UK Cybersecurity Threats 2025: How Businesses Can Build Cyber Resilience

Hoplon InfoSec
26 Oct, 2025
When you get to work, the whole company network is down. Emails stop coming in, files disappear, and you can't get to your daily systems. That situation is no longer just a distant "what if" for a lot of businesses in the UK today; it's a very real possibility. The head of Government Communications Headquarters (GCHQ) has even said in public that cybersecurity threats will get through even the strongest defenses unless businesses do more.
We'll talk about the growing threat of cybercrime in the UK, what the GCHQ cyber warning means for businesses, how well the UK can handle cyberattacks, and what companies can do to improve their defenses. Whether you're on the board, in charge of IT, or just worried about business cybersecurity threats, it's important to know how things are changing.
The Growing Number of Cybersecurity Threats in the UK in 2025
It's not just a guess about the cyberattack threat in 2025; it's happening right now. The UK's National Cyber Security Centre (NCSC) says that the number of "nationally significant" incidents rose from 89 the year before to 204 in the year ending in August 2025.
Even more shocking, the number of "highly significant" cyber incidents went up by about 50%. That means attacks that hurt the economy, stop important services, or hurt a lot of people are becoming more common.
Why is the threat growing so quickly? A few things:
• Attackers, whether they are criminals or linked to the government, are getting smarter and using tools like AI, automation, and spying.
• It's getting easier to get into cybercrime because some tools that were only available to government agencies are now more widely available.
• A lot of businesses and supply chains are digital. That makes more weak spots, and when one link breaks, the effects can spread quickly. For instance, a recent attack forced Jaguar Land Rover to stop making cars in all of its UK factories, which cost the company billions of dollars.
The message is clear when we talk about "business cybersecurity threats" and "UK cybersecurity threats 2025": we need to take action right away.
GCHQ said, "Attacks will get through."
Anne Keast Butler, the head of GCHQ, gave a scary but true warning at a cybersecurity conference in London: "What are your backup plans?" Because attacks will get through.
Important points from her statement:
• No matter how good the defenses are, they can't guarantee that there won't be any breaches. The enemy is always there, changes, and sometimes isn't seen until it's too late.
• It's not just about stopping it. It's about being strong: what you do after you get hit is just as important. She asked, "Do you have a plan written down in case all of your systems really go down?"
• She said that cybersecurity needs to be a part of the boardroom. Organizations need directors who ask the right questions and make sure management is responsible for cyber risk. She said that boards don't always have enough people with the right skills.
• Working together is important: businesses need to share information about attacks with government agencies in "safe spaces" to make everyone safer. Fear of damage to one's reputation or exposure shouldn't stop that.
This is the kind of honest message that can sometimes wake up whole industries: your cyber defenses are important, but so is your readiness for when those defenses are broken.
What This Means for Cybersecurity Threats to Businesses
Cyber risk must be the responsibility of the board and executive leadership.
Keast-Butler made it clear that cyber risk can't be something that only happens in the back office. It has to be at the top. If the board doesn't have someone who can question the current state of cyber resilience, then problems will continue to exist.
This means that business leaders need to:
• Make sure that cyber risk is seen as a strategic risk, not just an IT risk.
• Look over your incident response plans on a regular basis, not just your firewalls and antivirus.
• Get into the habit of thinking "when, not if" for serious breaches.
Only resilience, not prevention.
In the past, a lot of businesses thought that "if we fortify enough, we'll keep attackers out" when it came to cybersecurity. In today's world, attackers will find ways to get in. Now the focus has to be on "Can we stay alive when they get in?"
That means:
• Offline, analog backup plans (yes, paper copies!). NCSC says that businesses should have printed playbooks in case their digital systems stop working.
• A clear plan for how to talk to people during a disruption. How will people know what to do if email and internal chat stop working?
• Knowing what your most important dependencies are and where your supply chain is weak. Can you keep going if a subcontractor goes down?
• Regular drills and planning for scenarios like outages, data theft, and system shutdowns.
SMEs are at a higher risk.
