DarkCloud Stealer’s Hidden RAR Threat Draining Financial Companies

Hoplon InfoSec
15 Sep, 2025
DarkCloud Stealer financial companies RAR attachments
Over the past few years, financial companies have been hit by waves of cyberattacks. However, the arrival of DarkCloud Stealer financial companies’ RAR attachments has changed the story in a very bad way. This new malware feels almost personal, unlike older ones that used old tricks. It gets into inboxes by hiding inside compressed files and waits for an employee to make one simple mistake: click.
I remember a story about a junior accountant at a mid-sized investment firm who got what looked like a report from a client. The file was zipped into a RAR attachment, and the attacker got into the company’s network within seconds of opening it. That’s how DarkCloud has been getting away with it quietly but well.
Why Financial Companies Were the Best Targets
Banks, insurance companies, and investment firms all keep a lot of private information. Because money moves in and out all the time, they are one of the best places for cybercriminals to attack. It’s not just about taking money. It’s about information about people, private messages, and chances to make money in the future.
The people behind DarkCloud Stealer financial companies’ RAR attachments know that one weak spot in a financial system can open up doors to millions. Just think about how one hacked email server could let hackers watch transactions, steal invoices, or even trick executives into approving fake transfers.
The Trick That RAR Attachments Hide
A RAR file looks like any other file at first. Every day, employees download compressed folders that contain spreadsheets, contracts, or shared financial data. But hackers use this trust to hide malware that can be used as a weapon. The DarkCloud Stealer doesn’t show itself right away. It stays still until it is set off.
The fact that it seems so natural makes it even more dangerous. A senior manager once told me that her staff didn’t question the RAR file because it came from a fake address that looked exactly like their auditing partner’s. It’s smart social engineering mixed with technical accuracy.
How a DarkCloud Attack Works
When an employee who doesn’t know what they’re doing extracts the RAR file, harmful scripts run without anyone knowing. DarkCloud then starts to collect data like passwords, browser history, and even keys to cryptocurrency wallets. It acts like a thief in the night, taking things of value without leaving any signs.
The workflow usually goes through three stages: infiltration, reconnaissance, and exfiltration. First, the attacker gets in. The next step is for the malware to look for important data. Lastly, the attackers send the stolen data back to servers they control far away. And by the time IT finds out, it’s usually too late.
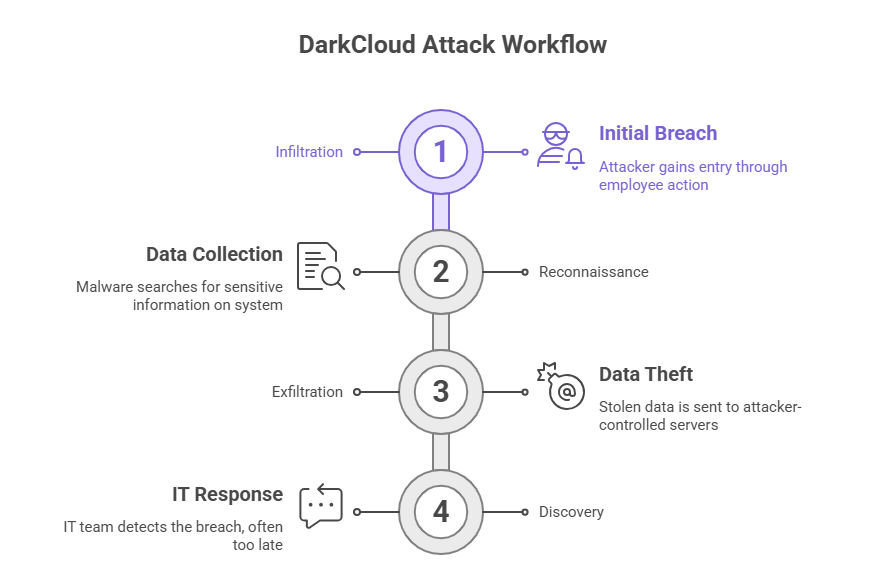
What we can learn from real-life cases
DarkCloud attacks have already happened to a number of financial companies. One bank in Europe said that unauthorized transactions happened all of a sudden after employees unknowingly started the malware. In another case, a small insurance company found out that its client files were being sold on secret forums just weeks after someone opened a suspicious RAR file.
