Cisco ASA FTD Zero Day Vulnerability PoC: How a Boundary Bug Triggered a Dangerous Authentication Bypass

Hoplon InfoSec
07 Oct, 2025
A small flaw in a device that is supposed to protect your network can often let an attacker in, which surprises me. That's exactly what happened with the new proof of concept (PoC) that was just released for the Cisco ASA/FTD zero-day vulnerability.
You can imagine that your firewall is the wall that protects your surroundings and keeps them safe at some point. People are less likely to trust perimeter fortifications when attackers use them to get in. This time, the attack is really secret. It first gets past authentication, and then it runs code on a computer that isn't close by.
If your company uses Cisco's Adaptive Security Appliance (ASA) or Firepower Threat Defense (FTD) with WebVPN (clientless VPN) turned on, you could already be at risk. The Cisco ASA FTD zero-day vulnerability PoC makes this threat very real. Let me tell you how it works, why it's important, and what you need to do.
What is the zero-day security hole in the Cisco ASA/FTD?
In September 2025, Cisco handed out a security warning to let consumers know about a group of big security weaknesses in its ASA and FTD devices. In the actual world, two of these, CVE-2025-20333 and CVE-2025-20362, have been used.
• CVE-2025-20362 is an issue that lets you get past authentication. It lets users who don't have the right credentials go to web endpoints that should be safe.
• CVE-2025-20333 is a problem with WebVPN's file upload handler that lets too much data into a buffer. In some cases, it lets code run on a remote computer.
They work together to create a fatal exploit chain: they get around the login first, and then they take control via overflowing RAM. Cisco also mentioned a third flaw, CVE-2025-20363, that people would probably use soon. These flaws are especially serious because they affect the WebVPN interface for VPNs. People often turn this option on so that people who are not on the same network can log in over HTTPS. This makes it available on the internet. Because of CVE-2025-20362, attackers may not even need any credentials. The PoC for the Cisco ASA FTD zero-day vulnerability is significantly more deadly now.
Getting around authentication and buffer overflow in the two-stage exploit chain
The exploit chain is more than just a problem. This is a planned set of flaws, and each one makes the next step possible.
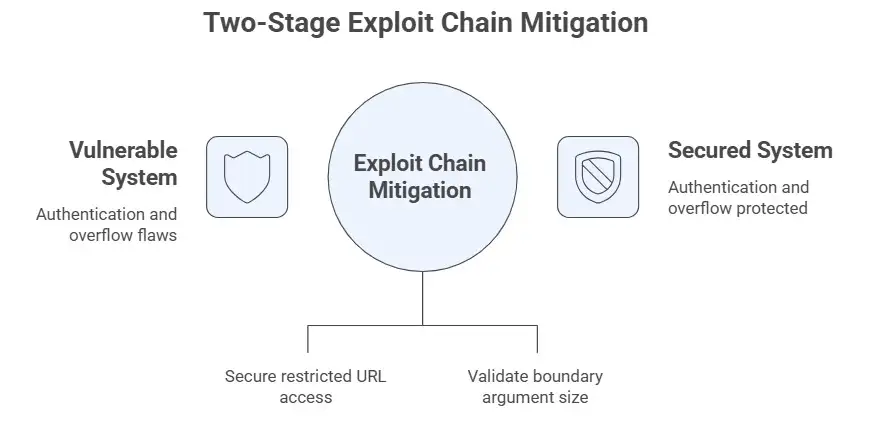
Step 1: Use path traversal to get around authentication.
The entry point is CVE-2025-20362. Attackers can employ path traversal or path normalization weaknesses to go to restricted URLs without logging in since there is a hole in the authorization process.
For instance, a keycard system that doesn't check if you can get to the second floor anymore. You didn't swipe your card, but the door opens. Attackers can utilize the bypass to call endpoints that only logged-in users can access.
If they are successful, the system may send back a message like "CSRF token mismatch" to let them know that the request went through.
