Critical Cisco IOS XE Remote Code Execution Flaw

Hoplon InfoSec
17 Oct, 2025
I remember the first time I learned that a single bug in network software could make a whole switch act like an open door. I was in a server room watching an engineer fix a stack of switches and talk about how small, hidden services like SNMP had become the most dangerous windows in big networks.
That memory is important because the recent problems with Cisco IOS and IOS XE have made that fear real again. With just one wrong packet or one carefully crafted HTTP request, devices that are the backbone of corporate networks can go from being harmless to being completely compromised.
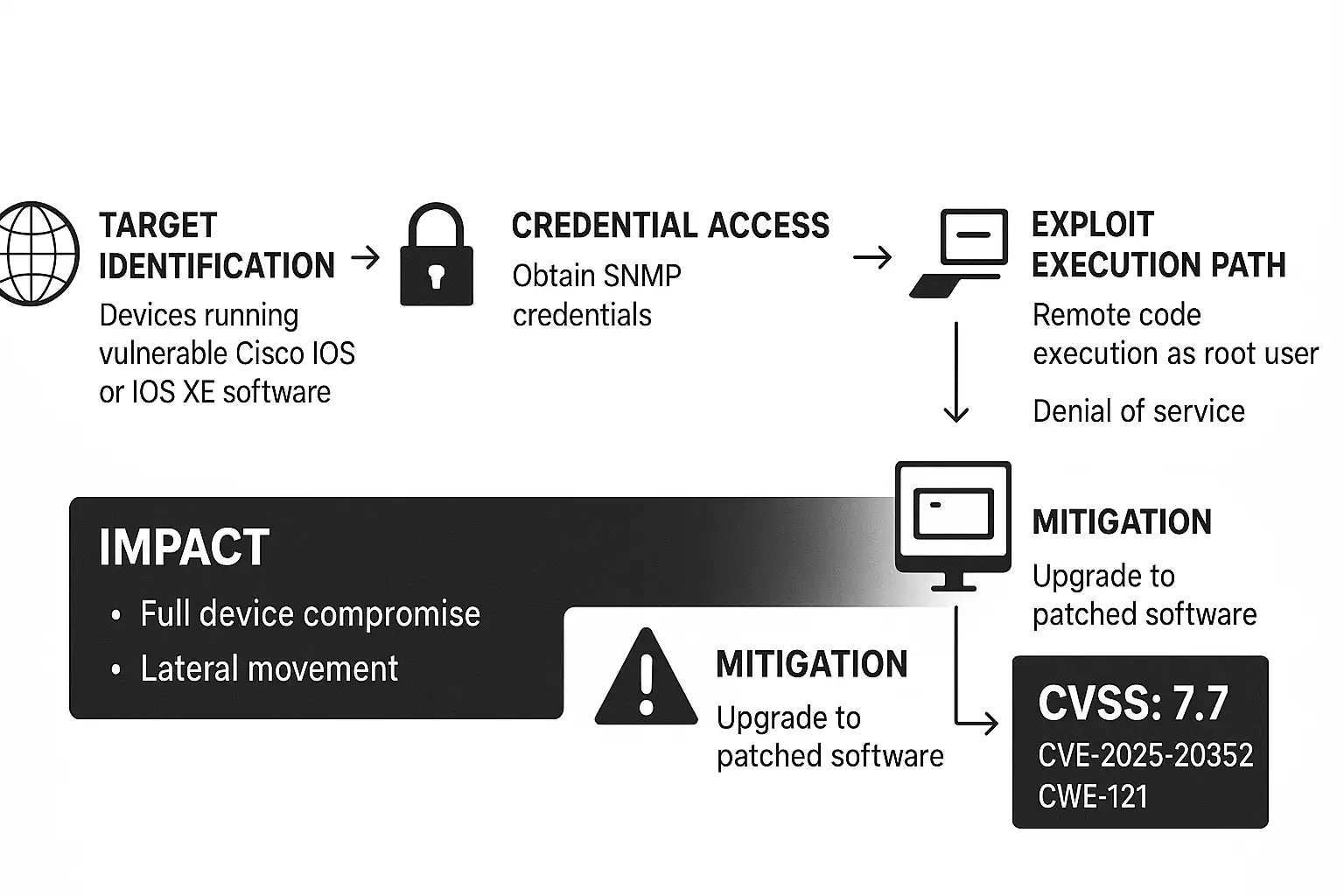
The main problem in the story is one that everyone hates: unchecked input and old services that haven't been updated. This year, the security community pointed out several problems that let remote attackers gain more access and run code as root. An SNMP subsystem fault that can cause stack overflow and a group of HTTP API bugs that let specially crafted requests cause heap or input validation errors were the two that kept coming up in advisories and incident reports.
