Cloud Penetration Testing Steps: Ultimate 2025 Guide
Hoplon InfoSec
26 Nov, 2025
I still remember the first time I ran a live cloud test and watched misconfigured roles spill secrets like a leaky faucet. That moment taught me that cloud security is less about walls and more about relationships.
Cloud penetration testing steps are the route every security team should know. These steps help you find weak points, fix them, and stop attackers from turning a tiny mistake into a major breach. In this article, I break down practical, human-tested steps you can follow.
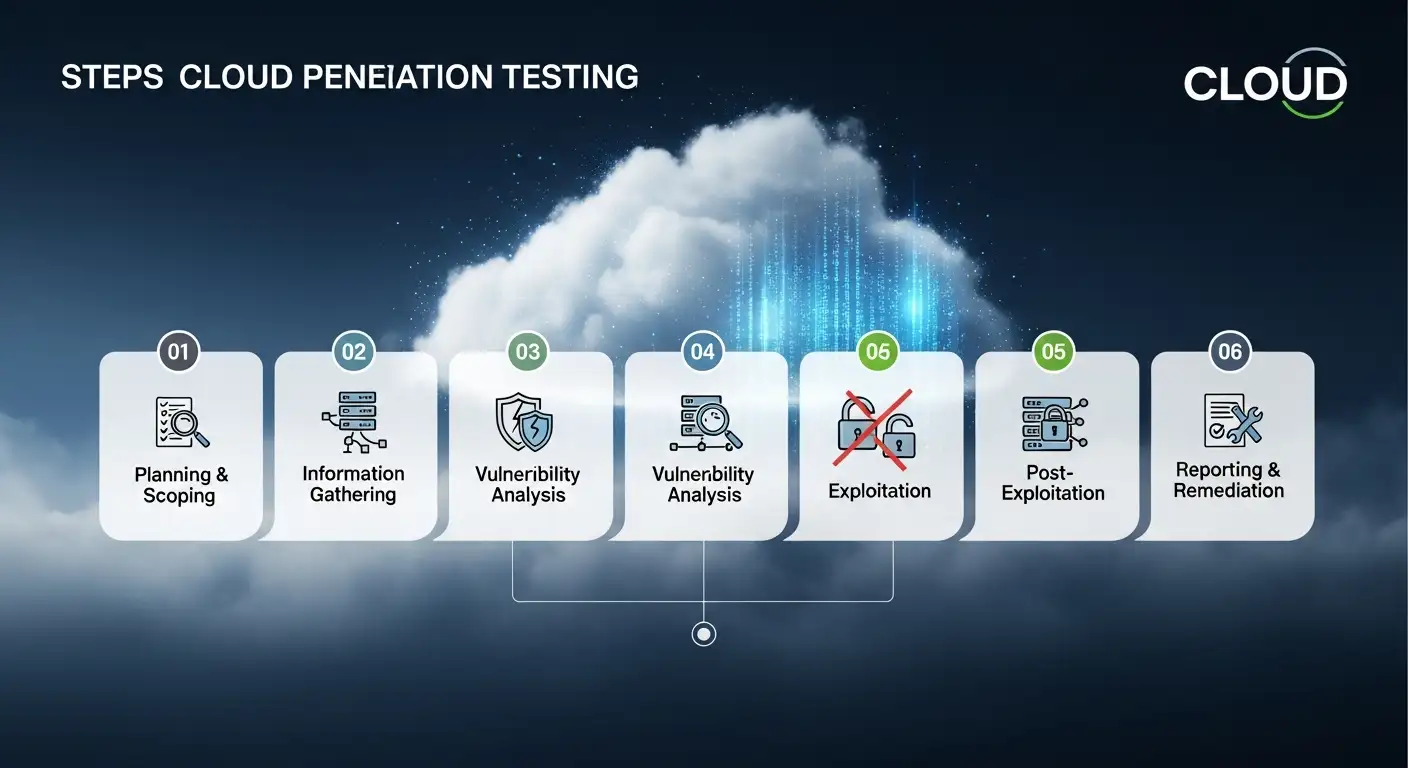
Scope and planning