Big companies usually have the money, insurance, and trained staff to deal with problems. But a lot of small and medium-sized businesses are in the line of fire and don't have as many resources. Chatham House, a policy think tank, said that the gap between policy and practice is still very wide.
This means that small businesses need to focus on basic protections like patching, backing up, multi-factor authentication, and simple recovery plans. Not all attacks are smart, but they can still have terrible effects.
Risks to the supply chain
One of the trends that worries me is that attacks on one point can spread. For instance, the JLR hack caused problems for its factories and suppliers. The NCSC warns of a "cascading cyber-crisis scenario" in which multiple sectors (transportation, energy, and finance) are hit at the same time.
So businesses shouldn't just look at themselves who do you get supplies from? Who needs you? What are their weak points when it comes to cybersecurity? It's important to include supply chain resilience in your cyber strategy.
Examples from the real world: When Cyber Threats Hit Home, Jaguar Land Rover (JLR) is an Example.
JLR showed how expensive it is to be unprepared when an attack shut down its UK production for weeks. Factories stopped working, supply chains froze, and the effects spread.
This shows that even big, well-known brands with a lot of money can be brought to their knees by a cyberattack.
Example 2: Problems in retail
Major UK stores like Marks & Spencer and the Co-op Group have publicly confirmed that cyberattacks have cost them millions of dollars and hurt their business.
These events show how "business cybersecurity threats" and the effects on everyday consumers and the supply chain can come together.
Example 3: SMEs and failures in analog backup
Hackers encrypted the systems of a transport company in Northamptonshire, which then went out of business. Even though they spent a lot on cyber security, they didn't have a tested manual fallback, which was very important: "It's not a matter of 'if' these things will happen, but 'when.'"
It's a warning that just putting money into something isn't enough; you also need to be ready and have a backup plan.
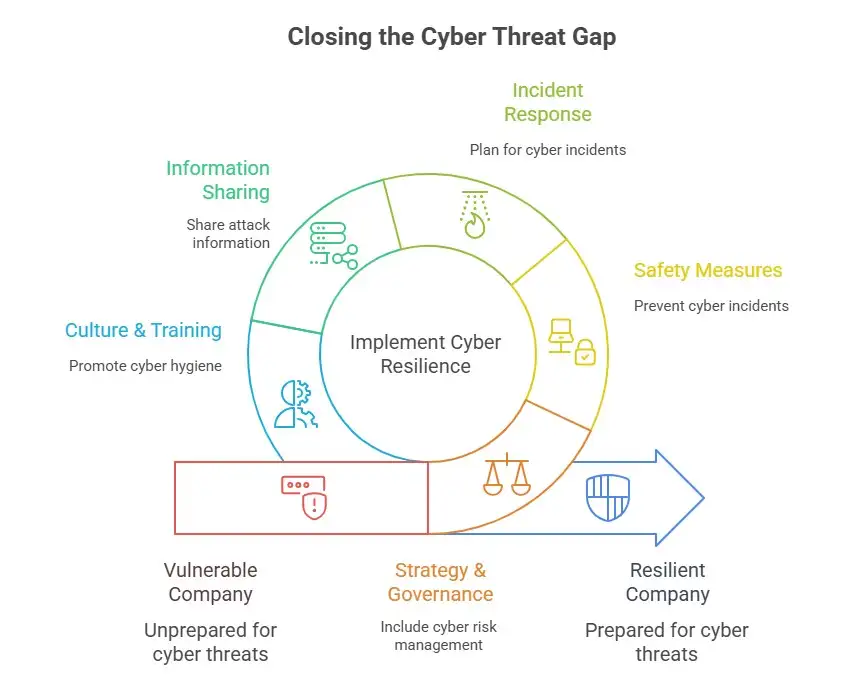
Making the Internet more resilient in 2025 and beyond
If your company really wants to close the gap between threats and being ready, here are some important areas to focus on.
1. Strategy and governance
• Include cyber risk in your company's risk management system.
• Make sure that cyber issues are governed at the board level with regular reviews and challenges.
