Chrome security update vulnerability patch: Fixes critical remote code execution; update now.

Hoplon InfoSec
10 Sep, 2025
Chrome security update vulnerability patch
I still remember the morning my colleague walked into the office with that same worried look you get when your phone shows 99 percent battery and then dies. We had users, servers, and a small army of browser extensions to worry about. A fresh security note arrived, and it was short, urgent, and strangely familiar.
That note announced a critical fix and, in plain terms, told everyone to update. The phrase that kept showing up in my head was simple and blunt: look after your browser. For the rest of this piece I will unpack that alert, explain what it means for you, and give a clear checklist to act on.
What happened: the short story of the patch
A recent release closed a serious hole that allowed attackers to run code remotely on an affected machine. That scenario is the one every security person hates, because it removes the barrier between a malicious web page and control of your system. The update was brief but important, and it landed as a routine security note with a recommended immediate upgrade.
For most users the fix is straightforward: update the browser and move on. For businesses and administrators there are extra steps, so the simple headline hides the chain reaction a single flaw can cause. In a crowded environment, one patched browser is not enough; you need coverage and confirmation.
Why remote code execution is so dangerous
Remote code execution is the technical name for letting a stranger make your computer do things. Imagine someone you do not know walking up and typing at your keyboard without permission. That is what the flaw allowed in theory. The consequences range from nuisance to full compromise depending on how the attacker chains other techniques.
Think of it like a cracked window on a ground-floor room versus a skylight on the top floor. Either way, once there is an opening, a determined intruder can find a way in. The worry is not just data theft. Malicious code can install persistent backdoors, harvest credentials, or turn devices into tools for wider attack campaigns.
How the vulnerability works, in plain English
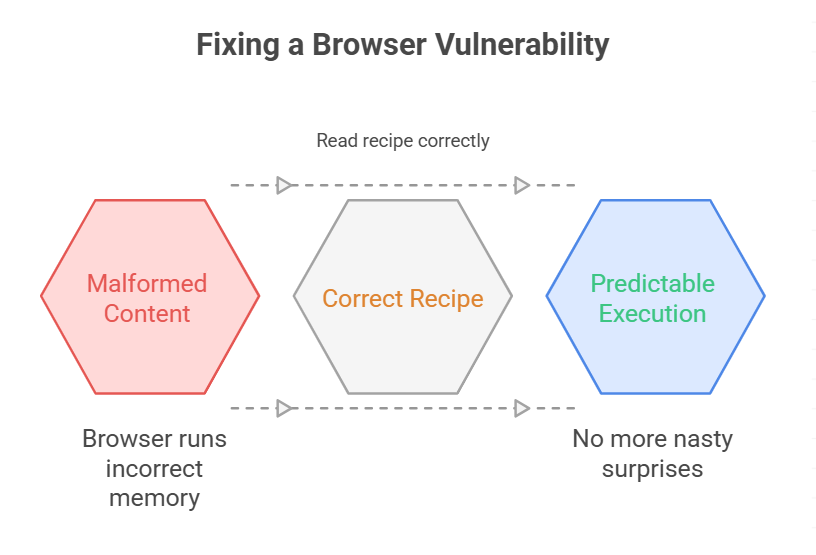
Technically, the bug lived inside a parsing or rendering component that processes content coming from websites. A malformed packet or content piece could trick the browser into running memory it should not. When memory is misused like that, it becomes possible to execute instructions an attacker has crafted.
To avoid drowning you in jargon, picture a recipe book that misreads an ingredient and mixes sugar where salt should be. The result is unpredictable. In computing, unpredictability equals opportunity for an exploit. Fixing the code ensures the recipe is read correctly and the nasty surprises are gone.
Who is most affected, and why does it matter to ordinary users?
Anyone who uses the browser can be affected, but the level of risk shifts with behavior. Casual users who browse trusted sites and keep extensions minimal have lower risk. People who visit unfamiliar sites, click on unusual links, or use legacy plugins are at higher risk.
