The Fog Gang Struck on Brazilian Ministries - Another Ransomeware Attack

Hoplon InfoSec
30 May, 2025
“Imagine waking up one morning to find the most sensitive data from nine federal ministries and even the national mint was quietly packed away and sent overseas. That was a true story, which is happened on July 23, 2024, when the ‘Fog’ gang struck on Brazilian Ministries to freeze massive amount of data with ransomeware attack.”
What Happened? or Full story of The “Fog Gang Struck on Brazil”
In the early hours of July 23, 2024, Brazil’s IT security teams at nine different ministries including Finance, Health, and Justice started noticing odd traffic leaving their networks. Within hours, a ransom note appeared on dozens of government servers:
“If you are reading this, then you have been the victim of a cyberattack. We call ourselves Fog and take full responsibility for this incident.”
By the end of the day, investigators confirmed that approximately 28 gigabytes of sensitive files policy drafts, audit logs, and citizen databases had been transferred to two cloud servers based in the United States. The hackers demanded $1.2 million in cryptocurrency to hand back the decryption keys and promised not to publish stolen documents publicly.
How did it happen?
Brazil’s first big mistake was trusting a single layer of VPN security. To let staff work from home, each ministry opened a VPN port to the internet. However, they only requested a username and password no second code or token. Fog’s hackers either tricked users into handing over their passwords with fake “IT update” emails or tried leaked logins until one fit. With a valid account in hand, they stepped through the VPN just like any legitimate employee and found themselves inside the network.
Once inside, the attackers ran a quick sweep for old, unpatched servers. Several machines hadn’t been updated in months, and public exploit code was already floating around online. In minutes, the hackers used those known flaws to gain full control of vulnerable servers no magic, just a few clicks of readily available tools. From there, they pushed out their scripts to disable security software and cover their tracks.
Because all nine ministries shared the same network segment, moving on was frighteningly easy. The hackers used “pass-the-hash” techniques to jump from one server to the next with stolen credentials,abbing domain-admin tokens as they went. With virtually no internal firewalls or access controls, they roamed at will copying 28 GB of files, planting ransomware, and finally locking everything down. In short, one weak VPN layer, outdated machines, and a flat network design let Fog turn a small foothold intoto a full-blown siege.
Step 1: Reconnaissance: Before any breach, Fog did its homework. They:
Hunted for leaked credentials on public forums and dark-web marketplaces, looking for any government usernames or passwords.
Scanned Brazil’s IP ranges to find open VPN portsd out-of-date software that they could exploit.
This phase let them map out which ministries used which VPNs and which servers hadn’t been patched in ages.
Step 2: Initial Access: Armed with credentials and network intel, Fog moved in.
They logged in with valid VPN accounts they’d bought or phished, slipping past the gateway like legitimate users.
In some cases, they sentent a spear-phishing email carrying a malicious .LNK file; once opened, it planted a backdoor on an edge server.
Within hours, the attackers had a beachhead inside the ministry networks.
Step 3: Privilege Escalation & Lateral Movement: Inside that entry point, Fog wasted no time:
They ran custom PowerShell scripts and used “pass-the-hash” tools to elevate their rights turning a simple account into a domain admin.
With admin privileges, they hopped across servers, connecting to file shares, backup appliances, and other critical systems.
To stay hidden, they disabled Endpoint Detection & Response (EDR) agents and wiped system logs, erasing traces of their activity.
In under 24 hours, they owned the entire shared network segment.
Step 4: Data Exfiltration: Next came the heist:
Fog compressed sensitive documents into archive files.
They used tools like MEGAsync and FileZilla to upload roughly 28 GB of data to cloud servers in the U.S.
Every exfiltration step was timed to avoid bandwidth spikes that might trigger alerts.
Step 5: Encryption & Extortion: Finally, they delivered the ransom blow:
The gang deployed their AES+RSA encryption payload, locking down remaining files across all nine ministries.
On each locked server, a “ReadMe” note popped up, demanding $1.2 million in cryptocurrency for the decryption keys and threatening to publish stolen data if the payment wasn’t made.
