Discord Data Breach 2025: Hackers Steal 1.5 TB of User Data and ID Photos

Hoplon InfoSec
17 Oct, 2025
I remember opening my email and seeing an official notice. It felt like a weight I couldn't quite put my finger on.
Discord is where a lot of people meet up with friends, plan games, and start small groups. You shouldn't have to worry about whether a picture of your passport or driver's license might show up somewhere you don't know.
The Discord data breach 2025 took away that comfort for thousands of users and raised a lot of uncomfortable questions about who has our data and how well those guardians actually protect it.
The numbers in the headline were shocking, and the story moved quickly. But the human side of this breach is quieter and deeper, and that's the part that matters.
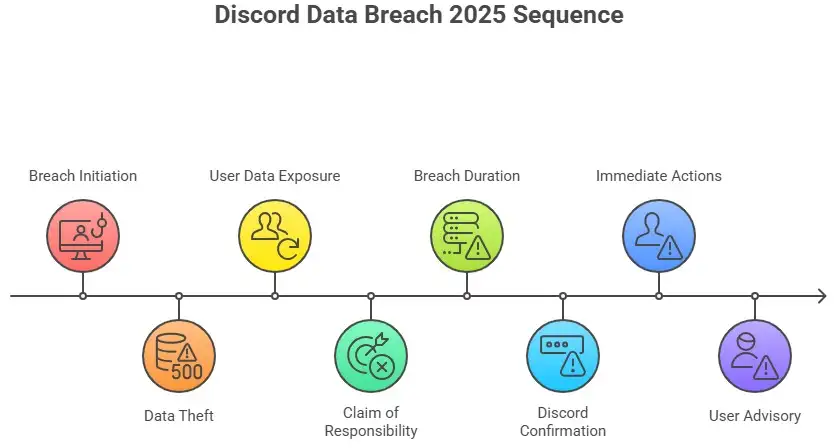
A simple explanation of how the breach happened
A customer support system run by a third-party vendor was at the center of the event. Attackers got into that support environment and took information from support tickets and attachments.
To put it another way, Discord's main infrastructure was not the problem. The weak link was a partner who could see private user information.
The group that took credit for the attack said they got a lot of data and used it to blackmail the company for money. They said they had 1.5 terabytes of data and more than two million pictures of government IDs.
Discord disagreed with those numbers and said that the public claims were part of an extortion scheme. The fact that hackers and companies said different things is a big reason why the story didn't end quickly.
The third-party point of view and why it matters
This attack didn't break into accounts by guessing passwords or brute-forcing servers. Instead, it used a hacked support account that was supposedly owned by an outsourced agent. This gave the attackers access to ticket data and attachments.
They had several hours to collect what they wanted once they got inside. This is a common pattern in supply chain or third-party incidents: compromise a smaller target that affects a lot of users, then move on without making a big deal out of it.
That feels especially wrong for users. Support tickets often have proof of identity sent to fix a problem, requests to change age restrictions, or payment information. T
hose are private moments, and when people see them treated like a database to be harvested, it changes how they think about submitting documents online. The vendor path here shows that keeping users' trust is about more than just protecting your own code.
What the attackers said and what Discord said was true
The people behind the threat sent out messages and samples that made it seem like they had stolen millions of ID photos and ticket records. Those are the shocking claims that quickly spread through social media and forums.
The attackers' public face was meant to scare people and make their extortion attempt more powerful.
But Discord's official update was more cautious. The company said that only a small number of users who had contacted customer support were affected and that it had found about 70,000 users whose government ID photos may have been leaked.
Discord also made it clear that they did not take full credit card numbers, passwords, or messages that were not support-related. That gap between the two extremes made it harder for users to figure out if they were affected.
Who leaked the information and why
A group that goes by the name Scattered Lapsus $ Hunters came out in connection with the documents and screenshots that were posted online.
The group's behavior included stealing from the company and making fun of it in public, which was meant to humiliate the company and get them to pay. Analysts who keep an eye on similar gangs say that these people often mix showmanship with data dumps to get attention and gain power.
Extortion is the main reason for many modern breaches: take sensitive information, threaten to release it, and demand money. Because IDs can't be changed like passwords can, the threat feels more real when there are pictures of government IDs. That's why businesses and the government are very concerned about this kind of theft.
What was at risk for users?
People had given the compromised items to support, like names, account handles, email addresses, parts of billing records like the last four digits of a card, IP logs, and attachments like ID photos.
