DarkComet RAT Malware: Hidden Bitcoin Tool Scam 2025
-20251114115648.webp&w=3840&q=75)
Hoplon InfoSec
14 Nov, 2025
You download a shiny new Bitcoin tool that promises faster transfers and a sleek wallet. You open it, follow a few prompts, and your screen looks normal. A week later your accounts act odd, your webcam light blinks for no reason, and files disappear. That harmless download was not a wallet at all. It was a disguise for DarkComet RAT malware, a long-standing remote access threat that keeps resurfacing in clever new scams.,
What is hiding behind the lure
Malware authors often package familiar tools in familiar packaging. In this case a bogus Bitcoin utility acts as bait while the real payload is a backdoor. The piece of code known as DarkComet RAT malware gives attackers remote control over an infected computer, including the ability to capture keystrokes, take screenshots, and access webcams. Because the original developer published the tool long ago, variants and modified builds still circulate and get reused in new scams.
This makes the threat doubly dangerous. New users see the crypto brand and let their guard down. Meanwhile the DarkComet engine operates quietly, collecting credentials and opening the door for follow-on malware. The fake Bitcoin tool is the social engineering hook. The DarkComet RAT malware inside is the real problem.
A short history so it makes sense
DarkComet began as a remote administration utility and later became popular among attackers because it is easy to configure and powerful in function. Over the years researchers tracked its use in targeted campaigns and widespread abuse. Even when the original author stopped official development, the code and compiled versions lived on in attacker toolkits.
That longevity explains why analysts still see DarkComet RAT malware in modern phishing and trojan drops.
The tool’s feature set is what keeps it relevant. It supports keylogging, file transfer, command execution, and webcam control. Those features, useful for legitimate remote support, are the same features attackers exploit to steal credentials and spy. When a fake Bitcoin installer bundles that functionality, basic users do not notice anything suspicious until it is too late.
-20251114115647.webp)
How the fake Bitcoin trick works right now
Researchers recently documented a campaign where threat actors disguised DarkComet as a Bitcoin management tool. The fake app mimicked UI elements and jargon that crypto users expect. Once executed, the binary unpacks and installs the RAT component, then establishes contact with a command and control server to await instructions. The result is a full remote foothold on the victim machine.
Attackers favor this path for a reason. Crypto tools draw an audience that tends to download executables, install custom utilities, and run unfamiliar apps. That audience provides an eager supply of potential victims, and a simple repackaging turns that interest into a high value target list for the attacker.
What the malware does on your machine
Once active the DarkComet RAT malware can run a raft of intrusive behaviors. It can log passwords typed into browsers, take periodic screenshots, upload or download files, and even record microphone input. Some builds also try to disable antivirus or whitelist themselves in system settings so they persist after reboots. These actions allow attackers to quietly harvest credentials, seed additional malware, or extort victims.
Threat intelligence feeds and malware databases list numerous indicators that match these behaviors.
The malware often shows up with telltale indicators of compromise, such as unusual outbound connections to dynamic DNS addresses, unexpected services running under user accounts, and new autorun registry keys. Network defenders should look for uncommon traffic patterns and new listening ports that align with known DarkComet signatures.
Detecting and removing an infection
If you suspect an infection from a fake bitcoin tool or other installer, run a full antivirus and anti-malware scan immediately. Manual checks include looking for unknown processes, reviewing startup entries, and scanning for recent changes in firewall or scheduled tasks.
If the system is infected, disconnect it from the network to block attacker access, then follow removal guides or seek professional incident response help. Several reputable security sites publish step by step removal advice for DarkComet RAT malware and a list of hashes and network indicators to block.
Keep in mind removal can be tricky. Sophisticated variants alter system settings and drop secondary components. Backups and image-level restores are often the safest route for a full cleanup, especially in business environments where data integrity matters.
-20251114115649.webp)
A short real life example
Imagine a small nonprofit that wanted to accept donations in Bitcoin. A volunteer tests a third party wallet that promises simple integration. They install it and share login steps with the team. Within days, donors report wrong transaction destinations and the nonprofit’s laptop shows signs of remote activity.
Later analysis finds a fake wallet package and a DarkComet presence. The attackers had harvested keys and credentials and used them to initiate fraudulent transfers. That story shows how easy social engineering plus a recycled RAT can become a major breach.
Technical Breakdown
When analysts started digging into the fake Bitcoin tool, the first thing that stood out was how quietly the hidden malware settled into the system. It did not drop files in obvious places. Instead, it tucked a renamed executable inside a roaming folder that most people never check. That single move allowed it to blend in with normal Windows activity and avoid raising suspicion. The moment it landed there, it added a startup entry so it would relaunch every time the computer powered on. Nothing flashy, nothing noisy, just a silent re-entry built into the system’s routine.