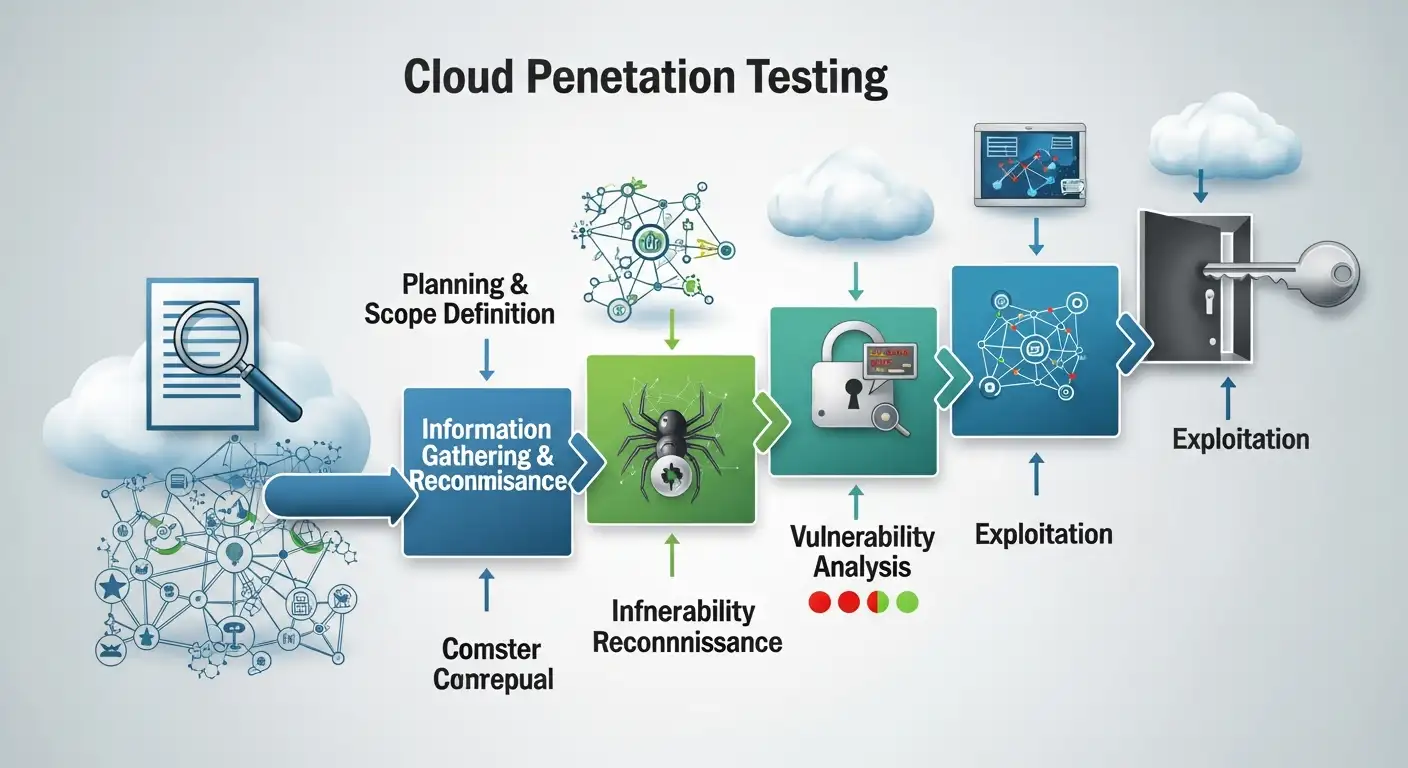
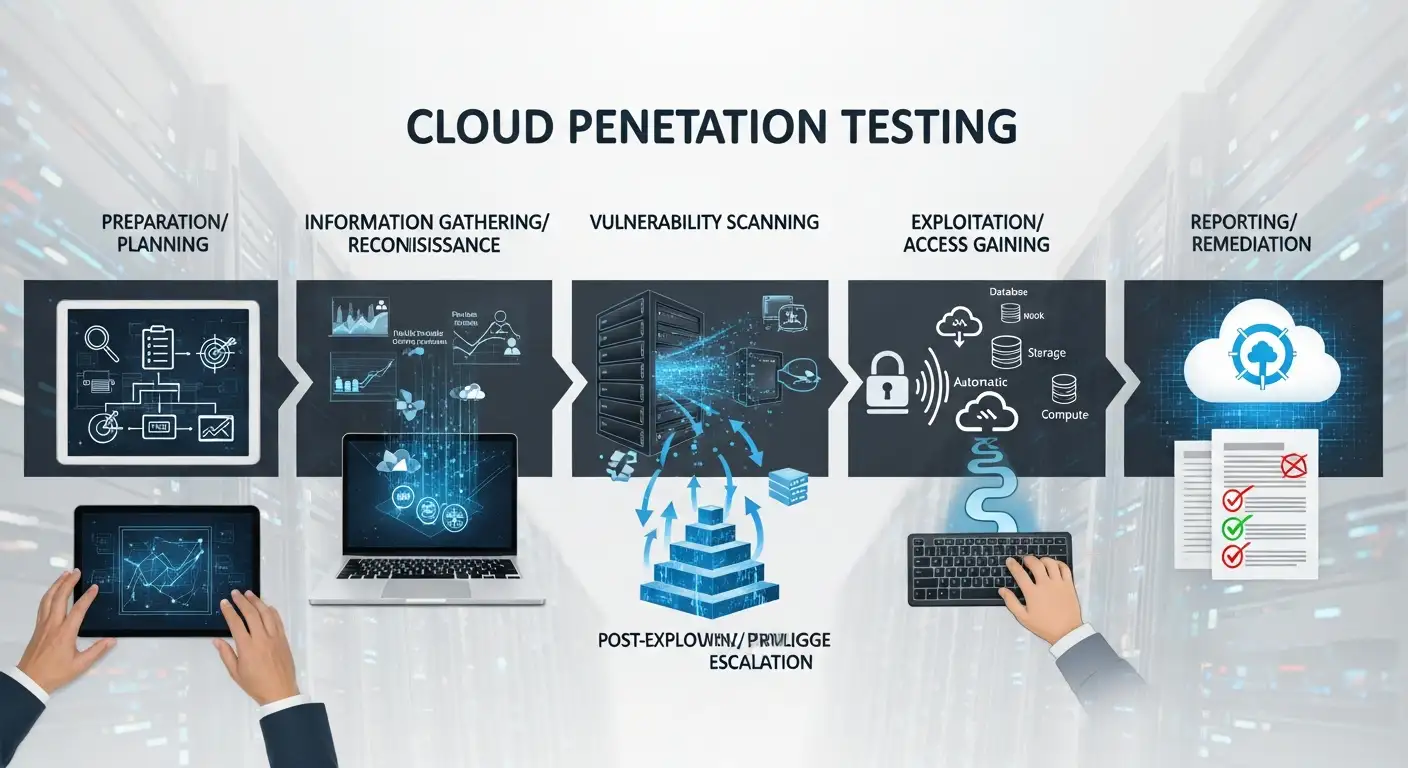
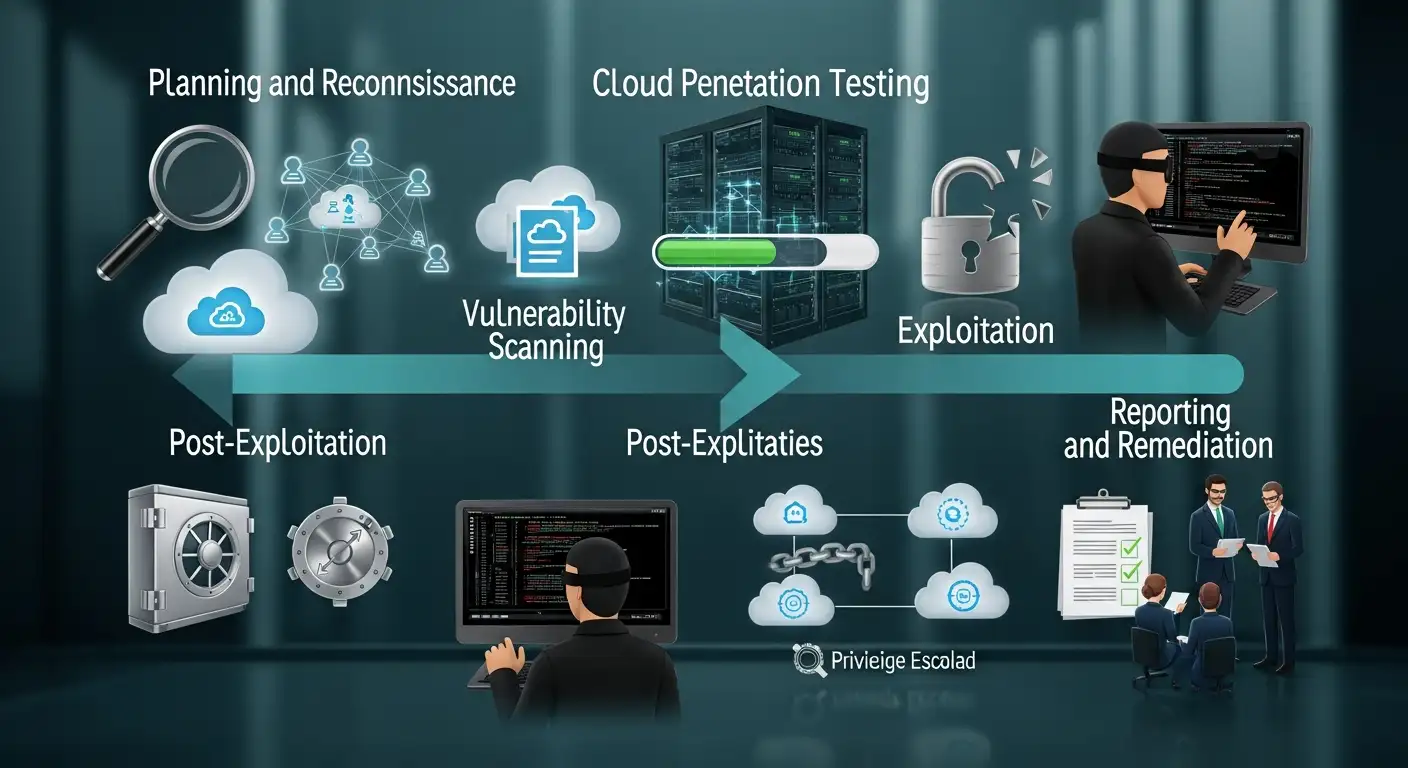
The first of the cloud penetration testing steps is scoping. A good scope avoids accidents and keeps tests legal and effective. Spend time mapping which accounts, services, and data you will test. Include any compliance needs and get written permission from the cloud provider if required. A strong plan also defines success criteria and communication channels. Remember that a scoped test is safer and produces higher-quality findings.
Reconnaissance
Reconnaissance is another key step. Use passive discovery like DNS, public buckets, and subdomain records. Watch for exposed keys in public code and record what you find without touching the target systems. Effective recon saves time later because you already know where to look. When possible, correlate findings with asset inventories and cloud tags. That context helps prioritize vulnerabilities that matter to the business.
Identity and access review
Identity problems cause most cloud breaches. In the cloud penetration testing steps, audit IAM roles, groups, and policies for over-permissive access. Try to find service accounts with old keys, roles that allow administration, and chains of trust that can be abused. Practical tests here reveal how easily an attacker can move laterally. Include role trust relationships and federation configurations in your checks.
Configuration and misconfiguration testing
Configuration checks are vital in cloud penetration testing steps. Look for publicly accessible storage, insecure firewall rules, and open object storage. Misconfigurations are common after rapid deployments. For example, a storage bucket set to public by default can leak backups and credentials. Also, examine CI/CD pipelines for exposed secrets and deployment keys.