People who needed proof of age for their appeals got those ID pictures for that reason, and they ended up being a target. That kind of exposure makes users more likely to fall for identity theft, phishing, and social engineering schemes.
Ticket transcripts can have more than just the documents themselves; they can also have information that makes scams seem more real.
For example, an attacker who sees a support exchange about a refund request can craft a follow-up message that looks deeply authentic, referencing details only an insider would know. That makes it more likely that follow-up fraud will work.
The technical story, but without the jargon
Investigators said that the breach was an account takeover, not a code-level exploit. One set of credentials opened all the doors. Once the attackers had access, they used the support platform's tools and APIs to get records, just like they were supposed to.
That is a simpler but often effective way to get into data troves: compromise a legitimate credential and then act from inside the system.
This kind of attack shows that strong engineering defenses alone aren't enough. Better process controls, stricter access management for vendors, short-lived access tokens, stronger multi-factor routines, and strict rules about how long sensitive uploads can be kept all help. In real life, it's harder to put those things into action with a lot of partners than it is with just one company.
What Discord did and what users should expect from companies now
Discord acted quickly to cut off the vendor's access, start a forensic review, tell the police, and email users who might have been affected from an official address.
The company also made it clear that it would not pay ransom demands and that it was working to make third-party systems more secure. That order is what users should expect from responsible handling of incidents.
But being open is still important. People want to know exactly if their information was involved, how long it was kept, and what steps will be taken to make sure it doesn't happen again. Clear timelines, easy-to-understand notification emails, and specific steps for those affected are better for rebuilding trust than vague statements. Regulators will also pay close attention to these kinds of answers.
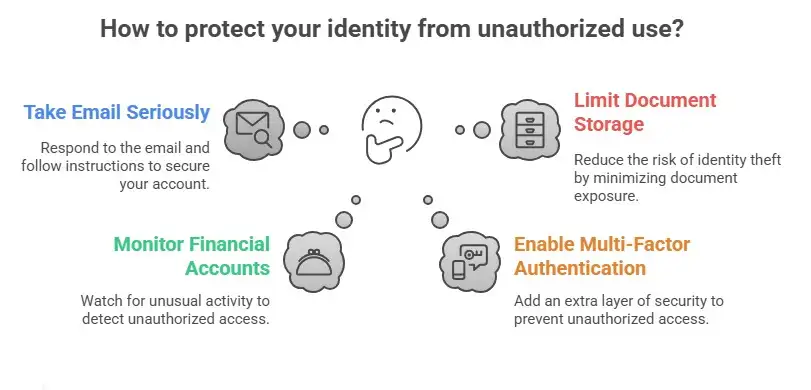
Users can take these two short, useful steps right now.
If you got an email from [email protected] saying that your ID might have been seen, take it seriously and do what they say. Keep an eye on your financial accounts and be on the lookout for strange messages that mention the support ticket or any other information that can only be found in a support exchange. Those signs are the first signs that someone is using your identity without your permission.
Also, turn on multi-factor authentication for all of your important accounts and limit the number of places where you keep pictures of government documents. If a platform asks for a scan, ask them how long they will keep it and if you can delete it after they check it. Those little things you do every day help lower your long-term risk.
The main lesson for businesses and regulators
This case is another reminder that risk in the supply chain and with vendors is a problem that needs to be dealt with right away. For scale or cost reasons, many businesses hire third parties to handle customer service.
This makes an external attack surface that needs to be treated like an internal one. Vendor audits, strict access controls, and security controls that are required by contract are now all important parts of corporate security programs.
When outsourced providers are involved, regulators will probably want clearer accountability. Users gave Discord their information with the hope that it would be safe, and many will expect companies to be responsible for problems that happen later. In the weeks and months after an event, that expectation has legal and reputational effects.
Final thoughts and a useful lesson
People who give proof of identity to fix a problem or get their account back are acting in good faith. This breach makes it clear that companies need to repay that trust with strong controls, short retention periods, and real vendor governance, not just checkboxes.
The effects of this event won't just be seen in the news; they will also be seen in how seriously platforms change the way they do business.
The best piece of advice for anyone who writes or talks about this event is to make it clear to their audience whether they were affected and what to do next. When you give someone honest information and clear actions, their distress goes away faster.
In response to the Discord Data Breach , Hoplon Infosec can help protect organizations with Deep and Dark Web Monitoring to detect leaked data early. Their services in endpoint security and penetration testing also ensure vulnerabilities are identified and secured, keeping user data safe and building trust.
Share this :