EV Charging Provider Data Breach: Customer Data Exposed

Hoplon InfoSec
23 Sep, 2025
EV charging provider data breach
You drive up to the public charging station, plug in, and go about your day. You could get coffee and look at your phone. Charging your car feels like the future. But what if that simple act showed more than your battery needed? That’s what happened when an EV charging company admitted to a data breach and said that customers’ personal information was accessed without permission. It’s the kind of twist that no one sees coming until it happens, and now we’re all watching.
Many users are upset about the EV charging provider data breach, especially those who thought their information was safe. But as we’ll see, the lines between “secure” and “vulnerable” aren’t as clear as most people think.
What happened exactly:The timeline of the data breach at the EV charging company
On September 19, 2025, Digital Charging Solutions GmbH (DCS), a company that provides white-label charging services across Europe, noticed strange activity in its logs. This is when the story really starts.
Forensic analysts soon discovered that one of DCS’s vendors, a service provider, had accessed records without permission. Names and email addresses of customers showed up in places that shouldn’t have been accessible outside of the customer-support portal.
DCS started looking into it within hours. By the next day, they had told the few affected users (in the single digits so far), gotten outside cyber investigators involved, and taken away the third party’s credentials.
Who is taking part: Provider, third-party service, and customers
DCS, the company that provides EV charging and confirmed the data breach, is at the center. DCS works with car makers and fleet operators and helps set up branded charging stations. Their systems are supposed to keep payment and support data separate, which is a big part of what was revealed and what wasn’t.
Then there’s the third-party service provider, which is a company that helps with customer support. They had permission to use it, but it seems like they went too far. That’s when the unauthorized access happens.
Last but not least, customers. Not a lot yet, but enough that names and email addresses have been stolen. DCS also sent some customers email alerts. A lot of people were worried when they heard about the EV charging provider data breach. Who owns their data, and how safe are they?
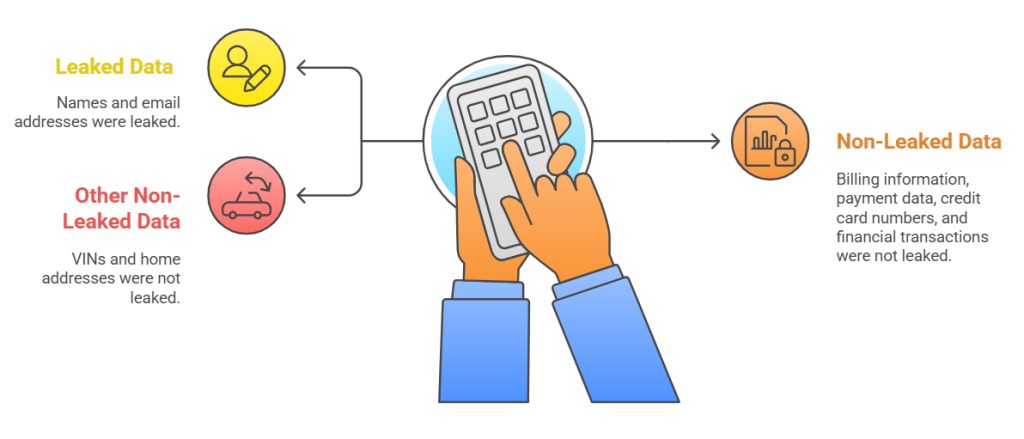
What information was made public: names, email addresses, and what wasn’t leaked
To be clear, the data that was leaked in this EV charging provider data breach is only names and email addresses in some cases. There is no confirmation of anything more sensitive.
It is important to note that the information that was accessed did not include billing information, full payment data, credit card numbers, or records of financial transactions. DCS said it keeps payment systems separate by using tokenization and point-to-point encryption.
There is also no sign that VINs or home addresses have been leaked in this case. That lowers some risks, but even with “just” names and email addresses, there is still a risk of spam, phishing, and identity theft.
Root cause: What caused the unauthorized access?