Network and perimeter testing
Network testing is a central part of these steps. Map VPCs, inspect security groups, and test network ACLs. Attackers use exposed endpoints and weak microsegmentation to bypass protections. Simulate attacks that mirror real-world adversary behavior.
Application and API testing
APIs and cloud native apps are often the weakest link. Among cloud penetration testing steps, API fuzzing, parameter tampering, and authentication checks expose flaws. Test for injection flaws, SSRF, and broken access control in serverless functions. When possible, pair functional testing with code review to reveal logic bugs that scanners miss.
Data protection and encryption checks
Check how data is stored and transmitted. This step focuses on key management, encryption in transit, and encryption at rest. Evaluate whether encryption keys are rotated and whether key policies are overly broad. Assess backups and snapshots too. Old snapshots often contain secrets and may not be covered by encryption policies.
Logging, monitoring, and detection testing
If you cannot detect an attacker, you cannot stop one. One of the critical cloud penetration testing steps is to test logging pipelines and alerting. Simulate suspicious activity and make sure logs arrive and trigger meaningful alerts. Measure the time from activity to alert and include that metric in reports.
Privilege escalation and lateral movement
A realistic pen test will attempt to escalate privileges and move laterally. The cloud penetration testing steps must include pivot techniques like abusing metadata services, exploiting misconfigured roles, and using exposed credentials. Document every pivot path and show how an attacker might go from a public app to sensitive data. Making the path tangible helps leadership focus on priorities.
Automation and tools
Use automation carefully. Automation supports many cloud penetration testing steps by scanning for known misconfigurations and vulnerable services. Combine automated scans with manual proof of concept exploits to avoid noisy false positives. Document tool versions and settings so results are reproducible. Post-exploitation and persistence
After gaining access, test how an attacker would persist. This step looks at backdoors, scheduling jobs, and long-lived credentials. Document persistence techniques and suggest mitigations. Also, simulate cleanup and recovery to ensure the ops team can respond quickly.
Reporting and remediation
Reporting is more than a list of bugs. Include risk ratings, exploitability, and recommended fixes. A good report explains business impact and shows what to change first to get the most security return. Add a technical appendix for engineers and an executive summary for decision makers.
Retesting and continuous improvement
Fixes need verification. Retesting completes the cycle by confirming that fixes work and no new issues have appeared. Encourage organizations to adopt a continuous testing cadence as infrastructure changes fast. Continuous improvement reduces the distance between discovery and mitigation.
Real-world example
In one engagement, a misconfigured role allowed a tester to read secrets in a database snapshot. The fix was a principle of least privilege change and a policy that reduced service account permissions. The team also added automated checks to their deployment pipeline so the same mistake could not be repeated. That small automation step prevented repeated exposure and saved weeks of manual audits.
Final Thoughts
Cloud penetration testing steps form a practical roadmap. Follow scope, reconnaissance, identity checks, configuration tests, network and application probes, data and logging validation, escalation, automation, reporting, and retesting. These cloud penetration testing steps are practical and actionable. Start small if you must, but start. Over time, these exercises become part of engineering life, and the overall security posture strengthens.
FAQs
What tools should I use for cloud penetration testing steps?
Use Useprovider-specificc tools, open source scanners, and manual techniques. Balance automation and manual review.
How often should this be performed?
At a minimum, annually, and after major changes or deployments. Many teams scan templates on each deployment and run deeper tests quarterly.
Can I run tests without provider permission?
No. Always get written permission. Cloud providers often have rules and required notifications.
What are common mistakes? Skippingg scope, failing to check identity policies, and ignoring logging are the top mistakes. Also, do not rely only on automated scans.
Author: Hoplon Infosec
Bio: Security enthusiast with over 10 years in mobile cybersecurity. Connect with me on LinkedIn.
Address: 1415 W 22nd St Tower Floor, Oak Brook, IL 60523, United States
Phone: +1 773-904-313 , Contact: [email protected]
About/Privacy: At Hoplon Infosec, we provide expert insights into cybersecurity. Our editorial policy: all articles are written by in-house specialists or thoroughly reviewed by them to ensure accuracy, credibility, and up-to-date information.
Share this :