Devices that share corporate networks or hold sensitive logins are especially valuable to attackers. A single browser compromise on an employee laptop can be the beachhead into the rest of a company’s systems. That is why updating across endpoints matters far more than updating a single home machine.
Timeline: discovery, disclosure, and the patch rollout
Vulnerabilities often follow a predictable rhythm. Someone discovers odd behavior, a researcher or internal security team investigates, and then they notify the vendor. The vendor confirms, develops a fix, and issues a patch, usually accompanied by a security advisory that explains severity and mitigation.
That advisory also triggers a race: defenders push the patch, and attackers analyze the public write-up for exploit ideas. Ideally the window between disclosure and patch availability is small. Realistically, every hour matters, and that is why prompt updates are the repeated refrain in every security bulletin.
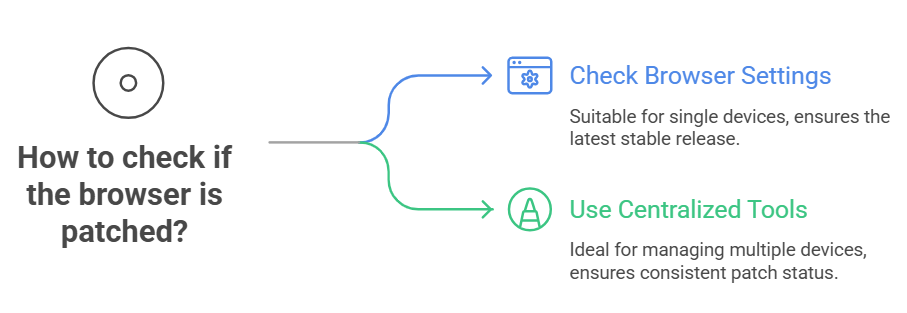
How to check whether your browser is patched
Open the browser menu, go to settings, find About, and let Chrome check for updates. The status will tell you whether you are on the latest stable release. If an update is available, install it and restart the browser; that typically completes the patch.
For other platforms, such as managed workstations or older operating systems, check the update channel or your patch management console. A manual check is fine for a single device. If you manage many devices, use centralized tools to confirm patch status rather than relying on whispers in Slack.
What enterprise and IT teams should do now
If you are in charge of multiple machines, don’t rely on individual users to update. Use enterprise management tools to force the updated version, test the rollout on a subset of machines, and then push broadly. Logging and reporting will show which endpoints still need attention.
Communicate clearly. Tell users what to expect, provide update windows if reboots are required, and keep a fallback plan for mission-critical systems. Coordination reduces panic and prevents users from taking risky shortcuts to avoid downtime.
Indicators of compromise and what to watch for
A browser-level compromise can leave subtle signs: unexpected popup activity, new processes spawned by the browser, sudden changes in browser settings, or unusual outbound network connections. Detection often requires looking at process trees and network logs.
If you spot these signs, isolate the device, collect logs, and scan for persistence mechanisms like new services or modified startup entries. Treat the incident as potentially serious, because what starts as a browser issue can escalate quickly into a full endpoint breach.
Short-term mitigations if you cannot patch immediately
If an immediate update is not possible, reduce exposure. Disable unnecessary extensions, restrict browsing to trusted sites, and block potentially dangerous content via enterprise policies. For high-risk users, consider temporary network segmentation.
Another tactical move is to enable additional browser hardening features, such as site isolation, stricter plugin policies, or controlled sandbox settings. These measures do not replace a patch but buy time while you stage updates.
Real-world examples and mini case studies
In one mid-size firm I worked with, a delayed browser patch led to a phishing email exploiting an unpatched rendering flaw. The result was credential theft and a costly cleanup. We learned that manual patching across 300 devices is a coordination problem, not a technical one.
By contrast, another team with automated updates pushed the patch within hours and experienced no impact. The difference was process, not luck. The lesson is blunt: automation and governance blunt the sharp edges of these vulnerabilities.
Impact on extensions and third-party integrations
Extensions and plug-ins complicate the picture because they add functionality that can also carry risk. A patched browser helps, but extensions that request broad permissions may still amplify damage if they are malicious or compromised.
