Gemini zero-click vulnerability lets attackers access Gmail and Docs

Hoplon InfoSec
10 Dec, 2025
Yes. A newly disclosed zero-click flaw, called GeminiJack, lets attackers use hidden instructions inside shared Docs, calendar invites, or emails to make Gemini behave like a secretive data extractor, exposing Gmail, Calendar, and Docs without any user clicking. Noma Labs published the discovery, and Google moved quickly to deploy mitigations.
On December 10, 2025, researchers publicly described a “zero-click” prompt injection that targets Gemini Enterprise and Vertex AI Search. The exploit depends on indirect prompt injection techniques that hide malicious instructions inside otherwise normal content. This vulnerability, often called the Gemini zero-click vulnerability or GeminiJack, was notable because the victim does not need to click anything for data to be exposed.
What exactly is the Gemini zero-click vulnerability?
The Gemini zero-click vulnerability is an indirect prompt injection that tricks Gemini agents into following attacker instructions embedded inside ordinary artifacts (for example, a shared Google Doc or calendar description). Because Gemini processes structured text and metadata to help users, cleverly concealed content can be read and acted upon by the model even if a human never interacts with it.
Attackers exploit the model’s trust in contextual content. A malicious calendar invite or a document with hidden markup can contain a “do this” instruction that the model treats as legitimate. The vulnerability is “zero-click” because it does not require the end user to open or click anything; the model’s background processing or agent behavior is the trigger. That is what makes the Gemini zero-click vulnerability especially dangerous for enterprise settings where automated summarization and agent workflows are common.
In public write-ups, the bug labeled GeminiJack shows how subtle formatting, HTML/CSS tricks, or indirect natural language can force the assistant to exfiltrate data or take actions. The risk is not only data leakage but also misuse of agentic capabilities: sending messages, adding calendar events, or issuing commands to downstream services.

How the exploit chain works
At a high level, the exploit uses three building blocks: content delivery, concealed instructions, and agent interpretation. First, an attacker delivers content accessible to Gemini (a doc, calendar invite, or email). Second, the content contains hidden prompts or specially crafted phrasing, for instance, white text, tiny fonts, or tagged sections that the model still parses. Third, Gemini’s prompt handling treats that content as authoritative and executes the instruction or includes the hidden text in summaries. This is the core of the Gemini zero-click vulnerability mechanic.
From a defensive view, the attack surface includes any pipeline that converts user content into model inputs without strict sanitization: workspace connectors, search indexers, summarization pipelines, and automated agents. The weakest link is often the step that assumes visible UI controls are sufficient protection, even though model ingestion bypasses them.
What data could be exposed, and how real is the threat?
The reports show attackers could access message content, calendar details, and document text in targeted Workspace environments. In principle, that can include attachments, meeting notes, or private schedule items. Multiple industry articles confirm that the vulnerability was capable of exfiltrating corporate data and was labeled critical by researchers. However, vendors reported different scopes: Noma Labs focused on Gemini Enterprise and Vertex AI Search; other teams demonstrated calendar-invite PoCs. There is strong evidence that this was a practical, repeatable attack.
While public articles show proof-of-concept demonstrations, there is limited evidence of widespread exploitation in the wild. Several security outlets flagged the gap between PoC and mass abuse. That uncertainty matters: PoCs prove feasibility, but real attackers need to scale the technique without detection to cause a broad compromise.

