Jingle Thief Gift Card Scam: Protect Your Business

Hoplon InfoSec
23 Oct, 2025
Picture a cyber-heist taking place in the cloud. They don't breach into servers or use ransomware; instead, they silently steal value by giving out gift cards. That's exactly what is happening with the rising danger of phony gift cards. The Jingle Thief campaign highlights how thieves exploit cloud infrastructure and identity systems to change gift cards into real money.
Retail and consumer services companies need to understand that phony gift cards are no longer a small problem, but a big aspect of advanced cyber fraud in this digital age.
What is the scam with the Jingle Thief gift card?
In October 2025, Unit 42, which is part of Palo Alto Networks, found a cloud-based scam involving gift cards. They name it Jingle Thief. The attackers target companies that sell gift cards, which are typically in the retail and consumer services industries.
Here's a basic rundown of how the campaign goes:
• Attackers use phishing and smishing (SMS-based) baits to get people to give them their login information for cloud services like Microsoft 365.
• After users get in, they use identity systems, device registration, inbox rules, and SharePoint/OneDrive file shares to learn how to give out gift cards and how the business works.
• Once they have access, they can give out gift cards without authorization, generate money by selling them on the gray market, or launder them like short-term loans.
• All of this happens inside cloud workflows no malware-laden endpoints, no ransoms, simply little sums of value taken silently and at scale.
To put it simply, this is cloud-based gift card fraud that leverages identity-based tactics instead of typical endpoint breaches.
Why do you give gift cards? Why utilize the cloud?
There are a lot of reasons why scammers enjoy gift cards:
• To use them, all you have to do is give them some personal information.
• It's hard to find them once they're given out. They are nearly like cash.
Why Many businesses don't have gift card systems that are secure enough. They are easy to attack since they have a lot of internal rights, inadequate logging, and not much monitoring.
Why should you use cloud infrastructure?
As more companies switch to cloud-based services, so do criminals:
• Attacks that target identification are taking the place of the "perimeter." Jingle Thief actors don't use traditional malware as much as they do cloud identity services.
• Microsoft 365, SharePoint, and Entra ID are cloud platforms that contain policies and procedures for giving out gift cards. Once hackers break into these services, they may see how the business runs.
• Firewalls and endpoint detection programs don't work as well while you're in the cloud. The attackers use actual accounts and services to fit in.
"Gift card fraud via Microsoft 365 compromise" and "cloud gift card fraud attack" show how financial crime is changing.
Here's how the Jingle Thief Campaign works, step by step.
This is how the Jingle Thief campaign, which goes after cloud-based gift cards, works. I'll explain each process and provide you real-life examples to assist you in comprehending.
Getting in at first: Phishing or Smishing
At first, it's not dangerous. An employee gets an email or text notification that seems authentic, including "Your account will be locked," "ServiceNow ticket pending your review," or "VPN renewal required." These mails offer links to bogus login sites that look like Microsoft 365 or other services that people trust.
For instance, picture someone putting a bogus ID badge in your wallet. You let them in because you believe them and trust them. Then they utilize that badge to get into places they shouldn't be. This is what's going on here: People that steal credentials can use them to sneak into cloud services, just like phony badges.
Credential phishing via smishing, logged from attackers’ infrastructure: source
Cloud Reconnaissance: Looking at SharePoint and OneDrive
The attacker doesn't rush to give out gift cards once they're inside. They gaze around the surroundings instead. They check for things like spreadsheets, ticketing systems, workflow diagrams, VPN access guides, and directions on how to give out gift cards.
It's like getting into a bank's office at night and walking about the corridors discreetly, peeking through windows until you locate the drawings for the vault and the code to get into it.
Phishing and going sideways inside the corporation
The attacker then sends phishing emails to other workers using accounts that have been hijacked. Other employees are more likely to trust the emails because they come from people who work there. They build their base by using trust within the company.
This side-to-side motion enables you to gain higher-level rights or access to the system that gives out gift cards.
Stealth and Persistence: Rules for registering your device and inbox
During reconnaissance and lateral movement, stealth is highly important:
• Inbox rules are in place to automatically send some emails, like gift card approvals and financial workflows, to addresses outside of the company.
