DaVita Ransomware Attack Exposes Millions: What You Need to Know

Hoplon InfoSec
24 Aug, 2025
DaVita Ransomware Attack
You sit down with tea, half reading, half daydreaming, then a headline snaps you awake. The DaVita ransomware attack. Your mind goes straight to the practical things. Are appointments safe? Are lab results exposed? Is this going to mess with treatment? That quiet anxiety tells you what numbers cannot. A breach is not only a technical incident. It is an interruption of trust.
A few minutes later you start reading beyond the headline. You realize this is bigger than a single clinic or a random outage. It touches a national network and a population that depends on predictable care. That is why it lands like a punch to the gut. Not because computers failed, but because people rely on those computers to keep life steady.
Why DaVita Matters: A Lifeline for Kidney Patients
DaVita is a heavyweight in kidney care. It operates close to three thousand outpatient clinics along with home services, and it is one of the largest providers of dialysis in the United States. When a company like that stumbles, the ripple reaches a lot of living rooms. The DaVita ransomware attack was never just a corporate storyline. It sat in the middle of people’s routines and health plans.
Dialysis is not elective care. Most patients cannot skip a week and make it up later. That is why any disruption, even a partial one, raises blood pressure for families and staff. The company said critical care continued, which matters more than any other single detail because it separates inconvenience from real harm.
The Quiet Breach: When It All Began
Intrusions rarely arrive with flashing lights. Investigators say the initial unauthorized access began on March 24, 2025, and was discovered on April 12.
In that window the actors moved quietly, took data, and encrypted parts of the network. The moment the breach was identified, DaVita isolated systems and activated response plans. That was the point when the DaVita ransomware attack turned from a hidden problem into an all-hands incident.
Those dates matter for another reason. They explain why early public updates felt incomplete. You cannot assess a breach in a day or two. It takes time to rebuild logs, verify what was accessed, and coordinate with regulators and law enforcement. The timeline matches what you see in other healthcare incidents where the first notice is simply that something is wrong, not a final tally.
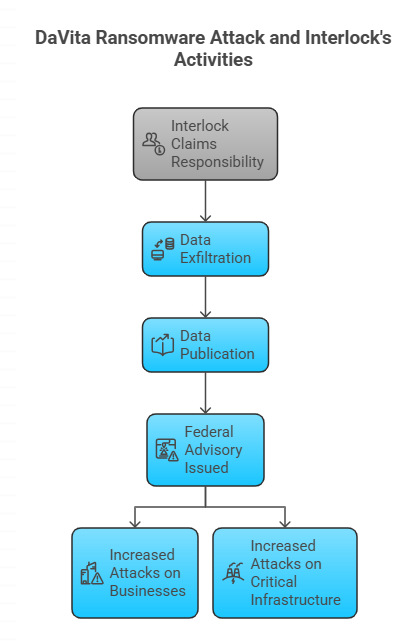
Interlock Emerges: Who Claimed the DaVita Ransomware Attack
Soon after containment, a group calling itself Interlock claimed responsibility. Public posts tied to the group said they exfiltrated a large volume of information and even published part of it to pressure the company. Reports vary on the numbers, but the theme is consistent.
This was a data theft plus encryption event, not a simple lock-and-unlock shakedown. That is why the DaVita ransomware attack drew so much attention from security analysts.
Federal agencies later issued a joint advisory about Interlock’s activity, warning that the group had accelerated attacks on businesses and critical infrastructure. That broader alert helps place this case in context. It was not a one-off. It was part of a run of aggressive campaigns targeting sensitive industries.
What Was Snatched: Scope and Scope Again
Early notices covered a little over one million people, which already counts as a major event in healthcare. As the review expanded, filings to federal regulators reflected a higher number. By late August, the U.S. Health Department site showed that around 2.7 million individuals were affected. Those moving targets are typical when investigators are still de-duplicating records and mapping systems. The DaVita ransomware attack sits near the top tier of breaches reported this year.
Why do totals shift? In large networks, the same person may have multiple entries across labs, billing, and clinic systems. Some records belong to former patients, contractors, or payer workflows. Reconciling all of that takes weeks. It is more honest to publish rolling updates than to guess once and be wrong.