Initial findings indicate insider misuse rather than a breach by an external hacker. That could be a member of the support staff or someone from the third-party company using credentials in a way that is not allowed.
We are still looking at logs from different systems, and some of the things we have found are strange SSH sessions and API calls that shouldn’t have happened. So, even though the vendor had permission to access some data, it happened outside of the workflows that were supposed to happen.
There is also the issue of weak credential management. Credentials for third-party support are often a weak point because they are sometimes shared and not watched closely enough. This incident shows that even “permitted access” needs to be closely watched.
Third-party risk: Why vendors are important for security
One of the most important things to learn from this data breach at an EV charging company is how risky vendors can be. You could lock down your systems, use encryption, and keep an eye on things inside, but if a vendor who helps you with customer service can freely browse data or abuse access, you are still at risk.
To save money or grow quickly, many businesses hire specialized companies to handle customer service. But that also means that outside people can get to sensitive information. Contracts may require privacy, but enforcement and monitoring are often not as strong as we think they are.
Example from real life: Earlier this year, Shell’s Recharge network had a huge leak because a cloud database that wasn’t set up right showed internal logs. The relationships with vendors or contractors are a big part of those kinds of exposure.
Finding the breach: logs, strange things, and what set off alarm bells
DCS found out about the breach when its system logs showed strange activity. There were strange entries, SSH sessions that weren’t expected, and signs of API calls that weren’t normal. That was a sign of trouble.
It can’t be stressed enough how important it is to keep an eye on things all the time. If DCS had waited longer to analyze the logs, the unauthorized access could have gone on for a lot longer. Finding problems early often keeps them from getting worse.
Forensic analysis also helped keep disks, memory snapshots, and other things safe. That’s forensic hygiene, which lets you find out how far access went, what was seen, and who did it.
Immediate response: What the provider did first
DCS acted quickly after finding out about the EV charging provider data breach. They took away the vendor’s credentials right away. They made access tokens change every time.
All third-party users had to use multi-factor authentication (MFA). They also improved auditing, especially for database queries (SQL anomaly detection), to stop strange patterns from happening.
Customers who were affected (so far, those in the “single-digit range”) were directly notified, in line with GDPR’s breach notification rules. People in charge were told. Steps were taken to make sure that the charging service would continue billing parts were not affected.
Steps to lessen the damage: technical and procedural
To keep customer support systems separate from payment and billing systems, DCS is using encryption and tokenization, requiring MFA, setting up anomaly detection, and checking every access. They are hiring outside experts to help with the forensic work.
In terms of process, they will probably change vendor contracts, make access permissions stricter, increase oversight, and maybe even plan regular reviews of how vendors act. Also, teaching employees or vendors what proper access means and what is off-limits.
They also told customers to be careful: don’t use the same password on more than one site, and be on the lookout for phishing. A lot of people forget about that, but it’s very important because in a lot of breaches, the email addresses that are leaked are used for scams.

Legal and regulatory issues: GDPR, data protection, and the people in charge
GDPR is very important for DCS because it works in Europe. Article 33 of the GDPR says that once a breach is known, you must tell the people who were affected and the supervisory authorities “without undue delay.”
DCS had to report this data breach because it was an EV charging provider. Not following the rules could result in big fines, damage to your reputation, or even limits on how you can do business.
Similar data protection laws are in place in other places as well. The UK has the Data Protection Act, the EU has the GDPR, and many other countries are making new laws about digital privacy. Local rules may also require vendors to disclose how they handle data across borders, among other things.
Effect on customers: trust, risk of phishing, and chances of identity theft
This breach only exposed names and emails, but for customers, that feels like an invasion of privacy. Your name and email address are personal information that can be used in phishing attacks. Scammers often use a real email address and the name of a company to pretend to be a service provider.
Some users might be more afraid of identity theft if more data is leaked or if the exposure spreads. Even though payment information is safe right now, trust is low. It’s hard to get trust back once you’ve lost it.
