Ultimate Guide to Fortinet SSL VPN Brute Force Attack Prevention: Protect Your Network Now

Hoplon InfoSec
13 Aug, 2025
Fortinet’s SSL VPN solutions let businesses all over the world access their networks safely from anywhere. But, like any service that is available on the internet, they can be attacked with brute force. These attacks use computers to try to guess usernames and passwords in order to get into systems without permission. Because these kinds of attacks are happening more and more often, it’s important to put strong prevention measures in place.
Understanding Fortinet SSL VPN brute force attack prevention
An attacker uses a brute force attack on an SSL VPN by trying different combinations of usernames and passwords over and over again until they find one that works. Tools that quickly test many credentials can automate these attacks. They often use weak or common passwords to get in. The goal is to get past the VPN’s security and get to resources on the inside.
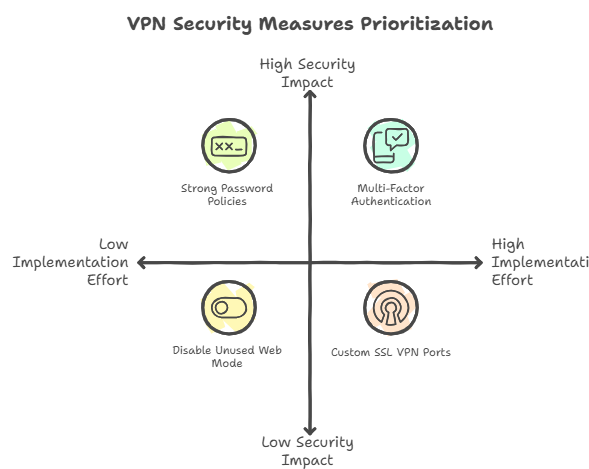
The Importance of Strong Password Policies
Using strong passwords is the best way to keep brute force attacks at bay. Passwords should be hard to guess and have a mix of uppercase and lowercase letters, numbers, and special characters. Making people change their passwords often and not letting them use old ones again can also make security better.
Enabling Multi-Factor Authentication (MFA)
Multi-Factor Authentication makes things safer by requiring users to provide two or more forms of identification. Even if an attacker gets a user’s password, they still need a second piece of information, like a mobile authentication code, to get in. This makes it much less likely that someone will be able to get in without permission.
Limiting Login Attempts and Implementing Account Lockout
Setting up the SSL VPN to limit the number of times someone can try to log in without success can stop brute force attacks. After a certain number of failed attempts, the account can be temporarily locked. This stops any more unauthorized access attempts. This step slows down attackers, making it harder for them to get what they want.
Utilizing Geo-Blocking to Restrict Access
Geo-blocking means limiting VPN access based on where you are in the world. You can stop people from logging in from countries or areas where you don’t expect legitimate traffic if your business mostly works in certain areas. This cuts down on the attack surface by blocking access from places that could be harmful.
Customizing SSL VPN Ports
Changing the default SSL VPN port can help keep the service hidden from automated scanners that look for common ports. Choosing a port that isn’t standard makes it harder for attackers to find and attack your VPN service. This should be part of a bigger plan for security, not the only thing you do.
Disabling SSL VPN Web Mode When Not Needed
SSL VPNs usually have different modes, such as Web Mode and Tunnel Mode. If your company doesn’t need Web Mode, it’s best to turn it off. This makes it harder for attackers to get in, which makes the system more secure overall.
Implementing Automation to Block Malicious IPs
Automation can help a lot when it comes to stopping brute force attacks. Setting up the system to automatically find and block IP addresses that have tried to log in multiple times can quickly cut down on possible threats. This proactive approach makes it harder for hackers to break in.