• Phishing emails that were sent are transferred to Deleted Items, and the replies from victims are deleted to hide their trail.
• Entra ID registers rogue devices, attacker-controlled authenticator apps, and MFA is discreetly circumvented or subverted.
Imagine someone sneaking around your building and softly adjusting the locks on your doors so they can get back in even after you change them. Setting up device registration and rogue MFA does that.
Giving out gift cards and then selling them for cash
Finally, the attacker accesses the system that issues gift cards and proceeds to make gift cards that aren't allowed. These cards are usually worth a lot of money and may be used in a lot of different ways. People then sell these cards on gray markets or use them in money-laundering chains.
It's hard to discover the fraud because it happens in a real cloud workflow and the logs are minimal. It might not be detected for a long time. One case that was reported showed that access was left open for almost 10 months, and more than 60 user accounts were stolen in one organization.
Why it's easy to hit retail and consumer services
It's clear why this kind of fraud damages firms that sell things to people the most. A lot of these stores have gift card systems that permit a lot of individuals in, such as staff and merchants from outside the store. If just one account is hacked, an attacker can get in and use that access.
Most of these companies also use cloud services like Office 365, SharePoint, or OneDrive to do their daily work. This makes it easier for people to work together from different places, but it also means that thieves may do all of their work in the cloud without sending off the traditional security sirens.
The time is also helpful for them. During the holidays and major sales, stores get busy and hire temporary labor. Sometimes security checks aren't as strict. That's when assailants frequently strike, which is why the campaign is called "Jingle Thief."
It becomes worse because it's hard to find out where a gift card went or who used it after it was used. The money is gone before anyone knows what occurred if a criminal rapidly cashes it out or sells it again.
