The Columbia University Data Breach Case Study: A Wake-Up Call for Campus Security

Hoplon InfoSec
03 Jul, 2025
What if your university email suddenly stopped working, then your lecture notes vanished, and bizarre images of political propaganda lit up the dorm room walls?
That was the chilling reality for thousands at Columbia University in the summer of 2025, when a mysterious “technical glitch” spiraled into a full-blown cyberattack, revealing not only the fragility of institutional cybersecurity but also the terrifying power of digital sabotage in the hands of politically driven hackers.
Columbia University Data Breach Case Study In details
What began as a seemingly routine IT disruption on June 24, 2025, quickly escalated into one of the most significant cyberattacks on a U.S. university in recent memory. Columbia’s initial internal communications described the event as a “technical outage,” with affected systems including campus email servers, payroll portals, and remote learning tools. Many students assumed it was a typical maintenance issue.
However, when screens across residence halls began flashing bizarre imagery, including digital posters of Donald Trump, the situation took a strange turn. The theatrical visual hijacking suggested the presence of something more sinister. Internal systems remained down for over 36 hours, and concerns began spreading through faculty and student forums.
By July 1, Columbia publicly admitted what had already become apparent: this waglitch/glitchliberate cyberattack. Columbia immediately retained the cybersecurity firm CrowdStrike to initiate forensic analysis. The breach wasn’t random, and it wasn’t financially motivated; it was political, precise, and deeply invasive.
Who Was Behind the Attack? A Hacktivist with a Cause

The individual responsible for the attack identified themselves as a hacktivist, motivated by political ideology rather than profit. Using the pseudonym “Computer Niggy Ope,Ope,acker claimed their goal was to expose Columbia’s alleged noncompliance with the 2023 Supreme Court ruling that banned the use of affirmative action in college admissions.
Unlike typical hackers who exploit weak endpoints or use phishing, this attacker methodically infiltrated the university’s Active Directory, Student Information System, and VMware ESXi servers over a two-month period. They claim to have accessed network shares, admissions databases, and financial record systems, eventually stealing over 460 GB of data.
The hacker even released a 1.6 GB sample of the data, including anonymized admissions files, applicant demographics, and decision records. Cyber journalists and analysts who reviewed the sample confirmed its legitimacy by matching real students’ identities with their admission outcomes, including racial classifications and academic profiles.
The Extent of What’s at Risk
This incident was not merely a breach of Columbia’s digital ecosystem. The stolen data touched nearly every facet of university operations and community life. Analysts estimate that the breach affected over 2.5 million individuals, including current students, applicants, alumni, faculty members, and in some cases, even their family members.
Among the most sensitive categories of exposed data:
Admissions Records: Including years of application essays, SAT/ACT scores, high school GPAs, race and ethnicity data, and decision rationales by admissions officers.
Personal Identifiable Information (PII): Names, Social Security numbers, birthdates, visa/passport scans, immigration details, home addresses, and contact numbers.
Financial Records: Scholarship and loan applications, financial aid award letters, bank account routing numbers, payroll information, and tax documents.
Internal Communications: Email logs between faculty and staff, internal memos, and student conduct reports.
The long-term harm includes not only identity theft and fraud but also the exposure of confidential academic and legal matters, including disciplinary actions, medical leaves, and mental health accommodations.
Political Context: Tensions Surrounding Affirmative Action and Federal Funding
The breach took place amidst intense political scrutiny. In June 2023, the U.S. Supreme Court ruled that race-based considerations in college admissions violated the Equal Protection Clause, effectively outlawing affirmative action.
Columbia, like many Ivy League institutions, was rumored to be quietly preserving diversity benchmarks through less transparent means. The attacker alleged that they found internal documents showing continued racial tracking and flagged decision patterns that disproportionately favored underrepresented minorities, which they claimed violated the ruling.
At the same time, Columbia was already under federal pressure for unrelated reasons. The Department of Education had frozen $400 million in federal research funding due to alleged mishandling of antisemitism complaints on campus. This forced Columbia to adopt new protest guidelines and academic oversight measures.
In this context, the hack evolved from being merely a security incident to becoming a significant political flashpoint. It was designed to uncover what the attacker viewed as systemic hypocrisy and constitutional violations under the guise of elite education.
Institutional Response: Investigation & Damage Control
Columbia’s immediate response was both technical and reputational. They shut down all major systems, including those not directly affected, to isolate potential breach vectors. CrowdStrike began conducting packet captures, log analysis, and malware detection procedures.
Within 72 hours, Columbia began issuing email updates acknowledging that sensitive data had been accessed, though they refrained from confirming specifics. Their language was cautious, likely shaped by legal counsel, with phrases like “potential data exposure” and “limited unauthorized access.”
They promised full cooperation with federal and state authorities and pledged to notify all impacted parties individually. Privacy experts, however, criticized the university for taking nearly a week to publicly disclose the true nature of the breach, arguing that the delay could have worsened victims’ exposure to fraud or scams.
As of July 3, Columbia is still evaluating the full scope of the damage. Their website now hosts a special incident response portal and a public FAQ, but many questions remain unanswered, particularly about how long the hacker had access and why detection took so long.
Broader Cybersecurity Implications