Step Two: Start a buffer overflow to get RCE.
The attacker can now reach CVE-2025-20333 because the protected endpoints are no longer closed. This issue is in the Lua script that handles file uploads. It has to do with whether or not it checks a "boundary" argument. The code expects that a size check will happen; however, it doesn't work well in versions that can be hacked.
The attacker provides a boundary string that is bigger than 8,192 bytes, which is the size of the buffer that is thought to be secure. This makes the buffer overflow. This can hurt memory and let anyone run code on the ASA/FTD device with root access. In real life, attackers link stage one to open the door and then stage two to gain control of the gadget. Rapid7's in-depth research supports this exploit chain.
How the PoC and Exploit Work in Real Life
Cisco and researchers first said there was no public proof-of-concept (PoC), but that changed when researchers made vulnerability code public.
The PoC uses the bypass to reach the file upload endpoint. Then it sends a multipart HTTP request with a boundary that is too big, which breaks the RAM. Some versions of the exploit make this easy by connecting the two parts.
The attack worked in the lab on select versions of ASA/FTD firmware, notably on devices that run ASA software 9.12, 9.14, and other versions that weren't fixed.
One difficult factor is that memory layouts are different in real deployments, security measures like ASLR can make it tougher to exploit, and device settings are different. But attackers who are good at tinkering with memory can change it.
In some cases that have been reported, opponents used this exploit chain to put a bootkit (RayInitiator) and a loader (LINE VIPER) on the machine and make sure they stayed there.
An attacker might scan public IPs, discover a WebVPN front end, and then send the request to get around it. If they are successful, they immediately start the buffer overflow process and take control, usually without anyone noticing. That's how the proof of concept for the Cisco ASA FTD zero-day flaw turns into a weapon.
What happens in the actual world: Who is in danger, and what is being attacked?
This isn't just a guess. There are still thousands of Cisco ASA/FTD devices that are connected to the internet that need to be fixed. TechRadar said that the new problems could affect about 50,000 firewall devices all across the world.
The effects are quite big:
• Full device compromise: Once attackers get root access to a device, they can change settings, steal network traffic, create backdoor accounts, turn off logging, and even rewrite firmware or ROM.
• Stealth and persistence: Malware like RayInitiator can change the boot sequence or firmware on your computer so that it stays there even after you restart or upgrade it.
• Network pivoting: The hacked ASA/FTD is at the edge of the network. If you have control there, you can see traffic, get in from the side, and get in even further.
• Espionage and targeted attacks: Many of the attacks that have occurred are espionage attempts that focus on networks that are important to the government, defense, or critical infrastructure.
If you have ASA 5500-X series or Firepower devices that expose WebVPN as part of your infrastructure, your risk is not small, especially if you haven't updated the firmware or turned off services that you don't use.
The Shadow That Attacks is where it comes from.
According to public sources, UAT4356, also known as Storm-1849, is the group that is using these zero-day flaws.
People think that this group is a well-funded threat actor that may have connections to the government. Previously, they ran the ArcaneDoor campaign, which used old zero-day flaws to attack Cisco edge devices.
They use stealthy implants, switch off logs, intercept management commands, cause forced crashes to cover their tracks, and deeply embed themselves in firmware to spy.
It's interesting that the actors seem to be especially interested in gadgets that are no longer supported or are soon to die. It could be because these devices don't have as good of security.
This campaign reminds us that edge devices are more than just walls that don't do anything. A skilled enemy can use them as weapons.
Cisco's answer: updates, alerts, and repairs
Cisco got back to us right away. On September 25, 2025, the company sent out security advisories and software updates to fix CVE-2025-20333, CVE-2025-20362, and CVE-2025-20363.
Cisco said that businesses should immediately upgrade any ASA, ASAv, or FTD devices that are at risk.
Cisco also made it easier for organizations to check for past compromises by giving them tips on how to discover them, look for hazards, and evaluate core dumps.