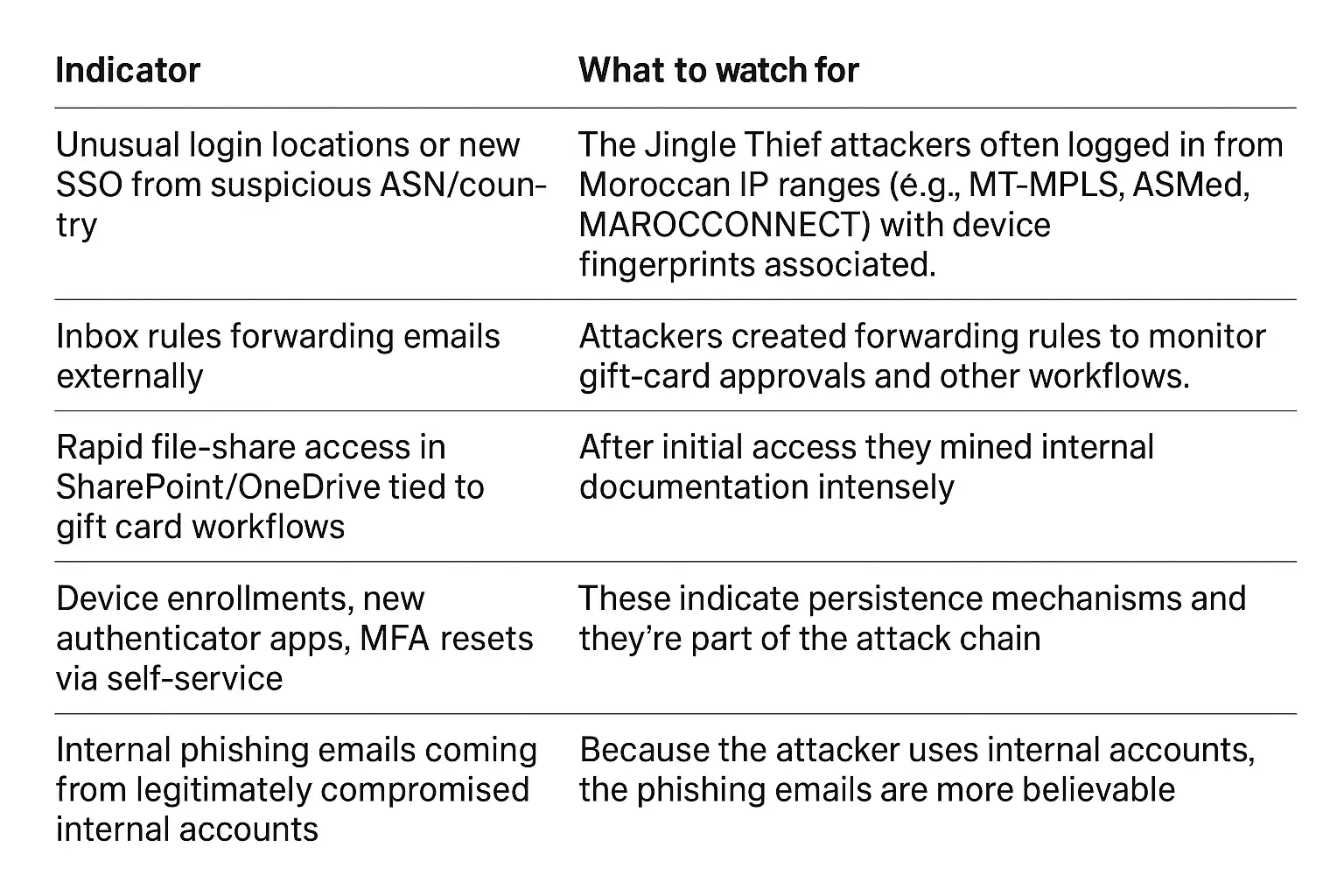
Important Signs and Warnings
Mitigation and Defense
campaign? Fighting gift card theft in the cloud Here are some useful things to do that go along with the signs above:
Strengthen protection of identity.
Let's start here: this whole campaign is centered on stealing people's credentials and using them for negative things.
• In Microsoft 365 (and other similar cloud services), use strict conditional access controls to stop logins from devices or places that look suspicious or aren't known.
• Require MFA everywhere and keep an eye out for unusual authenticator app sign-ups.
• Watch the flows of device registration: alerts should go out when bad devices come up.
Make it easy to keep an eye on cloud workflows.
You need to be able to observe what's going on because hackers use cloud services without making a big deal out of it.
• Watch over who has access to SharePoint and OneDrive, especially when there are sudden increases in access to documents about issuing gift cards, internal procedures, or ticketing systems.
• Watch out for inbox rules, mail forwarding rules, and mailbox transfers that don't seem right, such as moving from Sent to Deleted.
• Use Identity Threat Detection & Response (ITDR) and User Entity Behavior Analytics (UEBA) to look for trends that don't make sense.
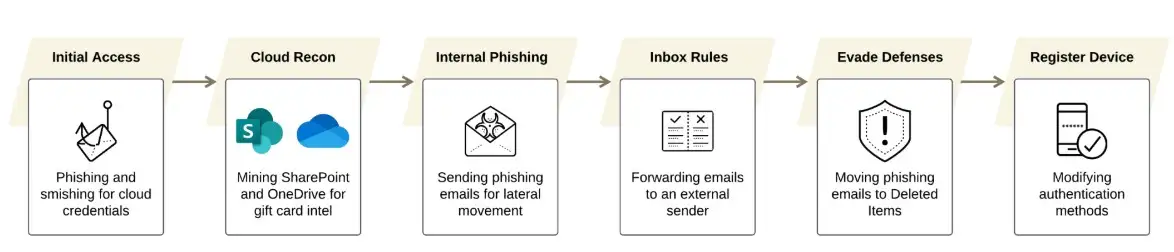
Jingle Thief phishing attack chain across Microsoft 365. source
Make it harder to receive gift cards.
Because giving out gift cards is the most common way to perpetrate fraud:
• Only a small number of people should be able to issue cards, and their jobs should be different.
• Keep an eye on all the processes for giving out gift cards and pay special attention to any that stick out, including cards that are worth a lot or cards that are given out at odd times.
• Find out who can utilize issuance systems for suppliers and store personnel, and use the least-privilege approach.
Make email security and internal awareness your top priorities.
That includes
• Show your workers how to tell the difference between phishing and smishing messages, especially ones that look like IT service bulletins.