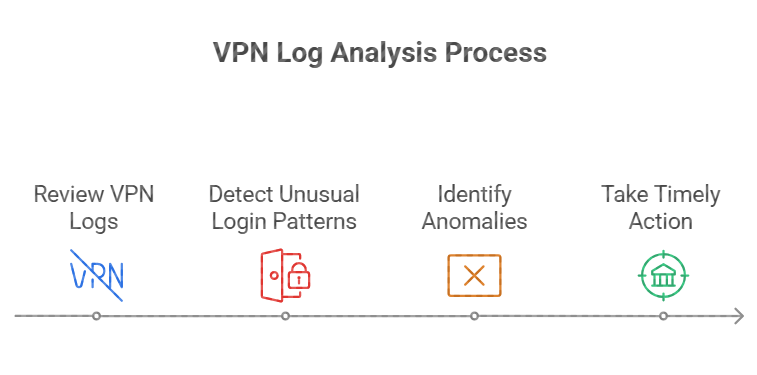
Monitoring and Analyzing VPN Logs
Regularly reviewing VPN logs allows administrators to detect unusual login patterns, such as multiple failed attempts from the same IP address or rapid login attempts from different locations. Identifying these anomalies can help in taking timely action to prevent successful brute force attacks.
Configuring SSL VPN on a Loopback Interface
Putting the SSL VPN on a loopback interface can make it safer by letting you use firewall rules that are only for VPN traffic. This setup gives you more control over who can use the VPN and when, which lowers the risk of unauthorized access.
Educating Users on Security Best Practices
User awareness is an important part of any security plan. Teaching users how to spot phishing attempts, make strong passwords, and report suspicious activity can greatly lower the chances of successful brute force attacks. Common attack vectors are less likely to work on users who have been given power.
Regularly Updating and Patching FortiGate Devices
Updating the firmware on your FortiGate devices regularly lowers the risk of exploitation by fixing known security holes. Regular updates can also make your defense against brute force attacks stronger by adding new security features and making your system run faster.
Implementing Intrusion Detection and Prevention Systems (IDPS)
Network traffic can be watched for known threat patterns and suspicious activity by an intrusion detection and prevention system. You can add an extra line of defense against brute force attacks by integrating IDPS with your FortiGate devices, which allows you to identify and stop malicious activity in real time.
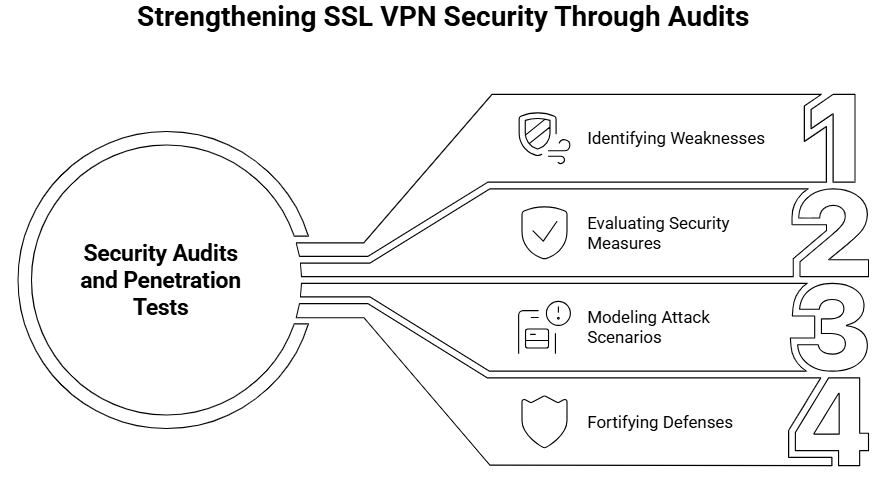
Conducting Regular Security Audits and Penetration Testing
Frequent penetration tests and security audits assist in locating possible weaknesses in your SSL VPN configuration. You can evaluate the efficacy of your security measures and make the required modifications to fortify defenses against brute force attacks by modeling attack scenarios.
Responding to a Successful Brute Force Attack
In the regrettable event that a brute force attack is successful, having an incident response plan in place is essential. This plan should include actions to contain the breach, assess the extent of the damage, notify the affected parties, and implement preventative measures. Rapid and well-coordinated action can reduce the attack’s impact.
Final Thoughts
You need to use a number of different methods to protect Fortinet SSL VPNs from brute force attacks. These include technical measures, teaching users about security, and keeping an eye on things ahead of time. Organizations can greatly lower the risk of unauthorized access by putting in place strong password policies, allowing multi-factor authentication, limiting login attempts, and using automation. Your VPN infrastructure will be even more stable if you keep it up to date, train users, and plan for problems. Cyber threats are always changing, so you need to be on the lookout and do what you can to protect your company’s digital assets.
Explore our services:
Share this :