These flaws have real-world effects because a lot of devices run management services on networks that aren't set up correctly.
Why this is important for you and your network
A network switch is like a small, specialized computer. It has an operating system, a way to manage things, and memory space. If an attacker can find a way to put code into that memory, they can write persistent hooks, make backdoors, or move to other systems. Recent events show that attackers are no longer happy with just causing outages.
They are putting Linux rootkits on infrastructure devices that will stay there. That means the device can still be compromised even after a reboot or a quick fix. Multiple threat reports show that attackers have taken advantage of an SNMP vulnerability to install rootkits on older devices that haven't been patched.
This isn't just a theory if you run networks. For the sake of ease of monitoring, many businesses still use old versions of SNMP. Those same conveniences can be used to attack. It's easy to see what you should do, but people don't always do it. Quickly patch. Check SNMP and management access. Limit those services to management VLANs and VPNs only. But like with any big system, it's easier to say "do the basic things" than to actually do them.
The technical picture in simple terms
Let's talk about how these attacks work without getting too technical. There is a group of problems in the SNMP subsystem. Older SNMP implementations expect requests to have certain sizes and item counts. An attacker can make a packet that overflows a buffer if the code doesn't check the length or bounds correctly. If the attacker knows what memory to target, that overflow can overwrite nearby memory and run any code they want.
In real life, this means that an attacker with even basic SNMP information or community strings can do a lot of damage. The official vulnerability record tells you what you need to do and how to get to the SNMP bug.
Another set of problems is with HTTP services and APIs that respond to requests from management. Web subsystems often read user input, ask internal services for information, and send the results to the OS functions that are below them. If validation isn't done right, a well-crafted HTTP request can mess up heap memory or get around protections and run as the root user.
This is a big risk because management web services can sometimes be accessed from networks outside of the company's own consoles. Vendors have written down how a carefully made HTTP request can cause code to run.
Who is at risk, and how big is the risk?
Big businesses, service providers, and even industrial networks are in danger. Some of the platforms that are affected are older Catalyst models and newer Catalyst 9000 family devices that are running certain versions of IOS XE. Public advisories list the affected releases and show which versions need to be updated in a matrix. Attackers often go after older switches and devices that haven't been updated or were set up with weak or default management credentials.
Because Cisco is used in so many different places, like campuses, branches, cloud edges, and industrial setups, a lot of people are at risk.
Exploitation in the real world is not just a theory. Many security companies and incident response teams have seen active campaigns use these weaknesses to install malware that stays on the system. Some of the activities seen include planting rootkits and enabling remote shells that stay active after a reboot. These reports make it clear that this is a zero-tolerance issue for important networks.
Finding and quickly hunting down steps
If you think your account has been hacked or want to be proactive, start with an inventory. Find out which devices are running old versions of IOS or IOS XE. Find out if SNMP versions 1 or 2 are turned on and where community strings are allowed. Look for exposed HTTP APIs in scan management interfaces. If the vendor offers them, use their configuration and software checkers.
When looking for signs of a problem, check for strange processes or modules in device outputs, open ports on management interfaces that shouldn't be there, or changes to device settings that shouldn't be there. Telemetry at the network level can show strange SNMP traffic or HTTP POST requests to management endpoints that don't make sense. Many vendor advisories and threat reports have indicators of compromise and detection queries that you can use with SIEM or network monitoring tools.