• Do mock phishing efforts inside the company to persuade people to pay attention.
• Watch for odd trends in internal email flows that come from internal accounts.
Check to see whether you are ready for forensic work and responding to incidents.
This campaign is very sneaky:
• Keep track of device registrations, changes to multi-factor authentication, changes to mailbox rules, and who has access to SharePoint and OneDrive.
• See if you can transition from identification indicators to procedures for issuing gift cards.
• Have plans in place for when you think someone is trying to conduct gift card fraud. For example, you could freeze the systems that issue cards, take away their credentials, and keep an eye on how they use the cards.
Case study
A retail worker gets a compelling text message that appears like a ServiceNow alert and, believing it to be real, inserts their Microsoft 365 login information into a bogus page. With those credentials, an attacker may easily go into the company's cloud space and look through SharePoint and OneDrive until they uncover the instructions for making gift cards and the system managers use to do it. The attacker sends fake internal messages to accounting while pretending to be IT and lures another employee into giving them additional access.
The attacker sets up a rule for their inbox to send approval emails to an outside address. Once they gain more access, they start handing away digital gift cards worth a lot of money. People sell those cards quickly on sites that aren't official. They register a rogue device and pair it with an authenticator app that the attacker controls to stay in the system. They can keep coming back even if they change their password this way.
The logs demonstrate that the behavior seems like routine business; thus, the theft might continue on for months without anyone knowing. It could cost millions of dollars before anyone figures it out. This is how fraudulent gift cards function in a cloud-based Jingle Thief campaign.
Why the Trend Matters to You
This is important for you to know if you work in cybersecurity, retail, banking, or vendor management.
• Your conventional defenses may not function as well anymore because hackers are moving away from endpoint-based attacks and toward identity and cloud-only operations. The attacker doesn't need to drop malware; they just use stolen credentials and legitimate services.
• Gift card fraud has a hidden financial effect: it can go unreported for months, and if the cards are used or sold, it is very hard to track down and retrieve back.
• Retail and consumer services organizations are being attacked from both within and outside by cyber threats and flaws in their processes and identities. A lot of people think that the road from employee credentials to losing money is longer than it really is.
• Campaigns like Jingle Thief are anticipated to become more popular around the holidays when consumers buy more gift cards. Timing is essential; attackers take advantage of moments when there is less monitoring and more traffic.
• If you don't include issuing gift cards in your threat model, you're not protecting yourself well enough against financial fraud. People are using gift cards more and more to commit cloud fraud for money.
Things you should keep in mind
• Fraudulent gift cards are no longer just a basic fraud; they are now at the center of intricate cloud-based schemes like Jingle Thief.
• The "cloud gift card fraud attack" approach is centered on stealing people's identities, using cloud operations, and issuing gift cards in retail and consumer services organizations.
• Defense entails making it difficult for anyone to get to private information, making it easy to observe what's going on in the cloud, limiting who can open new accounts, and teaching employees about phishing and smishing.
• Keeping a watch on device enrollments, inbox rules, SharePoint access logs, and the issuing of high-value gift cards should all be part of your security strategy
• Businesses that don't pay attention to this risk could be the next victims of a campaign like Jingle Thief if gift cards become easier to transfer into cash and harder to manage.
Last Thoughts
People could think of "small-time scam" or "stealing gift card codes" when they hear the phrases "fraudulent gift cards." The Jingle Thief campaign reveals that gift card fraud on a corporate level is a complicated, clandestine, cloud-based organization conducted by crooks who want to make money. They go inside Microsoft 365 and issue workflows for months at a time by using stolen identities.
Then they strike when the timing is appropriate. Companies may fight back effectively by considering identification as the new perimeter, focusing on cloud infrastructure gift card fraud, and treating gift card issuance systems as financial-risk assets.
If you haven't already, now is the time to review your policies for sending out gift cards in the cloud. There is no longer a small-time concern from bogus gift cards; they are a full-scale hazard that you should pay attention to.
Penetration testing helps uncover weak points in cloud systems, gift card workflows, and employee access before attackers can exploit them.
Share this :