Cloud Security Guide 2025: Protecting Data, Businesses, and the Digital Future

Hoplon InfoSec
31 Aug, 2025
Cloud Security Guide
If you look back at the early 2000s, the idea of storing your photos or company data in something called “the cloud” felt like science fiction. Yet here we are, living in a time when businesses, schools, and even our personal devices rely on cloud systems every single day. It is invisible, but it runs our lives. With that convenience comes a question that often keeps people awake at night: how safe is it really? That question is at the heart of what experts call Cloud Security.
It’s not just a technical term; it’s the invisible shield that protects our messages, our banking apps, and even the movies we stream late at night. Without it, the modern internet would feel like leaving your house unlocked with all the lights on.
Why Cloud Security Became a Big Deal
The rush to adopt cloud services grew faster than anyone expected. Companies realized they could cut costs, move faster, and innovate without buying bulky hardware. But that speed came with risks. Hackers saw an opportunity. If they could breach one cloud platform, they could reach thousands of clients in a single strike. That’s why Cloud Security is not just an IT issue anymore, but a boardroom conversation.
Think about it. When a hospital puts patient records in the cloud, it’s not just about convenience. It’s about life and death decisions. A single breach could expose confidential details or even shut down critical systems. Suddenly, security became more than just protecting passwords.
Understanding the Basics of Cloud Security
So what does Cloud Security actually mean? At its core, it’s the collection of strategies, policies, and tools designed to keep data safe when stored, processed, or moved through cloud environments. Imagine a bank vault, but instead of steel doors, it uses digital walls, codes, and constant monitoring.
It includes simple measures like strong passwords but also complex processes like identity verification, encryption, and compliance checks. For regular users, it might look invisible. For IT teams, it’s a full-time battle that never ends.
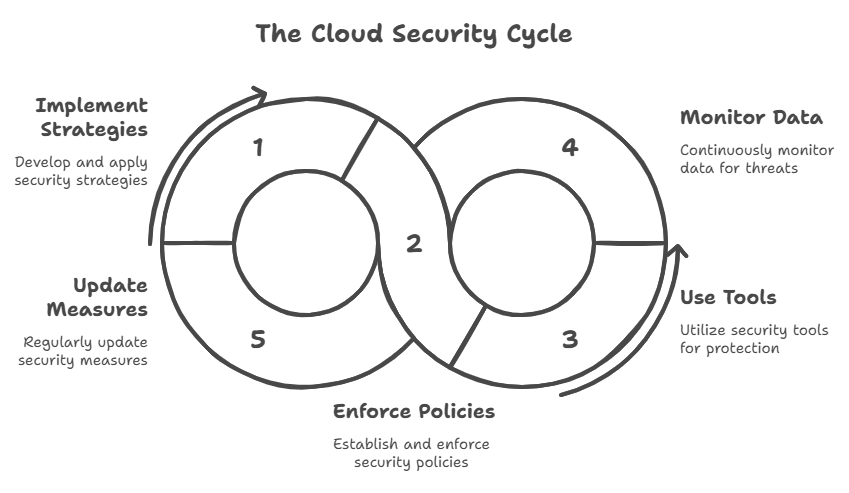
How Data Travels in the Cloud
One way to understand cloud safety is to follow your data’s journey. When you upload a photo, it doesn’t just float in space. It bounces between servers, networks, and storage centers spread across the world. During that journey, it faces risks from interception, misconfiguration, or outright theft.
That’s why Cloud Security focuses on securing every stage of this travel. It ensures that when data moves from your device to a remote server, nobody else can peek inside or alter it. Think of it like a heavily guarded delivery service, where every box is locked, tagged, and monitored until it reaches its destination.
Shared Responsibility: Who Protects What
One common misunderstanding is believing that cloud providers handle everything. In reality, cloud safety works under what’s called a “shared responsibility model.” The provider ensures that the infrastructure is secure, but customers must protect their applications, accounts, and access controls.
It’s similar to renting an apartment. The landlord gives you a safe building, locks for your door, and maybe even a security guard. But if you leave your windows wide open, that’s on you. Cloud Security works the same way: both sides need to play their part.
The Most Common Threats in the Cloud
Like any good thriller story, there are villains in the cloud world too. Some of the most common risks include data breaches, stolen login details, insider threats, ransomware, and misconfigured storage. Misconfiguration is surprisingly common; sometimes businesses accidentally leave data buckets wide open, which hackers then discover.
Another danger is denial-of-service attacks, where criminals flood systems with traffic until they crash. Each of these risks highlights why Cloud Security is not something that can be handled casually.
Real Incidents That Changed the Way We Think
One of the most eye-opening moments came when a major retail chain’s customer data was leaked due to poor cloud configurations. Overnight, millions of people faced the risk of fraud. Another example is when a popular photo app accidentally exposed user images due to weak access controls.
These incidents made headlines and pushed companies to take Cloud Security seriously. They also served as lessons for smaller organizations: if global giants can be vulnerable, anyone can.
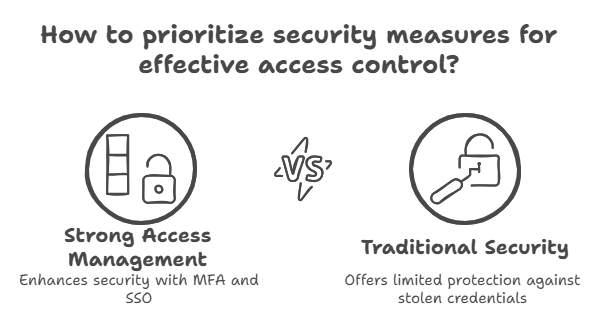
Identity and Access Control: The Front Door Matters
If you think about security like a house, the front door is where identity and access control come in. Who gets in and what they can do once inside matters more than anything else. Tools like multi-factor authentication and single sign-on act like extra locks and security guards.
