BlackLock Ransomware Strikes Windows, Linux, and VMware ESXi

Hoplon InfoSec
22 Sep, 2025
BlackLock ransomware
Picture this: you walk into your office one morning and find that all of your files, servers, and even your cloud backups are locked up with a digital padlock. A scary note flashes on your screen: pay up or your most private information will be posted on the dark web. This is not a made-up thriller. When BlackLock ransomware hits, it’s the worst thing that can happen to a business.
I saw a small business go out of business because of a ransomware attack. One computer started acting weird, and it all began. The whole network was quiet within an hour. Their client files were gone, and their systems were frozen. Attackers rely on that silence that makes you feel helpless. BlackLock ransomware is meant to make people feel shocked and desperate at that exact moment.
What is the BlackLock Ransomware?
BlackLock ransomware is a fairly new threat that appeared in the world of cybercrime in 2024. Before it got its current name, researchers connected it to an older group called Eldorado. The change in branding was more than just looks. It showed how the group had grown from a small player to a big one. Based on the way they write code and act online, security experts think that the people behind it speak Russian.
The group didn’t just show up out of nowhere. It looks like they had been testing things out for months before they showed up on underground forums. By 2025, BlackLock ransomware was already known for spreading to many systems and going after industries with a lot of money.
The Business That Makes Malware
The Ransomware-as-a-Service model is one reason why it has grown so quickly. In this system, the main developers keep the malware and rent it out to other people. The affiliates do the attacks, and the developers give updates, leak sites, and help with technical problems. Both sides get a cut of the money from successful ransoms.
This setup lets the threat grow. BlackLock is available for rent to skilled hackers who don’t have time to make their own ransomware. In the meantime, the developers are working on making the code better and getting more affiliates. It is a business structure that is like a startup, but it is based on crime.
Systems Under Fire
BlackLock ransomware is different from other types of ransomware because it can attack more than one platform. This new type of ransomware doesn’t just attack Windows like older ones did. It also attacks Linux and VMware ESXi. That means it can bring down not just personal computers and servers, but also big virtualized environments that run important apps.
The version for Windows is better. It can delete shadow copies, go through shared folders, and even take credentials to get to remote drives. The Linux version is simpler but still harmful; it focuses on encrypting files and directories. For ESXi, the ability is there but still in the works. Some features are hinted at in code but aren’t always fully active.
Inside the Attack Chain
When BlackLock ransomware is started, it first reads commands. Attackers can choose which folders to attack, which files to ignore, or even whether to encrypt local disks instead of network shares. These choices give affiliates a lot of freedom.
Strong algorithms are what make the encryption work. ChaCha20 and elliptic curve techniques work together to make it almost impossible to recover data without the attacker’s key. Encrypted files have metadata attached to them so that the attackers can give you a working decryption tool after you pay the ransom. Data is being stolen in secret at the same time as this process.
More Than Just Locked Files
The double extortion strategy makes things even worse. Even if a company has good backups, the theft of data changes everything. If you don’t pay the ransom, your private records, customer information, or unique designs could be made public online.
Victims are stuck in a painful situation. Restoring systems from backups might fix the operational problem, but it won’t stop leaked files from hurting the company’s reputation. After such leaks, regulators and clients often act quickly. The attackers are betting on this fear.
Pressure Through Leak Points
The people behind BlackLock ransomware run data leak sites that they use to put public pressure on people. These sites list victims and sometimes show samples of stolen files. Researchers who tried to keep an eye on them saw tricks that were meant to make things harder. When you try to download something, it might come back with empty files, or the system might slow down browsing.
These kinds of tactics aren’t random. They make things less certain and force victims to talk things over. If you can’t see all the data that was taken, you’re more likely to think the worst. This mind game is just as important as the encryption itself.
First Steps to Getting on a Network
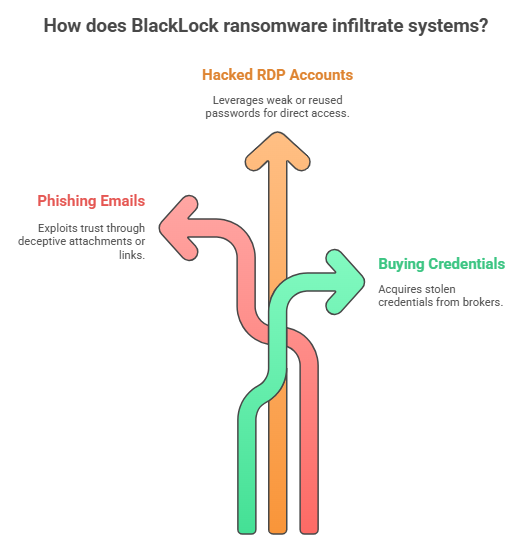
How does BlackLock ransomware get in in the first place? Affiliates have a lot of options. Phishing emails are still a common way to do this. An email with an attachment or link that seems real can give attackers the chance they need.
Another way is to use hacked Remote Desktop Protocol accounts. Weak or reused passwords let hackers get into systems right away. Affiliates also buy access from brokers who are good at selling stolen credentials. This ecosystem makes it hard to block every way in.