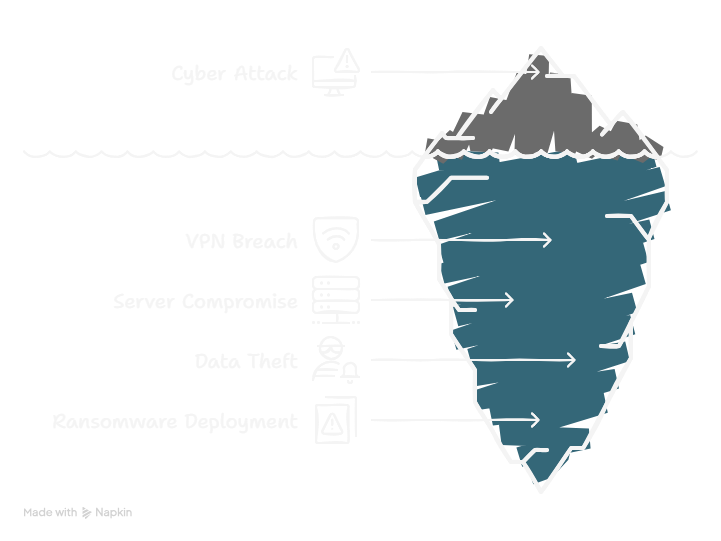
And just like that, what began as a subtle reconnaissance turned intoto a full-scale siege, crippling Brazil’s federal IT systems in a matter of days.
Who was Behind the Keyboard?
Imagine a shadowy collective so ruthless that they turn trusted government networks into their playground and vanish into the dark web before anyone even knows they were there. That’s the Fog gang, and they’re more than just “another ransomware crew.”
Since emerging in mid‑2024, they’ve rapidly evolved from low‑level attacks on schools and small shops into a full‑blown cyber army capable of toppling federal agencies. Their methods are cold, calculated and terrifying:
The Fog Gang
They surfaced without warning, slipping past defenses like ghosts. Their signature “double extortion” isn’t just about locking files it’s about blackmail so sinister that victims would rather pay than face public exposure of their deepest secrets.
eir TOR-hidden leak portal isn’t a simple blog; it’s an online torture chamber where they drip‑feed stolen data, inflicting maximum panic before any ransom is paid.
Size & Structure
Fewer than 20 core operators control everything from malware creation to high-stakes ransom negotiations. Each one is a specialist some write the code that silently worms through networks, and others manage encrypted communications on the dark web.
Behind the scenes, a network of freelancers handles the dirty work: phishing campaigns that strike like daggers in inboxes, rented VPNs for untraceable access,, and money-laundering rings that scramble cryptocurrency trails. This is organized crime at Internet speed and scale.
Possible Origins
Forensics on seized servers and VPN logs point to Eastern Europe likely Russia or nearby states where cybercrime syndicates enjoy a haven under lax enforcement. But make no mistake: their reach is global, and their aim is simple cripple your systems, steal your data, and leave you with a ransom demand as your only path to recovery.
This isn’t a drill. When Fog rolls in, they come with the precision of a scalpel and the brutality of a sledgehammer. Understanding their ruthless playbook is the first step in defending against it. Stay alert, strengthen every defense layer, and never assume you’re too big or too small to be their next target.
Counting the True Cost
Beyond the headline ransom note, the financial blow cut deep. Brazil’s attackers demanded $1.2 million in cryptocurrency just to decrypt locked files and even if the government refused to pay, emergency response teams still had to be called in. Forensic experts, incident managers, and legal advisers raced against the clock, billing $2–3 million in overtime and consultancy fees. That’s taxpayer money diverted from health clinics, schools, and infrastructure upgrades simply to clean up a mess that never should have happened.
Then there’s the data and service fallout. Roughly 28 GB of classified documents everything from draft legislation to audit trails slipped into criminal hands. Ministries were forced offline for weeks, slowing benefit payments, passport renewals, and critical policy decisions. Families waiting on social welfare faced delays. Public hospitalsned non-urgent procedures. Even routine government bulletins vanished, leaving citizens confused and frustrated.
On the world stage, Brazil’s cyber resilience took a reputational hit. Journalists pounced on sloppy security lapses, painting a picture of a nation unprepared for modern threats. International partners including trade allies and financial institutions paused to ask if their data was safe. Regulators in Brasília received urgent letters demandingicter cyber-budget oversight, while lawmakers debated new security laws under the glare of global scrutiny. In short, the Fog gang’s strike didn’t just cost millions in hard dollars it rattled public trust, slowed critical services, and sparked political firestorms both at home and abroad.
How Could You Fall Victim? When you are noticed
Imagine this is just between us: the moment you let a simple password slip no second code you hand attackers a master key to your VPN. One crafty phishing email and that hidden . The LNK file quietly installs a backdoor. An unpatched router or VPN box? It’s a welcome mat. And with a flat, open network, once they’re in, they roam free, grabbing everything they need.