How Labs Became the Digital Jackpot
The core of the breach was a laboratory database. Labs hold concentrated, highly valuable information. Identity data. Clinical data. Insurance data. In some cases, investigators say the files included full birthdates, Social Security numbers, insurance details, clinical results, and even images of checks or tax identifiers for some individuals. Put simply, labs are where personal and medical lives meet inside a computer. That is why the DaVita ransomware attack set off alarms across the industry.
Attackers look for targets where the data can be monetized in many ways. Health information can fuel identity fraud, medical billing scams, and social engineering. If a single database ties a name to a policy number and a diagnosis code, a criminal can build convincing phishing messages or open fraudulent accounts. That is the uncomfortable truth that security teams have to plan around.
Patients Still Got Dialysis: How Care Kept Flowing
Here is the part that matters most to families. Clinics stayed open. Staff leaned on manual methods where needed, switched to paper workflows, and prioritized continuity of care while the IT teams cleaned up.
Public statements emphasized that life-sustaining treatments continued without interruption. That is what separates a bad day from a disaster. The DaVita ransomware attack hurt systems, not appointments.
Keeping a national operation running during an incident is not luck. It reflects planning. Incident runbooks, downtime procedures, and backup communications are boring to set up, but they let teams protect patients when the screens go dark. This case is a practical example of why tabletop exercises and redundancy are not optional in healthcare.
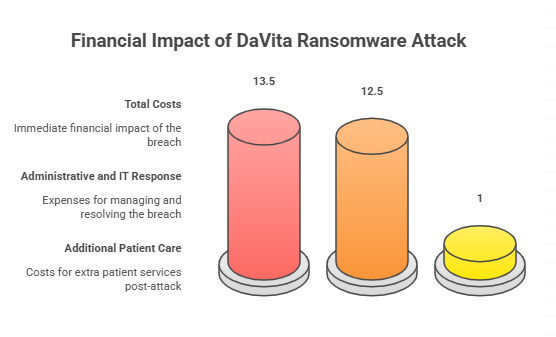
The True Price: Dollars, Disruption, and Data
Incidents like this burn money quickly. According to company disclosures and subsequent reporting, the breach led to about 13.5 million dollars in costs during the second quarter of 2025. Roughly 12.5 million covered administrative and IT response, and about 1 million covered additional patient care expenses.
Those figures do not count longer tail costs like legal fees, insurance changes, or deferred billing. The DaVita ransomware attack will have a financial echo well beyond one quarter.
There is another cost that is harder to measure. Trust. When people share lab histories and identity documents, they do it because they must. Rebuilding confidence after any breach requires ongoing transparency. Clear notices, support services, and visible security upgrades are not public relations. They are part of clinical care in the digital era.
At Least the Data Is Not Being Misused Yet
As of the latest updates, the company has said it has not observed confirmed misuse of the stolen information. That is a relief, but it does not mean the risk is gone. Identity data has a long shelf life. It can sit in private forums for months before being used. The right response is calm vigilance. The DaVita ransomware attack is a reminder that harm can arrive long after headlines fade.
If you received a notice, treat it like a smoke alarm that keeps chirping until you change the battery. Keep an eye on credit reports, health plan explanations of benefits, and tax transcripts. Small, regular checks beat one big audit at the end of the year.
Identity Safety Net: How DaVita Is Helping You
Notices mailed to affected individuals include enrollment codes for complimentary credit monitoring and identity protection through Experian IdentityWorks.
Depending on your relationship with the company, coverage lasts 12 to 24 months. The package typically includes credit reports, alerts, and identity theft insurance. If you were notified, enrolling is worth the few minutes it takes. That is the direct personal support tied to the DaVita ransomware attack.
Credit monitoring is only part of the safety net. Take advantage of free credit freezes from the bureaus, and turn on account alerts with your bank and insurer. Pair those steps with basic cyber hygiene at home. Strong passwords, a reputable password manager, and multi-factor logins cut the risk of follow-on fraud.
A Wider Trend: Healthcare’s Growing Cyber Woes
This event lands in a rough year. Healthcare has been a consistent target because the data is rich and downtime is costly. Reporting around this case shows it ranks among the larger incidents reported to federal regulators in 2025. Security teams know the pattern.
An initial foothold through a phish or vulnerable service, followed by lateral movement and data theft. The DaVita ransomware attack fits that broader profile.