Cisco also makes it clear that you can't cure both problems at once; you need the patch.
Cisco is also keeping an eye out for "continued attacks" and has sent out updates to let admins know how attackers are acting, such as by switching off logs or intercepting CLI.
But you have to utilize patches for them to work. That leads to detection, forensics, and best practices that will help keep your devices safe.
How to Strike a Balance Between Detection and Forensics
This kind of exploit is hard to find since good hackers like to stay hidden. Defenders can still hunt for clues and use forensic methods.
Analysis of core dumps
Cisco and CISA made it possible to get core dumps from ASA/FTD devices, look at them, and figure out what they mean. Even if logs were deleted, these core dumps can still provide memory traces of the intrusion.
Even if forced reboots are used to delete evidence, researchers may still be able to find traces in flash memory or firmware sectors.
Strange behavior
Check for settings that change without warning, services that start up without warning, strange processes, or new user accounts. You should also search for syslog entries that are blocked, CLI commands that are stopped, and system crashes that are forced.
Another positive clue is when WebVPN endpoints get a lot of HTTP requests with strange lengthy strings or boundary parameters. CVE-2025-20362 is about path traversal; therefore, a lot of broken paths could be a sign.
In comparison to the baseline,
Check the current firmware, configuration, file signatures, and modules against known clean baselines. If something changed, someone could have messed with it.
Forensics on a network
Network records may show strange traffic patterns if hackers steal data or send messages back through WebVPN or ICMP channels. This is especially true when connections are made to unusual IPs or command-and-control sites.
The ASA/FTD device is the gateway; therefore, keeping track of its own traffic and internal logs can help show lateral movement.
Using host forensics, configuration auditing, and network monitoring together can help defenders find a stealthy breach more readily.
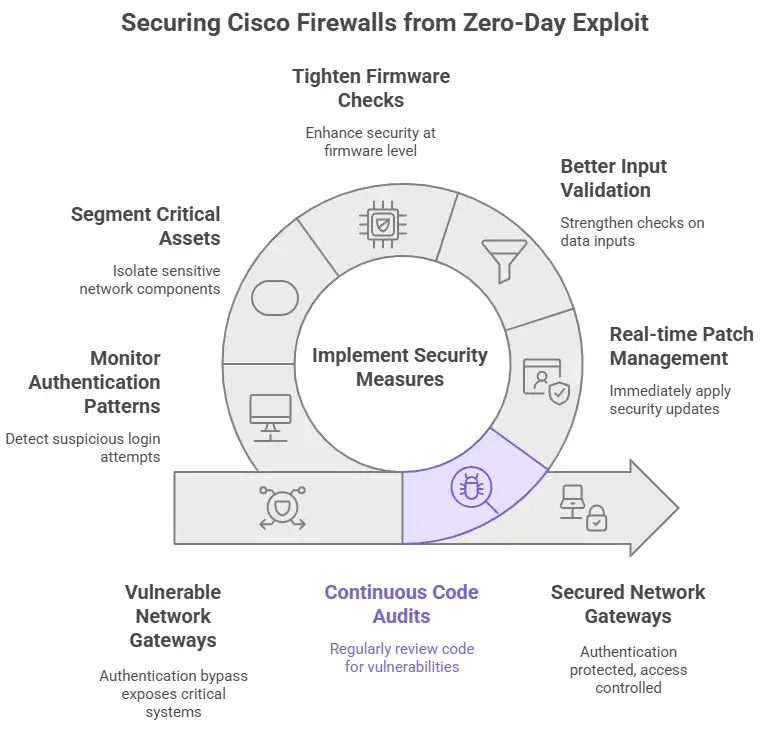
The safest ways to use ASA/FTD devices
Right away, fix it. That's clear, but it can take a long time. The Cisco ASA FTD zero-day issue PoC only works if the firmware is not upgraded. Cisco recommends you should update your devices to the fixed versions.
