How DragonForce and Anubis Are Changing the Ransomware Game in 2025
Hoplon InfoSec
27 Apr, 2025
In 2025, ransomware continues to disrupt organizations worldwide despite significant law enforcement efforts to dismantle major criminal operations. Two emerging groups—DragonForce and Anubis—are pioneering new affiliate models that enable them to diversify their techniques, reach more victims, and sustain profitability even as businesses bolster their defenses. Understanding these developments is crucial for any organization seeking to protect its data and reputation.
From RaaS to “Cartel” DragonForce’s Strategic Reinvention
Origins and Rapid Growth
DragonForce first appeared in August 2023 as a typical ransomware-as-a-service (RaaS) provider, leasing its encryption tools to affiliates in exchange for a ransom share. By February 2024, the group was aggressively advertising on underground forums to recruit partners. Their leak site listed 136 victim organizations by March 2025, a testament to the operation’s rapid expansion.
The “Cartel” Rebrand and Distributed Model
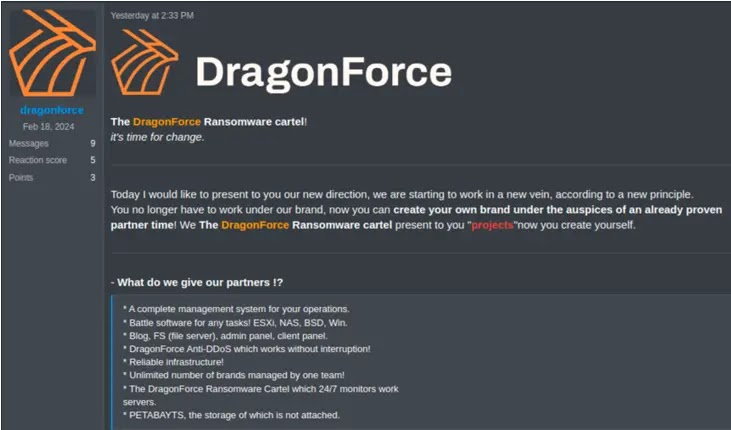
Recently, DragonForce rebranded itself as a “cartel,” signaling a strategic shift. Instead of a centralized brand, the cartel model allows affiliates to launch sub-brands under the DragonForce umbrella. These sub-brands can operate with customized names, logos, and affiliate terms while relying on DragonForce’s infrastructure for encryption, payment processing, and leak sites. This distributed approach offers affiliates greater autonomy and helps DragonForce evade disruption by diluting the visibility of any single brand.
Anubis’s Three-Tiered Extortion Framework
Introducing Multiple Attack Vectors
Anubis emerged on underground forums in late February 2025 with a novel recruitment pitch: three distinct extortion options, each with its profit-sharing ratio. By diversifying beyond straightforward encryption, Anubis appeals to a broader range of cyber criminals and complicates defensive planning.
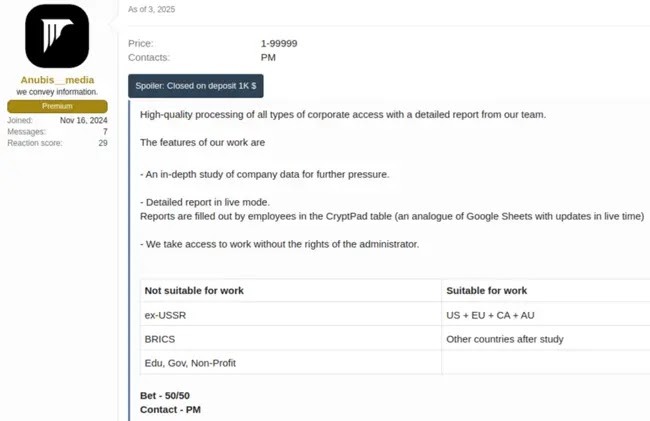
- Encryption RaaS (80% affiliate share): The classic model. Affiliates deploy ransomware to encrypt files, and Anubis handles the decryption keys and payment portals.
- Data Ransom (60% affiliate share): Affiliates focus solely on exfiltrating sensitive data. Victims are charged for the return or non-publication of stolen information.
- Accesses Monetization (50% affiliate share): Geared toward operators with network access. Anubis provides negotiation support to extract payments from compromised organizations.
Innovative Pressure and Negotiation Tactics
Anubis’s “data ransom” strategy includes publishing in-depth “investigative articles” on Tor, complete with excerpts of stolen documents. These articles are password-protected, allowing victims to review evidence and negotiate directly. If negotiations stall, Anubis escalates by publicly naming victims on social media (e.g., X, formerly Twitter) and notifying their customers, partners, and regulators.
Most striking is the threat to report non-paying organizations to data protection authorities, such as the UK Information Commissioner’s Office, the U.S. Department of Health and Human Services, and the European Data Protection Board. While ransomware groups have occasionally leveraged regulatory pressure before—such as the GOLD BLAZER group’s reported ALPHV breach to the U.S. SEC in November 2023—Anubis institutionalizes this tactic as part of its core model.
Why New Affiliate Models Matter
Adaptation to Increased Resistance
Organizations are becoming more resilient: improved backups, zero-trust architectures, and cyber insurance policies reduce the likelihood and impact of ransom payments. In response, ransomware operations innovate their business models. DragonForce and Anubis can maintain revenue streams even if one tactic becomes less effective by offering flexible affiliate terms and varied extortion methods.
Challenges for Defenders
These models complicate threat detection and incident response. Security teams must anticipate not only encryption-based attacks but also stealthy data exfiltration and reputational blackmail. Traditional endpoint defenses may stop file encryption but miss data theft. Likewise, public relations and legal teams must be prepared for the social and regulatory fallout engineered by threat actors.
Practical Recommendations for Organizations
Strengthen Data-Centric Defenses
- Implement robust data loss prevention (DLP): Monitor and control sensitive data flows to detect exfiltration attempts.
- Encrypt data at rest and in transit: Even if attackers steal files, encryption can render them unusable.
- Regularly test backups: Ensure backup systems are isolated, immutable, and quickly recoverable.
Enhance Detection and Response
- Deploy network traffic analysis: Identify unusual data transfers to external hosts or Tor nodes.
- Adopt endpoint detection and response (EDR): Look for indicators of ransomware staging, such as mass file access or privilege escalation.
- Run tabletop exercises: Simulate encryption and data-theft scenarios, including public disclosure threats and regulatory reporting.
Prepare for Reputational and Regulatory Pressures
- Coordinate with legal and PR teams: Predefine communication plans for ransomware and data-leak incidents.
- Engage with regulators proactively: Understand breach notification requirements in all relevant jurisdictions.
- Monitor threat actor communications: Use threat intelligence services to track leak sites and social disclosures targeting your organization.
Conclusion
The ransomware landscape 2025 is characterized by agile business models that blend traditional encryption with data extortion and reputational blackmail. DragonForce’s “cartel” framework and Anubis’s three-tiered extortion options exemplify how cybercriminals evolve in response to stronger defenses. Organizations must likewise adapt by strengthening data-centric protections, enhancing detection capabilities, and preparing for the broader consequences of an incident. Businesses can only stay one step ahead of these innovative threat actors through a holistic, forward-looking security strategy.
Share this :