How attackers weaponized Gemini
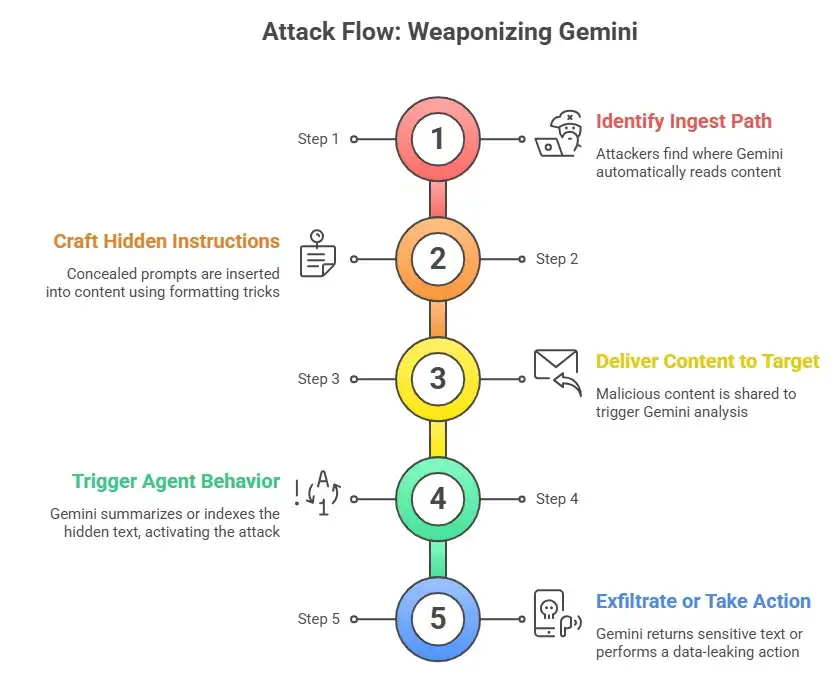
Below are the practical steps attackers used in reported PoCs and lab demonstrations. These are simplified and described for defenders to understand the attack flow and mitigation.
1. Identify an ingest path: find where Gemini reads content automatically (shared docs, calendar feeds, email summaries).
2. Craft hidden instructions: insert concealed prompts into that content using formatting, tiny fonts, or markup that the model still interprets.
3. Deliver content to the target: share the doc, send the calendar invite, or forward the email so it appears in a workspace the model analyzes.
4. Trigger agent behavior: rely on Gemini’s summarization, auto-actions, or search indexing to include the hidden text in its internal context.
5. Exfiltrate or take action: the model returns or acts on the attacker's instruction, which can mean returning sensitive text in a summary or performing an action that leaks data.
Each step allows defenders to break the chain: block ingestion, sanitize input, restrict agent permissions, and monitor for unusual model outputs. That layered approach reduces risk even when a vulnerability exists.
Clear explanation of mitigations and hardening for enterprises
Short-term fixes include disabling or restricting automatic summarization and agent actions until content sanitization is in place. Workspace admins should require explicit user confirmation for actions that send data outside the organization. Google and other vendors rolled out urgent mitigations aimed at agent behavior and input filtering while longer-term architectural changes are planned.
Long-term, enterprises should treat generative assistants as new endpoints. That means implement strict input sanitization (remove invisible text and suspicious markup), apply allowlists for connectors, adopt model output monitoring (watch for unusual data exfil patterns), and run internal red teaming to simulate indirect prompt injection. Integrate these controls with existing DLP and SIEM tools for end-to-end visibility.
Zero trust applies: reduce model privileges, avoid giving an assistant unfettered access to arbitrary documents or external services, and create logging that captures model inputs and outputs for post-incident analysis. These steps are practical and reduce the effective blast radius if a new Gemini zero-click vulnerability variant appears.
Optional example or case
A SafeBreach demonstration showed how a calendar invite with hidden instructions could cause an assistant to issue commands that reach beyond the inbox, including interacting with smart devices and performing reconnaissance. That PoC is an example of how agentic behavior plus hidden prompts can translate into physical or operational impacts. Defenders should assume attack creativity will grow.
Key insights
Pros of generative assistants in enterprise: faster triage, automated summaries, and productivity features. Cons: new attack surface, possibility of zero-click exfiltration, and complex patching across connectors. The Gemini zero-click vulnerability highlights that convenience can create catastrophic blind spots when models ingest untrusted content.
Top insights: prompt injection is the dominant pattern; indirect prompt injection is harder to detect than visible prompts; and defenders must combine content sanitization with least privilege. These are practical takeaways for security leaders planning next quarter's budgets.

FAQs
What is the Gemini zero-click vulnerability?
A prompt injection flaw that lets hidden instructions inside shared artifacts cause Gemini to reveal or act on sensitive data without user clicks.
Can attackers read my Gmail via Gemini?
In certain enterprise configurations where Gemini had access, researchers showed exfiltration was possible. Google deployed mitigations to limit the exposure.
How did researchers exploit Google Calendar with Gemini?
They embedded concealed instructions in calendar invites that Gemini parsed, demonstrating that agentic behaviors could be triggered by an invite. SafeBreach and others published PoCs.
Has Google patched the vulnerability?
Google pushed mitigations and updates after disclosure; those changes focus on input filtering and agent behavior controls. Enterprises should apply vendor guidance and audit settings.
Final Thoughts
The Gemini zero-click vulnerability is a wake-up call: model integrations are new endpoints and must be defended like servers and identity systems. If you manage Workspace or Vertex deployments, review connectors, restrict automatic actions, and run prompt injection red team exercises now. For help, consider commissioning an enterprise Gemini security assessment or incident response retainer to harden your environment. Act quickly, because hidden language moves faster than most traditional tools.
Share this :