If you don't need WebVPN (clientless SSL VPN), turn it off. There are fewer ways for intruders to get in because the surface is less exposed.
Limit who can access management interfaces. Allow access to ASA/FTD admin panels only from inside the network, and use network segmentation. Don't allow the general internet to see these kinds of links.
People who need to use the VPN should use multi-factor authentication (MFA) and certificate-based access. Even if one of the holes in this example lets attackers get past security, layered defenses nonetheless help keep them from moving around and limit their reach.
Make sure your logging is strong, but additionally check logs from outside the device (for example, stream logs off the device) so that you still have copies even if logging is turned off on the device itself. Set up notifications to go off right away for things that seem strange.
Make backups of your settings often, but don't let them be changed or saved online. You should go back to a backup that you know is clean and start over if someone compromises your device. You should change all of your keys, passwords, and certificates after you get them back. The attacker may have taken them.
Don't trust anything by default; only give people the access they need. Always keep an eye on everything. If ASA/FTD is hacked, segmentation can make it tougher for the hacker to move about.
Run scans using CVE detectors, look for the Cisco ASA FTD zero-day vulnerability PoC on your own devices, and remember that security is something you should do all the time, not just once.
What Comes Next: The Future of Security for Edge Devices
This event illustrates that firewalls, VPN gateways, and edge devices are very good targets. They are the times when trust breaks out. When we defend them, we frequently think they can't be hurt, but their enemies know otherwise.
There may not be any zero days in the WebVPN, SSL modules, SNMP, or APIs of firewall appliances in the future. Manufacturers of devices need to include more security features for memory, code, runtime, and secure boot in their products.
Network operators should be ready for the worst on the defense side and make sure that a breach of a gateway doesn't mean the end of the world. Microsegmentation and zero trust architectures can stop hackers from getting too far into the network.
Hackers will also change PoCs as soon as they are made public. Teams in charge of security need to work rapidly. Now, you need automation, patch orchestration, and proactive scanning.
Last but not least, government agencies, contractors, and security groups need to work together more quickly. Alerts, shared telemetry, and cooperative defense (sharing threat intelligence) all help stop attacks before they get worse.
People will probably use the Cisco ASA FTD zero-day vulnerability proof of concept incident as an example of how to get ready for both attacks and defenses.
Summary and Key Points
Finding and actively using the Cisco ASA FTD zero-day vulnerability PoC is one of the most audacious assaults in a long time. It's not straightforward to link a bypass to a buffer overflow such that someone can get remote root access to firewall devices.
But the lessons are clear: you have to move quickly. A lot of patching. Make your settings more secure. Never think that something is impossible. And always be on the lookout for strange behavior.
Edge devices like ASA/FTD are no longer just walls that keep people out. They become tools for attackers. Get ready.
By being vigilant, acting quickly, and having a strong defense, we can limit the damage and stay one step ahead.
Cisco's official security advisory on ASA/FTD WebVPN vulnerabilities says, "The vulnerabilities, CVE-2025-20362 and CVE-20333, make up an exploit chain that lets an attacker run code on a vulnerable device without having to log in."
The Box of Hoplon Insight
• Check all of the Cisco ASA/FTD devices near you right away.
• Don't wait to install approved patches; they should be at the top of your list of things to accomplish.
• Turn off WebVPN if you don't need it.
• Limit the number of persons from outside who can access the interfaces for managing devices.
• Send logs to a server and set up alerts for WebVPN queries that don't appear right.
• Use the core dump and forensic methods that Cisco and CISA give you to detect risks.
• Change all of the passwords and keys on hacked devices to set them up again from scratch.
• Use zero trust and microsegmentation to keep a breach from doing too much damage.
Hoplon Infosec’s Endpoint Security protects ASA/FTD devices and network endpoints, offering real-time threat detection, monitoring, and rapid response to keep your systems safe.
Share this :