Government agencies warned specifically about the Interlock group this summer. That joint advisory matters because it shares the technical indicators defenders can use to block future attempts. It also underscores that many providers are fighting the same battle at the same time, which is why information sharing through industry groups and ISACs is so valuable.
Analogies That Stick: The Heist in Your Clinic
Picture the lab system as a vault in a bank. The attackers scoped the building, found a side door, and slipped in after hours. They copied stacks of documents, locked a few rooms, and left a note. Meanwhile, the front desk still opened in the morning, and tellers kept serving customers.
That is the strange part. A robbery that the public barely sees while the back office scrambles. In that image you can feel how the DaVita ransomware attack looked from both sides.
Analogies help because they translate a technical story to everyday experience. You do not need to know how an endpoint detection sensor works to understand that layered locks, cameras, and trained staff make a bank safer. Healthcare needs the same layers. Good logs, network segmentation, strong authentication, and regular drills. None of it is flashy. All of it matters.
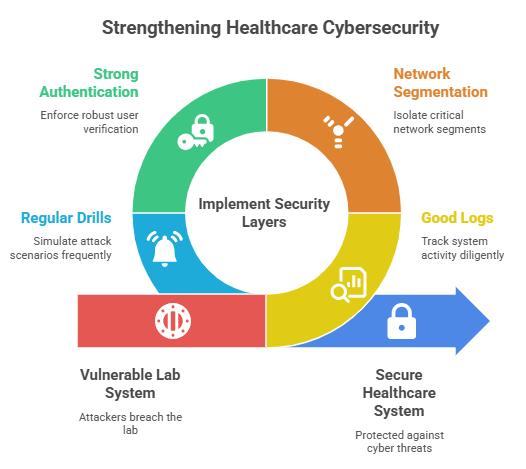
Fixes and Forewarnings for Other Clinics
If you run a clinic or a lab, start with the basics. Segment networks so credentials in one area cannot unlock everything else. Require multi-factor authentication on remote access and administrator accounts. Patch aggressively and track your attack surface, especially internet-facing systems.
Train staff to spot phishing. These steps help contain the damage when something goes wrong. The DaVita ransomware attack is a case study in why fundamentals are not optional.
Then move up the stack. Test your incident response plan with tabletop exercises. Practice switching to downtime procedures so staff are not learning under stress. Keep immutable backups and test restores on a schedule. Join your sector’s information sharing group so you see the latest indicators quickly. What you do before an incident is what saves your operation during one.
What You Can Do Now (Because It Is Personal)
For individuals, a simple checklist works. Enroll in the free monitoring if you received a letter. Place a credit freeze with the major bureaus. Turn on alerts for new credit inquiries and large transactions. Watch for mail that looks like insurance explanations you do not recognize. Save your notice letter in case you need it later. Those small habits help you stay a step ahead after the DaVita ransomware attack.
If you manage a household for someone receiving dialysis, add a basic data kit to your health folder. Copies of ID, insurance cards, clinic contacts, and a short log of appointments can make it easier to verify legitimate calls and ignore scams. The goal is not to live in fear. It is to make fraud inconvenient for the people who try it.
Summary Table
TitleCore IdeaPanic StartHeadline shakes trust, not just tech.Why DaVitaVital dialysis provider; disruption hits lives.Breach TimelineBegan Mar 24, found Apr 12.InterlockGroup claimed attack, stole + encrypted data.Scope2.7M people affected.Lab JackpotLab DB with IDs, SSNs, medical + insurance data.Care FlowedDialysis continued via manual workarounds.Cost$13.5M + trust damage.MisuseNo misuse yet, risk remains.Safety NetFree credit/ID monitoring offered.TrendPart of rising healthcare cyberattacks.AnalogyLike a bank heist—back office hit.FixesStrong basics + drills for clinics.You Can DoFreeze credit, watch alerts, prep docs.Final NoteHuman resilience kept care steady.
Final Thoughts: Hope, Healing, and Human Resilience
The last word belongs to the people who kept the chairs full and the machines humming. Incidents will keep coming. Technology will fail sometimes. What cannot fail is the human part. Staff who adapt, patients who show up, and leaders who tell the truth. The breach was serious and costly, but the story also includes steady hands and smart planning. That is worth remembering when the next headline lands.
Share this :