These things really happened. They show how DarkCloud Stealer financial companies’ RAR attachments take advantage of mistakes people make and weaknesses in organizations. And the scary part? A lot of victims didn’t know they were in trouble until clients or regulators told them.
What Makes DarkCloud Different from Other Malware
Many types of malware have gone after banks, including Zeus, Dridex, and TrickBot. Dark Cloud, on the other hand, feels different. It is strong because it is simple. It doesn’t use complicated delivery systems; it just uses something as simple as an email attachment.
DarkCloud, on the other hand, doesn’t set off alarms right away like some older malware. Experts say that this virus is more than just another one because it is very specialized and only targets financial companies. It hunts for patients.
Mistakes made by employees: the weakest point
Even though cybersecurity systems are getting better all the time, employees are still the biggest risk. People are busy, distracted, or just too trusting. A file with the name “Q3 Report” might not seem suspicious. Many cybercriminals actually plan their scams around financial calendars, sending out fake reports around tax deadlines or audit season.
One IT manager told me that training employees to stay away from suspicious files is like teaching someone to see a wolf in sheep’s clothing. It sounds easy, but it’s hard to do. And that’s why DarkCloud Stealer financial companies keep getting RAR attachments that work.
What Social Engineering Does
Technology is only part of the story. The attacks are most powerful when they mess with how people think. Hacking has always used social engineering, but DarkCloud makes it sharper. People who want to attack send emails that look like they need to be answered right away, with subject lines like “Payment Overdue” or “Client Request.”
The pressure makes the person who gets the email miss small details by the time they read it. It’s not just a hack; it’s a code-based scam.
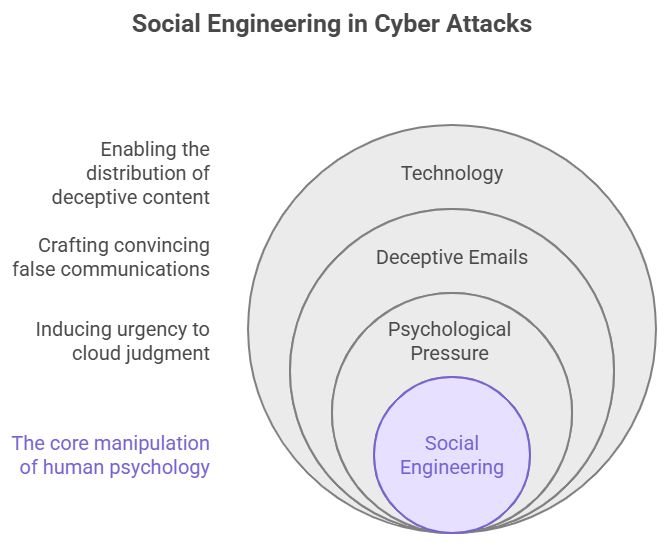
The Secret Market for Stolen Data
Information that has been stolen almost never stays in one place. DarkCloud collects data that often ends up in underground markets where stolen financial records are traded like money. There is a buyer for everything, from credit card numbers to private loan applications.
Think about what would happen if the details of a company’s upcoming merger got out because of a broken RAR file. Competitors might use that to change the stock markets or get an edge over you. That’s how far the damage can go.
How it affects the victims’ mental health
There is a human cost in addition to the money lost. People who clicked on the bad file often feel bad about it. Managers doubt their own judgment. People don’t trust you anymore. For some smaller businesses, losing money is easier to recover from than losing their reputation.