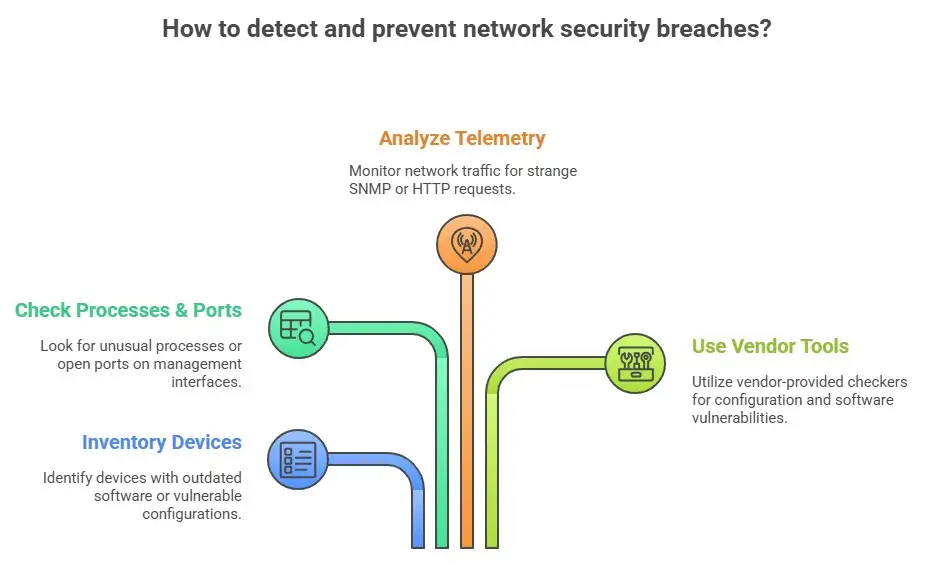
Useful advice on how to fix and avoid problems
The best way to protect yourself is to install vendor patches as soon as they are confirmed to work in your environment. Cisco put out warnings that included steps to fix the software and lessen the damage. If you can't patch right away, turn off the affected services on interfaces that connect to untrusted networks to lower your risk. Restrict SNMP to SNMPv3 with strong authentication and get rid of default community strings.
Put all management traffic on separate management VLANs and use access control lists and jump hosts to keep those networks safe.
It helps to take a layered approach. Use software updates along with network segmentation, strict credential management, multi-factor protection on admin portals, and regular backups of your configuration. If an attacker has administrative access or valid management credentials, software fixes alone may not be enough, so keep that in mind. After a breach, cleaning up often means reimaging devices or restoring from known good backups after making sure there are no permanent implants left.
How attackers are taking advantage of these flaws right now
Recent attacks show that attackers are using more than one method at a time. They start by making a list of all the devices and looking for SNMP or HTTP endpoints that are open. If they find versions that are vulnerable, they try to use code execution to install a lightweight rootkit.
Once they have root access, they change passwords, keep tools, and make tunnels that go back to their infrastructure. Researchers found that exploitation mostly happened on older hardware, like legacy Catalyst families and some Meraki-managed devices that share some software components. The pattern is automated and takes advantage of opportunities, which means that a lot of devices can be targeted quickly.
Because of this, defenders should assume that once a device is vulnerable, it will be scanned and targeted within days. Patching windows that last for weeks is easy to take advantage of. That might be hard to hear, but it's the truth about how automated threat operations work today.
Making a strong plan for the security of network devices
Make a practical plan and break it down into steps that you can do over and over.
First, make a list of all the OS versions that are on your computer.
Second, patch devices that are connected to the internet or are important for internal services first.
Third, set up secure configuration baselines that turn off old protocols and make sure that management is strongly separated. Fourth, set up regular checks for known signs and oddities.
Add one more step that people often forget to do. Do tabletop exercises to practice what to do if your network infrastructure is hacked. Reimaging and replacing switches costs a lot of money and takes a lot of time. When the alarm goes off, knowing the order to isolate, capture forensics, and recover will save you time and trouble.
Last thing to remember
Cisco IOS and IOS XE have security holes that are more than just another vendor's warning. They remind us that the infrastructure we depend on can be attacked in ways that are more than just temporary disruptions. Handle management services like any other public service.
Patch right away. Restrict access. Keep a close eye on things. And get ready for the painful truth: if a device shows signs of being compromised, you should treat recovery like a forensic process, not just a reboot
You would find different tools in that server room I talked about at the beginning, but the same logic would still apply. The engineer would say the same thing that I have heard a hundred times. Keep the software up-to-date. Take charge of the management plan. Think that attackers will come. If you do those three things, you can avoid a near miss and a full-blown outage that will have long-lasting effects.
Hoplon Infosec's Penetration Testing service helps businesses find and fix flaws like the Cisco IOS XE remote code execution flaw before hackers can use them. Our experts pretend to be attackers, test how well patches work, and make your network's defenses stronger.
Share this :