Audit your extension inventory. Remove rarely used items and prefer extensions from reputable authors. For organizations, apply allow lists and block lists so only vetted tools can run. This reduces the attack surface even when browser code has been tightened.
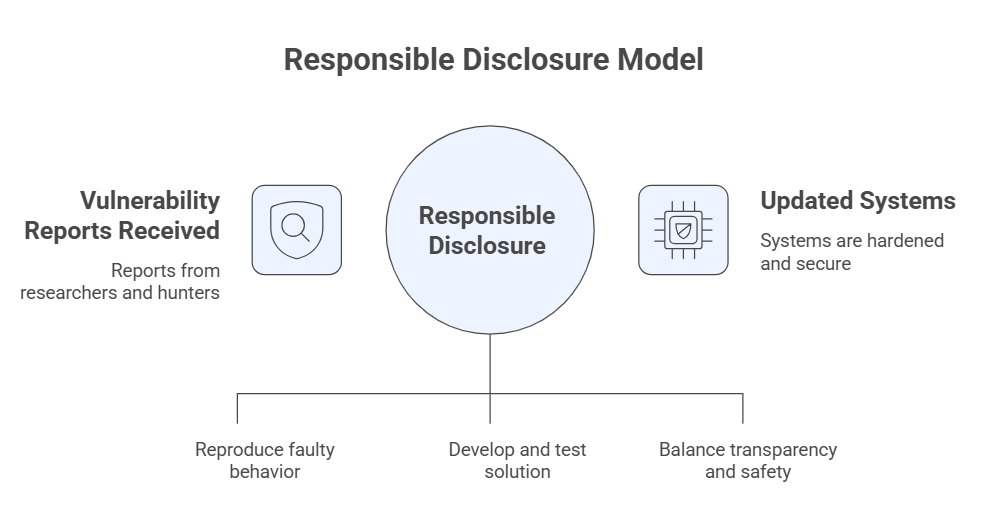
How Google finds, fixes, and discloses these flaws
Google receives reports from internal researchers and external hunters. Their team triages reports, reproduces faulty behavior, and prepares a fix. The disclosure cadence balances transparency and safety: enough detail to inform users, but not so much that attackers get a ready-made exploit.
This responsible disclosure model has proven effective, but it depends on vendors, defenders, and users acting quickly. The advisory is a starting point for action, not an end. Treat it as a call to update and harden systems.
Long-term lessons for users and admins
Short-term panic fades, but habits matter. Keep browsers and underlying systems patched, use multi-factor authentication so stolen credentials are less useful, and avoid running with unnecessary privileges. Small habits reduce the value of any single exploit.
Also, do not let the horizon lull you into complacency. New bugs will appear. Building simple, repeatable patching practices and training users to recognize risky patterns is both economical and effective. Security is the art of preventing the easy win for an attacker.
Practical FAQ and final checklist
What should I do right now? Update the browser, check extensions, and run a quick security scan. If you manage many machines, verify patch status through centralized systems. If you spot suspicious activity, isolate and investigate.
Keep this checklist handy: confirm update, verify extensions, audit high-risk users, enable extra browser safeguards if needed, and document the action. Treat the advisory as urgent but manageable with the proper steps.
Closing takeaway
This episode is another reminder that browsers are first-line infrastructure. A single flaw can ripple across many systems, and the simplest defense is often the best: install the available fix and verify. When you see a security note, act fast and log the result.
If you follow a steady cadence of updates and good operational hygiene, these alerts turn into small bumps rather than crisis points. Update the browser, check your controls, and move on with the confidence that you reduced a real risk today.
Constant vulnerabilities make every device a target. Hoplon Infosec’s Endpoint Security protects your laptops, desktops, and mobiles with proactive defense, fast patching, and real-time monitoring to stop threats before they spread.
Follow us on X (Twitter) and LinkedIn for more cybersecurity news and updates. Stay connected on YouTube, Facebook, and Instagram as well. At Hoplon Infosec, we’re committed to securing your digital world.
Share this :