from the device to the access point.
The Jamf Ecosystem includes Jamf Pro, Compliance Editor, and Trusted Access.

When most of your fleet is made up of Apple devices, Jamf has a more polished and audit-friendly way to do things. You can set baselines based on the mSCP (macOS Security Compliance Project) and NIST frameworks using the Jamf Pro management platform and the Jamf Compliance Editor. You can then enforce these baselines on iOS/iPadOS/macOS. The rules you make don't just stay as paperwork; they become living policies.
Jamf's "Trusted Access" layer links identity, device posture, and application access so that only devices that meet your compliance standards can get full access. Jamf is still a great choice for Apple stores that want tight control, clear rules, and better conversations with auditors.
One good thing about Jamf is that its compliance baselines often come with prebuilt mappings to common control frameworks. This means you don't have to spend as much time translating what auditors say into technical settings. The platform's reporting features, such as status dashboards and control maps that can be exported, also make it easier to gather proof during audits or reviews.
Kandji: Apple Management with a Focus on Compliance
Kandji has made itself a lean, modern Apple-only option that works best for compliance workflows. Kandji can find state changes more reliably and almost in real time, without having to wait for device check-ins, thanks to its support for Apple's Declarative Device Management (DDM). This makes it easier to enforce good posture.
Its "one-click" compliance templates, like CIS benchmarks, let you enforce a lot of controls with very little setup. Auditor mode and read-only views let compliance teams check the status of a device without worrying about configuration drift. Kandji is a popular choice for Apple-first companies that need mature compliance practices because it is easy to use and ready for audits.
VMware Workspace ONE and Workspace ONE Mobile Threat Defense
Workspace ONE is still a full-featured UEM if your environment really does include iOS, Android, and possibly Windows devices. Workspace ONE lets you do posture checks, risk scoring, and flexible enforcement because it has built-in Mobile Threat Defense (or works with third-party MTDs).
Workspace ONE lets you manage your devices in different ways, such as BYOD, corporate, or COPE, and it lets you change settings easily. Its reporting and dashboards are well-developed, and its threat detection can block, quarantine, or limit access based on risk. Together, these features make it possible to have a single compliance posture across many types of devices.
Top Mobile Threat Defense Add-Ons: Zimperium, Lookout, and Harmony Mobile

MDM or UEM platforms alone can't find zero-day threats, advanced rooting, app exploits, or network attacks in a lot of places. That's why the best MTD providers are still important. Here is a quick look at some important people and how they help with compliance.
Zimperium is known for its strong ability to find threats on devices (apps, OS, and networks). It works with Intune to help companies stay compliant while being aware of risks. Devices that aren't enrolled can still get protection from app protection.
Lookout Mobile Endpoint Security: It does a great job of protecting against phishing, app threats, and network risks. It works with Intune to turn threat signals into compliance gates.
Check Point Harmony Mobile: This is especially helpful if your company already has a Check Point firewall or VPN setup. It can automatically install on enrolled devices and use risk data to make access decisions.
Your compliance engine (like Intune) can use these MTDs to decide if a device is safe enough to access sensitive systems. If it isn't, it will automatically block or fix it.
Comparison Table of Leading Platforms
In the table below, we compare platforms across key dimensions relevant to compliance decision-makers.
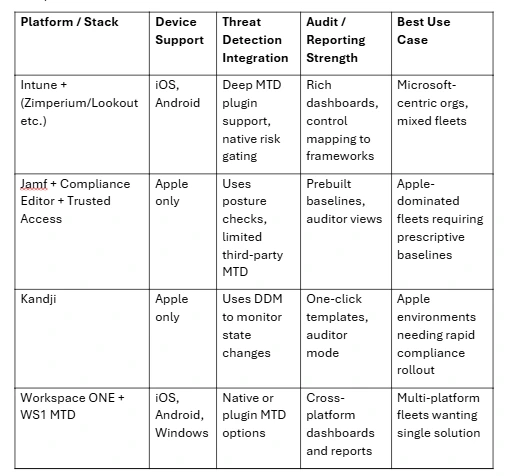
This table helps you see where each solution excels and how they align to your device mix, audit needs, and security expectations.
Which Stack Should You Pick?
Environments that focus on identity
Intune plus a threat provider (Zimperium or Lookout) makes sense if your identity is important for access control (like Azure AD or Entra). You'll get native posture gating, easy-to-understand compliance policy definitions, and a single device posture fabric.
Environments that are all about Apple
Jamf or Kandji are better for businesses that rely heavily on iOS and macOS. If you already use or plan to use Jamf Pro, choose Jamf. If you want a lighter, more modern tool that can be deployed quickly for compliance, choose Kandji.
Environments with Different Devices
If your fleet has both iOS and Android (or possibly Windows), Workspace ONE is a mature cross-platform solution that can centralize policy, posture, and threat enforcement in one place.
Compliance That Knows About Threats
No matter how good a UEM is, it can't find zero-day exploits, rooting, or attacks at the network level. If your compliance posture needs strong device assurance, that's why you need to pair with a mobile threat defense engine. Your UEM becomes the gatekeeper, and the MTD becomes the sensor.
Teams that are small or care about costs
If your company is smaller or you don't have a lot of money, you might want to look into lighter UEMs like Hexnode, Scalefusion, and ManageEngine MDM Plus. Many of them now support posture checks, app control, and basic compliance reporting, which is enough to meet the requirements of many audit frameworks.
Advice on how to make compliance work
Start by linking your control framework (like CIS, NIST, or ISO) to the settings on your devices, the signals they send, and the rules for using your apps. Set clear rules for what kinds of violations are okay (warnings) and what kinds of violations must stop access. At the start of your rollout, turn on threat connectors so that your compliance engine can see risk and not just configuration.
For BYOD users, use app protection (containerization) to enforce posture inside corporate apps without requiring full enrollment. Use declarative management whenever you can, especially on Apple, so that posture updates happen almost in real time. For audits, keep a clean evidence pipeline with control mapping dashboards, compliance reports that can be exported, and peer reviews of policy drift.
Finally, make sure the stack is easy to handle. Don't sew together too many tools that don't go together. A tightly integrated UEM + MTD + identity setup makes things easier, fills in gaps, and gives auditors a clear picture of how things are going.
Conclusion
Mobile security compliance requirements have become stricter in 2025. Locking devices isn't enough; your tools need to constantly check posture, include threat signals, and feed directly into decisions about who can access what.
If your infrastructure is based on Microsoft identity, the best combination is Intune and a top MTD. Jamf or Kandji can help Apple-heavy fleets keep their compliance processes simple. Workspace ONE is a great all-in-one solution for environments that use more than one platform. No matter which option you choose, making sure that your UEM and MTD work well together makes sure that compliance isn't just a theory; it's something that can be enforced and audited.
Share this :