I once talked to an employee who said he couldn’t sleep for weeks after realizing that his mistake had led to stolen payroll data. That emotional weight shows that cyberattacks aren’t just technical issues; they have a big impact on people.
How Security Teams Are Fighting Back
Financial companies are not just sitting around. Many people are making their defenses stronger by using advanced email filters, tools to find threats, and systems that watch things in real time. Some people are even running tests by sending fake RAR attachments to employees to see if they know what to do.
But the problem is still there. Hackers are always changing, coming up with new ways to get around security. It’s like a game of chess where both sides keep figuring out new moves.
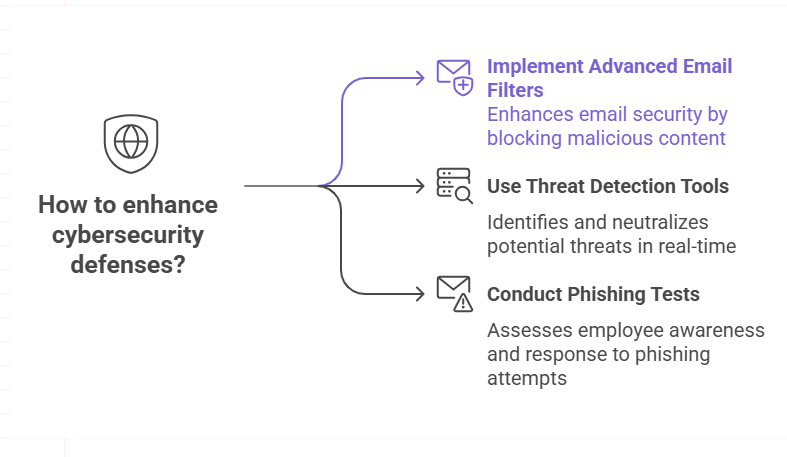
Creating a culture of cyber awareness
Tools are important, but so is culture. A business that tells its employees to question files that seem strange is more likely to stay safe. Regular training, easy ways to report problems, and open conversations about cyber threats make it harder for attackers to get in.
The point isn’t to scare workers; it’s to get them involved in the defense system. After all, the first line of defense against DarkCloud Stealer financial companies’ RAR attachments is often just one careful click away.
Governments and regulators get involved in the fight.
Regulators all over the world are making cybersecurity rules for banks and other financial institutions stricter. Banks now have to report breaches within hours, not days, in some areas. Some people are being forced to use stricter rules for handling data and sending emails.
These steps make it harder for attackers to take advantage of weak defenses, even though compliance can be hard. It reminds us that keeping our computers safe is not just the job of one company, but of everyone.
What will happen to DarkCloud and threats like it in the future?
Is DarkCloud going to go away soon? Not likely. Cybercriminals change quickly, and as long as financial companies have valuable data, they will keep being targets. We might see malware that is even smarter, maybe even using AI to stay hidden.
But more and more people are becoming aware. There is hope that defenses will get better as more people realize how dangerous DarkCloud Stealer financial companies’ RAR attachments are. The key is to be proactive instead of reactive.
A Last Thought: Believe but Check
The rise of DarkCloud teaches us that trust can be dangerous. A simple attachment can undo years of work to keep things safe. A mix of doubt and checking is the best way to go. Check the sender again, verify requests through other channels, and don’t assume an attachment is safe just because it looks familiar.
In the end, it’s not so much about technology as it is about how you think when you fight threats like DarkCloud. Financial companies will last as long as people are careful, ask questions, and remember that one small mistake can lead to big problems.
DarkCloud Stealer shows how fast one attachment can compromise an entire network. Hoplon Infosec’s Endpoint Security helps financial companies block such threats at the device level, keeping sensitive data safe.
Follow us on X (Twitter) and LinkedIn for more cybersecurity news and updates. Stay connected on YouTube, Facebook, and Instagram as well. At Hoplon Infosec, we’re committed to securing your digital world.
Share this :