Without strong access management, even the best firewalls and encryption mean little. Hackers often use stolen passwords as their golden ticket. That’s why experts say the human login is the most valuable key in Cloud Security.
Encryption: Turning Secrets into Puzzles
Imagine sending a love letter in plain text. Anyone who picks it up can read it. Now imagine writing it in code so only the intended person knows how to decipher it. That’s what encryption does in cloud environments.
Encryption ensures that even if hackers grab your data, it looks like meaningless gibberish without the right key. From credit card transactions to healthcare reports, encryption is one of the unsung heroes of Cloud Security.
Keeping an Eye with Monitoring and Alerts
One lesson companies have learned is that prevention is never enough. You need real-time monitoring and alert systems. These act like motion sensors in a house. If someone breaks in, alarms go off.
Cloud Security platforms now come with advanced monitoring tools that detect unusual behavior, like a login from a strange country or a sudden spike in file downloads. Early warnings can mean the difference between a minor incident and a full-scale breach.
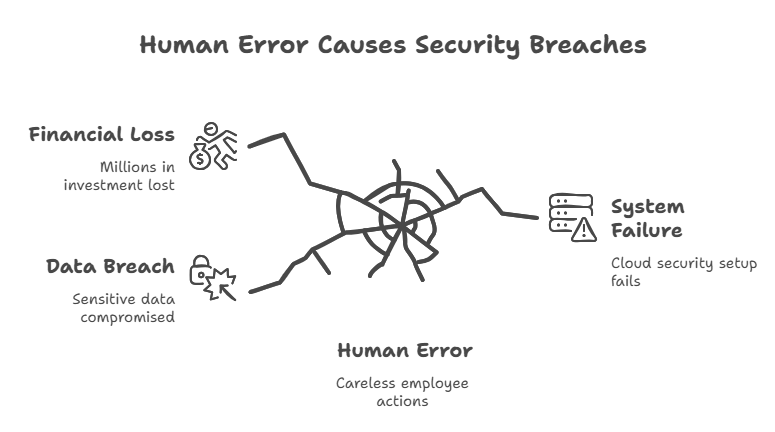
Human Mistakes: The Weakest Link
It’s easy to blame hackers, but studies show most breaches happen because of human error. Maybe someone reuses a weak password, clicks on a phishing link, or forgets to secure a storage folder. One careless action can unravel millions in investment.
This is why training is just as important as technology. Employees need to know how to spot scams, handle sensitive data, and follow best practices. Without that, even the strongest Cloud Security setup can fail.
Cloud Security in Business Growth
For businesses, cloud adoption is not just about technology; it’s about survival. Startups can compete with giants because the cloud gives them scalable tools. But growth without safety is a recipe for disaster.
Investors, partners, and customers now ask companies about their Cloud Security posture before signing deals. A single data leak can shatter trust that took years to build. In many ways, security has become the silent foundation of modern business success.
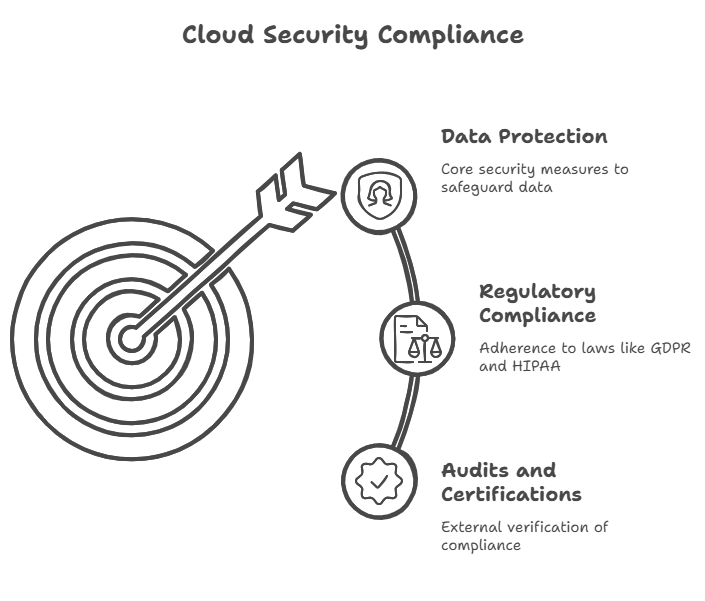
Regulations and Compliance in the Cloud Era
Another layer to consider is regulation. Governments now demand strict protection for sensitive information. From GDPR in Europe to HIPAA in healthcare, companies must follow rules or face massive fines.
Cloud Security strategies must align with these laws. That means not only protecting data but also being able to prove it. Audits, certifications, and compliance checks have become part of the daily routine for cloud-powered businesses.
The Future of Cloud Security: AI and Beyond
Looking ahead, the battlefield is changing. Criminals are using automated tools and even artificial intelligence to hunt for weaknesses. In response, Cloud Security teams are doing the same. AI-driven monitoring, predictive analysis, and self-healing systems are the future.
Imagine a cloud that can defend itself, patching weaknesses before hackers can exploit them. That’s where the industry is heading. The question is whether defenses can keep up with the speed of new threats.
Final Thoughts: Building Trust in the Digital Sky
At the end of the day, Cloud Security is not just about firewalls and software. It’s about trust. We trust the cloud to hold our memories, our work, our identities. That trust has to be earned and protected every single day.
No system is perfect, and no defense is absolute. But by learning from past mistakes, adopting smarter tools, and remembering that people matter as much as technology, we can keep building a digital sky that feels safe to live under.
Share this :