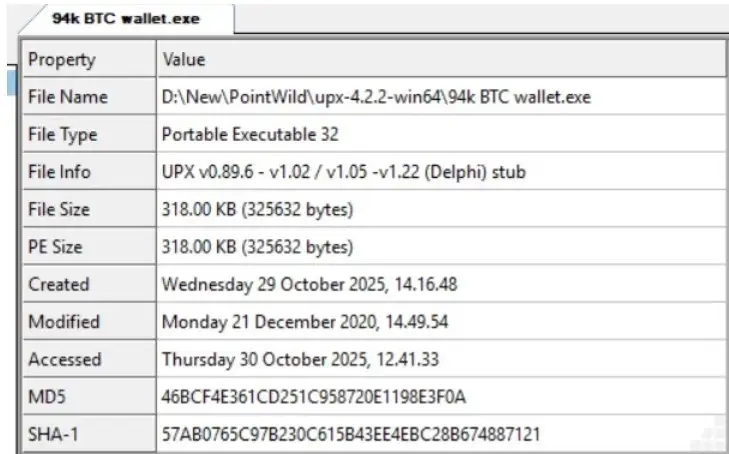
File Info image-Source
Once researchers peeled back the layers, they saw the executable was packed. That explained why simple antivirus checks barely reacted. The compressed structure hid the actual malicious code until someone unpacked it manually. After unpacking, the file finally revealed a familiar layout that lined up with traits of old DarkComet families. It was almost like the attacker reused a vintage RAT engine but wrapped it inside a modern crypto tool.
During behavior tests, the malware created a unique internal lock so only one copy could run at a time. This tiny detail said a lot about the attacker’s experience. They didn’t want the system to glitch or crash, because stability is what keeps a RAT alive.
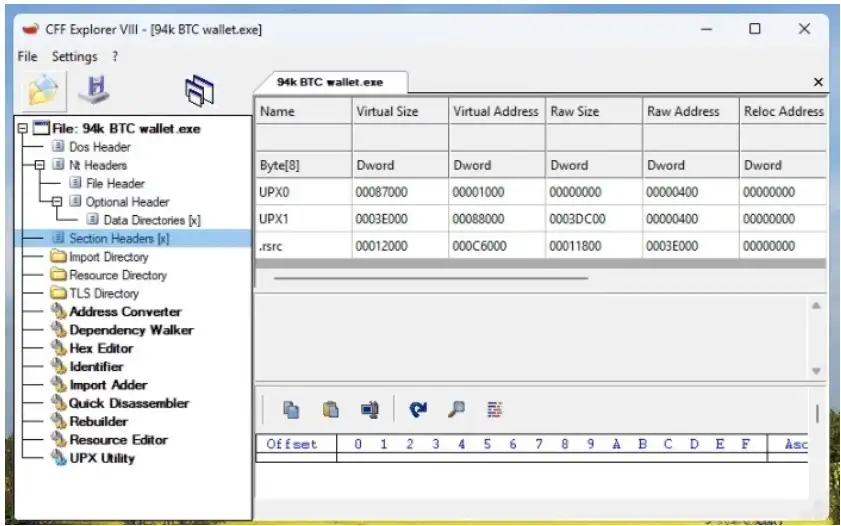
UPX Packed: Source
The more the analysts watched the sample, the more it started acting like a typical remote access implant. It tried reaching a command server again and again, even though the server didn’t respond. Meanwhile, it slipped a portion of its code into a legitimate Windows process. After that, the infected process quietly captured keystrokes and screen details. Instead of sending everything instantly, it saved little log files inside the system, waiting for the perfect moment to upload them.
Practical prevention steps you can take today
Do not run executables from untrusted sources. Use official vendor sites or app stores and verify digital signatures when possible. Keep operating systems and security tools patched. Enable multifactor authentication on wallets and exchange accounts so stolen passwords alone are useless.
For organizations, implement application allow lists, network segmentation, and outbound traffic monitoring to catch unexpected C2 connections. These measures will make it far harder for any RAT, including DarkComet RAT malware, to succeed.
Train your teams to question offers that seem too convenient and to verify tools before installing. In the world of crypto, skepticism is a useful security control.
Actionable takeaway
Fake Bitcoin tools are an opportunistic delivery method. The real threat lies in what they drop. The DarkComet RAT malware is an example of how old tools remain dangerous when repackaged for modern scams. Protecting yourself starts with cautious downloads, solid backups, and layered defenses that limit what a single compromised machine can reveal.
FAQ
Q: How can I tell if a Bitcoin tool is safe A: Verify the publisher, download only from official sites, check digital signatures, and search for community reviews. If the installer asks for system level permissions without clear purpose, treat it as suspicious.
Q: Does antivirus detect DarkComet reliably
A: Many antivirus engines flag known DarkComet builds, but attackers modify samples to evade detection. Use layered detection including EDR and network monitoring.
Q: If my PC is infected what steps should I take A: Isolate the device from the network, document evidence, run forensic scans if possible, restore from a clean backup or perform a full OS reinstall, and rotate credentials used on that device.
Q: Are Macs and Linux machines affected A: DarkComet historically targets Windows. However social engineering can deliver other cross platform threats, so follow safe download practices on any OS.
Author: Hoplon Infosec
Bio: Security enthusiast with over 10 years in mobile cybersecurity. Connect with me on LinkedIn.
Address: 1415 W 22nd St Tower Floor, Oak Brook, IL 60523, United States
Phone: +1 773-904-313 , Contact: [email protected]
About/Privacy: At Hoplon Infosec, we provide expert insights into cybersecurity. Our editorial policy: all articles are written by in-house specialists or thoroughly reviewed by them to ensure accuracy, credibility, and up-to-date information.
Share this :