Extended Detection and Response (XDR)
What is XDR (Extended Detection and Response)?
Extended Detection and Response (XDR) is a comprehensive cybersecurity solution that integrates multiple security systems into one unified platform. Unlike the traditional security models where endpoint, network, cloud, and email are isolated to apply individual tools, XDR combines them into a unit. The integrated solution offers a fully visible image of the entire infrastructure of any organization, allowing it to detect threats faster and respond to them more efficiently.
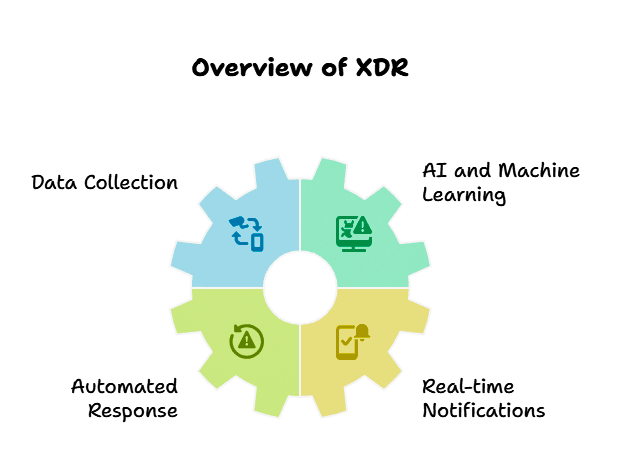
How Does XDR Work?
XDR is also able to collect and correlate security data across many different sources, including endpoints, network traffic, servers, cloud workloads, and email messages. With the help of powerful artificial intelligence (AI) and machine learning, XDR can detect suspicious patterns and anomalous activities among these mixed data points in a very short period. The moment they find a threat, XDR systems can instantly provide automated action, separate the infected regions, and notify security departments in real-time. This assists in reducing possible damage and interruption of business activities.
Key Components of XDR Systems
A powerful XDR platform should integrate three important entities:
- Data Collection: Constant surveillance in all digital grounds (servers, endpoints, cloud, networks, emails).
- Threat Analysis: Sophisticated AI-based analytics that detect and match criminal tendencies.
- Automated Response: Instant actions to isolate threats, block malicious activities, and notify cybersecurity teams immediately.
Benefits of Extended Detection and Response

XDR vs EDR (Endpoint Detection and Response)
XDR vs SIEM (Security Information and Event Management)
XDR vs Traditional Threat Detection
XDR vs MDR (Managed Detection and Response)
XDR vs NDR (Network Detection and Response)
XDR vs ITDR (Identity Threat Detection and Response)
XDR Solutions for Threat Detection
XDR Technology Explained
AI-Powered Threat Correlation and Context
Enhanced Root Cause Analysis and Forensics
Seamless Integration and Operational Efficiency
Future-Ready, Scalable Architecture
How to Implement XDR Effectively

Why Choose Hoplon Infosec?
Frequently Asked Questions
Everything you need to know about Extended Detection and Response (XDR)
We're Here to Secure Your
Hard Work
Protect your system from cyber attacks by utilizing our comprehensive range of services. Safeguard your data and network infrastructure with our advanced security measures, tailored to meet your specific needs. With our expertise and cutting-edge technology, you can rest assured that your system is fortified against any potential threats. Don't leave your security to chance – trust our proven solutions to keep your system safe and secure.
Share this :