So, what should you whisper to yourself each morning to stay safe? Start by locking down every login with multi-factor authentication no excuses. Hunt for patches like it’s your day job: routers, servers, even that little IoT gadget. Master the art of network segmentation so a breach in one corner doesn’t topple the whole house. Learn to spot phishing: never click onent tax-style emails without verifying the sender. Dive into online coursess on zero-trust architectures and endpoint threat detection they’ll be your best friends in this digital jungle.
And here’s the clincher: you don’t have to go it alone. If you’re serious about locking down your defenses, let Hoplon Infosec guide you. Our Endpoint Security Service brings expert audits, real-time monitoring, and rapid response playbooks straight to your doorstep. Ready to stop waiting for the next attack?
Schedule your consultation today, and let Hoplon Infosec turn those whispers of worry into a fortress of confidence.
You’ll know you’re walking into Fog’s trap the second something just “feels off” in your systems:
Unexplained Login Alerts: If you see VPN logins from odd locations or at strange hours, pause everything.
Spike in Network Scans: A sudden surge ofrnal port-scanning or file-share queries means someone’s mapping your territory.
Disabled Security Tools: If your EDR or antivirus suddenly stops reporting, that’s a red flag they’ve found a way to blind you.
Slow File Access or Strange File Extensions: Encrypted or oddly renamed files often come just before a ransom note.
No Cyber-Security Background? Here’s Your Fast Track When you Noticed
Hit “Pause” and Isolate: The moment you suspect intruders, disconnect affected systems from the network stop the spread.
Switch to a Clean Device: Use a known-good computer (like your personal laptop) to call for help and manage communications.
Document Everything: Note times, error messages, odd filenames, or alerts. This will guide investigators.
>> Engage Emergency Support: You don’t need to reinvent the wheel. Call in specialists who live this every day.
Your Next Steps- When You are Under Cyber Attack
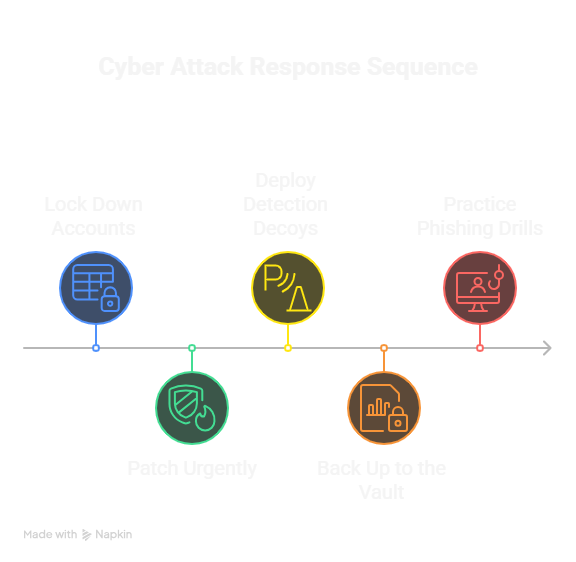
Step 1: Lock Down Accounts: Reset all admin and VPN passwords with strong, unique passphrases and immediately enable MFA on each one.
Step 2: Patch Urgently: Identify the most exposed devices VPN gateways, routers, domain controllers and apply security updates now.
Step 3: Deploy Detection Decoys: Even if you’ve never set up honeypots, simple canary files in critical folders can tip you off when someone’s poking around.
Step 4: Back Up to the Vault: Make a snapshot of your clean systems, store it offline or in a separate cloud account, and test a restore so you know it works.
Step 5: Practice Phishing Drills: Run a mock attack on your team see who clicks, then coach them on spotting red flags.
Emergency Support: Don’t Go It Alone
If you’re half-convinced that something’s wrong but don’t know how to fix it, Hoplon Infosec stands ready. Our rapid-response experts will:
Triage your alerts and isolate threats in hours, not days.
Conduct a full forensics sweep to uncover every backdoor.
Guide you through patching, segmentation, and recovery step by step.
No more guessing games. Schedule your emergency consultation with Hoplon Infosec today, and turn that whisper of doubt into a confident defense.
Wrapping Up
The July 23, 2024, fog attack was a wake‑up call. Even top‑tier government agencies can fall prey when basic cyber-hygiene is lax. The good news is these mistakes are fixable. Stronger authentication, faster patching, and smarter network design can turn the tide.
Stay vigilant. Because in today’s digital battlefield, any unguarded door no matter how small, can blow the whole house down.
Sources
Trend Micro
OCCRP
Crowdstrike
Share this :