• Follow well-known guidelines like the UK's Cyber Governance Code of Practice.
2. Safety measures that stop things from happening
• Scanning for vulnerabilities and managing patches.
• All access requires more than one form of authentication.
• Network segmentation to stop lateral movement if a breach happens.
• Supply-chain assessments: Know your vendors, what you depend on, and how well they keep their computers safe.
3. Answering and getting better
• Make a plan for how to respond to an incident that includes a manual fallback (with paper playbooks).
• Do drills on a regular basis to test communications, decision-making, and response in a worst-case scenario.
• Make sure backups are safe and not connected to the internet. Check the steps for restoring data on a regular basis.
• Keep other ways to communicate open: how will employees, suppliers, and customers be told if systems go down?
4. Working together and sharing information
• Share attack information in government "safe spaces" or trusted communities, but don't give away any business data.
• Sign up for NCSC's early warning services.
• Peer groups based on the same industry can help businesses share what they've learned and make their sector more resilient.
5. Culture and training
• Everyone is responsible for cyber hygiene; it's not optional. Employees need to learn about phishing, social engineering, and supply-chain risks.
• Leaders should show how to think about resilience and make sure that cyber drills aren't just a way to check off a box.
• Create a space where people can report incidents without fear of getting in trouble, so they can learn instead of hiding.
Why the Warning Is Important to You
This isn't just a headline in the UK. If you own a business, you need to know that being dependent on digital technology can be bad for you too. The same technologies that help businesses grow and come up with new ideas also make them more vulnerable. The GCHQ cyber warning makes it very clear that a breach is very likely to happen.
If you care about keeping your business running, your reputation, and your finances stable, you can't ignore it.
Also, the regulatory environment in the UK is getting better. FTSE350 companies, and soon many more, will be under pressure to show that they can handle cyber threats and have board-level oversight. If you wait until a crisis hits, it will cost a lot more to recover than if you invest ahead of time.
Final thoughts
In a world where cybersecurity threats are no longer distant warnings but real threats, the head of GCHQ's message couldn't be clearer: attackers will get through, so you need to be ready. "We'll just patch and pray" is no longer an option. Cyber resilience is what matters now: being ready for when systems fail, having plans for when defenses are broken, and having leaders who are willing to see cyber risk as a strategic issue.
Now is the time to act if your business hasn't already made cyber risk its top priority. It's not a question of if the breach will happen, but when.
This is your wake-up call. Get your business ready for cyber threats so that they don't just affect your IT but also your future.
Questions and Answers
Q1: What are the biggest cybersecurity threats to UK businesses in 2025?
A1: Ransomware attacks, supply-chain intrusions, espionage linked to the government, AI-enhanced phishing, and cascade failures across critical infrastructure are some of the biggest threats. Recent data from the UK shows that "highly significant" incidents have gone up by 50%, and there have been more than 200 attacks that are important to the whole country in the past year.
Q2: What did the head of GCHQ's statement mean for businesses?
A2: Anne Keast-Butler's statement was a blunt reminder that defenses alone are not enough. Companies need to plan for a breach and make sure that their leaders take cyber risk seriously. They also need to have backup plans, including ones that don't involve technology, and practice them.
Q3: What steps can a business take to build cyber resilience instead of just stopping attacks?
A3: Cyber resilience is the combination of being ready, preventing, and recovering. That means putting money into strong controls as well as plans for responding to incidents, backup plans, alternate ways to communicate, mapping the supply chain, and regular drills. A resilient mindset accepts that attackers will always find a way in.
Q4: Is this threat only for big businesses?
A4: No. Big companies often make the news, but small and medium-sized businesses (SMEs) may be even more vulnerable because they usually have fewer resources and less reliable backup systems. A big problem with one supplier or small business can have effects on bigger networks.
Penetration testing , Mobile security simulates real-world attacks to uncover vulnerabilities before hackers do, strengthen defenses, and improve incident response. It ensures businesses are better prepared for the cybersecurity threats GCHQ warns about.
Share this :