Going Deeper Into the System
Once they get in, the attackers don’t usually stop at just one machine. BlackLock ransomware is made to spread sideways in search of administrator accounts or shared drives. People often misuse tools like PowerShell or PsExec to run programs on other computers.
The malware looks for network shares and drives that are connected to them so it can encrypt them. It will try to delete shadow copies on Windows computers, making it less likely that you can easily restore them. It focuses on paths that the attacker gives it on Linux servers. This ability to spread across the network makes the effect stronger.
Important Technical Choices
The Go programming language is one reason why BlackLock ransomware can run on many different platforms. Go makes it easier to build for multiple platforms, so you can use the same code base to make versions for Windows, Linux, and ESXi.
It also takes a lot of command-line arguments, which gives affiliates control. They can choose which directories to attack, whether or not to include network shares, and which machines to leave alone. This flexibility makes it different from older types of ransomware that didn’t give you as many choices.
Who Are the People Who Were Hurt?
There are a lot of different kinds of victims. BlackLock ransomware has been seen in the government, healthcare, education, construction, and manufacturing sectors. It has hit businesses in North America, Europe, and Asia. Companies of all sizes, from small to large, have used its leak sites.
It’s interesting that some areas are missing. BlackLock, like many other ransomware groups, doesn’t go after targets in Russia or some of its neighbors. This pattern gives a hint about where its operators might be based or where they want to stay out of the spotlight.
When the attackers make a mistake
Groups that are well-organized can still mess up. A flaw in BlackLock’s leak site once made it public, showing internal logs and server information. At another time, a rival group broke into their site, made fun of them, and messed up their work.
These kinds of mistakes hurt the group’s reputation with its affiliates. Reputation is important in the underground world. If affiliates don’t trust you anymore, they might switch to other ransomware families. These flaws show that even strong threats can be beaten.
Signs that an attack is still going on
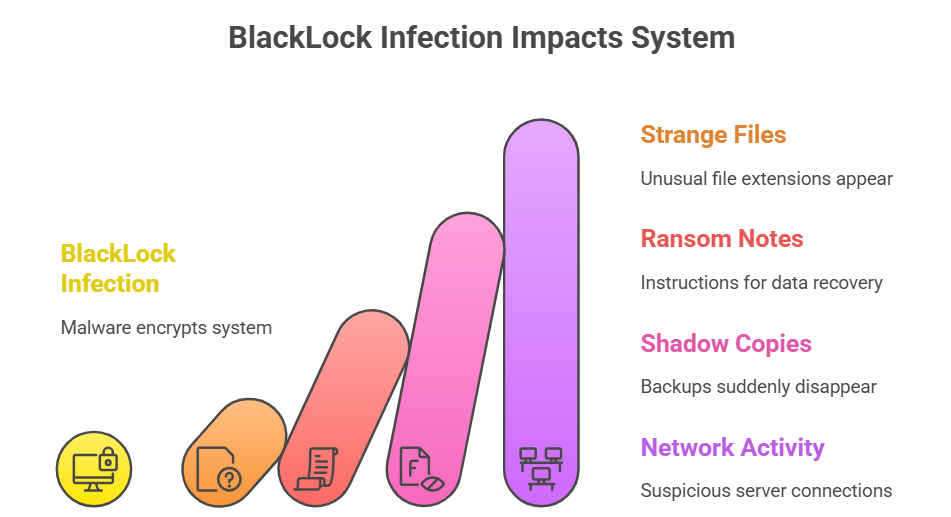
Defenders have found some signs that a BlackLock infection is present. Files with strange extensions, ransom notes with the title “HOW_TO_RETURN_YOUR_DATA.TXT,” and shadow copies that suddenly disappear are all signs of trouble.
Heavy scanning of SMB shares or connections to suspicious servers are examples of strange network activity that could mean trouble. Finding out about an attack early can make a big difference because it gives defenders a chance to stop it before full encryption starts.
How to Protect Yourself from the Threat
There isn’t one answer, but there are a few things you can do to lower the risk. It’s very important to back up your files regularly offline. During an attack, backups that are only stored on the same network could be lost. All accounts that allow remote access should have multi-factor authentication turned on.
All of these things help: keeping systems up to date, limiting services that aren’t needed, and keeping an eye on network traffic. Training employees to recognize suspicious emails or attachments is just as important. A lot of attacks start with a single click. A tested incident response plan can stop things from getting out of hand during a real crisis.
What the Future Might Bring
BlackLock ransomware is not just another type of malware. It shows how cybercrime is set up, sold, and done in the modern world. It takes advantage of both technical flaws and people’s fears. It works on all operating systems and threatens victims with leaks to get what it wants.
The lesson is clear for businesses and organizations. Protection isn’t just about keeping machines safe; it’s also about being ready for the possibility that stolen data could be used as leverage. The defense includes strong backups, strict access controls, and being aware.
If you don’t pay attention to these warnings, you might wake up one morning to find your screen locked and wonder if the world is about to see your company’s secrets.
Share this :