The Columbia incident represents a seismic shift in the landscape of cybersecurity threats facing universities. Until now, most breaches in education involved ransomware or accidental data exposure. This attack, by contrast, was deliberate, ideological, and structurally invasive.
Higher education institutions are especially vulnerable due to:
Large, complex IT infrastructures
Decentralized data governance
Legacy systems
Open-access environments (labs, research, student development)
Moreover, universities store a blend of personal, financial, and academic data, making them high-value targets. Yet many institutions still lack dedicated security budgets, skilled staff, or incident response plans.
This breach signals that activists with political motives may now target universities just as frequently as criminal groups do. The need for zero trust architecture, real-time monitoring, and AI-driven anomaly detection has never been clearer.
Individual Risks & Protective Measures

For individuals affected by the breach, the fallout could last for years. Many students and alumni now face the risk of:
Identity Theft: With SSNs and birthdates leaked, fraudsters can apply for loans, credit cards, or unemployment benefits.
Employment Impacts: If job applicants have private disciplinary records leaked, it could impact future hiring.
Immigration Consequences: International students could face legal risks if their visa or passport data is used maliciously.
Reputational Harm: Some leaked documents include health, counseling, or behavioral records.
Legal experts are already preparing class action lawsuits, and Columbia expects to offer 12–24 months of free identity monitoring. In the meantime, those affected should act quickly: place credit freezes, monitor bank activity, and update passwords across all platforms that may share login credentials with Columbia.
What Happens Next: Long-Term Outlook
The next several months will determine Columbia’s accountability and the extent of its liability. Several scenarios are likely:
11. Regulatory Review The Department of Education and New York Attorney General will likely conduct investigations into FERPA and SHIELD Act compliance.
2. Financial Fallout: If deemed negligent, Columbia could face multi-million-dollar fines and lose portions of its federal funding.
3. Legal Action: Multiple law firms are preparing to launch lawsuits on behalf of students and staff. If successful, Columbia could face settlements or court-ordered compensation.
4. Reputational Damage: College ranking organizations and prospective applicants may reconsider Columbia as a top-tier choice.
5. Policy Reform: This breach may trigger broader efforts to enforce minimum cybersecurity standards in higher education potentially tied to federal grants or accreditation.
Lessons Learned: Broader Takeaways
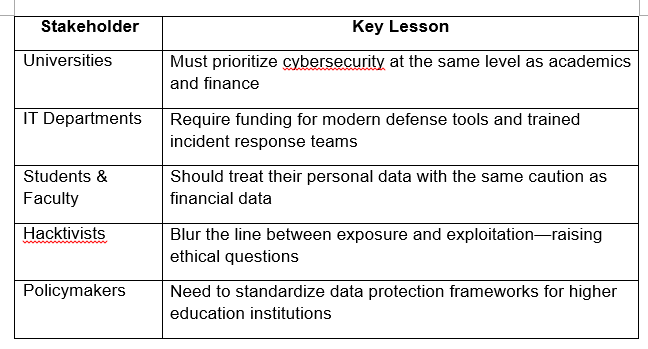
Here’s a condensed breakdown of how different stakeholders can interpret this event:
Conclusion: Cracks in the Ivory Tower
The Columbia University breach serves as a glaring reminder that no institution is immune from cyber threats, especially when ideology intersects with technology. The attacker’s motivations, whether lawful or not, have started a global conversation about transparency, race in education, and data ethics.
While the full fallout will take months, possibly years, to play out, one thing is clear: the ivory tower must adapt. Academic excellence must be paired with cyber resilience, or else the trust that institutions hold trust with student futures, research integrity, and national data will erode rapidly.
2026 Update: Settlement and Long-Term Resolution
As of February 2026, the following updates have been confirmed regarding the fallout of the Columbia University data breach:
Massive Financial Settlement: Columbia University has reached a $250 million class-action settlement to compensate the 2.8 million individuals affected by the breach, covering identity theft protection and damages.
Federal Oversight & Funding: Following a complete overhaul of its cybersecurity protocols, the $400 million in frozen federal research funding was restored under a strict three-year compliance monitoring agreement.
Admissions Transparency: To address the hacker's claims regarding affirmative action, the university implemented a Digital Audit Trail for the 2026-2027 admissions cycle, allowing federal regulators to ensure transparency and legal compliance.
Implementation of Zero Trust: The campus network has fully migrated to a Zero Trust Architecture. This includes AI-driven behavioral monitoring that automatically severs connections if unauthorized large-scale data exfiltration is detected.
Resources:
AP News
New York Times
Share this :