Stories from the real world: After one visit to Shell Recharge, some fleet customers began checking their credit reports, updating their contact information, and asking for more information. Some people didn’t want to use certain services for a while.
Context of the industry as a whole: Other EV charging data leaks and threats
This data breach at an EV charging company is not the only one. In 2023, Shell Recharge’s database leaked, exposing millions of logs, customer names, emails, and phone numbers. That put both individual and fleet customers at risk.
Also, studies show that attacks on electric vehicle charging systems are on the rise. Upstream reported that in 2024, about 6% of all automotive and smart mobility cybersecurity incidents had to do with EV chargers. This was up from about 4% the year before.
All of these problems point to the same weaknesses: vendors having too much access, cloud systems being set up wrong, logs not being protected, gaps in monitoring, and weak credential controls.
Things EV charging companies can learn: What to include from the beginning
If I were giving advice to an EV charging company, I would tell them to do these things from the start: make sure that support data and billing data are kept separate, use strong encryption, do regular audits, use zero-trust models for vendors, limit access permissions, and follow the least privilege principle.
Also, keep a close eye on and log everything. Not only do you need to collect logs, but you also need to look at them with tools that can find anomalies. And don’t think that vendors will always do the right thing; make sure there are contracts, oversight, audits, and penalties in place.
Another lesson is to practice incident response. DCS acted quickly when they saw the EV charging provider data breach. This is probably because they already had some plans in place. Things get worse if you wait until they go wrong.
What customers can do: How users should protect themselves
You might feel like you don’t have much control as a customer, but there are things you can do. First, don’t use the same password for more than one account. If an email gets out, using the same credentials somewhere else can be dangerous.
Keep an eye on your inbox. If you get emails that look like they are from DCS (or your charging provider), especially about payments or account suspensions, check with official sources. Breach leaks will be used by scammers.
Also, think about the permissions you give when you sign up. Do you let vendors share your information? What kind of information is being asked for? Being careful about privacy settings and only giving out the bare minimum of contact information can help keep you safe.
The best ways to keep your computer safe are no trust, encryption, and audit trails.
Providers should use a “zero-trust” architecture, which means that no one, inside or outside the organization, is automatically trusted. Verify every request and authenticate everything. Even from sellers.
Use strong encryption both when data is at rest and when it is being sent. Tokenize or limit access to private information. For example, billing systems should be more secure than customer service systems.
Set up continuous auditing so you can see who accessed what, when, and from where. Set up anomaly detection to flag strange patterns, like accessing data outside of business hours, a support user accessing multiple records, or an unusually high number of API calls.
Looking ahead:How this will change vendor contracts and monitoring
This data breach at an EV charging provider will likely make vendor contracts stricter. Expect more rules about how to handle data, punishments for misusing it, more frequent audits, and periodic reviews of who can access it.
Providers might start requiring vendors to use specific cybersecurity tools or meet certain certification standards. External security audits may become standard.
Monitoring will get better with SIEM systems, SOAR platforms, and so on. There will probably be more rules as well. Governments are paying attention to infrastructure for mobility, such as charging stations for electric cars. Privacy and safety are no longer up for debate.
Final thoughts: The EV charging provider data breach should make everyone pay attention.
In the end, this isn’t just a “company problem.” It has an effect on all of us who give our data to services. Charging EVs is a step toward a clean, green future. But privacy and security shouldn’t be left behind; they should be in the passenger seat.
The data breach at the EV charging provider shows that we need to protect customer information. When even simple things like names and email addresses get out, there is a risk of phishing, spam, and loss of trust.
We could come out stronger if providers, third-party vendors, regulators, and customers all learn the right lessons. But being too comfortable costs money. Because next time, more than just your name and email address may be shown. And for users, staying alert, asking questions, and demanding openness will help keep your identity safe in a connected world.
Follow us on X (Twitter) and LinkedIn for more cybersecurity news and updates. Stay connected on YouTube, Facebook, and Instagram as well. At Hoplon Infosec, we’re committed to securing your digital world.
Share this :